Major Cyber Attacks Targeting Transportation & Logistics Industry
The global transportation and logistics industry is the backbone of modern commerce, enabling the smooth flow of goods and services across the globe. However, as the industry becomes more digitized, it has become an increasingly attractive target for cybercriminals. These attacks go beyond just disrupting transportation systems; they affect a wide range of operations, from warehouse management systems to public infrastructure like Wi-Fi services at major train stations.
In recent years, the sector has seen a sharp rise in cyberattacks, with incidents ranging from ransomware and data breaches to cyber vandalism. High-profile examples include disruptions to logistics hubs, delays in air transportation operations, and incidents of public Wi-Fi attacks, which can cause widespread public panic. Cybercriminals are increasingly targeting sensitive data, such as passenger information, shipment details, and personal records, putting both businesses and consumers at risk.
This article focuses on major cyber attacks that have impacted the transportation and logistics industry, shedding light on the evolving tactics of cybercriminals and the serious risks they pose to operations and data security.
Cyber Threats Targeting the Transportation and Logistics Industry: Key Insights
The global transportation and logistics industry, a crucial backbone of international trade and commerce, is facing increasingly sophisticated cyber threats. In SOCRadar’s Global Logistics & Transportation Industry Threat Landscape Report, we see that cybercriminals are honing in on this sector due to the immense value of the data it holds and the disruption that a successful attack can cause.
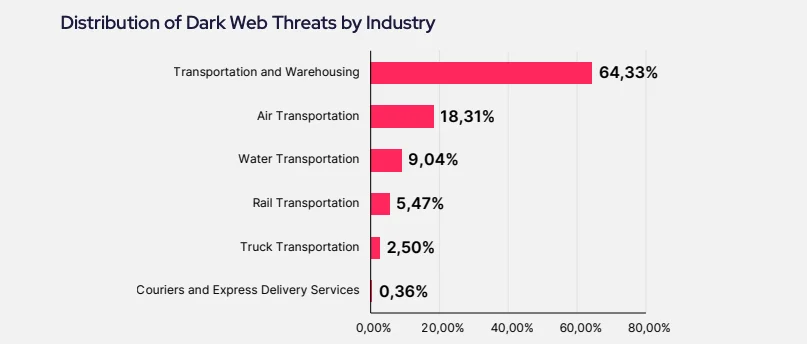
One of the most striking findings in the report is that the Transportation and Warehousing sector bears the brunt of these cyberattacks, with a staggering 64.33% of threats aimed at disrupting supply chains. Cybercriminals are targeting third-party logistics providers and warehouse management systems, hoping to exploit vulnerabilities to cause chaos in the supply process. The nature of these attacks means that even a small breach can ripple through entire industries, resulting in massive operational disruptions.
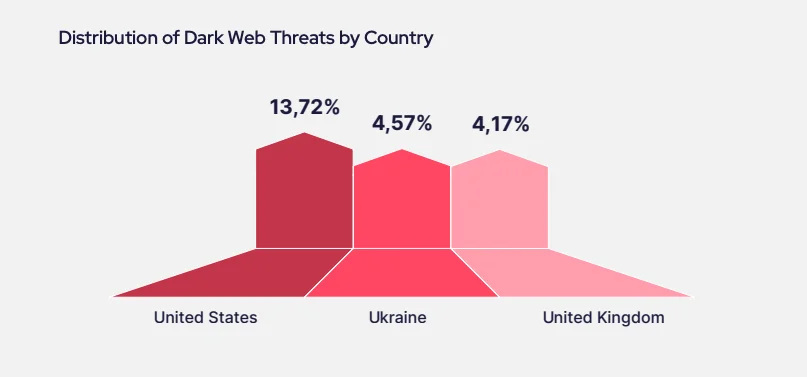
Looking at the geographical distribution, it’s clear that the United States (13.72%) is the most targeted country. Its vast and complex logistics infrastructure makes it a prime target for cybercriminals. Additionally, Ukraine (4.57%) stands out, likely due to the geopolitical tensions in the region, which have made it a hotspot for cyber warfare. This paints a picture of a world where regional collaborations and intelligence sharing are essential to fend off rising cyber threats.
Delving into the specifics of how cybercriminals operate, the Global Logistics & Transportation Industry Threat Landscape Report reveals some telling patterns in dark web activity. Hack Announcements (44.47%) are the most common type of threat, showing that cybercriminals aren’t just interested in stealing data—they want to publicize their breaches to create fear, intimidate victims, or boost their reputation. Following this, Selling (28.54%) and Sharing (26.04%) highlight the financial nature of these crimes. Cybercriminals profit by selling or distributing stolen data, putting organizations at risk of credential stuffing, fraud, and supply chain disruptions.
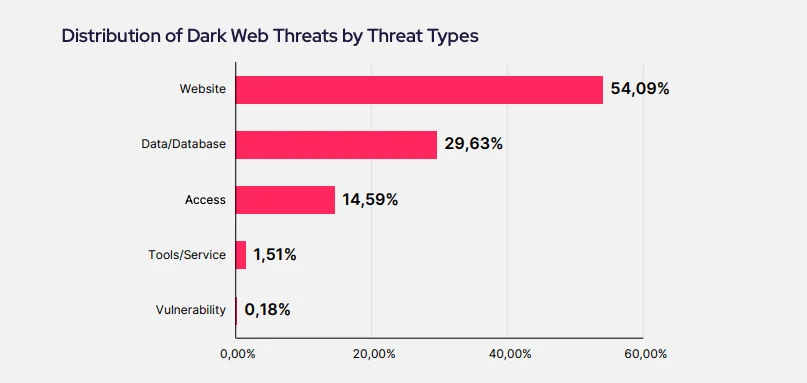
The types of data most at risk are website-related threats (54.09%), where hackers target logistics sites for phishing or credential leaks. Data and database theft (29.63%) is another prevalent threat, with cybercriminals stealing sensitive records such as customer information and shipment details. Access threats (14.59%) round out the list, indicating that compromised credentials and unauthorized entry points are hot commodities on the dark web.
SOCRadar’s Global Logistics & Transportation Industry Threat Landscape Report makes one thing clear: the transportation and logistics sector is under constant siege by cybercriminals, and the consequences of these attacks can be catastrophic. The data shows the urgent need for companies to strengthen their cybersecurity measures, particularly in areas with high exposure such as warehousing and large-scale transport operations.
Notable Cybersecurity Incidents in the Transportation and Logistics Sector
After examining the key statistics related to cyber threats in the transportation and logistics industry, it’s clear that the sector faces significant risks, particularly in the realm of dark web activity. These threats are not merely theoretical but have manifested in real-world attacks, disrupting operations, stealing sensitive data, and impacting global supply chains.
The following sections will delve into some of the most notable incidents, including ransomware attacks and data breaches that have targeted critical transportation hubs and logistics operations worldwide, highlighting the growing sophistication of cybercriminals.
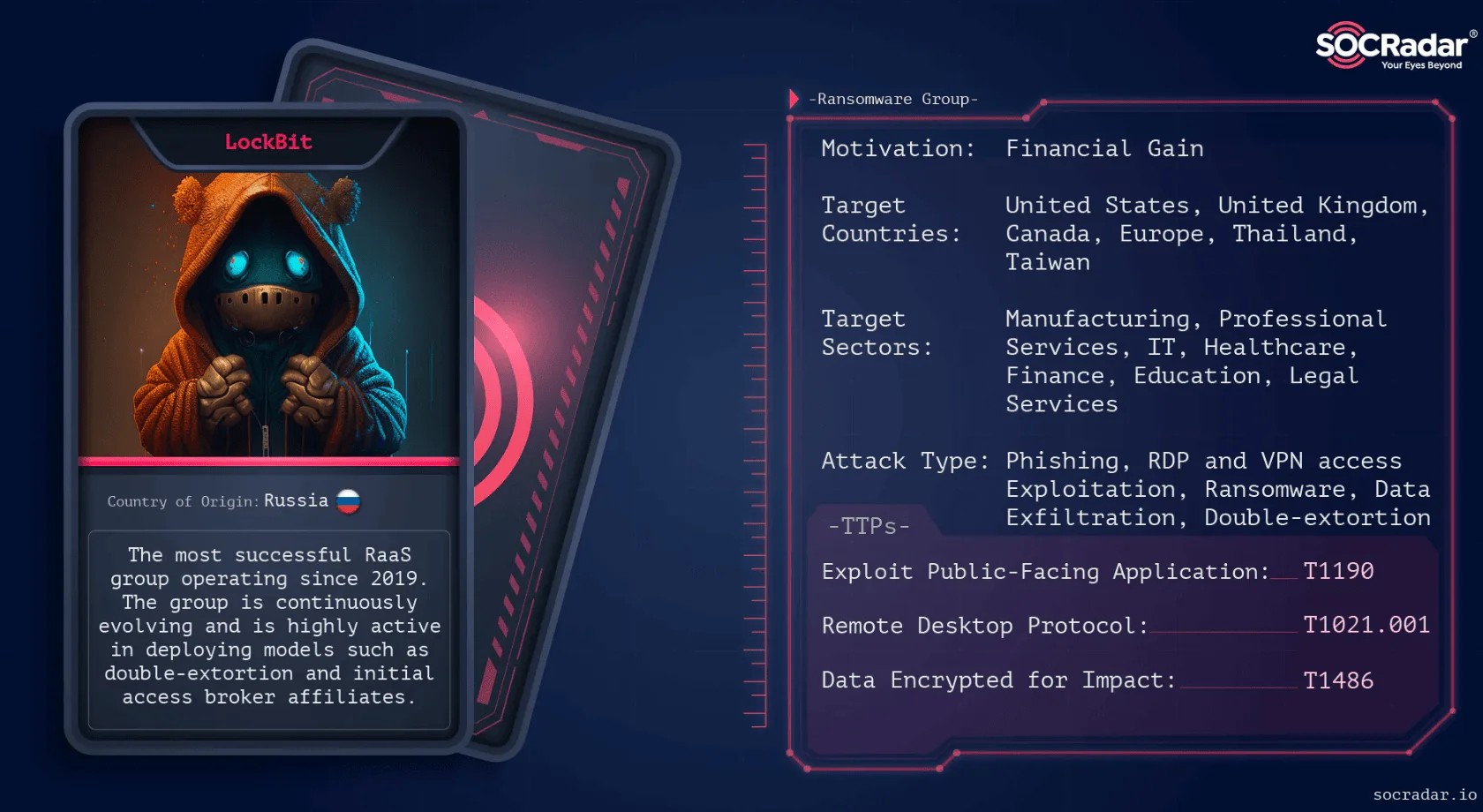
Nagoya Port Allegedly Hit by Ransomware, LockBit Suspected
In July 2023, a ransomware attack forced the Port of Nagoya—Japan’s largest maritime hub handling 10% of the nation’s trade volume—to suspend container operations.
The attack disabled the Nagoya Port Unified Terminal System (NUTS), with some terminals forced to operate manually. A ransom note, allegedly from the attackers, was discovered on a printer. Local sources and the Nagoya Harbor Transportation Association attributed the attack to the LockBit ransomware group, although the group has not claimed responsibility.
Flat design illustration of the Port of Nagoya with cultural elements and cargo ships – created by DALL-E
Trailer congestion was observed during the outage, with port operations gradually resuming by July 6. This incident follows a 2022 DDoS attack by Killnet and adds to a growing list of ransomware attacks targeting global ports, reflecting rising cyber threats to maritime logistics.
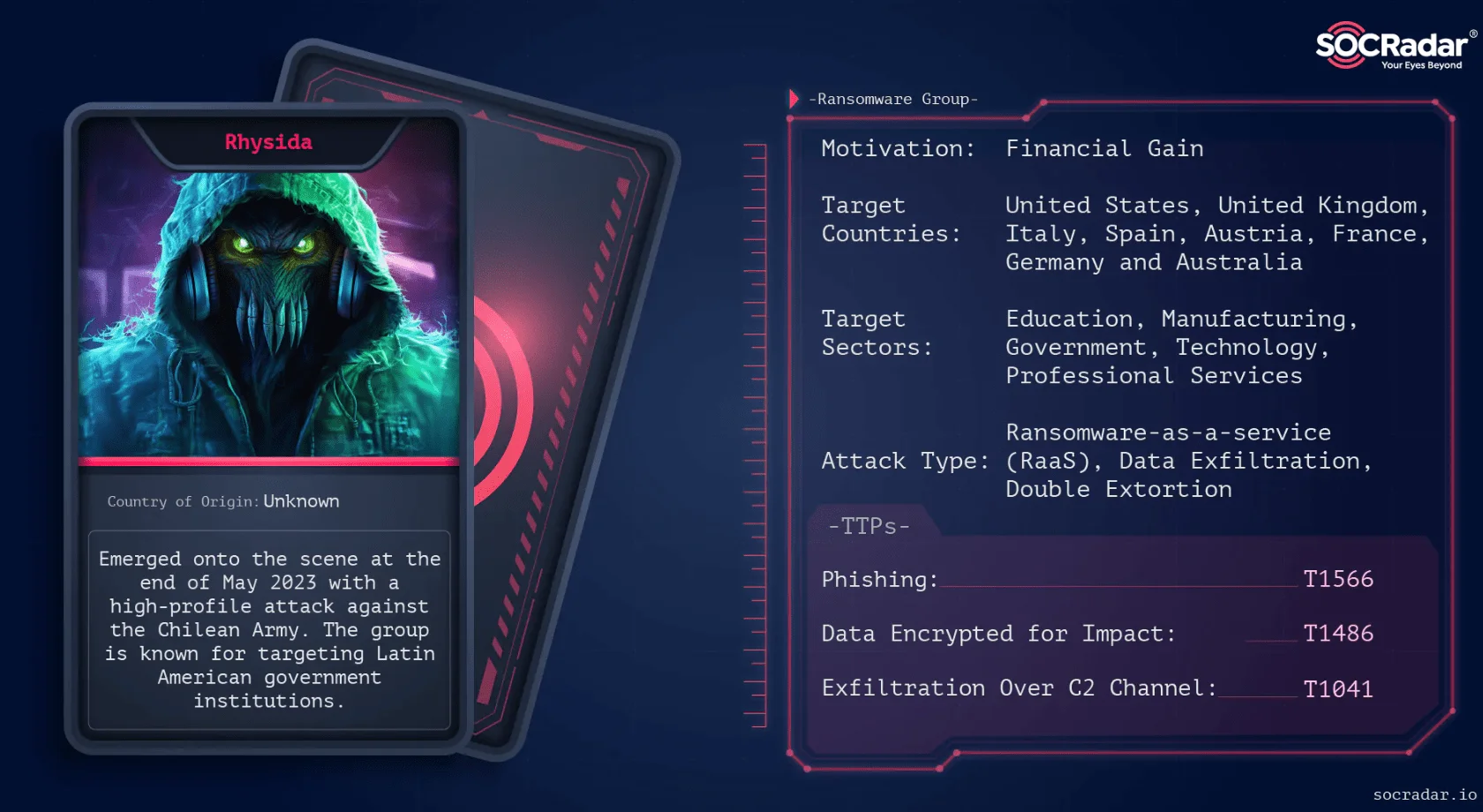
Rhysida Ransomware Allegedly Disrupts Seattle-Tacoma International Airport
In August 2023, the Rhysida ransomware gang launched a cyberattack on Seattle-Tacoma International Airport, crippling key systems for nearly three weeks. The attack disrupted boarding operations, delayed baggage delivery, and took down the airport’s website and flight information systems.
The ransomware group allegedly encrypted data and demanded a ransom of 100 Bitcoin threatening to sell the stolen files if payment wasn’t made within seven days. Exfiltrated data allegedly includes scanned U.S. passports, tax forms with Social Security numbers, and other sensitive personal information.
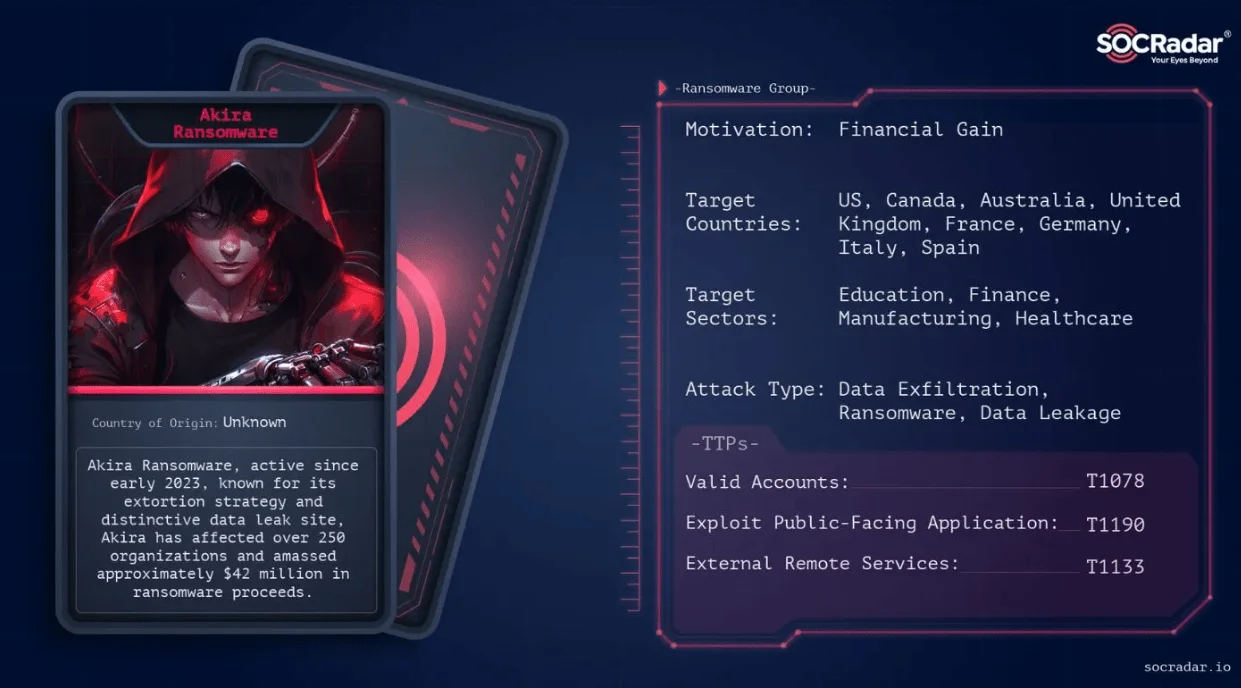
Akira Ransomware Attack Leads to Collapse of UK Logistics Giant KNP
In June 2023, UK-based KNP Logistics suffered a major ransomware attack attributed to the Akira group. Threat actors allegedly exploited a weak password through brute-force methods and gained access to critical systems due to the lack of multi-factor authentication.
The incident severely disrupted operations and compromised financial data, ultimately leading the company to declare insolvency three months later. Over 700 employees were laid off, though the sale of one group entity helped preserve around 170 jobs.
KNP’s collapse is a stark reminder of how ransomware can become an existential threat—particularly for businesses already facing market pressures. The company was added to Akira’s leak site shortly after the attack.
Cyberattack on DP World Australia Exposes Employee Data, Disrupts Port Operations
On November 10, 2023, DP World Australia—responsible for 40% of the country’s container trade—suffered a cyberattack that disrupted operations at five major ports. The incident left over 30,000 containers stranded and forced the company offline. Port activity resumed by November 13 and fully normalized by November 17.
Flat-style illustration of DP World logistics in Australia with a truck, Sydney Opera House, Harbour Bridge, and kangaroo – created by DALL-E
Although no ransomware was deployed and no ransom demands were issued, attackers exfiltrated internal data, including personal information of current and former employees. Customer data remained unaffected.
While no threat actor has claimed responsibility, some speculation has pointed to the possible involvement of state-sponsored groups. The incident remains under investigation by Australian cybersecurity and law enforcement authorities.
ORBCOMM Ransomware Attack Disrupts Fleet Tracking
On September 6, 2023, ORBCOMM—an international provider of fleet management and asset tracking solutions—suffered a ransomware attack that disrupted its FleetManager platform and Blue Tree Electronic Logging Devices (ELDs). The outage left many transportation companies unable to track their vehicles, while truck drivers were forced to revert to paper logs. The U.S. Federal Motor Carrier Safety Administration later issued a temporary waiver to avoid regulatory complications.
Flat-style illustration of a ransomware attack in the U.S., featuring a hacked satellite, truck, Statue of Liberty, and American landmarks – created by DALL-E
Although the company confirmed the incident and worked with cybersecurity experts to contain the threat, the identity of the ransomware group behind the attack remains unknown. Most affected systems were expected to be restored by late September 2023.
However, more than a year later, the situation resurfaced in dark web channels. According to SOCRadar Dark Web News, on November 5, 2024, a threat actor on BreachForums claimed to possess and sell a full database allegedly stolen from ORBCOMM. The post advertised over 70TB of SQL data for $30,000, with an additional $100,000 fee to have the data removed. While the legitimacy of the leaked files remains unverified, the post included screenshots and sample links as evidence.
This incident highlights how ransomware attacks can extend beyond their initial impact, with data often reappearing on underground forums months later—posing ongoing risks to both organizations and their clients.
To detect and mitigate such risks, organizations can leverage SOCRadar’s Advanced Dark Web Monitoring module. This advanced threat intelligence solution offers continuous monitoring of dark web forums, marketplaces, and Telegram channels, helping security teams identify data leaks, compromised credentials, and brand impersonation early. With automated alerts and detailed incident context, the module enables proactive defense before threats escalate into full-scale breaches.
TfL Cyberattack Disrupts Services, Exposes Data
On September 1, 2024, Transport for London (TfL) detected signs of a cyberattack that has since evolved into a prolonged and costly cybersecurity incident. The organization later confirmed that certain customer data had been accessed, including names, contact details, addresses, and banking information.
Flat-style illustration of a cybersecurity breach in the London Underground, featuring the Underground logo, a red train, ticket barriers, and a warning sign – created by DALL-E
Although public transport services like the Tube and buses remained operational, several digital services were taken offline as a precaution. These included live arrival times, jam cams, Dial-a-Ride bookings, refund processing for contactless journeys, and applications for Oyster and Zip photocards. TfL engineers also performed a full IT reset for staff, who were temporarily instructed to work remotely.
The financial impact of the attack is estimated in the millions of pounds. TfL has not disclosed the identity of the threat actor, and no group has claimed responsibility. However, the nature of the breach has been described as both sophisticated and aggressive, raising concerns about the vulnerability of public infrastructure to long-term cyber threats.
Insider-Linked Cyberattacks Hits Wi-Fi at Major U.K. Train Stations
In late September 2024, a cyberattack disrupted public Wi-Fi services at 19 major railway stations across the U.K., including London Euston, Manchester Piccadilly, and Edinburgh Waverley. Passengers attempting to log in were confronted with Islamophobic messages referencing terror attacks, sparking public alarm.
Flat-style illustration of a Wi-Fi cyberattack at a U.K. train station, featuring a hooded hacker, warning symbols, concerned passengers, and a red train – created by DALL-E
The attack, initially feared to be a security breach, was later identified as an act of cyber vandalism originating from within the network of Global Reach, the internet provider working with Telent and Network Rail. An unauthorized change was made using a legitimate administrator account, suggesting potential insider involvement.
British Transport Police launched an investigation into the incident, which occurred amid heightened national tensions following recent anti-Muslim riots. Although no personal data was compromised, the Wi-Fi service was suspended pending security checks and was restored by the end of the weekend.
This case underscores the risks posed not only by external threat actors but also by trusted internal accounts—particularly when public infrastructure is involved.
Ward Transport & Logistics Hit by 574GB Data Breach Linked to DragonForce
DragonForce Ransomware allegedly targeted Ward Transport & Logistics on March 4, 2024, claiming to have exfiltrated 574.14GB of internal data. The group listed the files on dark web platforms, though the authenticity of the leaked material has not been independently verified.
DragonForce Ransomware first emerged in December 2023 and has since been associated with a string of impactful cyberattacks. Allegedly linked to the infamous LockBit group, DragonForce has demonstrated advanced capabilities in breaching corporate networks and encrypting sensitive data. Their tactics combine traditional ransomware techniques with aggressive data-leak extortion strategies aimed at maximizing financial pressure on victims.
One of the most common methods ransomware groups exploit for initial access is leaked credentials—often obtained from past data breaches or stealer logs circulating on the dark web.
With SOCRadar Labs’ Free Dark Web Report, you can instantly check whether your organization’s email addresses, domains, or employee credentials have been exposed on hacker forums, leak sites, or Telegram channels.
Baltic Region Experienced Widespread GPS Jamming Linked to Russia
Since late 2023, thousands of civilian flights across Europe have faced GPS signal interference, particularly over the Baltic, Black Sea, and eastern Mediterranean regions.
Officials from Baltic states accuse Russia of jamming and spoofing GPS signals from areas near St. Petersburg and Kaliningrad. Affected flights include a RAF jet carrying UK Defence Secretary Grant Shapps and several Finnair routes to Estonia, some of which were suspended.
While aircraft rely on backup systems, experts warn that the persistent interference poses growing risks to aviation safety and violates international norms.
Hades Ransomware Attack Allegedly Hits Forward Air, Causes $7.5M Revenue Loss
In December 2020, U.S.-based freight and logistics provider Forward Air was targeted in a ransomware attack that severely disrupted its IT and operational systems. The incident, later linked to the emerging Hades ransomware group, forced the company to take systems offline and led to significant freight delays.
Forward Air confirmed the breach in regulatory filings, stating that it caused service interruptions across its terminals and impacted customs-related documentation. The company reported an estimated $7.5 million loss in revenue tied to the incident.
Hades, operating in human-led attacks, encrypted systems and used Tor-based communication methods similar to other advanced ransomware gangs. While the ransom demand was not disclosed, the attackers threatened to leak stolen files through social media channels.