
Microsoft Exchange Server Cyberattack Timeline
Microsoft Exchange Server is a mail calendaring server developed by Microsoft. Microsoft Exchange is considered an essential goal for hackers to control business networks because it provides an exclusive field that could allow attackers to operate many tasks. Therefore, several nation-state groups have attacked Microsoft Exchange in the past.
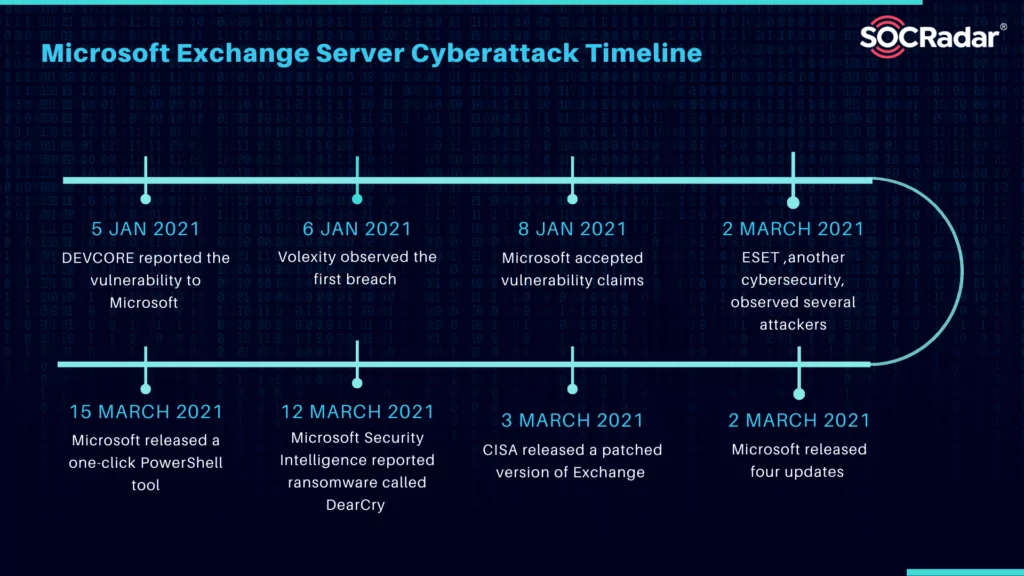
Global cyberattacks and data breaches were noticed in Microsoft exchange servers in January 2021. These cyberattacks and data breaches caused attackers to fully access user emails and passwords on servers and administrators’ privileges and connect to devices on the same network. Security testing company DEVCORE reported the vulnerability to Microsoft on 5 January 2021. Then, Microsoft accepted this claim on 8 January. Microsoft has reported the following vulnerabilities attackers use to gain access to victim systems.
Significant Microsoft Exchange Server Breaches
Cybersecurity company Volexity observed the first breach of a Microsoft Exchange Server on 6 January 2021. Volexity discovered that a breach in the server caused attackers to spy on two of their customers and reported this case to Microsoft. On 2 March 2021, ESET, another cybersecurity company, stated that they were observing several attackers, including Hafnium, that caused vulnerabilities to the server. Wired noticed that the vulnerability was patched, and many more attackers headed to reverse engineer to exploit still-vulnerable servers. After using these vulnerabilities to gain initial access, malicious actors distributed web shells on the compromised server.
The Actor Behind These Attacks
The Hafnium, a Chinese state-sponsored hacking group, perpetrated the attacks. Microsoft described Hafnium as “a highly skilled and sophisticated actor” that has targeted chiefly entities in the United States to stole data from several industry sectors, law firms, education institutions, defense contractors, policy think tanks, and NGOs. Attackers download a backdoor that enables them to access affected servers. 250.000 servers mainly belong to 30.000 organizations in the United States, and 7000 servers in the United Kingdom are affected by cyberattacks. On 19 July 2021, in a joint statement, the U.S., U.K., E.U., NATO, and other Western nations blamed the Ministry of State Security (MSS) for committing the Exchange breach and other cyberattacks.
Hackers utilized four vulnerabilities from Microsoft Exchange servers by accessing victims’ whole servers and networks besides emails and calendar invitations. The attacker uses two exploits; the first enables the attacker to connect to the server and falsely authenticate as a standard user. In this way, a second vulnerability can be exploited by increasing access to administrator privileges. These two exploits authorize attackers to upload code that automatically runs with these administrator privileges to a server in any location. Attackers utilize this to download a web shell by providing a backdoor to the restricted server. Small businesses, local institutions, and local governments are primary victims of cyberattacks since they have smaller budgets for security against cyber threats.
How did the Cyberattack Evolve?
When attackers hack Microsoft Exchange, they give automatic commands to download all emails from servers and download users’ passwords and email addresses since Microsoft Exchange stores these unencrypted in memory. This vulnerability enables attackers to add backdoors to affected systems, access other systems in the same network that are non-exploitable, and install ransomware. Although the Exchange server was patched against the exploit, installed backdoors do not remove. If other backdoors and user accounts added by attackers are not removed, attackers continue to access the server.
Microsoft released 2010, 2013, 2016, and 2019 updates to patch the exploit on 2 March 2021. Four Microsoft Exchange Server versions (2010, 2013, 2016, and 2019) were considered sensitive to cyberattack, but vulnerable editions are not yet entirely determined. Cloud-based services such as Exchange Online and Office 365 are not affected by cyberattacks.
The Most Targeted Sectors and Countries
Hackers have exploited the vulnerabilities to spy by affecting approximately 250,000 servers. Targets of the attack are disease researchers, law offices, universities, defense contractors, non-governmental organizations, and think tanks.
Check Point Research has revealed that the most attacked country with 17% of all exploit attempts is the United States. Followed by Germany with 6%, the United Kingdom and the Netherlands at 5%, and Russia with 4% of all exploits.
With 23% of exploit attempts, the most targeted sector is government/military, followed by manufacturing at 15%, banking and financial services at 14%, software vendors with 7%, and healthcare at 6%.
Attackers Used Social Engineering Tactics
Attackers were realized by downloading all emails belonging to particular users connected to Microsoft Exchange servers. Washington think tanks announced that attackers sent persuasive emails in a social engineering attack that stimulated recipients to click on a link. On 11 March 2021, Norway’s parliament announced that it was the attack victim, stating that threat actors had extracted its data. Also, The European Banking Authority was targeted in the attack.
On 12 March 2021, Microsoft Security Intelligence reported ransomware called DearCry that distributing on the servers by encrypting device contents and making servers unusable. After that, DearCry demanded payment to recover files, but according to Microsoft, no guarantee that paying the ransom will get you access to your files.
How Did Microsoft Exchange Server Attacks End?
On 2 March 2021, the Microsoft Security Response Center (MSRC) announced the Common Vulnerabilities and Exposures (CVE) release to the public; thus, it encouraged its clients to patch their Exchange server to overcome several significant vulnerabilities. On 15 March, Microsoft released a one-click PowerShell tool, The Exchange On-Premises Mitigation Tool, to rescue its servers by running a malware scan to detect installed web shells and remove threats. However, this is a temporary measure not as it does not install other available updates.
3 March 2021, an emergency directive that forced government networks to update to a patched version of Exchange was released by the U.S. Cybersecurity and Infrastructure Security Agency (CISA). In July of 2021, the government of Biden formally accused China of a cyber attack.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.


































