Recent DDoS Attacks: Microsoft Confirmed, Swiss & Malta Banks Hit, PowerOff Operation
This week, the cyber world is buzzing with news about DDoS attacks. Major tech company Microsoft has confirmed being targeted by Anonymous Sudan, while two European banks have also fallen victim to DDoS attacks. Additionally, the Polish police have successfully taken down a DDoS-for-Hire service that had been active since 2013.
This blog delves into the details and significance of these recent DDoS attacks.
Microsoft Confirms Anonymous Sudan DDoS Attacks Caused Service Outages
Microsoft has quietly confirmed that Anonymous Sudan, which they track as Storm-1359, conducted DDoS attacks that resulted in recent outages of its Outlook, OneDrive, and SharePoint online services.
Microsoft announced the attack in a blog post on June 16, 2023, revealing that the attackers most likely used virtual private servers, rented cloud infrastructure, and open proxies to carry out the Layer 7 DDoS attacks. The company assured customers that no customer data had been accessed or compromised.
Microsoft has observed that the Storm-1359 threat actor launched multiple types of layer 7 DDoS attack traffic: HTTP(S) flood attack, cache bypass, and Slowloris.
HTTP(S) flood attacks overload system resources by sending a massive number of requests, depleting CPU and memory. Cache bypass attacks overwhelm origin servers by bypassing the CDN (Content Delivery Network) layer and forcing requests to the origin. Slowloris attacks keep connections open and consume server resources by delaying or not acknowledging downloads.
A major company like Microsoft should have been prepared and should not have experienced any issues, as these attack types are common in DDoS attacks, and threat actors have been using them for a long time.
Security researcher Kevin Beaumont posted about the incident on Mastodon, the security community’s new Twitter, implying that Microsoft was relatively quiet while announcing the DDoS attack:
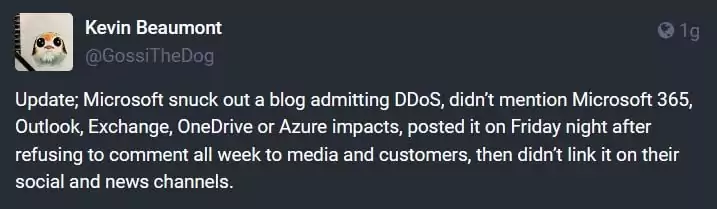
In response to the DDoS attack, Microsoft strengthened layer 7 defenses and optimized its Azure Web Application Firewall (WAF). The company has also included additional recommendations in the blog to provide further guidance to users seeking enhanced security against similar attacks.
THT Hackers Down the Swiss National Bank and the Central Bank of Malta
Turkish Hacker Group (THT) has been conducting a series of denial-of-service attacks against European financial organizations, and most recently, the Central Bank of Malta and Swiss National Bank fell victim to these attacks.
On June 18, 2023, the group issued a warning to the Swiss government on their Telegram channel.
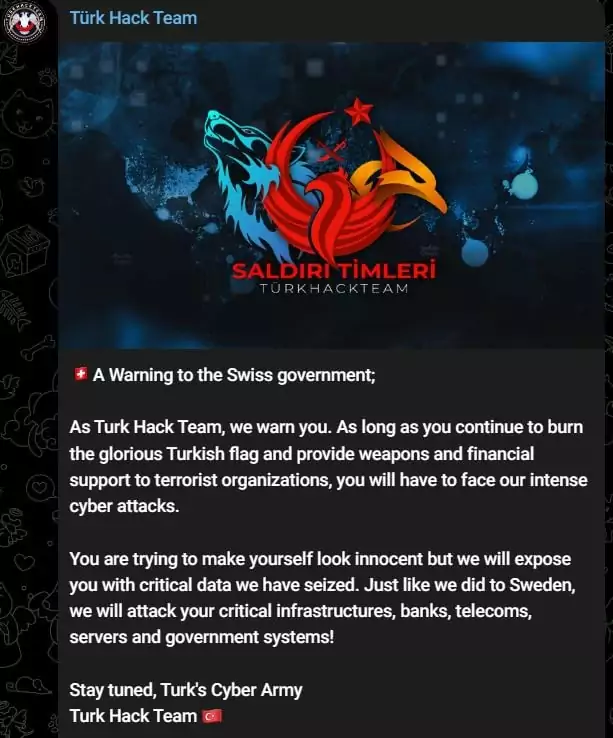
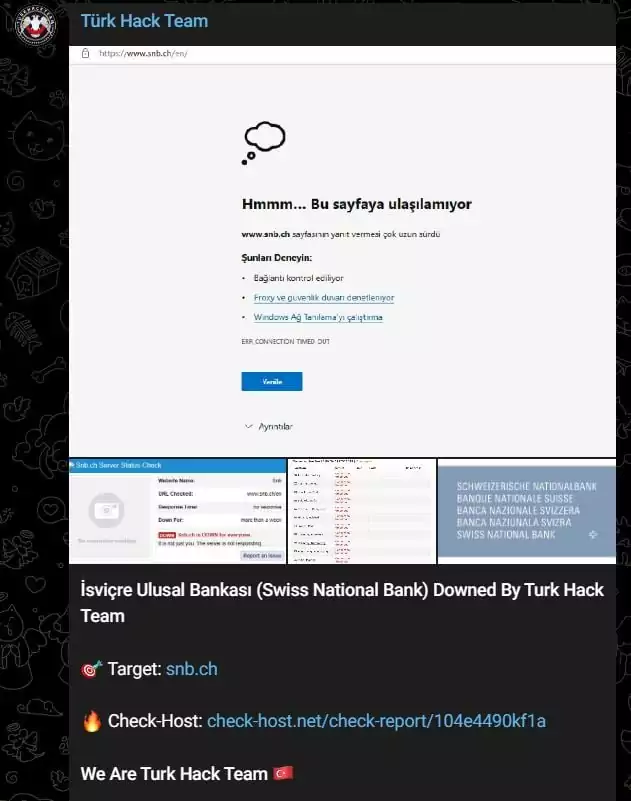
Shortly after, THT announced attacks on the Swiss National Bank and the Central Bank of Malta. They included reports in the posts showing the websites’ unavailability, proving the success of their DDoS attacks.

Operation PowerOff Dismantles a Long-Active DDoS-for-Hire Service
PowerOff, an international law enforcement operation, has successfully taken down a DDoS-for-Hire service that had been operating since at least 2013. The service enabled registered users to initiate DDoS attacks on demand, requiring no expertise.
The Polish Central Bureau for Combating Cybercrime, supported by Europol, the FBI, Joint Cybercrime Action Taskforce (J-CAT), and law enforcement agencies from the Netherlands, Germany, and Belgium, collectively conducted the operation PowerOff.
Polish police have arrested two individuals involved in operating the service. During the arrest, the police also confiscated electronic devices and gathered crucial evidence, such as login records and IP addresses connected to the service. Vx-underground has shared a video of the arrest on Twitter.
The investigation revealed that the service had over 35,000 registered user accounts, and customers had paid hundreds of thousands of dollars. Further analysis of the server unveiled 76,000 login records and more than 320,000 associated unique IP addresses.
According to a press release from the Polish police, they discovered 11,000 purchased attack plans, which included the buyers’ email addresses and amounted to $400,000.
Test Your Security Posture Against DoS Threats with SOCRadar
SOCRadar empowers you to enhance your threat investigation and analysis capabilities, strengthening your organization’s defenses against potential attack scenarios. The platform of SOCRadar proactively sends alerts about threats emerging from the dark web, specifically targeting your organization, while also delivering valuable insights into various threat actors and potential risks.
Furthermore, through SOCRadar Labs, you can assess and strengthen your DoS Resilience by testing your domain’s or subnet’s ability to withstand attacks like Slowloris and more.