
Identity is the New Perimeter: An Infostealer Perspective
As organizations navigate an increasingly complex IT landscape, traditional security boundaries continue to dissolve. The modern environment involves globally dispersed users, a blend of personal and company devices, and assets that stretch across hybrid clouds, on-premises data centers, edge deployments, and IoT networks. These shifts, combined with distributed application development across various departments, make defining and managing perimeters more challenging than ever.
Amid these changes, digital transformation and remote work trends have accelerated, bringing convenience but also exposing organizations to more sophisticated risks. The need for rapid, on-demand services has placed identity at the core of cybersecurity. Accessible from virtually any device, cloud-based applications amplify security risks that traditional perimeter-focused tools, like firewalls, can no longer effectively address.
What does all this mean? Simply put, our digital assets now extend far beyond our direct control, making management and security much more challenging than it once was. Many might think that as long as our supply chains, service providers, or major cloud platforms stay secure, we’re safe too—but that’s not the case. Securing the credentials used to access these systems and access control mechanisms are still the responsibility of your organization and its employees. So, how do these credentials become exposed or compromised? The primary threat comes from stealer malware, or infostealers. Let’s dive into the data to understand just how significant this threat really is.
What is the Stealer Threat?
Stealer malware has become a formidable threat in the cybersecurity landscape, particularly when viewed through the lens of identity-based security. According to Verizon’s 2024 Data Breach Investigations Report (DBIR), around 77% of web application breaches involve stolen credentials, making credential theft one of the most prevalent methods for cybercriminals. This statistic highlights how vulnerable organizations remain to credential-stuffing and brute-force attacks, where attackers reuse stolen credentials to gain unauthorized access.
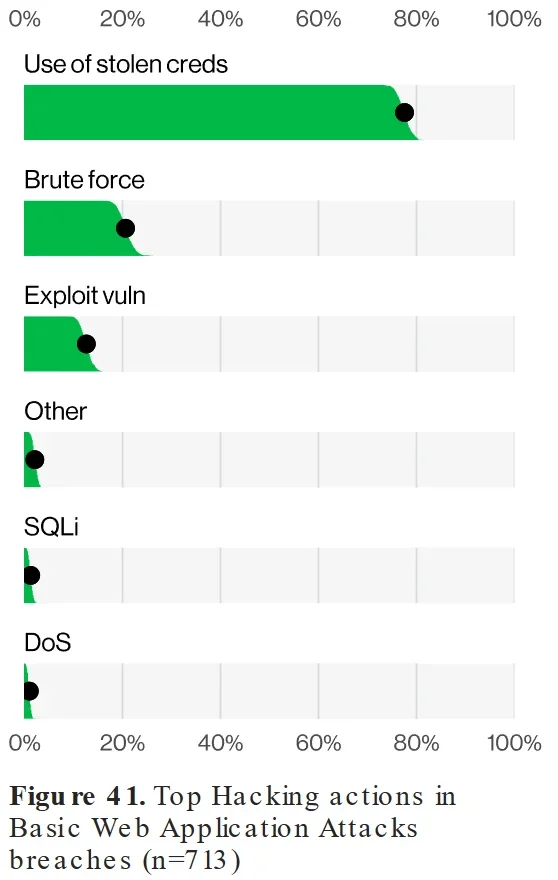
Top hacking methods (Verizon DBIR 2024)
The DBIR also reveals the top stealer malware used by threat actors, often listed for sale on cybercriminal forums. These stealer logs are rich sources of sensitive data, containing a wide range of stolen information, including financial details, login credentials, and personal data. Such logs feed the cybercriminal ecosystem, as attackers use them to infiltrate accounts, compromise networks, and conduct further malicious activities.
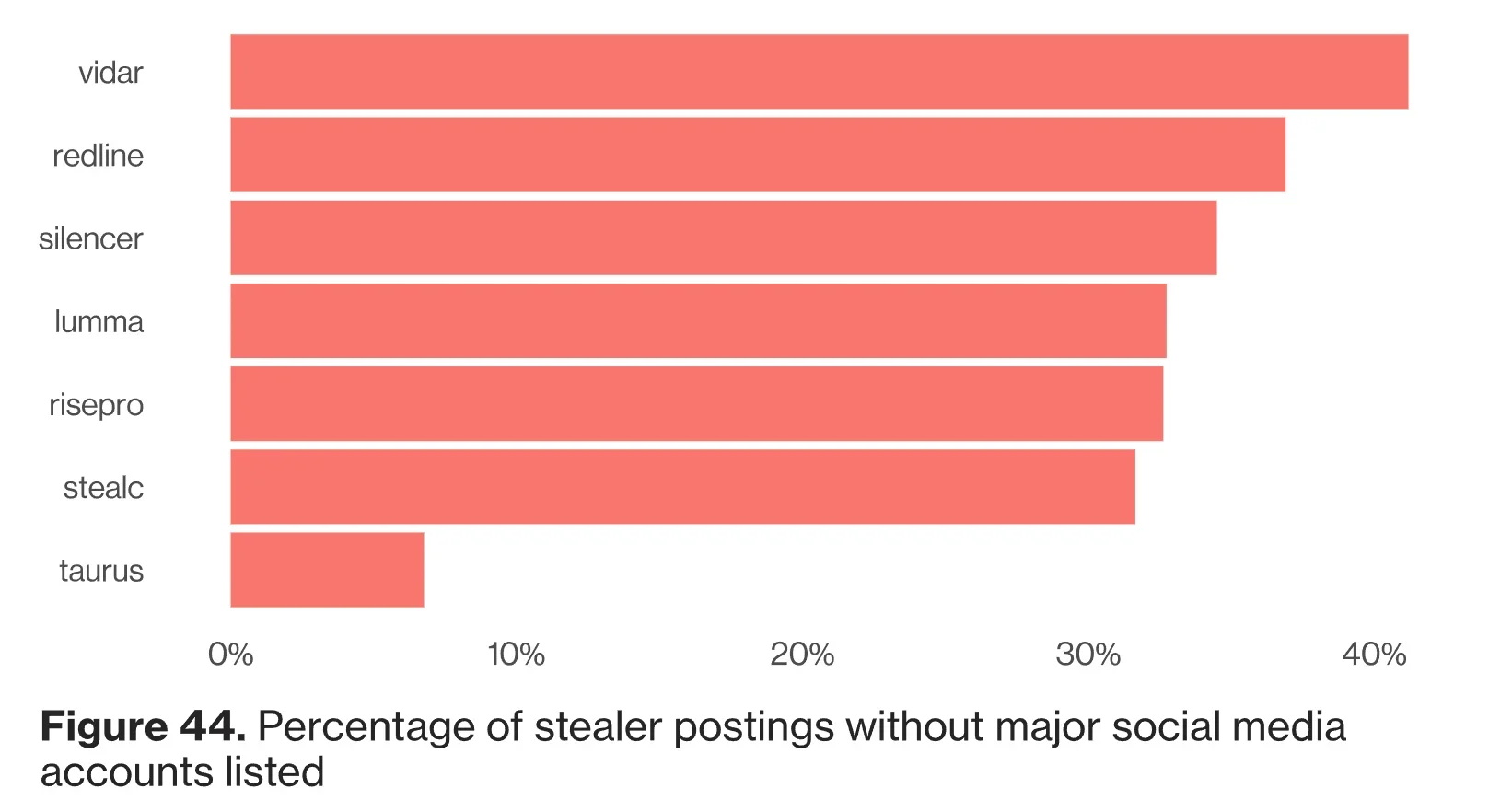
Top stealer malware from postings (Verizon DBIR 2024)
By infiltrating devices and collecting data from browsers and applications, infostealers bypass traditional perimeter defenses and target identity itself. This highlights why, in a world where identity is the new perimeter, organizations must prioritize protecting credentials and enhancing identity security to defend against this growing threat. Now, let’s see how this data disseminated or leaked.
How Identity Data Becomes Exposed
Stolen data, especially credentials from infostealer logs, often finds its way into various Dark Web forums, markets, and through initial access brokers (IABs), who specialize in selling unauthorized entry points to compromised networks.
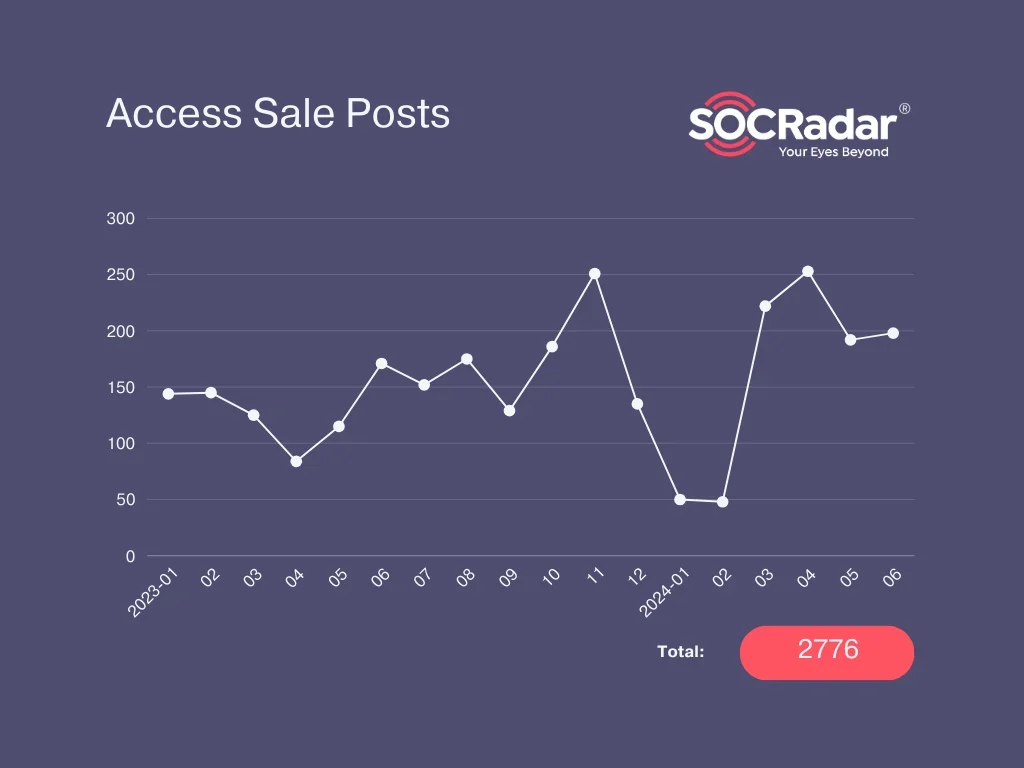
Unique access sale posts in hacker forums between 2023 and first half of 2024, The Rise of Initial Access Brokers on the Dark Web
On Dark Web forums, cybercriminals share and trade stolen data, including login credentials, personal information, and financial details. These forums create a marketplace for malicious actors to buy, sell, and exchange stolen data logs, fueling a continuous cycle of cybercrime. Many of the most active forums are dedicated to facilitating this exchange, connecting buyers with sellers while maintaining a degree of anonymity.
Dark Web markets further commercialize stolen data by providing structured platforms for selling data and cybercrime services. These markets operate like traditional e-commerce sites, offering everything from credentials and stealer logs to ransomware and hacking tools. The top Dark Web markets attract high traffic, making them prime venues for disseminating stolen data to a broader range of cybercriminals.
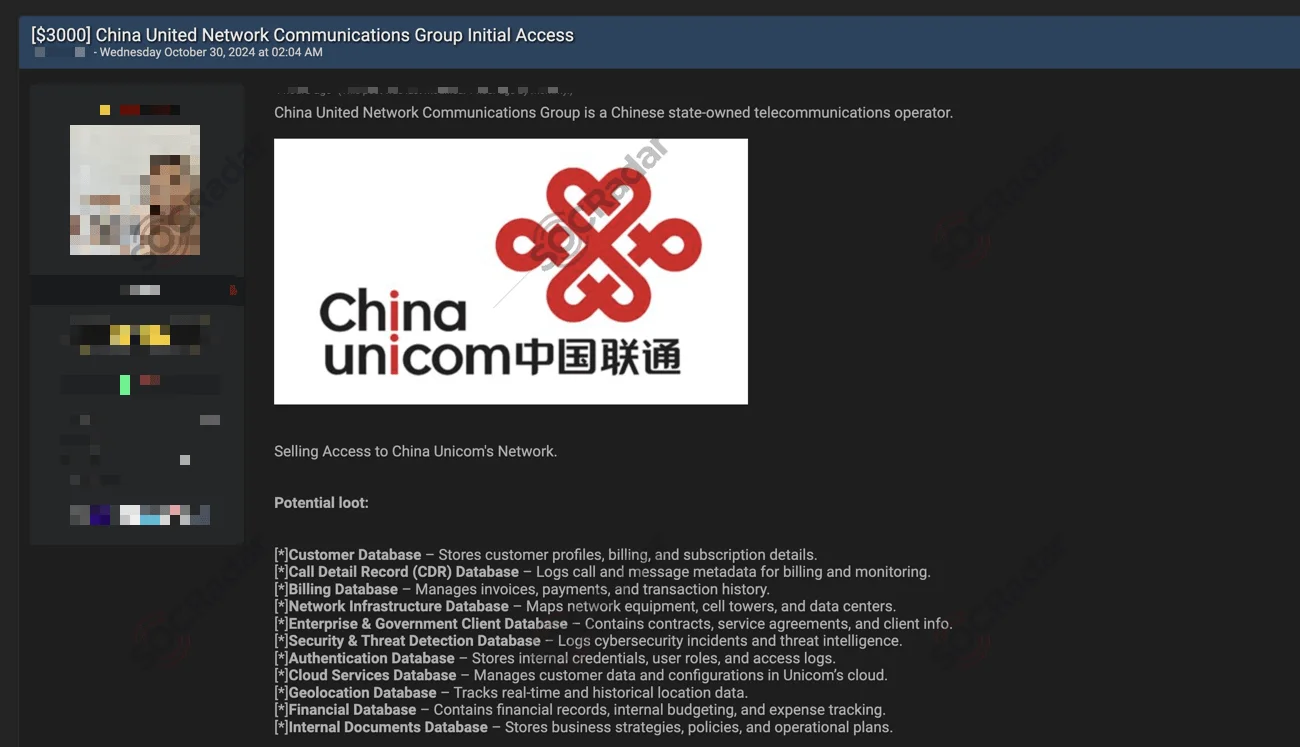
An access sale post in a hacker forum with potential loot defined
Initial Access Brokers (IABs) play a specialized role, acting as intermediaries who sell unauthorized access to compromised systems. This access can be in the form of RDP credentials, VPN accounts, or other network entry points. IABs acquire access from sources like stealer malware logs and make it available to threat actors, often leading to further breaches, ransomware attacks, or data theft.
This ecosystem of forums, markets, and IABs forms a sophisticated network that accelerates data dissemination, posing significant challenges for organizations aiming to protect their assets and identities in a digital world where identity is the new perimeter. We have defined and understood the threat landscape, but what should we do?
How Can You Defend Against These Threats?
One of the most effective defenses against stolen credentials and identity-related threats is Multi-Factor Authentication (MFA). MFA adds an additional layer of security by requiring users to provide multiple forms of verification before accessing accounts or systems.
Even if an attacker obtains a user’s credentials, MFA can prevent unauthorized access by requiring something they don’t have, such as a physical token or biometric scan. Implementing MFA can drastically reduce the chances of successful credential-based attacks, making it one of the best ways to protect against credential stuffing, brute-force attacks, and the exploitation of compromised login information. After these basic precautions, your biggest helper may be the SOCRadar Cyber Threat Intelligence module.
How Does SOCRadar Identity & Access Intelligence Enhance Security?
SOCRadar’s Identity & Access Intelligence is designed to help organizations secure their digital identities and prevent unauthorized access by providing deep insights into compromised credentials and risky user access patterns. By leveraging a vast pool of data from compromised credentials, breaches, and Dark Web sources, SOCRadar empowers organizations to detect and analyze exposed identities.
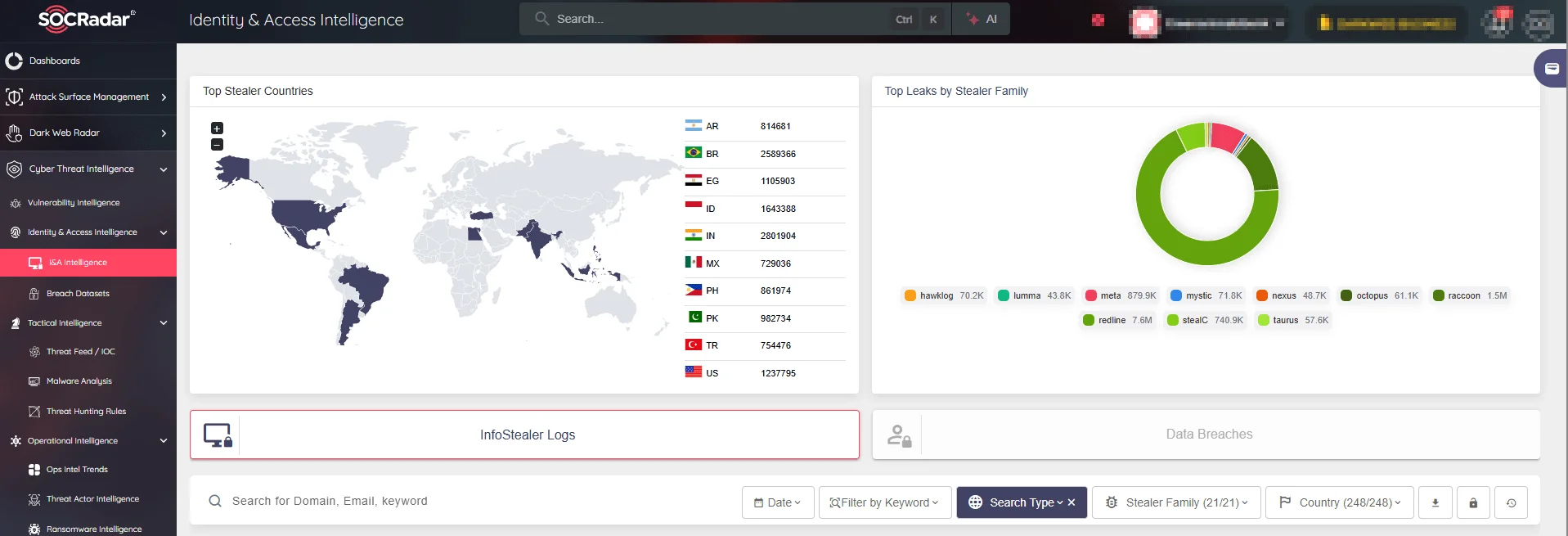
SOCRadar’s Identity & Access Intelligence
SOCRadar’s Identity & Access Intelligence gives you a comprehensive view of how and when identities have been compromised. It analyzes data from stealer logs and breaches, showing the specific identity details, such as username, email, and access URLs, that have been exposed. This enables businesses to understand the scope of the breach and take quick action to protect their assets.
Access Intelligence: The Missing Piece of Your Security Puzzle
While knowing which credentials have been compromised is a crucial first step, understanding the full context of the breach is essential. SOCRadar’s Access Intelligence goes beyond identifying stolen keys—it reveals when, how, and where those keys were exposed.
By analyzing the access patterns of compromised credentials, SOCRadar equips users with valuable data, such as the IP address, date of exposure, and the malware responsible for the theft, allowing for targeted remediation and strengthening of defenses.
The Power of Analyzing Info Stealer Logs with SOCRadar
Stealer logs are among the most commonly exploited data sources in cybercrime, containing vast amounts of stolen credentials and personal information. SOCRadar enables businesses to effectively analyze these logs by providing powerful search capabilities and filters, such as “Stealer Family” and “Country.” This helps you identify compromised accounts, assess the risk to your organization, and prevent further damage.
SOCRadar’s Exposure Timeline Visualization also offers an easy-to-understand overview of infostealer activity over time, allowing you to quickly assess the spread of compromised identities and prioritize responses.
Comprehensive Exploration of Breach Datasets
In the rapidly evolving landscape of cyber threats, timely identification of compromised data is crucial. SOCRadar’s Breach Datasets provide access to extensive collections of breached information, including sensitive documents, credit card details, and personally identifiable information (PII). By utilizing SOCRadar’s comprehensive breach search engine, you can gain critical insights into your organization’s exposure, enabling you to proactively protect sensitive data from malicious actors operating in the Dark Web.
By integrating SOCRadar’s Identity & Access Intelligence into your security strategy, you can take a proactive approach to safeguarding your organization against credential-based attacks and ensure comprehensive protection for your digital identities.



































