
How Browser Sync Can Unknowingly Risk Your Business
An innocuous and maybe a hard worker employee sought to simplify their routines, inadvertently setting a sinister chain of events in motion; they made the decision to activate browser sync via their personal email. It is a seemingly innocuous attempt to facilitate seamless transitions between their workplace and home environments; however, within this pursuit of efficiency lies a critical oversight – a lack of vigilance regarding password security, exemplified by the absence of two-factor authentication (2FA) through a virtual multi-factor authentication (MFA) device.
A threat actor, in a day, breached the employee’s personal email account. Armed with unauthorized access, they exploited the browser sync feature. This opened a digital gateway to their confidential world, unveiling stored credentials, browser extensions, and other guarded information. Through the compromised email, the infiltrator gained access to not only private information about the employee, they also glimpsed into their professional sphere.
The threat actor manipulated the acquired information to advance deeper into the corporate domain. With pilfered VPN credentials acting as their key, they infiltrated the company’s secure network. Confidential data and sensitive information became their treasure trove, as they exploited their unchecked access to the fullest extent.
The quest for convenience had precipitated this horror and unleashed a relentless adversary, capable of infiltrating and plundering both personal and professional domains with chilling efficiency – a stark reminder that the pursuit of convenience can inadvertently pave the way for dire consequences.
This is a true digital horror story, not fictional, it is what a famous company experienced in 2022, and depicts a chain of events that paved the way to hacking of a big company: Cisco.
Comfort vs. Security: The Dilemma Paving the Path to Hell
In today’s world, a constant dilemma exists: selecting between comfort and security. Achieving a balance between these factors is not always simple. While we seek comfort, the necessity of security becomes more apparent. The saying that “exceptions prove the rule” is accurate in this context.
Our entire digital life is intertwined with web browsers. They serve as conduits for accessing bank accounts, emails, business dashboards, and even tracking our children’s school progress. The beauty lies in the simplicity; browsers provide access to a diverse range of services without requiring excessive software installations. Just by typing our username and password, if we are not in a minority who takes security seriously and enables multi-factor authentication, we can access everything.
Browsers offer a plethora of features that streamline our lives, from automatically filling usernames and passwords to addresses. They efficiently manage payment information, providing an irresistible convenience. Seamless transition between devices at our home and work sounds fabulous at first. Continue to work at home, sync what we did overwork with our company laptop and more… Browser sync steps in as a remarkable advancement, allowing seamless transitions between devices, enabling users to synchronize beyond saved passwords to include payment methods, browsing history, active tabs, and extensions.
However, it is essential to consider the other side of the coin – the risks. Have we ever considered the risks we have exchanged for this sense of relief?
A Brief Overview: Evolution of Browser Sync
In 2006, we witnessed a primitive form of browser sync through an extension, Google Browser Sync, developed by Google, enabling Firefox users to sync their data with their Google accounts. This rudimentary version shared a similar data scope with today’s iteration, with one notable distinction: although it included cookies, it lacked extensions. This might be attributed to the absence of cross-browser extension compatibility during its inception.
Google then stopped this integration in 2008:
In 2009, we saw Google’s first step for browser sync between devices starting with bookmarks:
In 2012, Google led the way in browser sync with its well-known Chrome browser. This signaled the start, and shortly thereafter, other major browsers embraced this captivating feature, incorporating it into their own offerings. Zooming ahead to today, the panorama stands as evidence of the extensive embrace of browser sync. Notably, Google Chrome, Microsoft Edge, Opera, Brave, and various others have adopted this approach, firmly establishing its presence in the digital realm.
Default Behavior of Browser Sync
Upon initiating browser sync, users trigger a process that shares a plethora of vital data across devices. By default, this synchronization encompasses a comprehensive array of elements, including saved passwords, browsing history, meticulously curated bookmarks, settings, themes, and even the intricate network of extensions that enrich our browser experience.
Briefly, when you initiate synchronization, various data stored on the browser will be shared among the devices that use the same email address with which you started synchronization.
Unspoken Risks: Unforeseen Perils of Browser Sync
Data theft is the most significant risk among those that come with browser sync. An attacker exploiting synchronization can gain access to your browsing history, autofill passwords, addresses, payment data, and more.
Someone who requests permission to check their own email on your computer can, under this seemingly innocuous request, enable syncing and steal all the data from your browser.
When we prioritize comfort, it is important to recognize that security might be the price we pay. Similar to data, browser extensions can also be transferred between devices after synchronization. Unfortunately, some of these extensions can be malicious in nature. While Google strives to maintain a secure extension market, there is still a potential risk. Enabling debugging mode allows users to import extensions without requiring installation from the official extension market.
Moving beyond personal interactions, browser sync creates opportunities for larger breaches. By cleverly infiltrating less secure home environments, cybercriminals can use synchronization to expand their influence into more secure work settings. This becomes even more significant if malicious extensions are involved, as they automatically synchronize and seamlessly transfer to the targeted system, posing substantial threats.
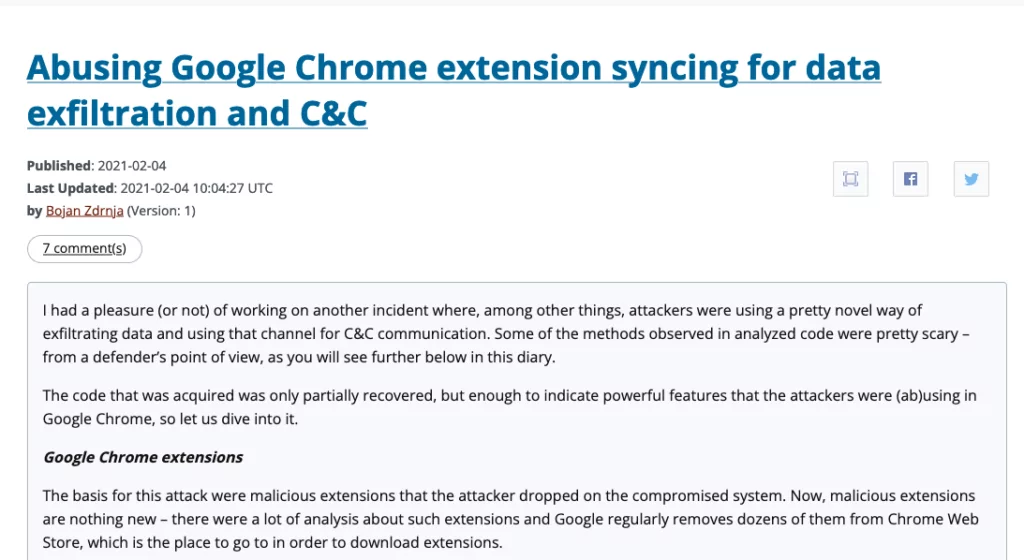
Physical access and using an email under their control is not the only way that a threat actor can initiate synchronization. Another risk we must consider when contemplating browser sync is business email compromise (BEC) or email compromise.
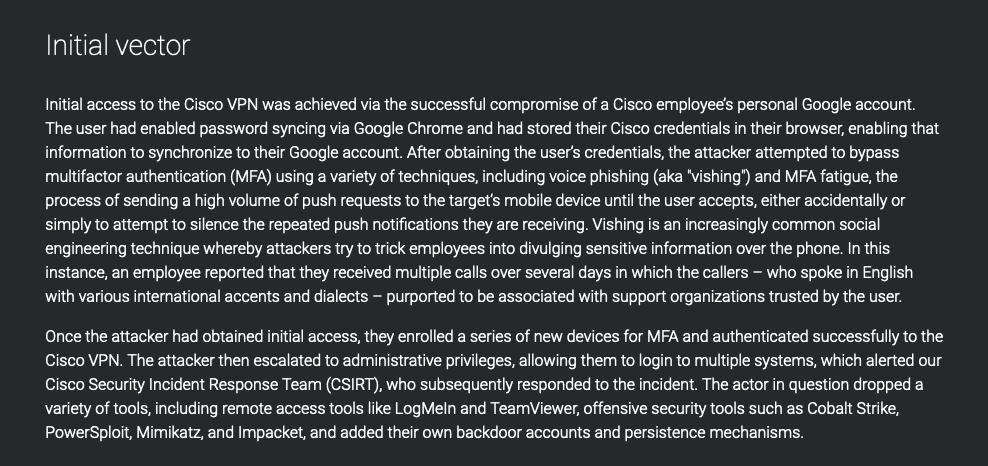
Cisco’s public disclosure of a case vividly underscores these possible risks. The compromise of an employee’s Google account unveiled a disconcerting truth – the credentials stored in the browser were synchronized, inadvertently exposing sensitive information to prying eyes. The implications extend from individual contexts to the corporate realm, where business email compromises can escalate into extensive organizational breaches.
How Can You Prevent the Issue of Browser Sync?
First of all, determining if browser sync is enabled is key. The clear indicator in the interface acts as a guard, helping you ascertain if your data goes between devices. This proactive approach balances comfort and security, guiding you through the digital landscape with clarity and caution.

You can disable syncing by using browser settings:

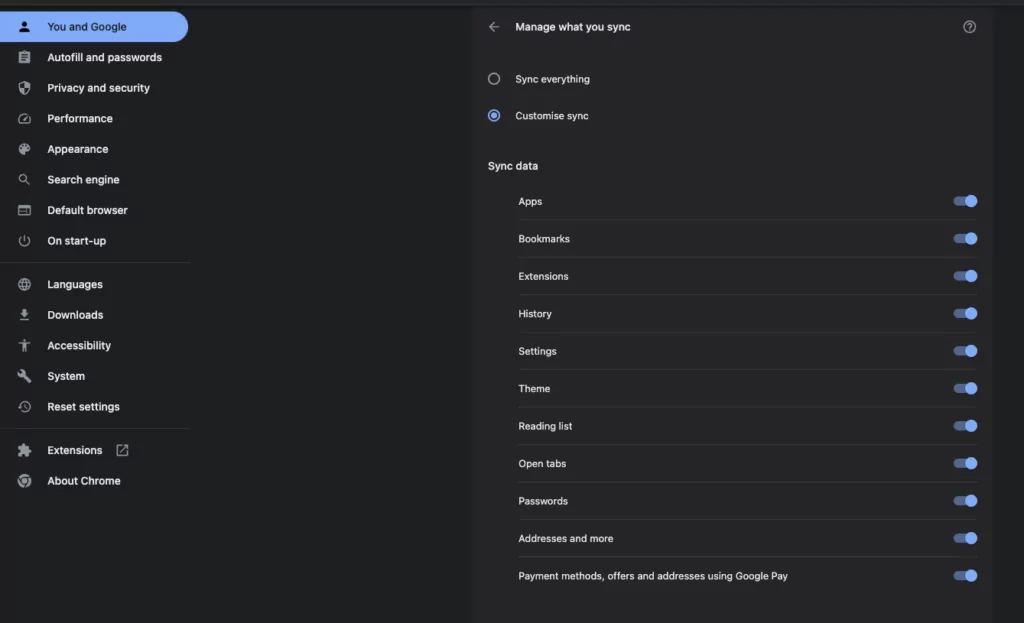
If it is required to enable browser sync, you can control which data will be synced between devices:
It is also possible to see between which devices our browser data has been synced by visiting the about:sync page.
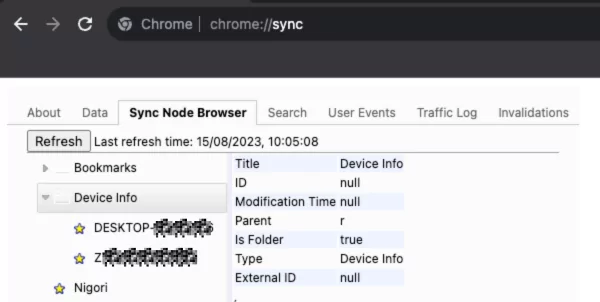
It is possible to check which data has already been synced through this URL. The dashboard displays the amount of data synchronized and stored in Google’s cloud system. The most recent sync date and time are also visible:
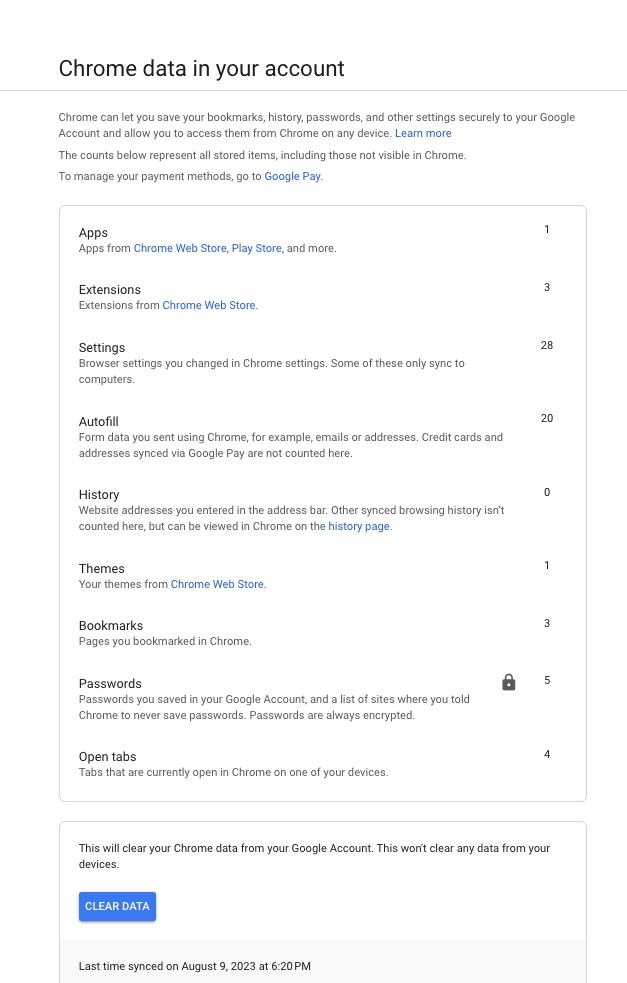
There are two significant details on this page: Firstly, we observe that passwords are stored in encrypted form within Google’s infrastructure. Additionally, there is a button enabling users to erase synced data. It is important to understand that this action will not eliminate data already synced with devices; it solely removes it from Google’s cloud infrastructure.
How to Disable Browser Sync?
To disable browser sync at OS level:
- To initiate this process, press the WIN and R keys concurrently, launching the RUN dialog box. Next, type “regedit” and hit Enter to unveil the Registry Editor.
- Navigate to the subsequent key: HKEY_LOCAL_MACHINESOFTWAREPolicies.
- Within the “Policies” key, establish a fresh key and designate it as “Google.” In case the key is already existent, proceed to Step 4.
- Under the “Google” key, generate another key entitled “Chrome.” If this key is already present, proceed to Step 5.
- The cumulative key path should now be: HKEY_LOCAL_MACHINESOFTWAREPoliciesGoogleChrome.
- Select the “Chrome” key, and in the right-side panel, right-click and opt for the “New -> DWORD (32-bit) Value” choice. Label the new DWORD as “SyncDisabled.”
- Double-click the “SyncDisabled” entry and configure its value to 1.
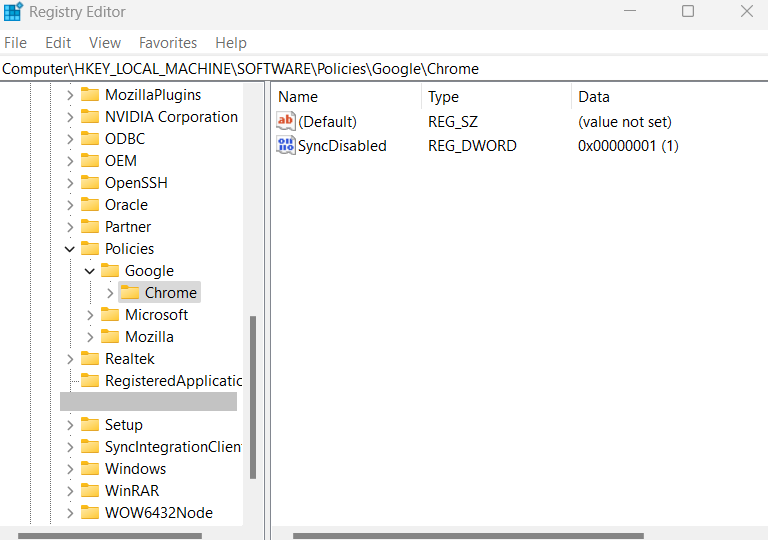
You will notice the message “Your browser is managed by your organization” displayed at the page’s top. This signifies the activation and implementation of the policy outlined earlier in Chrome.
Balancing Comfort with Vigilance
You do not need to sacrifice security to accommodate your requirement for seamless multi-environment utilization.
Organizations should implement policies encompassing secure device and email usage, and oversee BYOD principles.
- At the security policy level, disable profile synchronization.
- Prevent saving passwords in the browser, instead adopt use of password managers and use of MFA company wide.
- If necessary, limit the installation of browser extensions to a list of trusted extensions, or prohibit it altogether.
Utilize SOCRadar XTI to Get Informed Ahead of Time
As highlighted in the article, browser sync, as a feature, is not an issue or vulnerability by itself. However, it can become dangerous when combined with several factors, such as physical access to the device, lack of security policies, and email compromise.
SOCRadar offers a vigilant shield through VIP protection, triggering alerts if high-ranking company personnel become victims of hacking or digital asset breaches. Your organization’s CEO, CFO, and other key executives are primary targets for threat actors who try to exploit their names, images, and online presence to target them and their business network. Continuous monitoring for exposed personal data or impersonation of key executives can mitigate harm in both the cyber and physical spheres.
SOCRadar enables security teams to search for and monitor critically important personal email addresses of C-suite individuals, whether they are indexed within the expanding database of major worldwide breaches that adversaries may seek.
Furthermore, you can periodically refer to the SOCRadar breach database, which contains more than 10 billion records, to confirm whether your employees’ addresses appear in the breach listings.




































