
Essential CTI Capabilities for Effective SOC Operations
In the dynamically evolving threat landscape of the digital age, organizations must thwart sophisticated cyber threats that jeopardize their operations, sensitive personal and commercial data, and reputations. To shield organizations from such threats, Security Operations Centers (SOC) are deployed, encompassing human, process, and technology components. SOC teams actively, proactively, and predictively monitor, investigate, prevent, and detect potential cyber threats and attacks and respond swiftly to cyber incidents.
Staying a step ahead of adversaries, particularly threat actors, necessitates a continual refinement and enhancement of the SOC infrastructure. Cyber Threat Intelligence (CTI), furnishing indispensable insights into emerging threats and adversary strategies, serves as a vital asset in this conflict, significantly bolstering SOCs’ proactive defenses against cyber-attacks. This article delves into the significance of CTI for SOC teams and explores the critical CTI capabilities that are available and beneficial for SOC operations.
Why is CTI Pivotal for SOC Operations?
CTI can augment security functions for organizations of all sizes. SOC teams grapple with a growing workload of security incidents and alerts to investigate and review, which can lead to burnout. CTI can assist in discerning which alerts to prioritize, helping to eliminate less critical ones. Additionally, managing vulnerabilities can be a challenging yet crucial task. Contextual intelligence data can facilitate timely action against the most critical vulnerabilities. Moreover, by harnessing reliable and actionable cyber threat intelligence that delineates specific tactics, techniques, and procedures (TTPs) for crucial security processes like threat hunting and incident response, CTI can aid in intelligently and proactively thwarting threats and even fortifying defenses against future threats.
The synergy between CTI and SOC epitomizes a vital alliance, with CTI analysts increasingly being integrated within SOC teams. The emerging trend illustrates that the interaction between these two domains is evolving into a potent solution in the realm of IT security.
What are the Prominent CTI Capabilities for SOC Teams?
The intelligence yielded by threat intelligence significantly enriches the operations and processes of SOC teams. To optimally manage and comprehend the information accrued from diverse sources, it’s imperative to categorize the intelligence. Threat intelligence is segmented into four categories based on the nature of the information: Strategic, Tactical, Operational, and Technical.
These four variants of intelligence encompass a wide array CTI capabilities and can offer different advantages to SOC teams. While all this intelligence is pivotal for safeguarding a company’s IT environment, security teams often find it challenging to collect and utilize this intelligence. Employing assistant platforms can ameliorate these challenges.
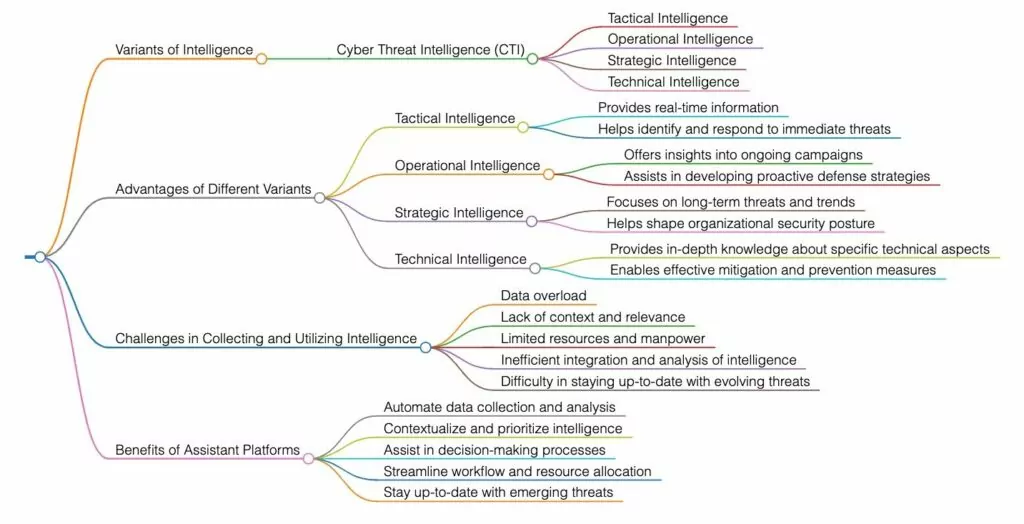
Cyber Threat Intelligence (CTI) is a critical element of robust cybersecurity, particularly within a Security Operations Center (SOC). SOCs depend on CTI to comprehend the threat landscape, allocate resources effectively, and respond to security incidents efficiently. Let’s examine the key capabilities that different types of intelligence information offer to SOC teams.
- Identification of Threat Indicators and TTPs
Identifying Indicators of Compromise (IoCs) and Tactics, Techniques, and Procedures (TTPs) is crucial to better understand and categorize threats. It is challenging to keep up with these indicators in a threat landscape where cyber-attacks are prevalent. By leveraging frameworks such as MITRE ATT&CK to contextualize and understand the behavior and actions of threat actors, CTI can illuminate threats and enable SOC teams to act rapidly.
- Vulnerability Intelligence
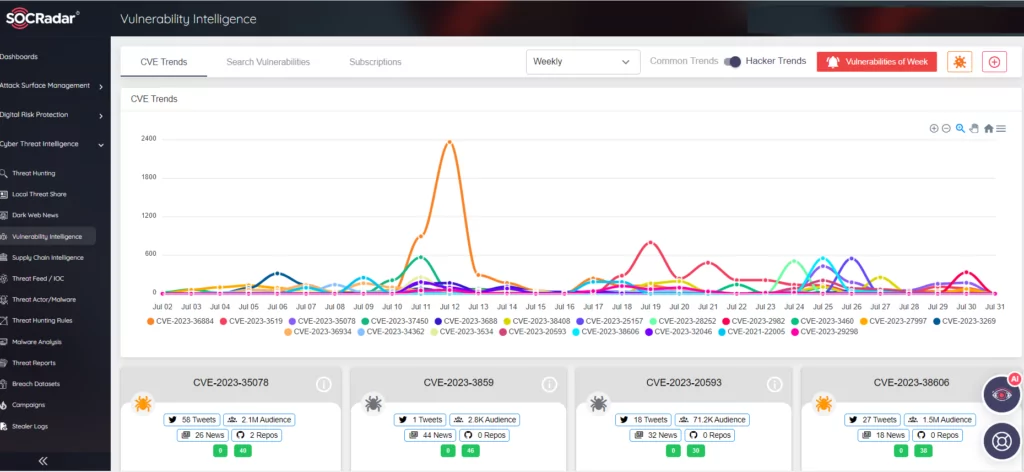
CTI provides information about newly discovered vulnerabilities and exploits, especially zero-day vulnerabilities. Armed with this knowledge, SOC teams can prioritize patching – or mitigation if patching is not available – to reduce potential risks in a timely and effective manner.
This proactive approach minimizes the opportunity for threat actors, especially ransomware groups, to exploit known vulnerabilities.
The SOCRadar Vulnerability Intelligence module can provide insights into which vulnerabilities are being exploited by threat actors, thereby accelerating risk assessment and information validation processes.
- Strategic Decision-making:
Security leaders can make informed decisions regarding resource allocation, security technology investments, and overall security strategy by analyzing long-term CTI trends and threat actor behaviors. This intelligence-driven approach ensures that security efforts are focused on the most relevant and necessary areas. You can read SOCRadar blog post on how CISOs can benefit from this information, which falls more within the scope of strategic intelligence.
Chief Information Security Officers (CISOs) have a critical and challenging role in today’s rapidly evolving cybersecurity landscape. They are tasked with complex cyber attacks, insider threats, compliance and regulatory requirements, third-party and supply chain risks and threats, cyber awareness training, emerging technologies, and budget and resource constraints. You can follow the SOCRadar CISO interview series for rich insights into threat intelligence, strategic decisions, and investments in Cyber Security.
- Advancement in Threat Hunting
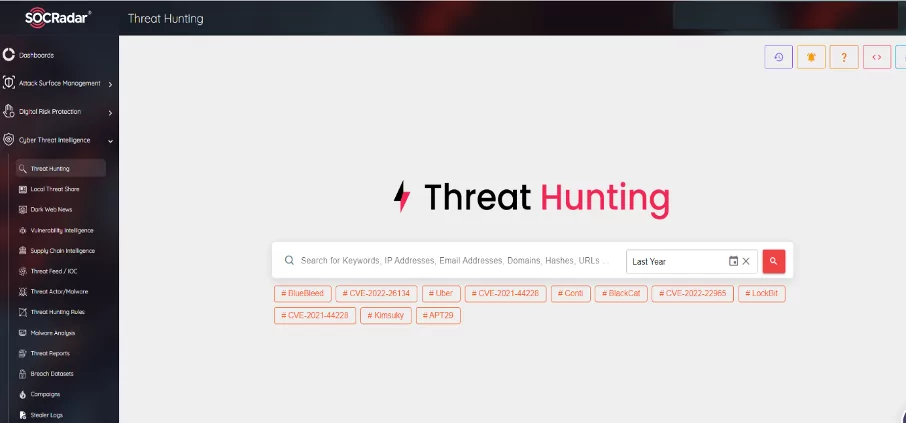
SOC teams can perform alarm prioritization that reduces human labor by matching alarms and events with threat intelligence obtained through SIEM logs, log management, and security analytics tools via CTI platforms to investigate threats that may have bypassed traditional security controls. By leveraging threat intelligence to identify signs of Advanced Persistent Threats (APTs) or new attack vectors, analysts can conduct targeted threat-hunting exercises to uncover potential threats on the organization’s network.
The SOCRadar Threat Hunting module provides a rich repository of TTP and IoA/IoC for proactive investigation by providing threat intelligence information collected, analyzed and filtered from the vast number of open and dark web sources available to SOC teams.
- Integration with Threat Intelligence Platforms (TIPs):
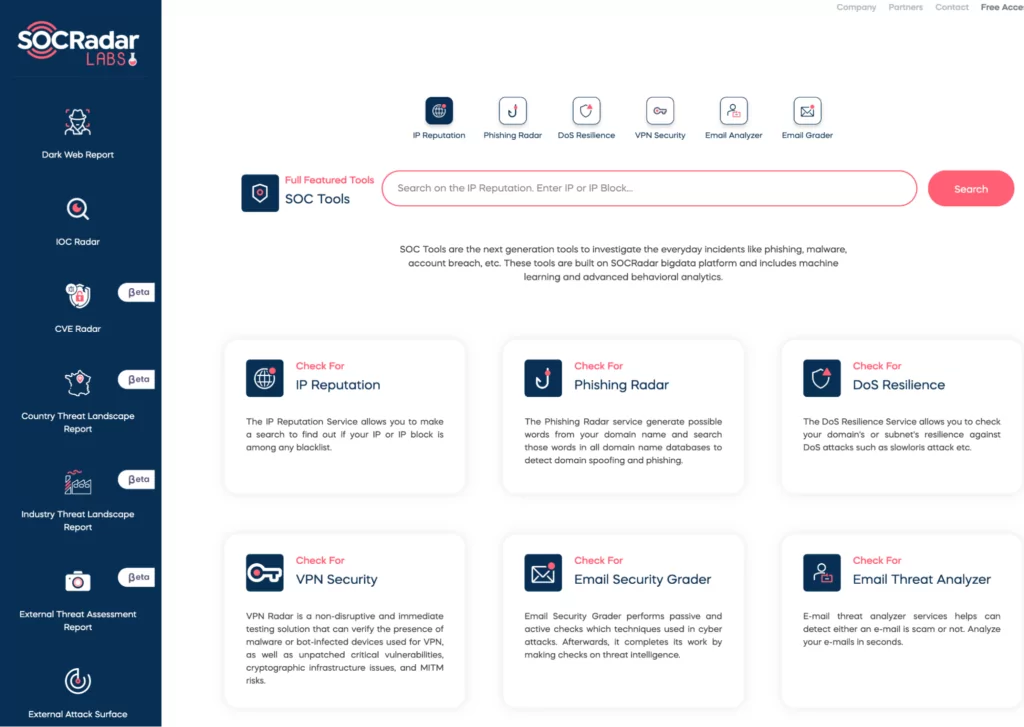
Utilizing platforms that undertake the labor-intensive work of collecting, correlating, and analyzing threat data from multiple sources can provide crucial insights for businesses. These platforms offer a centralized location to store and manage threat intelligence information. Various CTI tools, some of which are available free of charge, can be instrumental at different stages of the SOC process, facilitating the work of SOC teams. Featured tools and resources, most of which are free of charge, can be reviewed in this SOCRadar blog post.
- Contextualizing Alerts and Incidents
CTI can enrich security alerts and events with additional context, transforming a generic alert into a well-informed analysis based on data from multiple and diverse threat data feeds and sources. This context helps prioritize incidents, understand the potential impact, and translate appropriate responses into action, enhancing decision-making and future defense mechanisms.
In addition, SOC teams can understand the adversary’s tactics, techniques and procedures (TTPs) used in the attack, the targeted country, region and industry, and the relevant threat actors. This context helps to prioritize incidents, understand the potential impact and translate the appropriate response into action.
SOCRadar’s new standalone CTI solution CTI4SOC is a next generation threat intelligence platform designed to facilitate the work of SOC teams. With its 12 functional modules, it acts as a unique assistant to SOC teams.
Unlike traditional threat intelligence platforms, CTI4SOC draws its power from big data and provides all the data analysts need in an organized and contextualized way that can be obtained using various tools.
- Information Sharing and Collaboration
Sharing threat intelligence with trusted communities, industry groups, and government organizations, as well as participating in threat intelligence sharing platforms and forums, yields multiple benefits. Collaboration and the sharing of Cyber Threat Intelligence (CTI) with other organizations and sectors can enhance situational awareness, improve detection and response capabilities, and reduce costs and resource utilization.
Different models of CTI sharing exist depending on the type, level, and scope of information, as well as the trust and relationship between participants. These models include bilateral exchanges between two organizations with a common interest in the same threat or incident, multilateral exchanges between multiple organizations within the same sector or region, and cross-sectoral exchanges between organizations from different sectors or regions with overlapping or complementary interests.
Conclusion
In practice, CTI’s out-of-the-box capabilities prove most useful for operations teams monitoring events within the environment, actively searching for threats, and responding to incidents. CTI data, encompassing detailed information on malware, vulnerabilities targeted by attackers, and specific indicators, can be leveraged by teams in threat hunting and response activities to craft specific solutions across the broad threat landscape.
When applied effectively, these capabilities can significantly enhance the ability of SOC teams to detect, respond to, and mitigate cybersecurity threats in an informed and timely manner.
The increasing significance of CTI lies in the rapid detection and response, management, and, where possible, prevention of discovered vulnerabilities. This underscores the importance of continuous integration and interoperability within CTI platforms.
CTI is also becoming more common and useful for SOC teams. The trends show that CTI is delivering value now and will likely continue to deliver value in the future.



































