
ISO 27002 and Threat Intelligence: The New Security Standard
ISO 27000 series and their importance
ISO 27000 series consist of the standards determined by the International Organization for Standardization (ISO). It offers the best approaches for information security management systems (ISMS), focusing on controlling cyber risks via information security control tools.
Since the ISO 27000 set of standards covers various topics and applies to businesses of all sizes and industries, organizations take advantage of this series. Organizations can also use these standards to control their security properties.
Various standards have their theme in ISO 27000 series. ISO 27001 is one of the standards that this series provides. The organizations can be certified for ISO27001, which offers criteria and principles for developing information security management systems (ISMS).
Another standard of the ISO 27000 series is ISO 27002. ISO 27001 and ISO 27002 are mainly linked to each other. ISO 27002 is critical since it describes how the needed procedures are determined by ISO 27001, which means that all changes of ISO 27002 also affect ISO 27001. ISO 27002 is a lot more thorough than ISO 27001, and it specifies how corporations must apply ISO 27001’s control standards.
New standards are needed and produced since the technology advances to satisfy the new demands of information security in various businesses and situations. That’s why threat intelligence was included in ISO 27002 recently. This inclusion is a widely praised information security standard issued in March 2022.
What Will Change in ISO 27002?
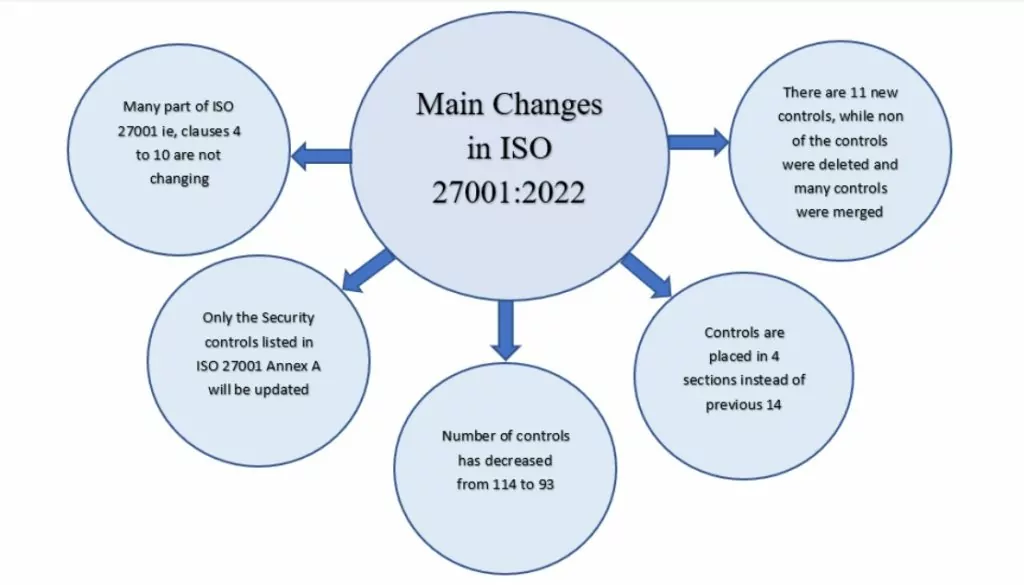
The main part of ISO 27001, i.e., clauses 4 to 10, will not change. These clauses include the scope, interested parties, context, information security policy, risk management, resources, training & awareness, communication, document control, monitoring and measurement, internal audit, management review, and corrective actions.
Only the security controls listed in ISO 27001 Annex A and ISO 27002 will be updated.
Number of controls
In general, changes are only moderate and were made primarily to simplify the implementation: the number of controls has decreased from 114 to 93 and placed in 4 sections instead of the previous 14. There are 11 new controls, while none of the controls were deleted, and many were merged. Technological advancements, and an improvement to the understanding of how to apply security practices, seem to be the reasons for the change in several controls.
ISO 27002:2022 will list 93 controls instead of the 114 controls of ISO 27002:2013.
These controls are grouped into 4 ‘themes’ rather than 14 clauses. They are:
-People (8 controls)
-Organizational (37 controls)
-Technological (34 controls)
-Physical (14 controls)
ISO 27002:2022 will include some new controls:
- 5.7 Threat intelligence
- 5.23 Information security for use of cloud services
- 5.30 ICT readiness for business continuity
- 7.4 Physical security monitoring
- 8.9 Configuration management
- 8.10 Information deletion
- 8.11 Data masking
- 8.12 Data leakage prevention
- 8.16 Monitoring activities
- 8.23 Web filtering
- 8.28 Secure coding
The controls now also have 5 types of ‘attributes’ to make them easier to categorize:
- Control type (preventive, detective, corrective)
- Information security properties (confidentiality, integrity, availability)
- Cybersecurity concepts (identify, protect, detect, respond, recover)
- Operational capabilities (governance, asset management, etc.)
- Security domains (governance and ecosystem, protection, defense, resilience)
These attributes will ease the integration of ISO 27002:2022 controls with other similar security frameworks, like NIST Risk Management Framework.
Renamed controls
23 controls have had their names changed for the sake of making them easier to understand. For example:
- Control 12.7.1 Information systems audit controls were changed to 8.34 Protection of information systems during audit testing.
- Control 15.1.3 Information and communication technology supply chain was changed to 5.21 Managing information security in the ICT supply chain.
These changes help keep the focus on the information security aspects of business processes and activities, reducing the effort for implementing and maintaining the Information Security Management System.
Merged controls
57 controls have been merged into 24 controls. For example:
- Controls 5.1.1 Policies for information security and 5.1.2 Review of the policies for information security were merged into 5.1 Policies for information security.
- Controls 11.1.2 Physical entry controls and 11.1.6 Delivery and loading areas were merged into 7.2 Physical entry.
Split controls
Only one control was split: 18.2.3 Technical compliance review was divided into 5.36 Conformance with policies, rules, and standards for information security and 8.8 Management of technical vulnerabilities.
Involvement of CTI into ISO standards
The importance of Cyber Threat Intelligence (CTI) is increasing every single day with the effects of globalization and technology. In this matter, ISO introduced an updated version of the ISO 27000 series.
The new version, which is named ISO 27002, is different from the previous ones with 11 new features. One of the most crucial parts is that ISO27002 gives information about implementing those standards. Also, it includes threat intelligence which enables companies to collect and analyze data. CTI in ISO standards aims to protect themselves beforehand by increasing awareness of the threats inside or outside of the organization. In other words, it is closely related to the IT security standards, which empower organizations to manage any secret information like financial documents or employee specifics.
Why is the involvement important?
Cyber Threat Intelligence (CTI) involvement enables organizations to take measures even before the attack occurs. Especially after the pandemic, organizations’ vulnerabilities have dramatically increased regarding changing work environments. Attackers took advantage of every gap in the system, and they did it fast. Thanks to CTI, establishing a well-optimized Information Security Management System (ISMS) is facilitated since it helps organizations obtain high-value information before the attack and act as fast as the attackers.
Having CTI helps prevent potential attacks and allows organizations to observe and shape according to ongoing and future threats. Therefore, the landscape of the threats, method of attacks, details, and type of technologies of the attacks can be observed and even may affect the budget or planning in the organization’s future investments.
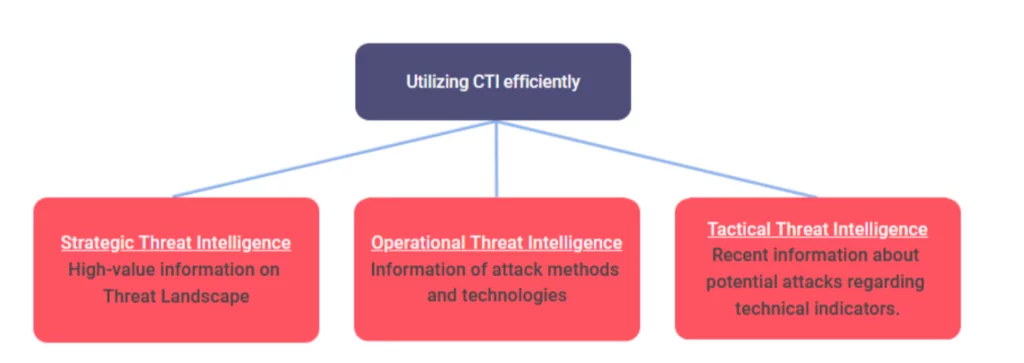
To utilize CTI with maximum efficiency, as exemplified above, ISO states three steps of intelligence required to be considered.
Utilizing all this information helps organizations build up their security and provide decision-makers with relevant data about their future steps.
Strategic:
- Create a decision advantage by understanding the overall cyber and physical threat landscape, the convergence of cyber and physical threats, threats and trends affecting your industry and peers, and relevant threats to your specific organization
- Ability to make informed security architecture and budget decisions based on strategic priorities informed by intelligence
- Creation and tracking of Priority Intelligence Requirements (PIRs) aligned to the organization’s security strategy and goals.
- Finished intelligence and ad-hoc tailored reporting to help decision-makers understand and prioritize risks and make better, more informed decisions.
- Identification of emerging threats, TTPs, and threat groups of which the organization should be aware.
Operational:
- Validated technical intelligence to understand specific attacks and the relationships between threat actors, indicators, and TTPs.
- Mapping threat intelligence to common frameworks like MITRE ATT&CK to classify behaviors, assess security gaps, and share intelligence with the cybersecurity community.
- Comprehensive intelligence from diverse sources and languages to understand not just the technical details but all aspects of threats and emerging events.
Tactical:
- High fidelity Indicators of Compromise (IoCs) integrated directly into security tools to enable analysts across all teams to access contextual intelligence in their established workflows.
- Ability to proactively hunt for indicators in your network using detection rulesets from hunting packages on threat actors and malware
- Real-time insights into current and emerging threats to your and your peers
How will this affect organisations implementing ISO 27001?
Besides the changes made in Annex A, many of the ISO 27001 changes are expected to be improvements and clarifications. Until the new version of ISO 27001 is published, your SoA (Statement of Applicability) must still refer to ISO 27001:2013 Annex A.
When ISO 27002:2022 is published, it will have an appendix comparing its controls to the 2013 version of the Standard. This will make it easier to compare with existing Annex A, making it easier to apply the differences.
Updating your post-comparison controls will also update your risk assessment. You may also review your Statement of Applicability (SOA) based on the new risk assessment and controls. There is usually a two-year transition period for certified organizations to revise their management systems to fit a new standard version, so there will be some time to make the necessary changes.
References
- https://www.itgovernance.co.uk/iso27000-family
- https://quointelligence.eu/2021/07/factsheet-iso-27002-including-threat-intelligence/
- https://www.kolide.com/blog/everything-you-need-to-know-about-iso-27000-standards
- https://www.cybersecurityintelligence.com/blog/about-strategic-threat-intelligence-3232.html
- https://resources.sei.cmu.edu/asset_files/Collection/2019_300_001_546590.pdf
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access


































