
How SOCRadar Helps You Improve Your CTEM Program
Gartner published a report at the beginning of December 2022 and predicted how enterprises should implement a cybersecurity understanding for 2023 and beyond. The report’s main argument was that organizations should expand their cybersecurity strategy from threat management to exposure management. Thanks to this perspective, which Gartner named Continuous Threat Exposure Management (CTEM), an evidence-based approach to risk management would be possible. Gartner also continued to mention CTEM when sharing its 2024 predictions for the cybersecurity world.
So, why was a program like CTEM needed? Earlier models didn’t work well enough? What kind of changes has occurred in the way organizations do business and on their attack surfaces, so a brand new management approach is required?
Actually, the answer is both simple and complex. In short, organizations’ attack surface has expanded predictably with cloud migration. Data controlled by third parties has reached a point where cybersecurity teams cannot control it. Thus, a new category of security vulnerability that we can describe as a “non patchable vulnerability” emerged.
This article will focus on CTEM and how SOCRadar Extended Threat Intelligence can contribute to CTEM applications.
What is Continuous Threat Exposure Management (CTEM)?
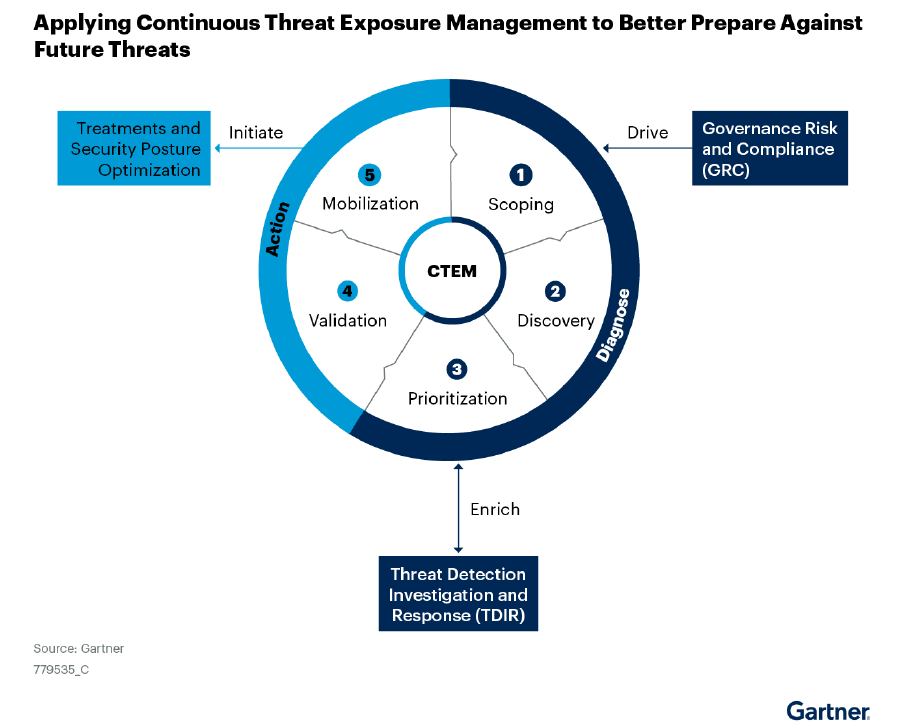
CTEM is a combination of many tools and processes. These include cybersecurity applications such as automated tools, penetration tests, and red teaming. CTEM aims to implement a series of attack simulations to detect a potential vulnerability in organizations’ digital assets before threat actors attack them.
In today’s world, where organizations are irreversibly connected to each other through the supply chain and third parties, it may be enough to look at remote working practices to understand how critical the role of CTEM is. Employees could remotely connect to the company’s digital assets was groundbreaking. It also opened up new lines for threat actors constantly looking for a point of attack.
According to Gartner, Continuous Threat Exposure Management’s biggest contribution is that it helps prepare for an attack at any time with realistic simulations.
SOCRadar’s Cyber Threat Intelligence, enriched with External Attack Surface Management and Digital Risk Protection, makes it much easier to perform the risk management aimed at CTEM. It notifies many potential threats with an early warning system, including cloud misconfigurations and third-party exposures.
SOCRadar Extended Threat Intelligence not only assesses your attack surface and digital assets but also provides contextual intelligence so you can focus on the more critical vulnerabilities under risk rating.
Five Steps of CTEM
CTEM is a program that demands continuity and consists of five phases that complete the cycle: scoping, discovery, prioritizing, validation, and mobilization. Let’s look closely at these processes and explore how to integrate threat intelligence into them.

1. Scoping
Scoping, the first phase of CTEM, is essential for organizations to establish a broad-based plan to detect potential threats and respond quickly. By identifying critical assets and third parties at this stage, organizations take the first step in an adequate protection program against security risks.
One of the essential points to be considered while determining the scope is the evaluation of the attack surfaces and cybersecurity levels of the stakeholders, as organizations host their data on other SaaS providers.
SOCRadar’s Extended Threat Intelligence concept simplifies security teams’ work in the first phase of CTEM as it covers both EASM and CTI services. In addition to discovering digital assets with the hacker mindset, Supply Chain Intelligence in the CTI service enables organizations to closely monitor relevant cybersecurity incidents attacking their 3rd party suppliers by adding vendors to their watchlist.
2. Discovery
The discovery phase includes a series of scans and tests to identify potential vulnerabilities. Identifying these vulnerabilities also makes it easier to prioritize them in line with the possibility of exploitation and the damage they may cause to the organization.
In this step, it is essential to identify all organizations’ digital assets and security controls. Detection of vulnerabilities caused by misconfiguration is also done during the discovery phase. SOCRadar’s Cloud Security Module within the scope of EASM allows defining third-party buckets as assets and following their status changes.
3. Prioritization
With the prioritization phase of CTEM, potential weaknesses uncovered during the discovery phase are evaluated and ranked according to their impact on the organization. This makes it easier for organizations to prioritize more critical vulnerabilities.
A comprehensive list of potential threats obtained by cybersecurity personnel during the discovery phase does not necessarily initiate actionability because not every digital asset requires the same level of security measures. Contextual threat intelligence speeds up the prioritization process.
SOCRadar’s Cyber Threat Intelligence enables classifying and tracking threats by industry or region. Security personnel can make comprehensive profiling, thanks to monitoring capabilities that assist in inferring the behavior patterns of threat actors.
4. Validation
During the validation phase, organizations use a series of processes to test the effectiveness of their cybersecurity postures. These are usually automated scans, manual tests, and penetration tests.
This stage involves emulating threat actors through the simulation of the CTEM program. Simulating a potential breach or attack determines whether the organization’s security controls are adequate.
The validation phase is critical to be prepared for attackers’ ever-changing and evolving attack vectors. SOCRadar’s IOC and Threat Feed services actively help predict adversary behavior by integrating with other cybersecurity solutions. It provides the ability to predict initial access vectors and the lateral movements of the malicious actor infiltrating the system.
5. Mobilization
Gartner summarizes this phase as “setting communication standards and workflows.” Since the cooperation of different departments within the scope of the CTEM program is required, the successful completion of the cycle depends on these organizational skills.
Appropriate tools must be available so that all of the IT, security, and other personnel who play an active role in the CTEM program are on the same page at the mobilization stage. Employees must attend training in line with the program, and relevant procedures must be updated if necessary.
With its easy-to-use interface, the SOCRadar Extended Threat Intelligence platform is a unique tool from which all teams can easily benefit. It is ideal for strengthening cooperation and ensuring all teams have the same perspective on processes. SOCRadar provides many reports, which could be industry, region, or threat specific. All the related personnel can easily reach these reports.
CTEM vs. Alternative Approaches
Traditional approaches like Vulnerability Management, Red Team exercises, and Penetration Testing have their limitations. While they provide valuable insights, they often fail to offer a comprehensive, continuous view of risk. CTEM, on the other hand, integrates these aspects into a unified program that addresses both cloud and on-premises assets, misconfigurations, and identity issues.
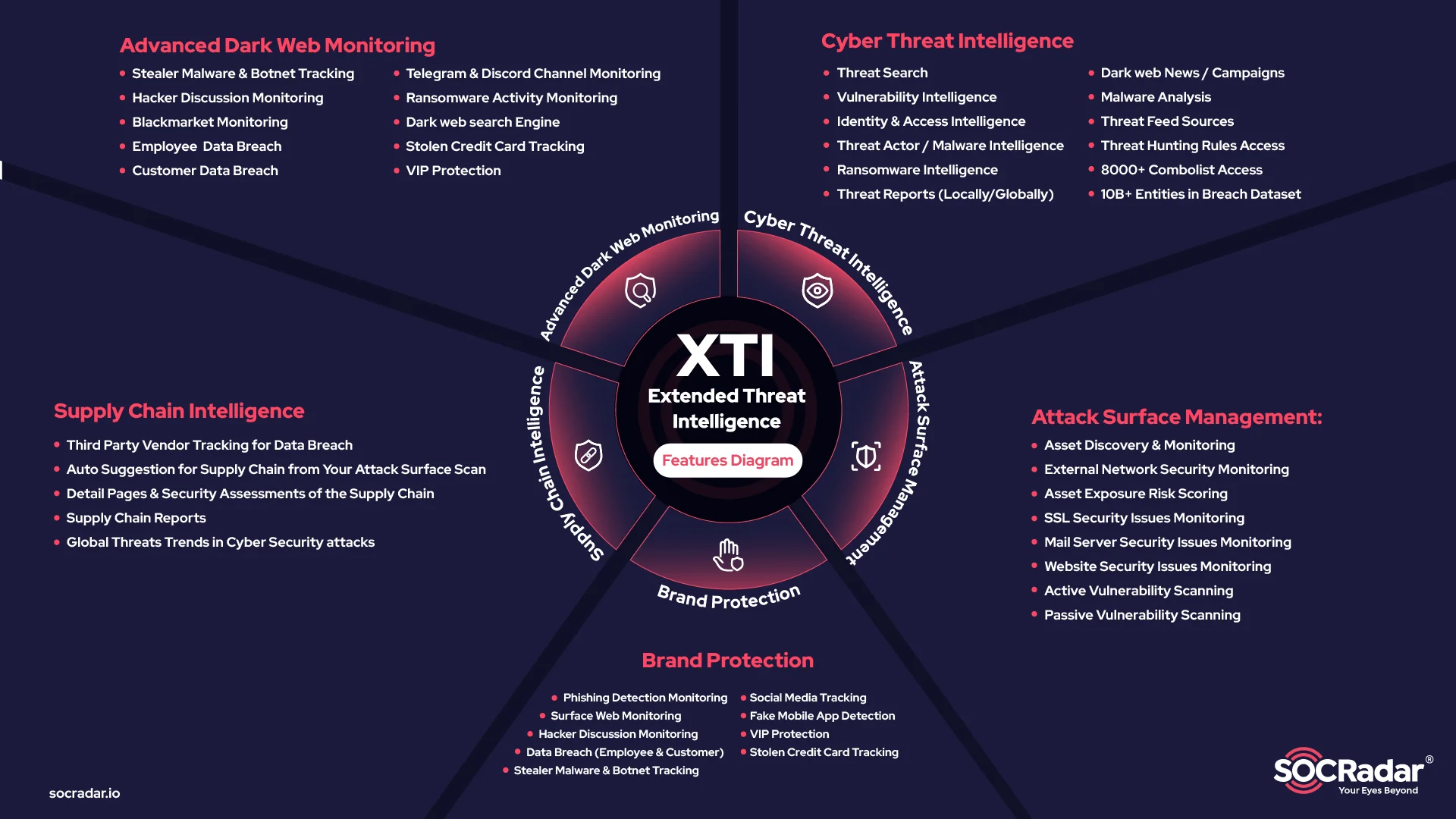
SOCRadar’s Extended Threat Intelligence (XTI) complements CTEM by offering:
-Real-time monitoring and threat detection.
-Comprehensive visibility into attack surfaces.
-Contextual intelligence for effective prioritization and risk management.
Benefits of Cyber Threat Intelligence in CTEM Program
Combining CTI, EASM, and DRP, SOCRadar’s Extended Threat Intelligence (XTI) concept acts as an early warning system against possible threats. With its ML-supported monitoring capabilities, which enable tracking and detecting attackers automated manner, it provides a better understanding of the threat landscape and facilitates threat investigation with its big-data-supported search engine.
SOCRadar’s holistic innovation in threat intelligence enables rapid incident response in scenarios where an attack occurs, as well as the continuous assessment and testing processes that CTEM targets.
Security teams must have a comprehensive view of vulnerabilities for effective risk management. SOCRadar helps identify critical security issues, both internal and external, with vulnerability intelligence and Cloud Security Module in the prioritization process. Thus, both “patchable” and “non patchable” vulnerabilities are controlled.
Improve Your CTEM Program with SOCRadar
In today’s working and business environment, it is not enough to eliminate the risks that cybersecurity controls only cover the risks inside the organizations. Many factors, such as the supply chain and third parties, must be considered and constantly tested to upgrade the security posture. The CTEM program, which aims to protect organizations against attacks from both internal and external threats, seems to become increasingly important as a requirement of this new order.
As we mentioned above, one of the most important conditions for implementing the CTEM program is to have access to the appropriate tools. With its extensive monitoring, asset discovery, assessment, and contextual intelligence capabilities, SOCRadar demonstrates how helpful its CTI solution can be for continuous threat exposure management.
You can request a 14-day demo right now to see Extended Threat Intelligence at work.

Gartner is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s Research & Advisory organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.


































