Implementing Cyber Threat Intelligence in Software Development Lifecycle (SDLC) Pipelines
The process of creating, refining, and deploying software, encapsulated within the Software Development Lifecycle (SDLC), is a dynamic journey marked by various stages, each posing unique challenges and vulnerabilities.
Cybersecurity in software development is not merely an auxiliary concern; it is a foundation upon which digital assets’ integrity, confidentiality, and availability rest. The escalating frequency and sophistication of cyber threats signify the critical need for proactive and integrated security measures throughout the SDLC. This need has given rise to integrating Cyber Threat Intelligence (CTI) as a decisive component in fortifying the software development process against potential risks.
At its core, the SDLC represents a comprehensive framework outlining the steps in conceiving, designing, developing, testing, and deploying software. Amidst this intricate dance of creativity and technical precision, security cannot be relegated to a post-development afterthought. Instead of considering security as a mere checkbox, it must be seamlessly interwoven into every facet of the development process, from the inception of code to the deployment of the final product.
The contemporary software landscape demands a holistic approach to cybersecurity, one that recognizes the fluid nature of threats and the need for real-time adaptive defenses. It is within this context that CTI emerges as a decisive force. By providing actionable insights into emerging threats, vulnerabilities, and exploit techniques, CTI empowers development teams to preemptively address potential risks, bolstering security in SDLC pipelines.
In the subsequent sections, we will dissect the SDLC stages, elucidating how CTI can be strategically harnessed at each juncture to fortify the development process. From source code analysis to production deployment, we will unravel practical examples and methodologies, showcasing how CTI can help guard against vulnerabilities and potential exploits in software development.
What Are the Steps of a Software Development Lifecycle (SDLC)?
The Software Development Lifecycle (SDLC) is a systematic and structured framework that guides creating, testing, and deploying software applications. It encompasses a series of well-defined phases, each playing a pivotal role in evolving a concept into a fully functional and deployable software product.
The Software Development Lifecycle (SDLC) unfolds in seven key steps:
- Idea Generation: Conceptualizing innovative ideas for software solutions.
- Requirement Analysis: Defining functional and non-functional requirements for the software.
- Product Design: Creating a blueprint for the software’s structure and user interface.
- Product Development: Translating design into tangible code through writing, testing, and refining.
- Integration & Testing: Ensuring seamless integration and conducting various testing phases.
- Build & Deployment: Releasing the software for use with careful planning to minimize disruptions.
- Maintenance: Providing ongoing support, addressing issues, and implementing updates.
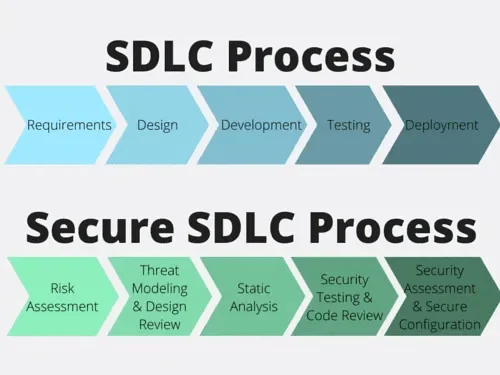
Compared to a Secure SDLC Process
Developers translate conceptual ideas into executable code in the Product/Code Development phase. This stage involves selecting appropriate programming languages, defining data structures, and crafting algorithms to breathe life into the envisioned software.
During the coding phase, as developers translate conceptual ideas into executable code, a foundational emphasis on security is required. This aligns with shifting left, where security is integrated into every stage. This approach advocates for integrating secure development principles, emphasizing that security considerations cannot be postponed until the testing phase following code development. Instead, developers should actively integrate security measures during the development process. Examples of such security measures include utilizing IDE plugins to ensure code security and practicing careful handling of sensitive data to prevent its unintended inclusion in the code.
The Build and Deployment phase involves assembling the code into executable binaries and preparing it for deployment. This process may include compiling source code, packaging dependencies, and creating installers or containers for seamless deployment across various environments. The late sub-stage of this phase is Production Deployment, where the software is released to end-users or clients. This phase involves carefully orchestrating the deployment process to minimize downtime and ensure a smooth transition from development to live production.
The SDLC is not a linear path; it is iterative and can involve revisiting earlier phases as needed. Effective collaboration, communication, and feedback loops are essential throughout the SDLC to enhance the quality of the final product and streamline the development process.
Understanding the intricacies of each SDLC phase lays the foundation for implementing robust security measures. In the subsequent sections, we will explore how Cyber Threat Intelligence (CTI) becomes an integral component at every stage, bolstering the security posture of the software development process.
Cyber Threat Intelligence (CTI) in SDLC
Throughout the Software Development Lifecycle (SDLC), Cyber Threat Intelligence (CTI) acts as a strategic watchtower, monitoring and fortifying the development process against a wide range of potential cyber threats and vulnerabilities.
To developers, filtered and contextually relevant CTI is the most important. Traditional threat intelligence feeds, centered around attack sources, malicious binary signatures, and malware analysis, may not resonate with developers seeking information about specific vulnerabilities.
All in all, in the realm of software development, the challenge lies in aligning threat intelligence with the unique needs and language of developers.
- Developers must always embrace the security best practices.
With economic pressures and the demand for agile development, the Iron Triangle model presents a choice between speed, functionality, and security – forcing developers to prioritize two out of three. By emphasizing security basics and adhering to best practices, developers can create a robust foundation for secure code, minimizing vulnerabilities and ensuring a more resilient software product.
- Incorporating real-world attack scenarios into secure development training provides developers with tangible insights into the impact of software defects on security.
Secure code writing can perplex developers, often due to a communication gap between security professionals and developers. Threat intelligence, especially, becomes a potent educational tool, especially incidents involving actual attacks approach bridges the communication divide and reinforces the notion that secure coding is not optional but a necessity.
- A substantial number of software projects use outdated open-source libraries, leaving potential security gaps.
In an era where developers heavily rely on open-source and commercial libraries, monitoring vulnerabilities within these libraries is crucial. CTI aids developers in staying ahead of threats by providing feeds from open-source libraries, ensuring they have up-to-date information on vulnerabilities. This proactive stance enhances the security posture of software projects, minimizing the risk associated with library-related vulnerabilities.
As we explore the symbiotic relationship between Cyber Threat Intelligence (CTI) and the Software Development Lifecycle (SDLC), the DevSecOps approach also comes to mind. Similarly to how CTI serves as a guardian throughout the SDLC, DevSecOps represents a holistic approach that elevates security from a requirement to an integral part of the development ethos.
What is the DevSecOps Approach?
DevSecOps approach, an amalgamation of Development, Security, and Operations, emphasizes the seamless integration and automation of security practices throughout the Software Development Lifecycle (SDLC), aligning with the overall theme of strengthening software against evolving cyber threats.
In the traditional SDLC model, security measures were often treated as a post-development consideration, leading to potential vulnerabilities slipping through the cracks. DevSecOps rectifies this by embedding security into every facet of the development process, fostering a culture where security is not an isolated phase but an integral thread woven into the fabric of software creation.
- Integration with SDLC:
DevSecOps extends beyond conventional security practices, advocating for security to be an inherent part of the development and deployment pipeline. This integration ensures that security is not a hindrance but an enabler throughout the SDLC, aligning seamlessly with modern development practices’ iterative and collaborative nature.
- Automated Security Checks:
One of the key tenets of DevSecOps is the incorporation of automated security checks at every stage of development. From code commits to deployment, automated tools continuously assess the security posture, identifying and addressing vulnerabilities in real-time. This proactive approach significantly reduces the window of exposure to potential threats.
- Shift-Left Approach:
DevSecOps embodies a “shift-left” mentality, advocating for the early integration of security considerations in the development process. This proactive stance ensures that security is not bolted on at the end but is an integral part of the code development and testing phases, minimizing the likelihood of security issues persisting into later stages of the SDLC.
- Collaboration and Communication:
DevSecOps fosters a culture of collaboration and communication between development, security, and operations teams. This collaborative approach ensures that security requirements are clearly communicated, understood, and implemented across all stages of the SDLC.
Examples of CTI Implementation in SDLC
- Source Code Analysis:
In this phase, CTI can play a role in identifying vulnerabilities within programming languages and libraries.
Understanding TTPs (Tools, Techniques, and Procedures) employed by attackers can also be valuable in threat modeling during the software development and design phase. In line with this objective, you can gain quick insights into attacker TTPs through SOCRadar’s Threat Actor Tracking.
By leveraging CTI insights, developers can proactively address potential security gaps during SDLC, ensuring the integrity of the codebase.
- Secret Removal:
The quest for secure coding also involves identifying and removing hardcoded secrets. Through continuous monitoring, developers can protect these secrets within the source code in case they are inadvertently left and exposed to the public, thus preventing potential cyberattacks in the future.
SOCRadar’s source code leakage monitoring feature continuously monitors public code repositories such as GitHub and GitLab to detect potentially exposed data, source code, login credentials, API and cryptographic keys, or database instances and can alert organizations on such incidents to keep their SDLC secure.
SOCRadar’s Source Code Leakage Monitoring
SOCRadar detects exposed private keys, authentication credentials, API keys, and other sensitive data in real-time using advanced algorithms and machine learning techniques. SOCRadar alerts enable organizations to respond quickly to potential risks, take necessary mitigation steps, and prevent malicious actors from exploiting vulnerabilities.
Receive alarms about code repositories on SOCRadar
- Dynamic Application Scanning:
During Dynamic Application Scanning, CTI integration can provide real-time threat monitoring. By incorporating CTI feeds, development teams can stay informed about emerging threats, enabling them to safeguard the application against potential exploits before deployment.
- Verifying Components:
CTI aids in the SDLC by ensuring the absence of redundant or outdated components carrying known vulnerabilities. This proactive approach minimizes the risk associated with using deprecated or compromised software elements.
An effective tool for such purposes is OWASP’s Dependency-Check. Through Software Composition Analysis, OWASP’s Dependency-Check can improve security throughout the SDLC. This tool scans project dependencies for vulnerabilities and provides developers with information about potential risks associated with third-party libraries.
SOCRadar, with its effective solutions, can also assist you in ensuring the safety of your components. The Vulnerability Intelligence and Attack Surface Management modules keep you updated on potential threats to your organization’s assets. Concurrently, the Supply Chain Intelligence feature allows you to add vendors to a watchlist and stay informed about security breaches. These solutions empower you to safeguard your assets and maintain vigilance against third-party risks.
SOCRadar’s Supply Chain Intelligence
- Fail Pipeline on Critical Vulnerability:
Integrating the EPSS (Exploit Prediction Scoring System) API into the SDLC pipeline can help organizations in assessing vulnerability exploitabilities. By setting thresholds, the pipeline can be configured to fail when a critical vulnerability surpasses a specified level, preventing the deployment of insecure code into production.
To understand how EPSS works and how it can effectively aid in vulnerability assessment, you can visit our other blog post: Predicting Vulnerability Exploitation for Proactive Cybersecurity: What’s EPSS, and How Can SVRS Enhance It?
In addition to EPSS, the SOCRadar Vulnerability Risk Score (SVRS) serves as a valuable indicator of a vulnerability’s prominence in the cyber landscape. This score, ranging from 0 to 100, provides a nuanced perspective on a vulnerability’s likelihood of exploitation based on diverse sources such as social media, news, and the dark web, as it also considers connections to threat actors and malware.
Given the constraints organizations face in addressing the multitude of vulnerabilities each month, it becomes critical to focus on those most likely to be targeted. Surprisingly, only about 7% of identified vulnerabilities are subject to exploitation by threat actors. The SVRS score, complementing CVSS and EPSS, offers a contextual approach, aiding security teams in deciding which vulnerabilities need to be prioritized.
Conclusion
Integrating Cyber Threat Intelligence (CTI) into the Software Development Lifecycle (SDLC) proves transformative, fortifying cybersecurity from idea generation to maintenance. This integration introduces several key benefits.
Proactive Threat Mitigation stands out as a primary advantage, empowering organizations to identify and address vulnerabilities proactively throughout the SDLC. This approach ensures potential threats are mitigated before they materialize, enhancing the overall resilience of the software. Real-time Threat Monitoring is facilitated by CTI in dynamic application scanning and source code analysis. Developers gain timely insights into emerging threats, enabling informed decisions and swift fortification of the software against potential exploits.
Enhanced Collaboration and Communication emerge as crucial factors in the CTI-empowered SDLC. By fostering a culture of collaboration among development, security, and operations teams, CTI ensures that security considerations are seamlessly integrated across all SDLC phases. Automated Security Checks become integral to the SDLC pipeline with CTI. This automation minimizes the window of exposure to potential threats, aligning with the rapid and iterative nature of modern development practices. Compliance with security best practices and industry standards further enhances the resilience of software against diverse cyber threats.
In conclusion, the integration of CTI and SDLC not only safeguards software projects from potential exploits but also cultivates a proactive cybersecurity stance. Embracing CTI as a strategic partner empowers development teams to create resilient, secure, and agile software, marking a paradigm shift toward a future where security is ingrained in every line of code.


































