
Main Analytical Frameworks for Cyber Threat Intelligence
Threat intelligence is a cyber-security discipline focusing on detailed knowledge about the cyber threats targeting an organization. Threat Intelligence Platforms create intelligence information by gathering raw threat data and security-related information from multiple sources, both clear and dark web sources, then filtering, correlating, and analyzing the data to uncover trends, patterns, and relationships between the actual or potential cyber threats.
This intelligence lifecycle process requires a robust understanding of IT infrastructure, operations, and decision-making and action. To create this evidence-based knowledge, which proves valuable to cybersecurity defenders, information about mechanisms and indicators – often referred to as “threat feeds” must be detailed and contextualized by comparing and enhancing it with other security information. Threat intelligence is challenging because threats are constantly evolving and require businesses to adapt quickly and take decisive action.
The threat intelligence feeds are obtained using “security analytics” techniques, thereby increasing the chances of threat detection and providing unique security visibility. For these analytic processes to be carried out effectively and to enable security teams to optimize their resources and respond effectively to the modern threat landscape, there are several commonly used and fundamental frameworks. Let’s explore what these frameworks are and discuss their respective features and advantages.
What Are the Most Commonly Used Frameworks for Threat Intelligence?
Frameworks used for CTI offer a structured approach to thinking about threat actors and cyber-attacks. This information assists security defenders in making decisions, acting more swiftly, and protecting assets from the damaging impacts of cyber-attacks. Aspects such as TTPs (Tactics, Techniques, and Procedures) are used to examine cyber incidents from a broader perspective, as well as specific situations in the attack lifecycle.
These baseline frameworks can also help to focus on the details that are useful for further analysis and investigation. Moreover, through this process, a real threat can be fully removed or mitigated, and lessons learned can be applied to take appropriate measures against similar attacks in the future.
Sharing strategic, tactical, technical or operational intelligence information with other teams and organizations can also be beneficial. With a common language and structure, relationships can be established between attack details, making it easier to obtain intelligence from vendors, open sources, and authoritative organizations. Consequently, this can be seen as one of the achievements that bring standardization to the cybersecurity realm.
While these are not frameworks created specifically for threat intel, they are frequently used for CTI to provide businesses with the information they need to continuously improve their defense. Finally, it is important to view these primary frameworks as complementary rather than focusing on finding and selecting the best one. This approach allows for the potential to maximize the benefits from all of them, given the appropriate circumstances and context.
These useful frameworks provide us with a facilitating structure when thinking about threat actors and cyber-attacks. This information can help security defenders to make decisions and take action faster and protect assets from the damaging impact of cyber-attacks, such as TTPs used to look at cyber incidents from a broader perspective, or specific situations in the attack lifecycle.
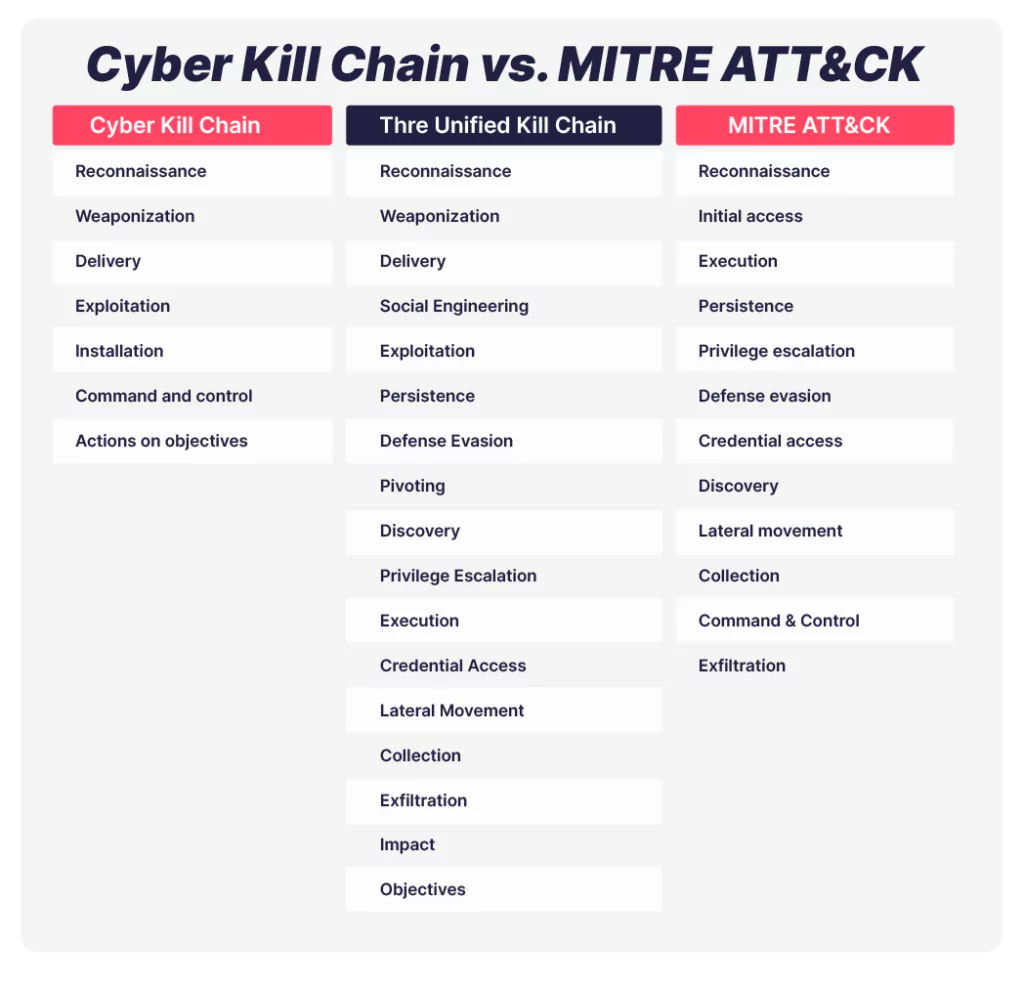
1- Cyber Kill Chain
The Cyber Kill Chain® was developed by Lockheed Martin, an American aerospace and security company, and is also referred to as the Cyber Attack Lifecycle. This framework, one of the earliest and best-known, takes a step-by-step approach to identify and interrupt adversarial activity. Drawing on a military concept, it breaks down cyberattacks into stages of the cyber kill chain with the aim of disrupting one kill chain step at a time. This allows cyber defenders to identify the current stage of an attack and deploy countermeasures accordingly.

The Cyber Kill Chain comprises seven steps that threat actors must complete for a successful attack. Organizations can integrate threat intelligence with the steps of the cyber kill chain to minimize the impact of a cyber-attack.
- Reconnaissance: This involves conducting research and investigation to understand which targets will allow the attackers to achieve their objectives.
- Weaponization: This stage involves preparing and staging the cyber operation.
- Delivery: The operation is launched by conveying malicious software to the target.
- Exploitation: At this stage, the attacker identifies known or unknown vulnerabilities that can be exploited to gain unauthorized access.
- Installation: The attacker creates a persistent entry into the victim’s environment to maintain ongoing operations.
- Command and Control (C2): The attacker opens a two-way communication channel to remotely manipulate the victim’s environment.
- Actions on Objectives: The attacker uses hands-on keyboard tactics to achieve goals, such as gathering credentials, escalating privileges, moving laterally through systems, and stealing data.
The Cyber Kill Chain Framework can be a highly useful tool for understanding how far a cyber incident has progressed. Considering the discovery or initial access phases, for instance, can provide clarity on the phase of attack and the specific actions taken. This makes it easier for Incident Response (IR) teams to respond effectively.
In the context of Cyber Threat Intelligence (CTI), the Cyber Kill Chain can help to understand how threat actors operate and how to develop countermeasures and defense strategies based on the stages of the attack lifecycle. You can collect useful OSINT information to discover what information is available about your organization and what information attackers can uncover during the Reconnaissance phase.
2- Unified Cyber Kill Chain
In 2017, Paul Pols introduced the Unified Cyber Kill Chain to augment and expand upon the Cyber Kill Chain. The Unified Kill Chain incorporates elements from both the Lockheed Martin-Cyber Kill Chain and the MITRE ATT&CK framework. It distills the attack process into three high-level steps:
- Initial Foothold
- Network Propagation
- Action on Objectives.
Such three steps make the attack process easier to understand, even for non-technical staff. Each of these tactics is then elaborated in detail with specific techniques.
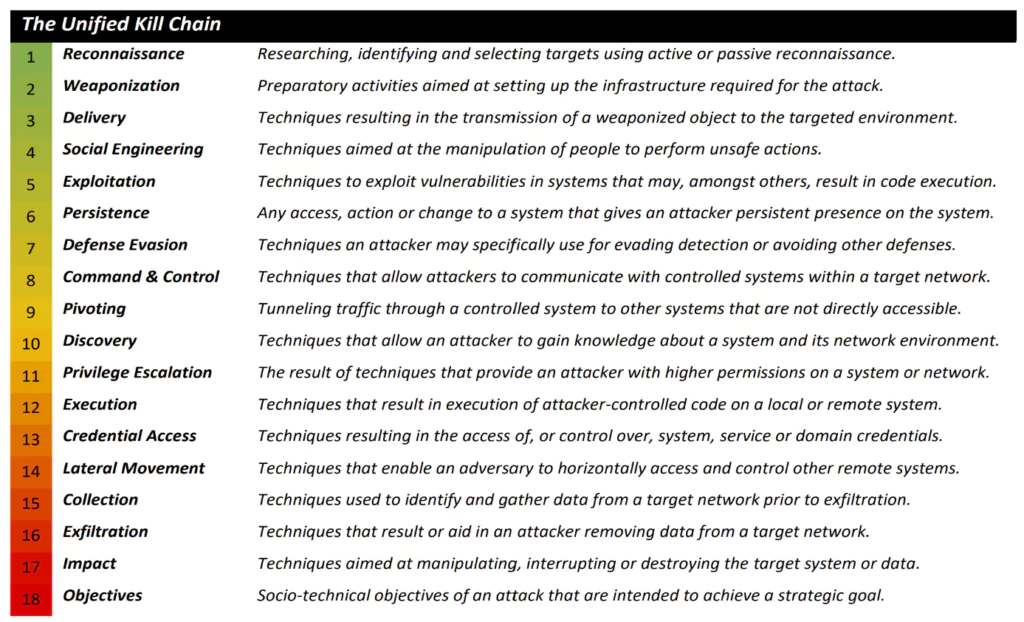
The Unified Kill Chain provides a robust foundation for strategically realigning defensive capabilities and cybersecurity investments within organizations, covering prevention, detection, response, and threat intelligence. It facilitates a structured analysis and comparison of threat intelligence concerning the tactical modus operandi of attackers.
For prevention, the Unified Kill Chain can be used to map countermeasures to the distinct phases of an attack. Detection can be prioritized based on insights into the ordered progression of the attack phases. In emergency response situations, the Unified Kill Chain aids investigators in triaging and modeling likely attack paths. This model is also particularly beneficial in enhancing the predictive intelligence of Red Team threat simulations, which are designed to harden an organization’s security posture.
3- The MITRE ATT&CK Framework
The MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK™) is a widely recognized framework that offers a comprehensive, systematic, and actionable way to understand attacker behaviors. It is accessible as an open-source tool and tracks the adversarial behaviors and TTPs (Tactics, Techniques, and Procedures) of threat actors. Due to substantial contributions from security analysts and researchers worldwide, the MITRE ATT&CK Framework has become a universal dictionary of TTPs.
ATT&CK uses 14 different tactic categories to describe adversarial behaviors:
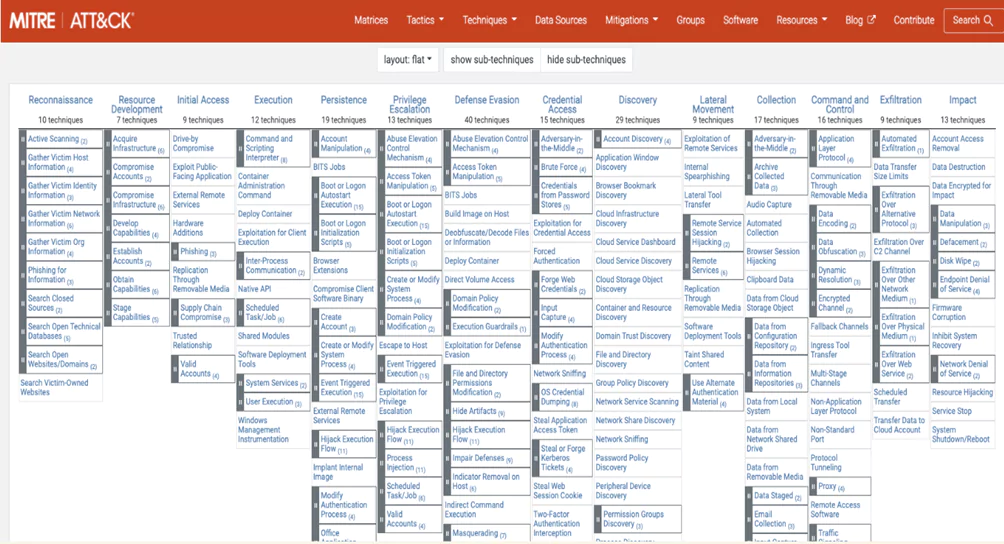
Each of these tactics comprises individual techniques and sub-techniques that further describe cyber-attack behaviors. This classification of adversarial behaviors allows security teams to obtain more granular information and structure to describe and track cyber attackers. Furthermore, it facilitates the sharing of actionable information among other teams and communities.
The ATT&CK™ framework is beneficial for a broad range of security functions, from security operations and threat analysis to digital forensics and incident response (DFIR). It empowers security teams to monitor adversarial behaviors more effectively in a structured and repeatable manner, assisting them in numerous areas:
- Prioritizing hunting, detection, and response based on observable real-world threat intelligence and threat behaviors.
- Mapping MITRE ATT&CK to malware families and techniques observed in their environment.
- Using standardized terminology with the ATT&CK matrix for clear communication.
- Utilizing the framework for linking adversary techniques to vulnerabilities for further threat analysis and adversarial TTP classification.
If the need arises to delve deeper into TTPs, which often forms a challenging level for cyber threat hunting in more complex cyber-attacks, and you wish to understand what adversary behaviors indicate and develop countermeasures, the MITRE ATT&CK framework can be utilized in conjunction with other frameworks.
When working with MITRE ATT&CK in the context of Cyber Threat Intelligence (CTI), CTI Analysts use this framework to map and classify observed threat actor behavior, identify gaps in their organization’s defenses, and enhance incident response and threat-hunting capabilities. It is a powerful tool to effectively understand and counter cyber threats.
The ATT&CK framework can also help an organization obtain actionable threat intelligence. Using the CTI provided under the framework, an organization can identify the behaviors, tools, techniques, and procedures of active threat groups and determine whether its current defenses have the capacity to detect and respond to attacks by these adversaries.
By leveraging various frameworks, SOCRadar Threat Actor Tracking provides intelligence information enriched with information from the MITRE ATT&CK database on current and future TTPs, which may be much more important than easily modifiable IOCs for dynamically understanding and tracking cyber attackers.
4- Diamond Model
The Diamond Model is a widely utilized threat modeling framework designed for intrusion analysis. This model comprises four (4) basic components and underscores the relationships between them: adversary, capability, infrastructure, and victim.
1- Adversary: An adversary is anyone aiming to compromise your systems or networks to progress towards their objectives. This could include an insider, a threat actor or group, or even an entire organization. To define adversaries more accurately, consider questions such as: Where are the attackers from? Who are they? Who is sponsoring them? Why are they attacking? What is their activity timeline and plan?
2- Capability: A capability refers to a tool or technique employed by an adversary in an event. The potential capabilities used by various attackers are vast, ranging from password guessing to installing backdoors for establishing remote command and control. To understand this aspect better, ask questions like: What skills do the attackers have to perform the cyber-attack?
3- Infrastructure: In this context, ‘infrastructure’ does not pertain to IT infrastructure, but instead to the communication structures that hackers use to deliver their capabilities. Examples include domain names, USB devices, compromised accounts, infected computers or servers, and data leakage paths.
4- Target (Victim): This element refers to the adversaries’ target, which could be a particular country or region, industry, individual, piece of software, or confidential/commercial data. The victim is not limited to a person or a company; it could be an asset such as an email address or a domain. By considering this broader range, it’s possible to conduct more granular analysis when defining victim personas (people, companies) and victim assets (the attack surface that includes all IT assets.)
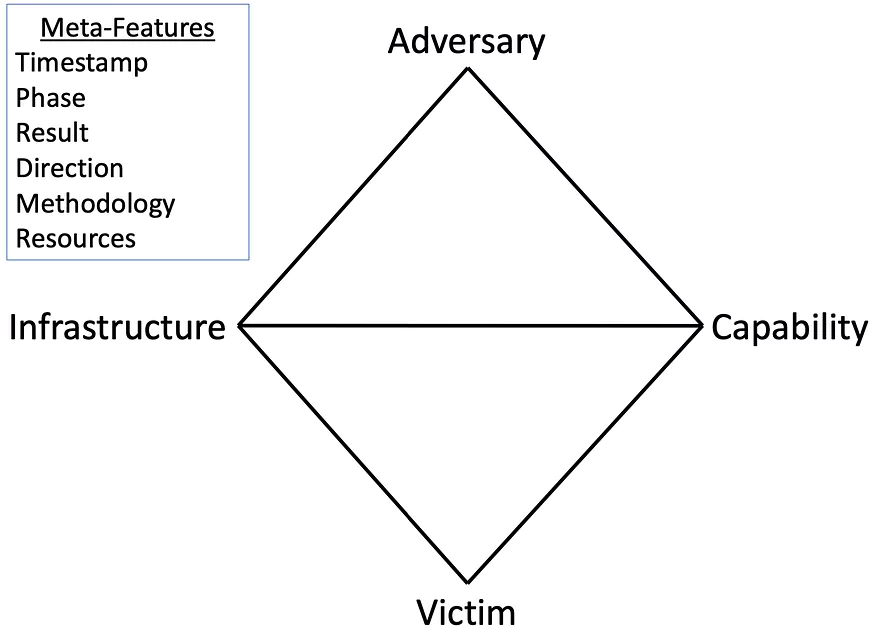
What Are the Meta-features of Diamond Model?
To delve deeper into cyber events within the Diamond Model, the meta-properties and their descriptions are listed below:
- Timestamp: The date and time when the intrusion event occurred.
- Phase: The specific event in the chain of events represented by this model.
- Result: The outcome of the intrusion (e.g., success, failure, or unknown; or whether confidentiality, integrity, or availability was compromised).
- Direction: The route of the event through the network or host (e.g., Victim-to-Infrastructure, Adversary-to-Infrastructure, Bidirectional).
- Methodology: The category of the event (e.g., spear phishing, port scan).
- Resources: Elements required for the intrusion (e.g., software, hardware, knowledge, funds, facilities, access).
- Social-political: The relationship between the adversary and victim, based on the victim’s needs and the actors’ demands.
- Technology: This encompasses the adversary’s capabilities and their use of cyberspace.
How to Use the Diamond Model for Threat Intelligence?
The Diamond Model is a beneficial tool for security analysts focused on threat intelligence when conducting intrusion analysis. This model enables CTI analysts to analyze vast amounts of intelligence data quickly and draw clear connections between various threat information. To achieve effective results, businesses must develop proactive measures against new and emerging cyber threats and better understand adversary intentions and strategies.
Moreover, the Diamond Model aids in identifying intelligence gaps and provides a foundation for developing cyber taxonomies, ontologies, threat intelligence exchange protocols, and knowledge management. While it is a highly effective tool for CTI analysts striving to stay ahead of an evolving threat landscape, it is crucial to acknowledge its limitations and insufficiencies, and to consider it in conjunction with other framework models.
The Diamond Model is a straightforward structure that explains the intrusion event in four parts. For instance, if we see an adversary using a particular malware family and a domain model today, and then we see this combination next week, the Diamond Model can help us quickly recognize their similarities.
5- VERIS Framework
In 2010, the Verizon Community developed a security data model known as the Vocabulary for Event Recording and Incident Sharing (VERIS) in JSON data format. It was primarily designed to represent CTI information such as incidents, victim demographics, impact assessment, discovery, and monitoring for collaboration. This concept was designed as “metrics” to articulate security information in a common and structured manner for information exchange. As a standard presentation, it allows the analysis of data from various cyber incidents and is used, among other uses, notably to generate the Verizon Data Breach Investigation Report (DBIR).
VERIS models assets and adversary behavior in a way similar to the ATT&CK framework. But, the VERIS Data Model is still under development. As it focuses on the incident and what led to it, it can only be used for strategic post-incident risk-based analysis rather than proactive analysis. On the other hand, the STIX 2.x Data Model also captures Indicators of Compromise (IoC), which enables the STIX Data Model to be more proactive and identify threats and assess their impact in advance.
VERIS is a risk-based model with a narrow scope, capturing cybersecurity incidents in a structured way for information exchange. However, VERIS offers a rich and comprehensive Event concept that covers all aspects of security events. The STIX Data Model adopted this Event concept from VERIS for its own purposes. A significant drawback of the VERIS Data Model is its inability to represent the relationships between its different concepts.
VERIS uses the “A4” threat model for the information gathering process, aiming to understand the specific characteristics that can be identified. These are described as follows:
Actors: Which threat actor or criminal group do the available indicators and signs point to?
Has this group or actor been previously identified by the authorities?
Actions: What type of actions affected the asset? This determines the impact of specific actions detected by the performance state of the asset.
Assets: Which assets were directly harmed? This serves to manage the extent of damage the assets actually receive.
Attributes: What characteristics affect the assets? This section defines the characteristics of the security incidents that negatively impact the assets.
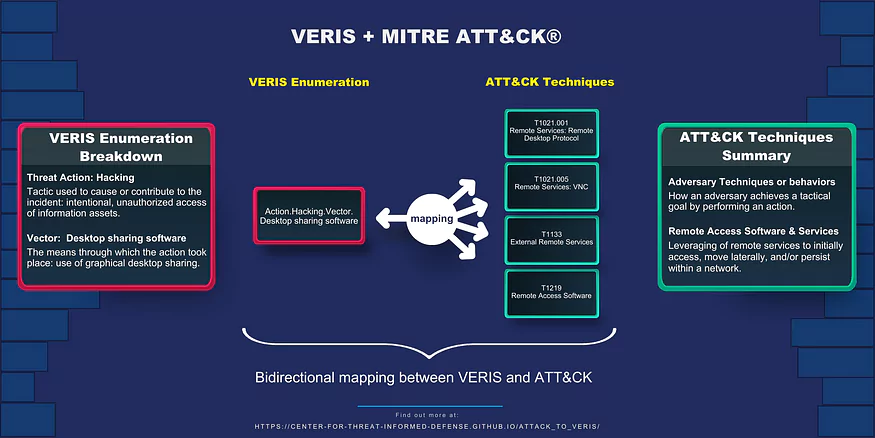
The example above demonstrates the bidirectional mapping of VERIS to a more granular set of ATT&CK techniques. This detailed depiction of an adversary’s behavior allows users to better understand how to detect and mitigate the advanced threats.
Moreover, expanded mapping and usage documentation have been developed to further show how the translation can be used to describe and communicate information about security incidents. Updated use cases and new scenario examples are provided to illustrate ways for defenders to effectively link adversary TTPs and their real-world impact by connecting ATT&CK-based threat intelligence with VERIS-based incident reports and vice versa.
Defenders carrying out essential capabilities can utilize the VERIS/ATT&CK mapping for various use cases. The Center for Threat-Informed Defense (CTID) welcomes feedback and contributions to further enhance the integration of ATT&CK with VERIS.
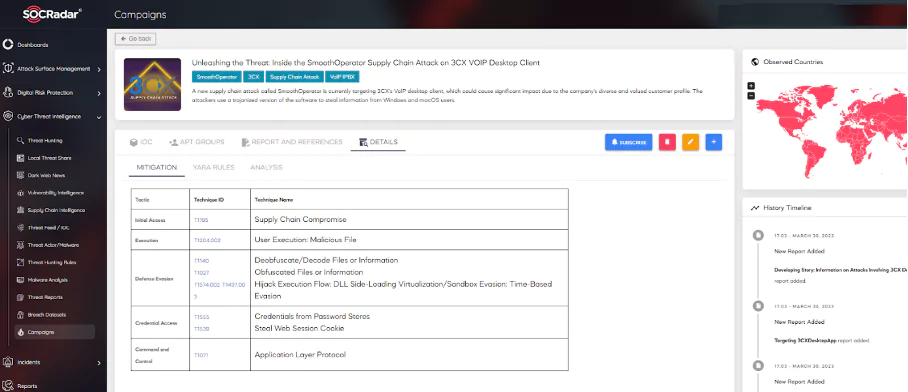
The SOCRadar Campaign page, along with other frameworks, is designed in line with the motivation of the MITRE Campaign. This page, which is enriched and constantly updated with dark web intelligence information on the latest malicious campaigns, includes a group of unauthorized intrusion activities carried out over a certain period with common goals and objectives. You can track such real-world threat risks spreading all over cyberspace on the SOCRadar Campaign page and support your security posture by gaining targeted insights.
Conclusion
These analytical frameworks commonly used in Cyber Threat Intelligence offer a standardized method for your security teams to track threats, Indicators of Compromise (IoCs), vulnerabilities, and threat actors. Understanding these frameworks and following their guidelines requires a certain level of expertise, so one of the quickest routes to proficiency might be to engage the services of security companies that specialize in this field. These frameworks are not plug-and-play solutions but models you can employ to make your security operations more efficient.
Each security incident can have its unique dynamics, and sometimes actionable and reliable intelligence information can save you time and protect you from a major data breach. Consequently, while a detailed deep-dive might be necessary for some types of cyber incidents, in other situations, it is more important to understand the stage at which the cyber attackers are. For instance, if you know a vulnerability is being exploited and you have software that is susceptible to such exploitation, the precautions you take during the period when you cannot update will be different.
For another example, if you receive intelligence indicating that there is a zero-day vulnerability sale involving a particular software product, you will need to scrutinize your anomaly detection mechanisms more closely.
Therefore, it is beneficial to follow playbooks containing specific scenarios beyond standard and routine ones, informed by threat intelligence information generated with these CTI frameworks.


































