
MGM Casino Hack and Realities of Social Engineering Attacks
In the complicated world of cybersecurity, the most unpredictable element remains the human factor. Social engineering attacks exploit this vulnerability, transforming human error into the most significant risk for digital defense systems. Our in-depth analysis begins with a startling example that brings the severity of this threat into sharp focus: the hacking of MGM Resorts International.
On the fateful day of September 11, 2023, a notorious cybercriminal collective, Scattered Spider, joined forces with the infamous ALPHV, also known as BlackCat, to orchestrate a breach into MGM’s network. Their method? A sophisticated social engineering scheme. As an MGM employee whose details were meticulously gathered from LinkedIn, they duped the MGM helpdesk into granting them initial access to the network.
This breach serves as a chilling testament to the destructive power of social engineering and the dangers of an exposed digital footprint. It demonstrates the ease with which cybercriminals can manipulate personal information for nefarious purposes. Our upcoming articles will delve deeper, examining stealer malware logs and highlighting the ever-present threat within our digital logs, drawing parallels to the MGM incident. This analysis underscores the necessity for heightened vigilance against human-targeted cyber threats, proving that even the most secure organizations are not impervious to such attacks.
Revisiting the MGM casino incident, the hack was masterminded by the group known as ALPHV or BlackCat. With deft social engineering maneuvers, they convinced MGM’s IT service desk to bypass multi-factor authentication for certain high-level accounts. This breach of protocol allowed them to gain elevated access, dismantle security protocols, and move laterally across the MGM network. Armed with superuser privileges, they launched a crippling ransomware attack, causing extensive operational disruptions and damaging MGM’s esteemed reputation.
We invite you to dissect this alarming breach. We will explore further real-life examples of social engineering attacks, providing insights and learning opportunities from each case. Stay with us as we navigate through the lessons these cybersecurity incidents have to offer.

Social Engineering and Subject Intelligence
Social engineering is a favorite trick of hackers and cybercriminals. It’s the modern-day version of “scam artistry.” Instead of hacking computer systems, social engineers hack into people’s minds. For instance, they might make a fake phone call saying, “I’m from IT support; you need to change your password via the link in which we just sent the email.” or send an email claiming, “You’ve won a big prize, just share your info to claim.” Then, the user can click on the URL address in the phishing e-mail, enter corporate information in this link, and leak corporate credentials to the attackers. These tactics are used to gain people’s trust, and sadly, many fall for these traps.
Social engineering relies on exploiting trust, not computer systems. So, knowledge and education are some of the best ways to protect yourself from these scams. Remember: if someone you don’t know calls or emails you claiming you’ve won a big prize or asking for your password, chances are they’re social engineers!
The concept of social engineering is the main frame for many of the tactics involved, like in the MGM Resorts case. To put it more accurately, this is Subject Intelligence, also known as people searching. Ree L. Baker defines subject intelligence as “the act of collecting information and producing intelligence about a specific person.” in “Deep Dive: Exploring the Real-world Value of Open Source Intelligence”.
Threat actors conduct subject intelligence by searching for digital footprints, which many people consider passive information they have no problem sharing (such as the router information you share to get support on a blog site). In some cases, even if people do not intentionally share this information, attackers can use other methods to obtain this information.
For example, you can install a cracked version of a program you need and be happy that you don’t pay anything for it. You should be aware that in the background, you are not only being charged in cash, but you are also sharing your personal information with the other party to try to run that program. At this point, a stealer malware will have already sent out the files on your computer, the passwords on your browser, your credit card information, your address if you saved it in your browser, your browser history, and all the other information on your computer. This is a problem that may turn out to be more than the cost of the program you didn’t pay for.
Scoping Digital Footprints
Profiling is a key part of social engineering, where cyber attackers carefully gather and use data to plan attacks. The MGM Casino breach showed how attackers pretended to be authorized personnel to trick an IT worker into resetting Multi-Factor Authentication (MFA). This incident reminds us how important it is to have strong cybersecurity measures and well-written and strongly declared policies and procedures.
As the SOCRadar Threat Research Team, we simulated scenarios related to data we encountered in the SOCRadar stealer log database to show how else a scenario like the MGM Casino hack could occur. By multiplying these scenarios, we should increase our cyber security awareness and clean our digital footprints against possible subject intelligence.
You can check your own or your organization’s accounts on the Threat Hunting page of the SOCRadar Extended Threat Intelligence product to detect information that can be used in such an attack in advance and increase your system security and cyber awareness.
People and organizations are advised to act quickly when personal data is leaked. Many people who are not sufficiently aware of information security continue to use their old passwords by adding one or two symbols or numbers at the end. Such situations remind us of the importance of these leaks for individuals and organizations and underline that these data may not expire. A hacking incident 2023 could be a new version of a password used in 2021 with a “1” at the end.
YouDontKnowMyPassword1 => YouDontKnowMyPassword1!
“I think it’s more safe this time.”
Although Multi-Factor Authentication (MFA) is one of the most preferred security measures today, when an account’s access information is obtained by stealing browser cookies with stealer malware, login screens can be bypassed, even if they use Multi-Factor.
When you connect to a website, cookies that identify the session between you and the website are stored in your browser. Websites utilize browser cookies to remember and authenticate your identity and preferences. The cookies stored at the time of your connection can be seen as a pass card for your connection. Therefore, if someone else gets this pass, they will hijack your connection to the website and can perform transactions on your behalf without needing your password. You can read our article, The Evil of Everything, about the attacks that can be made with cookies and sessions.
John Doe’s Company vs Stealer Malware Logs
As we said, we plan to simulate some scenarios similar to the MGM Casinos hack. John Doe, who will be mentioned in all scenarios, was a stealer victim and a previous Acme Casino employee. Our research is trying to determine the possible consequences for John, whose computer was infected with stealer malware, and his information was leaked.
John (meaning Real John) was a perfect profile for this research. Apart from the data leaked by the stealer malware, there is very little identifying information about him on social media. Therefore, the data leaked by the stealer malware will mirror a careful person about sharing information on social media and what happens.
Understanding Social Engineering Techniques
Cybercriminals use social engineering methods to obtain qualified information by tricking individuals into disclosing confidential information. They collect information about individuals or organizations by conducting social engineering studies beforehand to convince them.
The Process of Information Gathering
The process of obtaining digital fingerprints begins with the extensive collection of information. Cybercriminals scan social media sites, forums, stealer malware logs, and other online sources to gather information about their targets. In the MGM case, the LinkedIn platform was used to gather information. We proceed directly to information gathering based on data stored in SOCRadar’s database leaked by stealer malware in the past.
Stealer malware aims to allow cybercriminals to steal passwords, cookie/session information, credit cards, crypto wallets, and more. These logs contain various types of data that can be misused. Let’s see what data we will see about our John, also known as Acme employee:
- Personal Information:
Stolen logs can reveal personal information such as names, home/office locations, phone numbers, and identification numbers. This information can be used for identity theft or phishing attacks. We found John’s personal information, which we discovered while searching for Acme’s company logins using highly sophisticated methods (the secret method is Ctrl+F “acme”) within the stealer data.
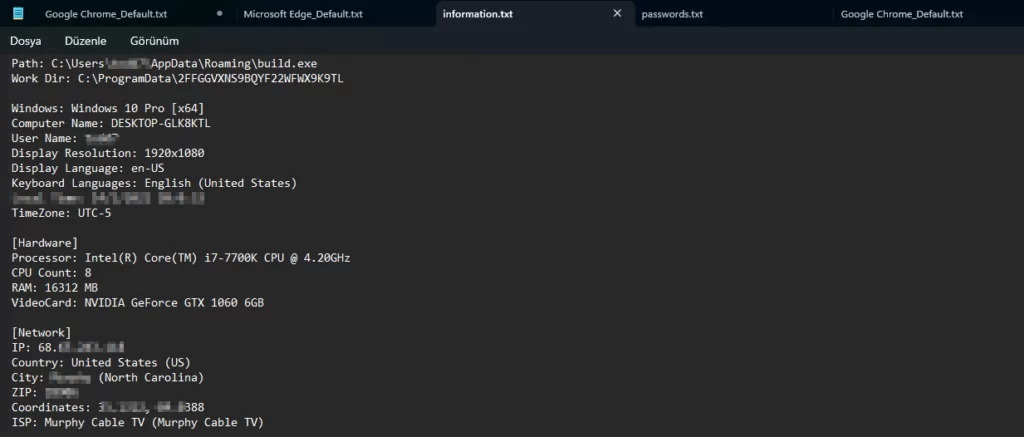
Once we have established that John is associated with Acme Casino, looking at the information.txt file prepared by the stealer can provide us with much information. After ensuring that his first name was John and his last name was Doe, we found his account on Facebook because he used the same avatar as his email address.
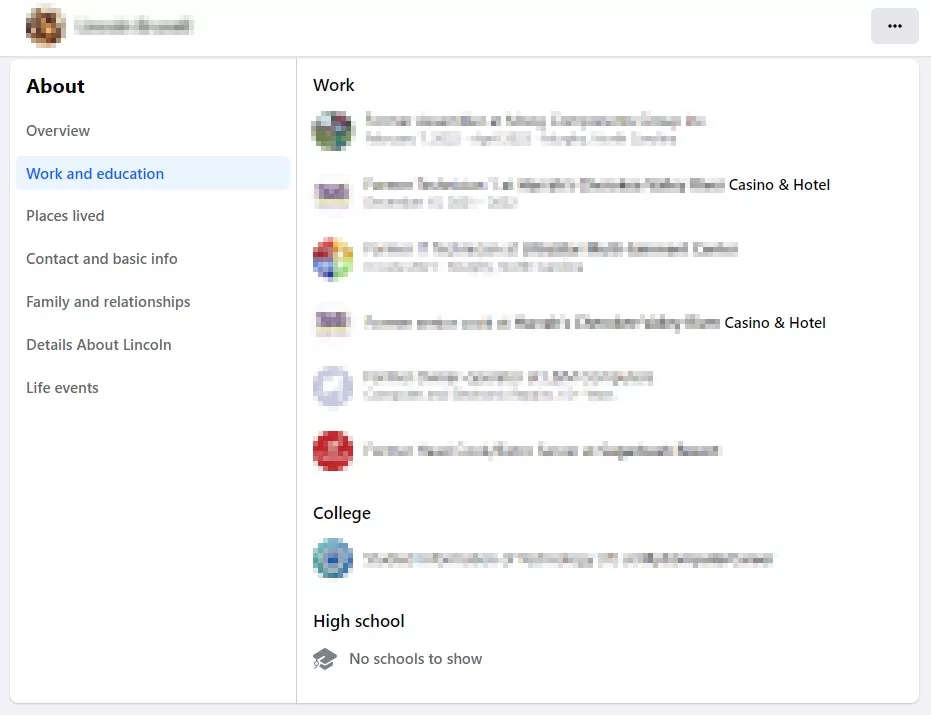
- Work Details:
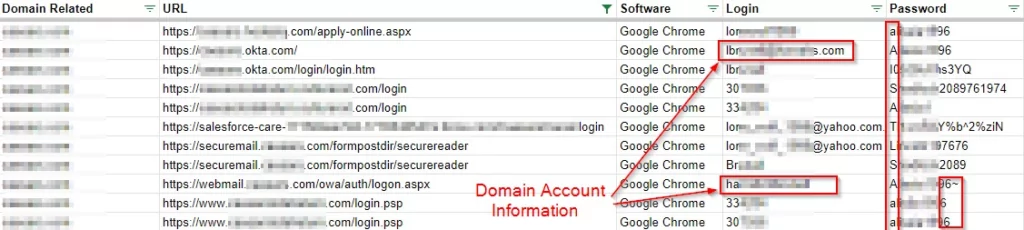
These stealer malware logs in the hands of attackers can also show where a person has worked in the past, their current job title, and personal/company email. Cybercriminals can forge a person’s identity or use this information for social engineering purposes.
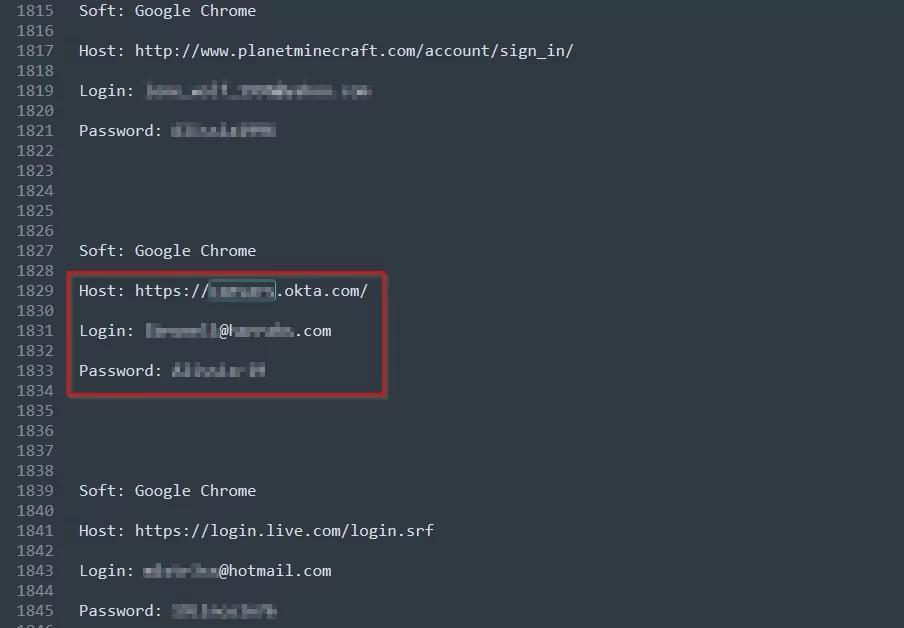
The help desk communication that played a role in the MGM Casino hack is worth recalling. The screenshot below shows that the number the attackers (a.k.a. John’s) can call for social engineering, stating they are having trouble accessing the account, is also clearly shared.
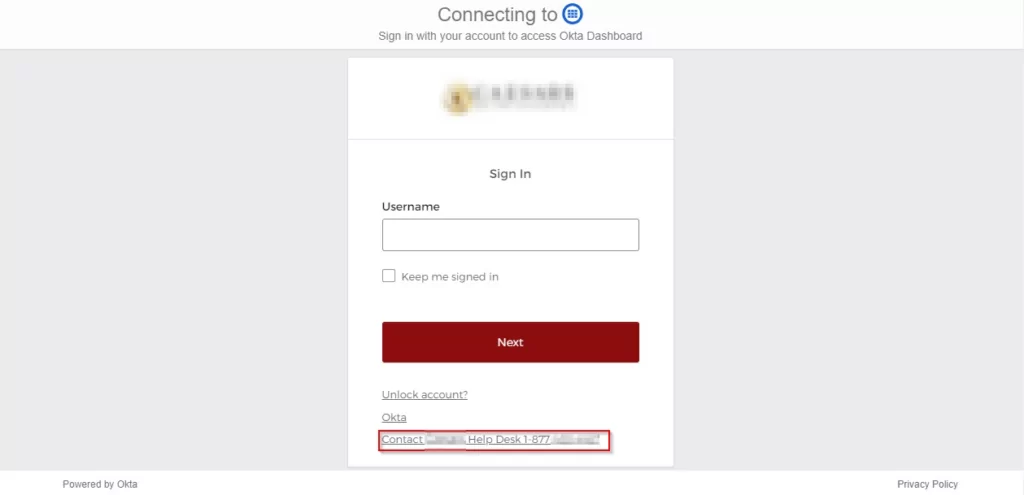
- Financial Data:
Also, stealer malware can steal financial information like bank account details or credit card numbers. This can lead to fraud or unauthorized transactions.
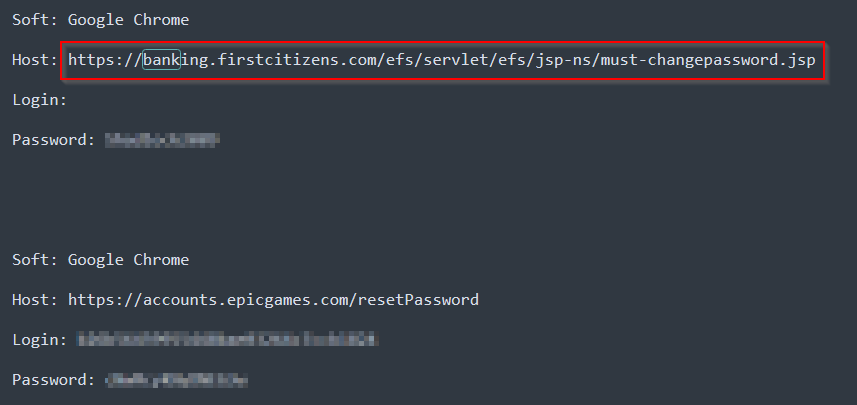
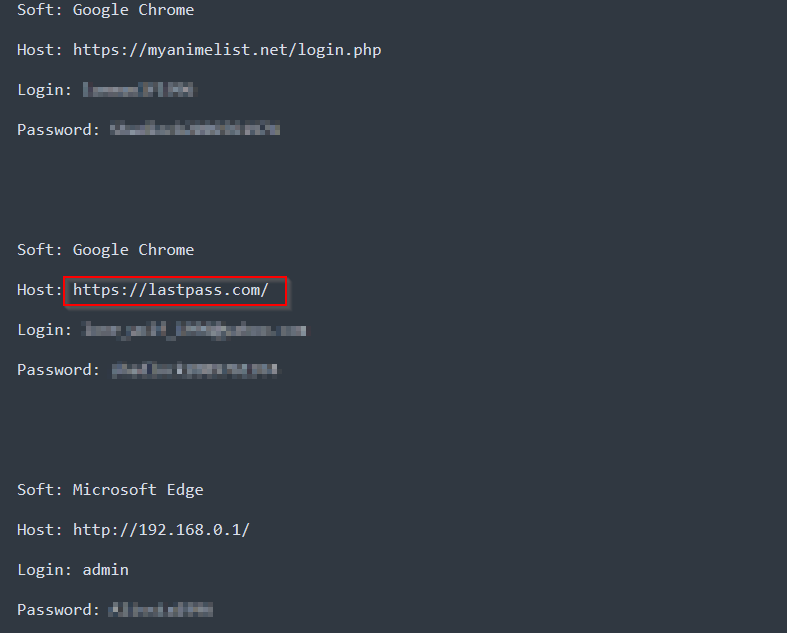
- Login Information:
Stealer logs often contain usernames and passwords for online accounts. Attackers can use these credentials to access personal and professional accounts. In some cases, the current status of these passwords can also be tracked by attackers. Storing your passwords in a password manager can be a good precaution. However, saving the password of this password manager somewhere on the operating system is not necessarily the safest way.
- Online Behavior:
They can provide insights into a person’s online habits and preferences, helping cybercriminals craft convincing attacks.
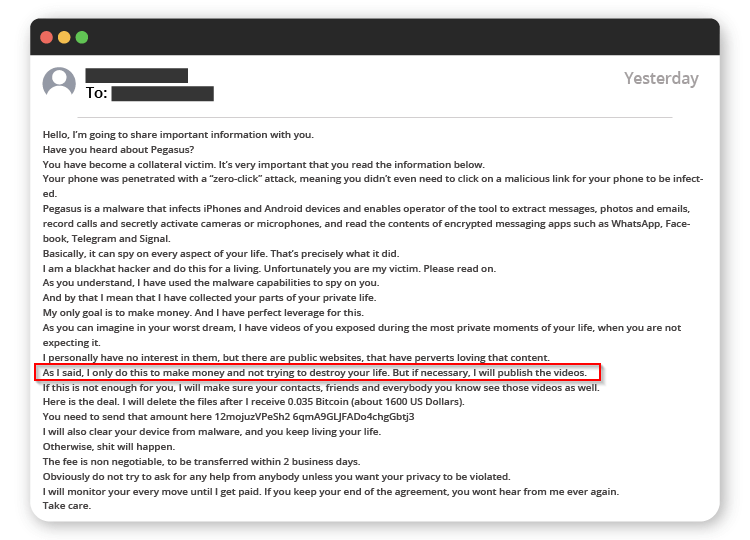
In one of the most common e-mails of the era (still), no one has not received this e-mail demanding BTC payment by saying that they have images of him. John would have been quite upset if the demand in this image was real.
We would all be disturbed by what an attacker could do if they could detect information about a person’s private life in the logs of the stealer malware.
- Technical Information:
Information about the victim’s computer setup, like the operating system and software, can be obtained. This helps plan further attacks.
Multiple devices can be licensed with Key Management Service (KMS). In the example below, the illegal Windows OS & Office Applications licensing tool called KMSauto-setup.exe explains why the device is a victim of stealer malware. Such illegal applications should always be considered as infected and should be avoided. A similar analysis of an infected KMS application can be found here.
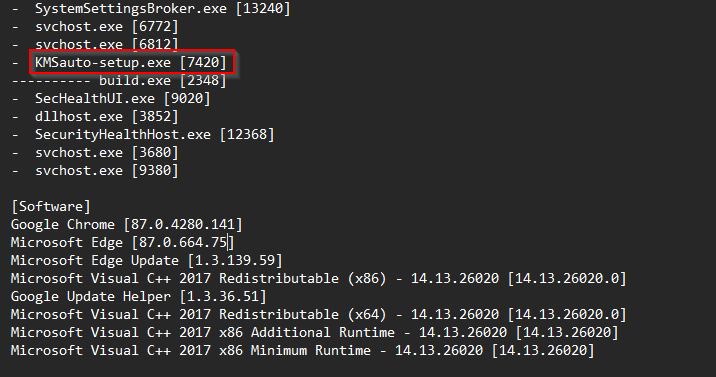
Analyzing these logs after a security breach reveals the extent of information at risk. It emphasizes the need for strong cybersecurity measures to prevent malware infections and protect sensitive data. Individuals and organizations should also stay vigilant, practice secure habits, and promote cybersecurity awareness to reduce the risks of stealer malware and data exploitation. With SOCRadar,you can monitor your brand and infected employee systems and take action by being informed when stealer malware logs are shared on underground platforms.
After all these examples, we don’t need to mention how inevitable an event like the MGM Casino hack is when attackers collect digital footprints for subject-related intelligence from stealer logs. However, let’s look at what John or the IT director of the company John works for can do if they want to protect themselves against the information that can be obtained from the stealers’ logs.
Scenarios: Attackers vs Acme Casino Company
In this scenario, the attackers could obtain the login credentials of an Acme Casino employee through the logs of malicious software called ‘Bad Stealer’. The attacker could have acquired the Acme Casino employee’s account username and password. This could have posed a significant issue for John, as it would have allowed the attacker to infiltrate the organization’s network, systems, and devices, enabling them to utilize these resources for social engineering purposes.
Threat Actors Steal Account Information
The attacker would have gained a substantial advantage by obtaining John’s username and password. Even if John had implemented Multi-Factor Authentication (MFA), the mere existence of these credentials would have significantly increased the risk of unauthorized access.
Upon further investigation into the stealer logs, the attackers could have uncovered a contact number for the company’s help desk, where John is employed. Seizing this opportunity, they could have impersonated John during a phone call. John, inexperienced in technical matters, might have said, “I can’t access my account. I urgently need to fill out a form and send it to the CEO. I forgot my phone at home and can’t get the code. I need help urgently! Send the code to this phone or deactivate it. The CEO’s may fire me.”

If the IT department could not have verified that the person on the phone was not John, they would have inadvertently disclosed personal information to the attackers. However, their highly cybersecurity-aware staff, armed with knowledge about social engineering, would have made a pivotal decision. They would have informed John that they could not assist him without written approval from the CEO and that disclosing account information or making changes in this manner was strictly prohibited.
At this point, thanks to our knowledgeable staff, the attackers would have been compelled to seek a different way.
Jane Doe, a Cyber Security Engineer, suggested to her manager a month ago, “Let’s consider implementing SOCRadar Extended Threat Intelligence to enhance the risk assessment of our employee domain accounts in response to leaks reported via our UEBA (User Entity Behavior Analytics) product. We could have established a rule, and whenever an action was taken against a staff member with a high-risk score, our SOAR (Security Orchestration Automation and Response) product would have generated an alert.” Nevertheless, her manager had responded, “There is no budget for that at the moment.” Jane might have suggested, “We could have allocated this (security) to next year’s procurement budget.”
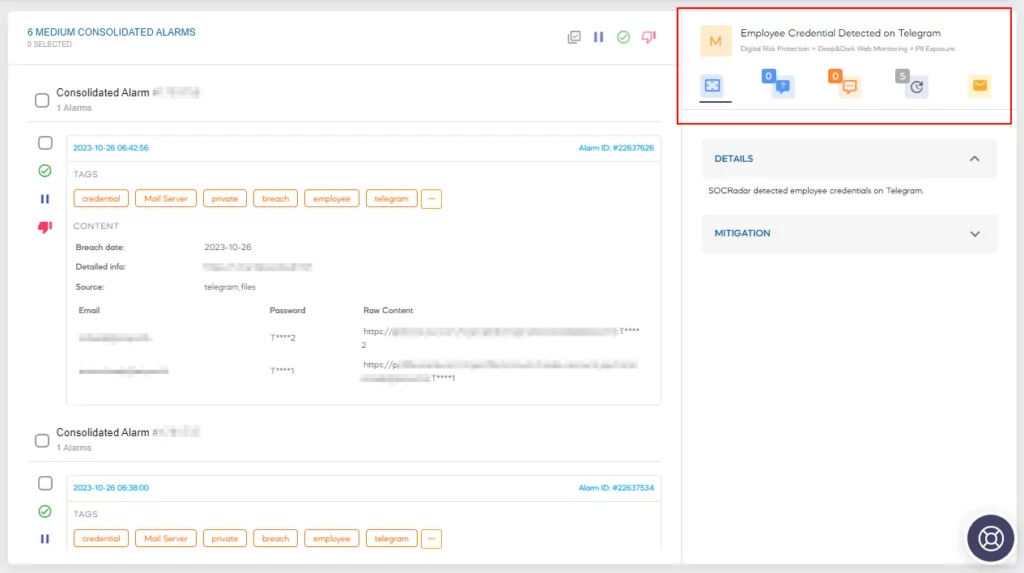
UEBA (User and Entity Behavior Analytics) products oversee and analyze the conduct of users and other entities (e.g., devices and applications). They achieve this by recognizing typical behavioral patterns and identifying security threats and risks by detecting anomalous behavior. Consequently, organizations can proactively detect potential security breaches and take appropriate measures.
By integrating employee leak reports from SOCRadar with SOAR, Jane could have enhanced the risk assessment of the leaked user within the UEBA system. Since users with high-risk scores are more susceptible to unusual activities than low-risk users, the rules established for such activities could have more effectively detected lateral movements or infrequent brute force attacks designed to evade detection by security systems. This approach would have allowed the organization to stay one step ahead of potential attackers with the assistance of SOCRadar.
Taking Advantage of John’s Password Pattern
In this scenario, potential actions that could have been taken, or might have been taken, can be outlined as follows:
Recent studies indicated that many individuals utilize identical passwords across various accounts. Even in cases where individuals do change their passwords, they often include symbols such as “*” or “!” or append a single number to the end. This slight alteration renders a password, which may have already been compromised by state-stealing malware, easily recognizable in less than a second.
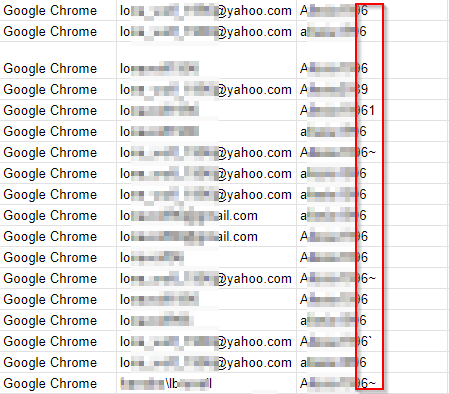
Unfortunately, John commits the same error in this instance. The attackers could have extracted John’s password profile, as illustrated below. They could have observed that he frequently adjusted his passwords by adding specific symbols or numbers. At the bottom of the page, they could have seen the domain account associated with the company where John was employed. Given that John was accessing company accounts from his personal computer, the attackers could have established a pattern based on John’s most frequently used passwords. For example, upon noticing that John’s passwords typically consisted of ‘Password1!’ or ‘Password1*’, they could have recorded the root word ‘Password1’ in a file. Armed with this information, the attackers could have created a new list of potential passwords using the CUPP (Common User Passwords Profiler) tool. Subsequently, they could have initiated a brute force attack by employing John the Ripper.
However, it should be noted that a significant amount of time had elapsed since the attackers’ attempts, prompting John’s company to heed Jane’s advice and implement the SOCRadar Extended Threat Intelligence product. Following the report of a security breach involving John’s account information, Acme Casino could have updated its password policy. This update would have automatically changed John’s password, necessitating that he select a new one during his next login. Consequently, the attackers would not have gained access to the account because John would have logged in again and modified his password.
John’s company might have integrated SOCRadar into its Security Orchestration, Automation, and Response (SOAR) system. Reports regarding account breaches from SOCRadar could have automatically adjusted the risk score associated with John’s account in the User and Entity Behavior Analytics (UEBA) product. A dedicated alarm for users with elevated risk scores could have detected the attackers’ incorrect password attempts based on a predefined rule and generated an alert. Analysts could have identified the IP addresses of the attackers and taken appropriate measures. In this case, the CEO would have convened John and Jane, expressing gratitude for their vigilance and willingness to adapt to advancing technology.
Social Engineering Prevention Methods
In the complex world of cybersecurity, the records produced by stealer malware serve as silent evidence of cybercrime activities. These records can expose individuals to threats, such as identity theft and social engineering attacks. The stories we’ve explored highlight the need for proactive vigilance in the face of these dangers.
- Early Awareness and Preventative Measures
Organizations must be promptly informed when someone falls victim to a stealer malware attack. Real-time detection is crucial, allowing institutions to respond quickly and reduce potential harm. Detecting a breach early can distinguish between a minor security incident and a significant data breach.
- Maintaining Separate Identities: Work and Personal
The most important lesson to be learned from these situations is that employees should keep their work and personal identities separate online and offline. Individuals should not use their work passwords or work-related information in their personal lives, such as username and password. This separation can act as a strong defense, preventing the leakage of sensitive corporate data into personal spheres and vice versa.
- SOCRadar’s Role in Proactive Defense
As a sign of our commitment to cybersecurity, SOCRadar Extended Threat Intelligence actively monitors our clients’ corporate identities in underground forums and the logs of stealer malware. This tracking allows organizations to develop proactive defenses against social engineering attacks and prepare for potential threats. You can schedule a demo via the contact form quickly.
- The Value of Early Alerts
Our proactive notifications enable companies to closely watch individuals at risk and take necessary precautions. Through User and Entity Behavior Analytics (UEBA) solutions, organizations can increase user risk scores, prompting IT personnel to be more vigilant. These early warnings can effectively deter and prevent potential threats.
- Revising Password Policies
Lastly, organizations should reconsider their password policies. Discouraging the reuse of old passwords and encouraging strong, unique passwords can significantly enhance security. Passwords should never be stored in unencrypted, public, or easily accessible locations, and corporate passwords should never be kept in private safes.
Conclusion
In conclusion, as the world of cybersecurity continues to evolve, so must our defense strategies. By emphasizing the criticality of timely awareness, employee awareness, and proactive defense mechanisms, we can collectively strengthen our resilience against the relentless ingenuity of cyber adversaries. Through these measures, we can safeguard our organizations and the integrity of our digital identities.
This research highlights the importance of strong passwords and that clever social manipulators can use even small personal details to their advantage. The constantly changing field of cybersecurity demands that we stay alert and take proactive steps to defend against threats that make it hard to distinguish between real communication and harmful intentions.
Suppose you need more information about what information stealers can disclose and how to protect yourself. In that case, you can read our past research on Stealer malware logs, “Snapshot of 70 Million Stealer Logs“.



































