
Mastering the Art of Monitoring the Dark Web for CISOs: Tips and Tricks
In the ever-evolving landscape of cybersecurity, Dark Web monitoring has emerged as a significant area of concern for Chief Information Security Officers (CISOs). Dark Web is a mysterious and often misunderstood part of the internet where cybercriminals lurk, carrying out illicit activities away from the prying eyes of law enforcement. This blog aims to equip CISOs and other cybersecurity professionals with the knowledge, tools, and strategies necessary to effectively monitor the Dark Web, identify potential threats, and protect their organizations from cyber threats. This journey will not only demystify the Dark Web but also empower you to leverage its insights for proactive cybersecurity management.
Understanding the Dark Web and Its Risks
The Dark Web, also known as the underbelly of the internet, is a place where criminal activities thrive. It provides an anonymous platform for hackers, scammers, and other cybercriminals to operate without fear of detection or prosecution. Understanding the risks associated with the Dark Web is essential for any CISO who aims to protect their organization from potential harm.
Facts:
- According to the 2021 Cost of Data Breach Report from IBM Security, the average total cost of a data breach is $4.24 million, making proactive detection through dark web monitoring critical.
- A study by the University of Maryland found that a hacker attack occurs every 39 seconds on average, underlining the importance of continuous dark web monitoring.
- As per Cybint’s data, approximately 15% of the internet is the dark web, housing a vast array of potential threats that require monitoring.
One of the primary dangers of the Dark Web is information theft. Attackers use tools like keyloggers to collect sensitive data from unsuspecting users infected with malware. This stolen information can then be sold or used for various illicit activities, posing a significant threat to individuals and organizations alike.
Phishing, another prevalent problem on the Dark Web, takes advantage of its unregulated nature. Users must be cautious and never disclose their financial information to anyone on the Dark Web. Scammers often use various tactics to trick individuals into sharing sensitive data, leading to identity theft or financial losses.
Moreover, the Dark Web is home to harmful content that can have severe consequences, especially for vulnerable individuals.
Lastly, browsing the Dark Web itself is a risky endeavor. It serves as a meeting ground for hackers and cybercriminals, increasing the likelihood of encountering malicious content. Downloading files from the Dark Web can expose users to viruses, malware, trojans, ransomware, and other malicious files that can infect their devices and compromise their security.
As a CISO, understanding the dark side of the internet is crucial for implementing effective cybersecurity measures. It is imperative to grasp the complexities and risks associated with the Dark Web. With its unregulated nature and prevalence of criminal activity, the Dark Web poses a significant threat to organizations. By understanding the Dark Web and staying informed about the latest trends and tactics used by cybercriminals, CISOs can better protect their organization from potential harm.
Importance of Dark Web Monitoring for CISOs
As cyber threats continue to evolve, the dark web has become a hub for criminal activity, making dark web monitoring a critical aspect of a CISO’s role. With the increasing sophistication of cybercriminals, organizations need to be proactive rather than reactive in protecting their sensitive data. Dark web monitoring is a powerful tool for identifying potential risks and mitigating cyber threats. By monitoring the dark web, CISOs can detect potential security breaches, respond swiftly, and prevent sensitive data from being compromised. This can help maintain stakeholder trust and minimize damage to an organization’s reputation.
In addition to its security benefits, dark web monitoring also aids regulatory compliance by ensuring data protection laws are being followed. The costs of a data breach are high, with the average total cost reaching millions of dollars. Investing in dark web monitoring can save organizations significant costs in the long run.
Dark web monitoring is an essential aspect of a CISO’s role, enabling them to detect potential cyber threats, protect sensitive data, and maintain regulatory compliance. Dark web monitoring is an ever-evolving field that requires constant updates and adjustments to remain effective.
Below are some tips and tricks for CISOs to enhance their dark web monitoring strategies.
- Start with a Clear Plan: Develop a clear plan of action that outlines the scope of your dark web monitoring program and aligns with your organization’s goals.
- Stay Up-to-Date: Stay abreast of the latest trends and tactics used by cybercriminals on the dark web through research and collaboration with industry peers.
- Choose the Right Tools: Select the right tools for your organization’s specific needs, taking into account factors like scalability, budget, and compatibility with your existing infrastructure. #CISODarkWebInsights
- Embrace Automation: Consider utilizing automation and machine learning technologies to increase the speed and accuracy of your dark web monitoring program.
- Use Intelligence-Based Threat Detection: Employ threat intelligence tools that use AI algorithms and machine learning models to sift through large volumes of data to identify potential threats.
- Conduct Regular Assessments: Regularly assess the effectiveness of your dark web monitoring program to identify areas of improvement and implement necessary changes.
- Collaborate with Your Team: Involve your team in the monitoring process, sharing intelligence and insights to create a holistic view of potential threats.
By following these tips and leveraging the right tools, CISOs can enhance their dark web monitoring programs and stay ahead of the evolving cyber threats lurking in the shadows of the internet. Monitoring the Dark Web closely can help CISOs to
- Protects Sensitive Data: Dark Web monitoring enables CISOs to safeguard their organization’s sensitive data like financial data, intellectual property, and personal information of employees and customers.
- Mitigates Cyber Threats: Through continuous monitoring of the dark web, CISOs can detect possible threats, such as leaked credentials, thereby mitigating the risk of cyber attacks.
- Helps in Incident Response: Real-time alerts on dark web activities relevant to their organizations aid CISOs in taking immediate action and preparing incident response plans.
- Facilitates Regulatory Compliance: Dark web monitoring aids in ensuring compliance with data protection laws and regulations, a key part of a CISO’s role.
- Enhances Reputation Management: By promptly addressing data breaches, CISOs can minimize damage to their organization’s reputation and maintain the trust of stakeholders.
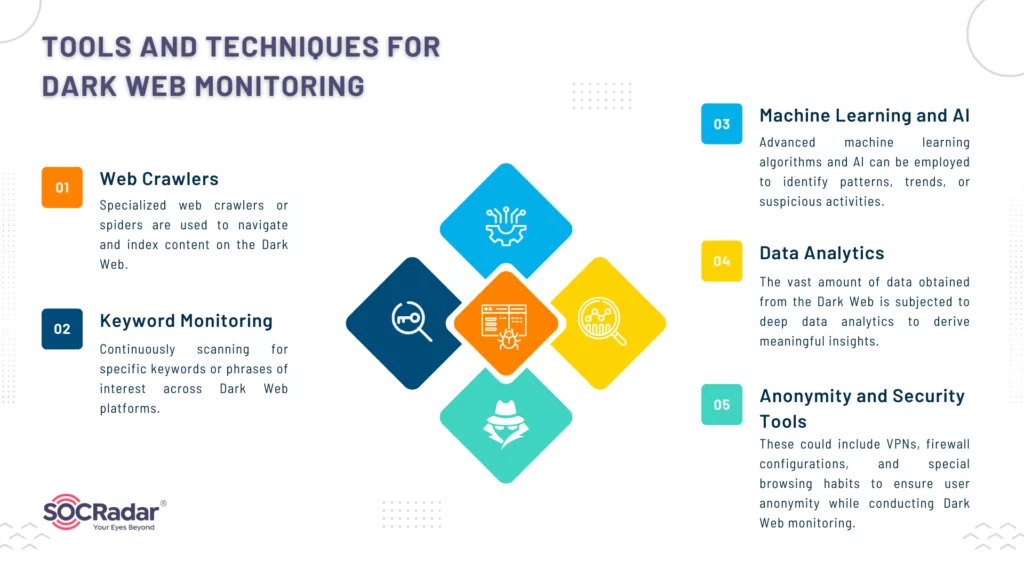
Tools and Techniques for Dark Web Monitoring
When it comes to monitoring the dark web, there are several tools and techniques that can be utilized to ensure effective detection and mitigation of cyber threats. One of the most important tools is specialized web crawlers or spiders that are specifically designed to navigate and index content on the dark web. These crawlers are able to handle .onion URLs and bypass various restrictions that would prevent regular search engine crawlers from accessing the dark web. Another technique that can be used is keyword monitoring. This involves continuously scanning for specific keywords or phrases of interest across dark web platforms. By scanning for specific data types like credit card numbers, social security numbers, or even specific company or product names, potential breaches or threats can be identified.
Machine learning and AI are also powerful tools for dark web monitoring. Advanced algorithms can be employed to identify patterns, trends, or suspicious activities. Semantic analysis can be used to understand the context around certain discussions and identify potential threats that may not be immediately apparent. Data analytics plays a crucial role in making sense of the vast amount of data obtained from the dark web. Utilizing big data technologies, the data can be organized, analyzed, and interpreted to derive meaningful insights. Lastly, it is important to utilize anonymity and security tools to ensure the user’s own security while conducting dark web monitoring. Tools like Tor (The Onion Router) are necessary for accessing the dark web, but additional measures such as VPNs, firewall configurations, and special browsing habits should be employed to ensure user anonymity. By leveraging these tools and techniques, CISOs can effectively monitor the dark web for cyber threats and take proactive measures to safeguard their organizations.
- Web Crawlers: Specialized web crawlers or spiders are used to navigate and index content on the Dark Web. Unlike standard search engine crawlers, these are specifically designed to handle .onion URLs and to bypass various restrictions that would prevent regular crawlers from accessing the Dark Web.
- Keyword Monitoring: This technique involves continuously scanning for specific keywords or phrases of interest across Dark Web platforms. This could include specific data types like credit card numbers, social security numbers, or specific company or product names to identify potential breaches or threats.
- Machine Learning and AI: Advanced machine learning algorithms and AI can be employed to identify patterns, trends, or suspicious activities. They can also be used for semantic analysis, to understand the context around certain discussions, and to identify potential threats that might not be immediately apparent.
- Data Analytics: The vast amount of data obtained from the Dark Web is subjected to deep data analytics to derive meaningful insights. This includes using Big Data technologies to organize, analyze, and interpret the data.
- Anonymity and Security Tools: Tools like Tor (The Onion Router) are necessary for accessing the Dark Web, but additional security measures are also needed to ensure the monitoring activity doesn’t compromise the user’s own security. These could include VPNs, firewall configurations, and special browsing habits to ensure user anonymity while conducting Dark Web monitoring.
Best Practices for Detecting and Mitigating Cyber Threats on the Dark Web
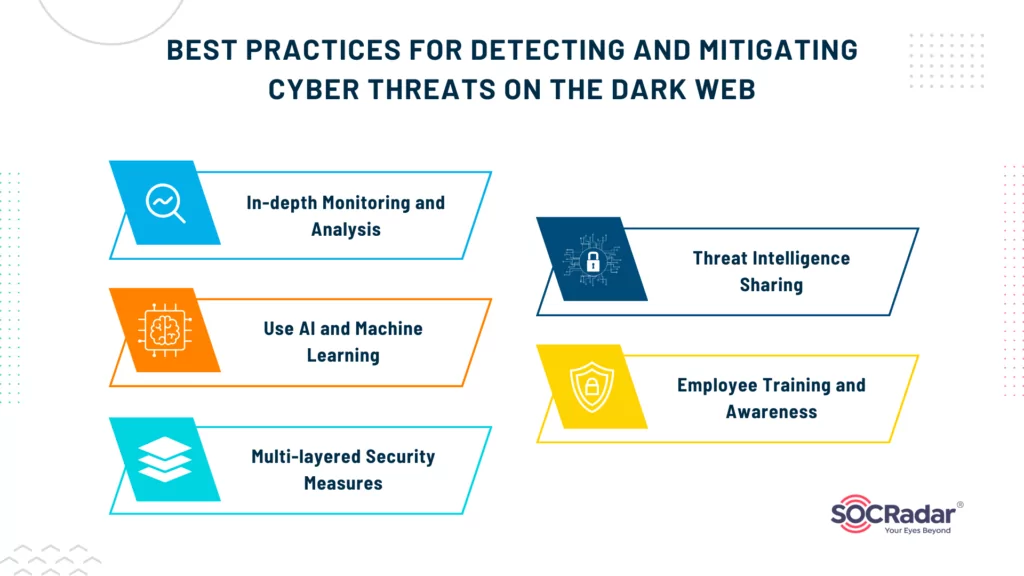
Detecting and mitigating cyber threats in the Dark Web requires a proactive and multi-faceted approach. Here are some best practices that CISOs should consider:
- In-depth Monitoring and Analysis: It is crucial to constantly monitor the Dark Web for potential threats and vulnerabilities. Utilize specialized web crawling and data analysis tools to gather intelligence on threat actors, hacking tools, potential leaks, and other cybersecurity-related information. This proactive monitoring can help detect and address threats before they impact your organization.
- Use AI and Machine Learning: Implement advanced AI and machine learning algorithms for predictive threat analysis. These technologies can help identify patterns and trends and predict future cyber threats emanating from the Dark Web before they materialize in real-world scenarios. By leveraging AI and machine learning, CISOs can stay one step ahead of cybercriminals and proactively defend their organization’s assets.
- Multi-layered Security Measures: Employ a multi-layered security approach that includes intrusion detection systems (IDS), firewalls, secure gateways, and robust endpoint protection. This comprehensive defense strategy will help detect and prevent Dark Web-originated threats before they infiltrate your network. By combining different security measures, CISOs can create a strong security perimeter to safeguard sensitive information.
- Threat Intelligence Sharing: Participate in cyber threat intelligence sharing networks or platforms. These platforms allow organizations to share information about cyber threats detected on the Dark Web and other sources, collectively enhancing everyone’s defense capabilities. By actively engaging in threat intelligence sharing, CISOs can gain valuable insights and stay informed about emerging threats in the Dark Web landscape.
- Employee Training and Awareness: Regularly educate and train staff about the potential cyber threats originating from the Dark Web. An aware and well-trained workforce can significantly reduce the risk of successful cyberattacks, as they will be better equipped to identify and avoid phishing attempts, malware, and other cyber threats. Conducting regular cybersecurity awareness programs and providing employees with the necessary training will enhance the overall security posture of the organization. By implementing these best practices, CISOs can strengthen their organization’s defense against cyber threats lurking in the Dark Web.
Case Studies: Real-world Success Examples of Organizations Which Monitor the Dark Web
Case Study 1: Financial Institution Thwarts Potential Data Breach
A major bank implemented dark web monitoring as part of its cybersecurity strategy. The monitoring tool detected a forum post on the dark web where a user was attempting to sell credit card information. The bank was able to identify that some of the card numbers were from their institution. They quickly alerted the affected customers, issued new cards, and prevented any fraudulent transactions, saving millions in potential losses.
Case Study 2: Healthcare Provider Prevents Patient Data Exposure
A healthcare provider monitored the dark web to protect patient data. The monitoring tool detected a dark web listing selling patient records. The provider was able to identify the data as their own and quickly patched the security vulnerability that led to the data leak. They also informed the affected patients and offered them identity theft protection services, thereby maintaining their reputation and patient trust.
Case Study 3: Tech Company Recovers Stolen Intellectual Property
A tech company had their proprietary software code stolen and noticed unusual activity on their network. They employed a dark web monitor service, which discovered the stolen code being sold on the dark web. The company was able to work with law enforcement to track down the culprits and recover their intellectual property, preventing potential revenue loss and competitive disadvantage.
Case Study 4: University Protects Student Information
A university’s IT department monitored the dark web as part of their cybersecurity measures. The tool detected a dark web post where a user was selling student social security numbers. The university was able to quickly identify the affected students, alert them, and work with authorities to track down the source of the leak, thereby preventing potential identity theft.
Case Study 5: E-commerce Company Stops Account Takeovers
An e-commerce company was experiencing a surge in account takeover incidents. They employed a dark web monitoring service, which discovered a cache of their customers’ login credentials being sold on the dark web. The company was able to force a password reset for the affected accounts, alert the customers, and enhance their security measures to prevent further incidents.
The Role of a CISO in Dark Web Monitoring
As the cybersecurity landscape evolves, the role of a CISO in monitoring the dark web becomes increasingly critical. Understanding the dark web and its associated risks is only the first step. CISOs must proactively identify potential threats and assess the level of risk they pose to the organization. In case of a security breach, they must have an incident response plan in place to contain and investigate the breach. Furthermore, the CISO must develop and implement an overall security strategy that takes into account insights gained from monitoring the dark web. Collaboration and communication are key to success in this area. CISOs must work with other departments, law enforcement, and external cybersecurity firms to effectively monitor the dark web. They must also communicate the importance of dark web monitoring to the organization’s leadership and ensure that they have the necessary resources.
In short, being a CISO is a multifaceted job that involves understanding the dark web and developing strategies to mitigate associated risks. With the right tools and techniques, CISOs can safeguard their organizations from potential threats on the dark web.
Furthermore, they must also communicate the importance of dark web monitoring to the organization’s leadership and ensure that they have the necessary resources to support these efforts. In addition to collaboration and communication, CISOs should also develop their own skills and expertise in understanding the dark web. This may involve staying up-to-date with the latest trends, tools, and techniques used by cybercriminals on the dark web. By continuously learning and adapting, CISOs can better anticipate and respond to emerging threats.
Ultimately, being a CISO in the realm of dark web monitoring requires a proactive and strategic approach. By mastering the art of monitoring the dark web, CISOs can effectively safeguard their organizations from potential cyber threats and ensure the overall security posture of their organization remains robust. Stay tuned for the next section, where we will explore some tips and tricks for effective dark web monitoring.
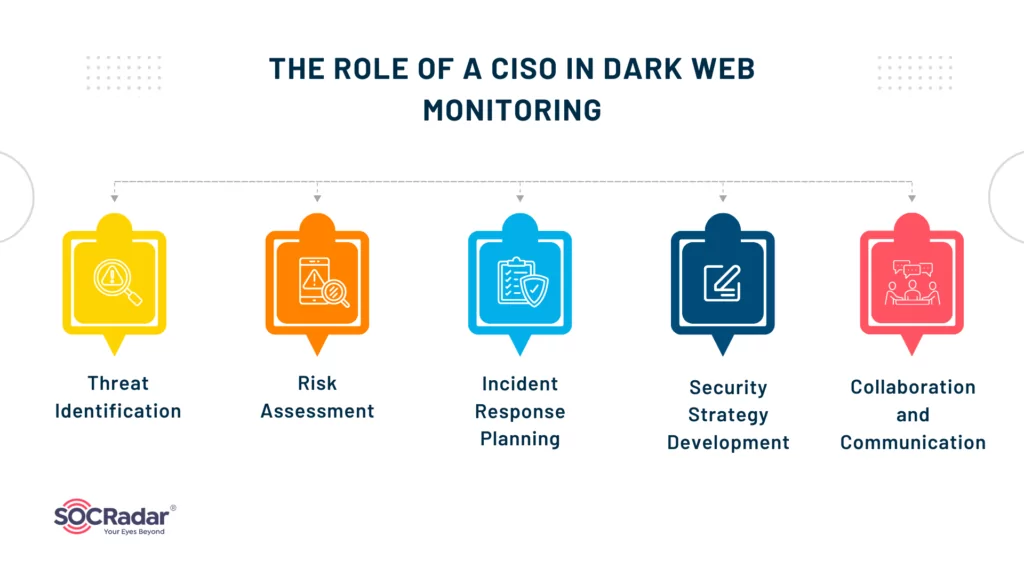
- Threat Identification: A CISO (Chief Information Security Officer) is responsible for identifying potential threats on the dark web that could impact the organization. This includes monitoring for leaked sensitive data, stolen credentials, or discussions about the organization on illicit forums.
- Risk Assessment: The CISO must assess the risk level of the identified threats. This involves understanding the potential impact on the organization’s operations and reputation and determining the likelihood of the threat materializing.
- Incident Response Planning: In case of a security breach or data leak, the CISO is responsible for coordinating the incident response. This includes containment of the breach, investigation, and recovery, as well as communication with stakeholders.
- Security Strategy Development: The CISO uses insights gained from dark web monitoring to inform the organization’s overall security strategy. This could involve implementing new security measures, training staff on cybersecurity best practices, or improving incident response protocols.
- Collaboration and Communication: The CISO must collaborate with other departments within the organization, law enforcement, and external cybersecurity firms to effectively monitor the dark web. They also need to communicate the importance of dark web monitoring to the organization’s leadership and ensure they have the necessary resources.
Tips and Tricks for Effective Dark Web Monitoring
To become an effective dark web monitor, CISOs must understand the landscape, use specialized tools, maintain anonymity, set up alerts, and stay updated. Using these will help you master the art of dark web monitoring.
Familiarize yourself with the structure and operation of the dark web to navigate through Tor networks and other darknet markets effectively. Utilize monitoring tools and services that can scan, index, and alert you about data leaks and threats.
Prioritize your safety and anonymity by using VPNs, the Tor browser, and other security measures. Configure your monitoring tools to alert you when specific keywords related to your organization or personal information appear on the dark web.
Lastly, stay updated on the latest trends, threats, and best practices in dark web monitoring. Use these to become an effective dark web monitor. By following these CISOs can effectively monitor the dark web and protect their organizations from cyber threats.
Additionally, the emphasizes the importance of staying educated and updated on the latest developments in dark web monitoring. This involves participating in online cybersecurity communities, attending relevant conferences and workshops, and staying informed about emerging threats and best practices. With these strategies in place, CISOs can proactively detect and mitigate cyber risks in the dark web and enhance their organization’s overall cybersecurity posture.
- Understand the Dark Web Landscape: Familiarize yourself with the structure and operation of the dark web. This includes understanding the difference between the surface web, deep web, and dark web, as well as knowing how to navigate through Tor networks and other darknet markets.
- Use Specialized Tools and Services: Utilize dark web monitoring tools and services that can scan, index, and alert you about data leaks, threats, and other relevant information. These tools can help you track and analyze dark web content effectively.
- Maintain Anonymity: Always prioritize your safety and anonymity when monitoring the dark web. Use VPNs, the Tor browser, and other security measures to protect your identity and location.
- Set Up Alerts for Specific Keywords: Configure your monitoring tools to alert you when specific keywords related to your organization or personal information appear on the dark web. This can help you respond quickly to potential threats or data breaches.
- Stay Updated and Educated: The dark web is constantly evolving, with new sites and threats emerging regularly. Stay updated on the latest trends, threats, and best practices in dark web monitoring. Participate in cybersecurity forums and communities to learn from experts and peers in the field.
The Future of Dark Web Monitoring
The future of Dark Web monitoring is a topic of significant interest, given the increasing prevalence of cyber threats and the growing importance of cybersecurity. As we look ahead, several key trends and developments are likely to shape the landscape of Dark Web monitoring.
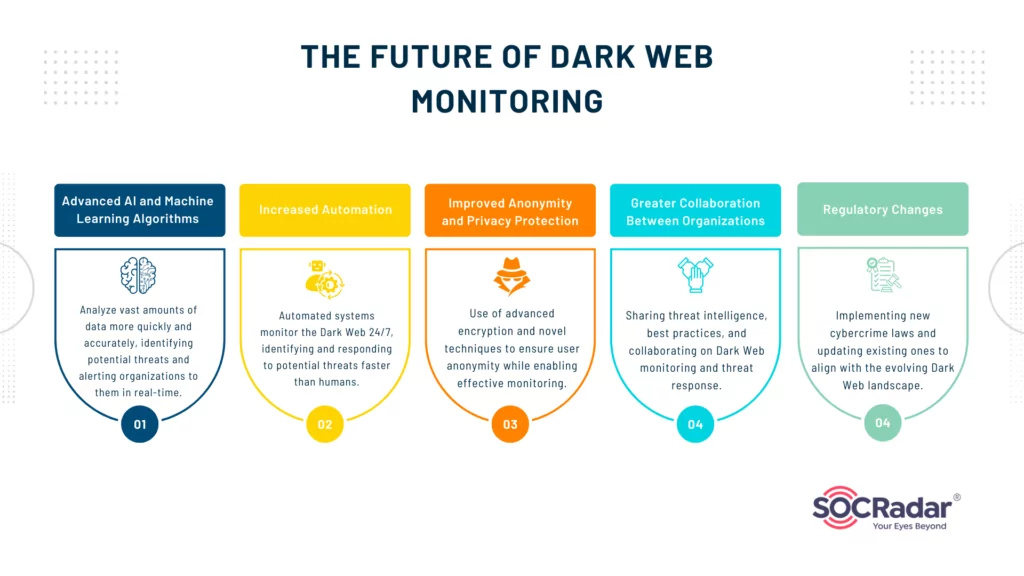
- Advanced AI and Machine Learning Algorithms: As technology continues to evolve, we can expect to see more advanced AI and machine learning algorithms being used in Dark Web monitoring. These algorithms can help to analyze vast amounts of data more quickly and accurately, identifying potential threats and alerting organizations to them in real-time. This could significantly enhance the effectiveness of Dark Web monitoring and help to prevent cyber attacks before they occur.
- Increased Automation: The future of Dark Web monitoring will likely involve a greater degree of automation. Automated systems can monitor the Dark Web around the clock, identifying potential threats and responding to them more quickly than human operators could. This could help to reduce the risk of cyber-attacks and improve the overall efficiency of Dark Web monitoring.
- Improved Anonymity and Privacy Protection: As the Dark Web is often associated with illegal activities, there is a growing demand for improved anonymity and privacy protection in Dark Web monitoring. This could involve the use of more sophisticated encryption technologies, as well as new methods for preserving user anonymity while still allowing for effective monitoring.
- Greater Collaboration Between Organizations: The future of Dark Web monitoring may also involve greater collaboration between different organizations. This could include sharing threat intelligence and best practices, as well as joint efforts to monitor the Dark Web and respond to potential threats. Such collaboration could help to improve the overall effectiveness of Dark Web monitoring and enhance cybersecurity on a global scale.
- Regulatory Changes: As the Dark Web continues to evolve, we can expect to see changes in the regulatory landscape. This could include new laws and regulations aimed at combating cybercrime, as well as changes to existing laws to reflect the changing nature of the Dark Web. These regulatory changes could have a significant impact on the future of Dark Web monitoring.
In conclusion, the landscape of cybersecurity is ever-evolving, and the dark web has become a significant part of that landscape. As the digital underworld continues to grow and become more sophisticated, it is more critical than ever for Chief Information Security Officers (CISOs) to stay one step ahead. Dark web monitoring has emerged as an essential tool in the CISO’s arsenal, providing invaluable insights into potential threats and vulnerabilities that could impact their organizations.
By proactively monitoring the dark web, CISOs can gain a deeper understanding of the tactics, techniques, and procedures employed by threat actors, enabling them to better protect their organizations. It is not just about defense but about understanding the game and the players involved.
In the high-stakes world of cybersecurity, knowledge is power. The dark web, despite its inherent risks and challenges, offers a wealth of information that can be harnessed to strengthen an organization’s security posture. Therefore, dark web monitoring should not be viewed as an optional extra but rather as a necessity in the modern cybersecurity landscape.
As we move forward, the role of the CISO will continue to evolve, and those who adapt and leverage the tools at their disposal, like dark web monitoring, will be best positioned to keep up with the game against threat actors. The dark web may be a murky and dangerous place, but with the right approach, it can provide the key to staying ahead in the ever-changing game of cybersecurity.



































