
Latest DDoS Threats: Condi Botnet, ShellBot, and Tsunami Malware
Notable Distributed-Denial-of-Service (DDoS) incidents dominate the cyber threat landscape this week, now accompanied by the reappearance of specific DDoS malware and the emergence of a relatively fresh peril.
This blog explores the rising number of Condi malware samples targeting TP-Link routers, along with the recent discovery of Linux servers being compromised for the distribution of Tsunami and ShellBot.
Condi Malware Targets TP-Link Routers to Expand Its Botnet
Researchers have observed that Condi, a new distributed DDoS malware, exploits a security vulnerability in TP-Link routers to recruit devices into a powerful DDoS botnet.
The Condi malware targets TP-Link Archer AX21 (AX1800) Wi-Fi routers and attempts to spread using a critical command injection vulnerability, tracked as CVE-2023-1389 (CVSS score: 8.8), disclosed in March 2023.
Fortinet FortiGuard Labs has noticed a surge in Condi samples since late May 2023, implying that threat actors are actively working on expanding the botnet.
Who Is the Threat Actor Behind Condi Botnet?
Researchers discovered a Command and Control (C2) domain (admin[.]duc3k[.]com) that previously displayed the message “contact @zxcr9999 telegram,” leading them to the threat actor’s Telegram channel.
The threat actor zxcr9999 has been managing the Telegram channel “Condi Network” for advertising purposes since May 2022. They also profit from their botnet army by offering DDoS-as-a-Service and selling the malware’s source code.
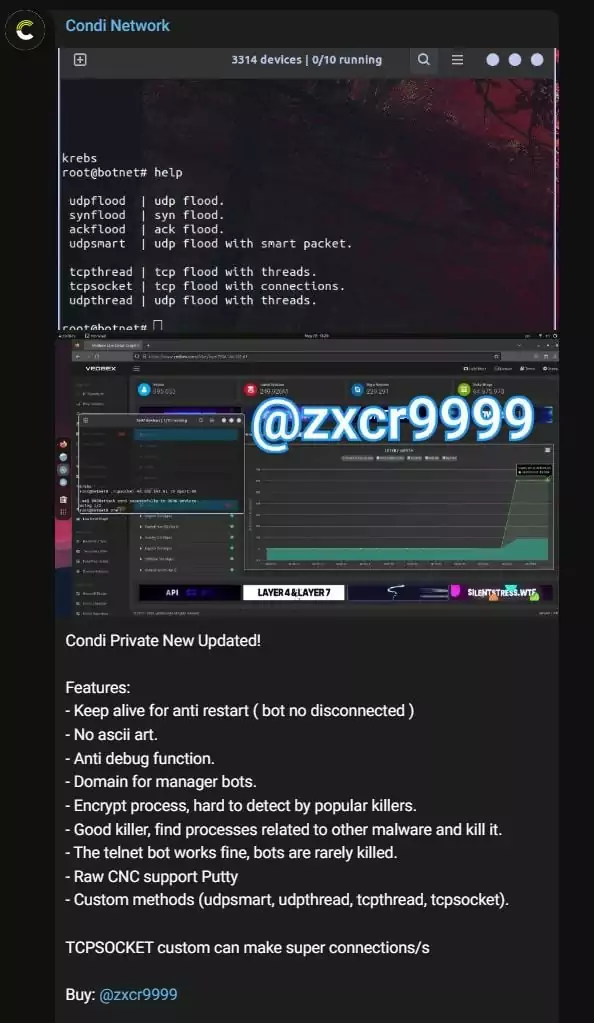
How Does the Condi Malware Infect Devices?
Fortinet researchers have conducted an analysis of the Condi malware and discovered that it targets specific processes and filenames to terminate them. Condi is unable to persist through a system reboot, a characteristic commonly observed in Mirai-based botnets, as highlighted by the researchers. Therefore, the malware takes this step to improve its survivability.
The malware can terminate other botnets on the same host and delete specific binaries responsible for system rebooting or shutdown. The Condi malware furthermore aims to kill older versions of it running on infected devices, but the implementation is flawed as it only considers the executable names and not their full paths.
Condi differs from other botnets that rely on brute-force attacks for distribution. It utilizes a scanner module, which targets the routers susceptible to CVE-2023-1389. The scanner searches for vulnerable TP-Link Archer AX21 devices and executes a shell script retrieved from a C2 server to deploy the malware upon discovery.
Fortinet has identified additional Condi samples that leverage different security vulnerabilities to distribute the malware, highlighting how unpatched software products will remain vulnerable.
See indicators of compromise related to Condi malware at the end of the blog. For more information, visit Fortinet’s blog.
Tsunami and ShellBot DDoS Malware Target Linux Devices for Cryptomining Operations
Researchers have discovered that attackers are breaching Linux servers to distribute DDoS bots Tsunami (aka Kaiten) and ShellBot, while also utilizing the servers for cryptocurrency mining operations.
According to researchers from AhnLabs, the source code of Tsunami is publicly accessible, and numerous threat actors use it in attacks against IoT devices and Linux servers, covertly exploiting their resources.
How Do Attackers Utilize Tsunami and ShellBot In Attacks?
The attackers start by compromising servers through a dictionary attack, enabling the execution of a malicious shell script. The shell script can download malware and establish persistent backdoor access by adding a public key to the “.ssh/authorized_keys” file.
The attackers scan external ports to locate exposed Linux SSH servers. With the aid of known account credentials, they conduct dictionary attacks to gain access to poorly managed servers and execute commands to install various malware. Among these malicious components is a downloader-type Bash script named the “key” file, responsible for installing additional malware, including the ShellBot malware, which presents itself as “bot” and “logo” in the command.
The specific malware employed in these attacks is a new variant of the Tsunami botnet called Ziggy. Ziggy bears notable similarities to the original source code and employs the Internet Relay Chat (IRC)protocol for C2 operations. This protocol facilitates real-time text messaging between internet-connected computers.
Once installed, the IRC bot on the compromised system connects to a designated channel controlled by the threat actor. It either transmits stolen information to the channel or awaits malicious commands.
Researchers have observed that the attackers install some additional malware, including Log Cleaner, a privilege escalation malware, and XMRig CoinMiner, to assist their malicious actions and also cover the tracks. For further information, see AhnSec’s analysis of the malware.
To prevent exploitation, researchers advise administrators to use stronger passwords and change them on a regular basis, and stay up to date with the latest patches.
How Can SOCRadar Help?
Stay one step ahead of malicious actors and protect your digital assets with SOCRadar. Our platform continuously tracks the behavior of threat actors and monitors the latest malware, providing you with real-time information and indicators of compromise. By staying informed about potential risks, you can take proactive measures to detect and eliminate threats before they can cause significant harm to your organization.
Enhance your organization’s defense against Denial-of-Service (DoS) threats with SOCRadar Labs’ DoS Resilience module. DoS Resilience allows you to test your domain’s or subnet’s ability to resist DoS attacks.
Indicators of Compromise (IoCs)
Condi Botnet IoCs
File SHA2-256 Hashes:
- 091d1aca4fcd399102610265a57f5a6016f06b1947f86382a2bf2a668912554f
- 291e6383284d38f958fb90d56780536b03bcc321f1177713d3834495f64a3144
- 449ad6e25b703b85fb0849a234cbb62770653e6518cf1584a94a52cca31b1190
- 4e3fa5fa2dcc6328c71fed84c9d18dfdbd34f8688c6bee1526fd22ee1d749e5a
- 509f5bb6bcc0f2da762847364f7c433d1179fb2b2f4828eefb30828c485a3084
- 593e75b5809591469dbf57a7f76f93cb256471d89267c3800f855cabefe49315
- 5e841db73f5faefe97e38c131433689cb2df6f024466081f26c07c4901fdf612
- cbff9c7b5eea051188cfd0c47bd7f5fe51983fba0b237f400522f22ab91d2772
- ccda8a68a412eb1bc468e82dda12eb9a7c9d186fabf0bbdc3f24cd0fb20458cc
- e7a4aae413d4742d9c0e25066997153b844789a1409fd0aecce8cc6868729a15
- f7fb5f3dc06aebcb56f7a9550b005c2c4fc6b2e2a50430d64389914f882d67cf
Download URLs:
- hxxp://85[.]217[.]144[.]35/arm
- hxxp://85[.]217[.]144[.]35/arm5
- hxxp://85[.]217[.]144[.]35/arm6
- hxxp://85[.]217[.]144[.]35/arm7
- hxxp://85[.]217[.]144[.]35/m68k
- hxxp://85[.]217[.]144[.]35/mips
- hxxp://85[.]217[.]144[.]35/mpsl
- hxxp://85[.]217[.]144[.]35/ppc
- hxxp://85[.]217[.]144[.]35/sh4
- hxxp://85[.]217[.]144[.]35/x86
- hxxp://85[.]217[.]144[.]35/x86_64
- hxxp://85[.]217[.]144[.]35/abc3.sh
- hxxp://cdn2[.]duc3k[.]com/t
Command and Control:
- 85[.]217[.]144[.]35
- cdn2[.]duc3k[.]com
Tsunami and ShellBot IoCs
MD5 Hashes:
- 6187ec1eee4b0fb381dd27f30dd352c9 (Downloader Bash script (key))
- 822b6f619e642cc76881ae90fb1f8e8e (Tsunami (a))
- c5142b41947f5d1853785020d9350de4 (ShellBot (bot))
- 2cd8157ba0171ca5d8b50499f4440d96 (ShellBot (logo))
- 32eb33cdfa763b012cd8bcad97d560f0 (MIG Logcleaner v2.0 (cls))
- 98b8cd5ccd6f7177007976aeb675ec38 (0x333shadow Log Cleaner (clean))
- e2f08f163d81f79c1f94bd34b22d3191 (Privilege Escalation Malware (ping6))
- 725ac5754b123923490c79191fdf4f76 (Bash launcher (go))
- ad04aab3e732ce5220db0b0fc9bc8a19 (Bash launcher (televizor))
- 421ffee8a223210b2c8f2384ee6a88b4 (Bash launcher (telecomanda))
- 0014403121eeaebaeede796e4b6e5dbe (XMRig CoinMiner (cnrig))
- 125951260a0cb473ce9b7acc406e83e1 (XMRig configuration file (config.json))
Download URLs:
- ddoser[.]org/key (Downloader Bash script)
- ddoser[.]org/a (Tsunami)
- ddoser[.]org/logo (ShellBot)
- ddoser[.]o]rg/siwen/bot (ShellBot DDoS Bot)
- ddoser[.]org/top (Compressed XMRig CoinMiner file)
- ddoser[.]org/siwen/cls (MIG Logcleaner v2.0)
- ddoser[.]org/siwen/clean (0x333shadow Log Cleaner)
- ddoser[.]org/siwen/ping6 (Privilege escalation malware)
Command and Control:
- ircx.us[.]to:20 (ShellBot)
- ircx.us[.]to:53 (Tsunami)
- ircx.us[.]to:6667 (ShellBot)
- ircxx.us[.]to:53 (Tsunami)



































