
Overview of the Australian Notifiable Data Breaches Report (H1 2024)
In September 2024, the Office of the Australian Information Commissioner (OAIC) released its most recent Notifiable Data Breaches (NDB) report, covering the first half of the year.
So far in 2024, there is a significant rise in data breach notifications, with 527 incidents recorded – an increase of 9% compared to the second half of 2023. This surge highlights the ongoing challenge of protecting personal information in an increasingly digital world, as reliance on technology grows and so do the risks of cyber threats.

OAIC published the latest Notifiable Data Breaches (NDB) report in September 2024
The report delineates key trends, emphasizing that cybersecurity incidents remain the dominant cause of data breaches. These incidents include phishing attacks, ransomware, and compromised credentials. Alarmingly, one breach alone affected over 10 million Australians, while the health sector, government entities, and financial services are some of the most affected industries.
Key Themes from the Report
The H1 2024 Notifiable Data Breaches (NDB) Report by OAIC identifies several critical areas where organizations must focus to improve their data security practices.
One of the core themes is the need for proactive cybersecurity measures to reduce the occurrence of breaches. The Notifiable Data Breaches (NDB) report stresses that organizations should manage supplier risks more effectively and address the significant role human errors, also known as insider threats, play in breaches. Additionally, it highlights the shared responsibility for securing cloud-based data and urges entities not to downplay breach notifications based on assumptions about the threat actor’s intent.
Lastly, the report emphasizes the strategic regulatory approach adopted by the OAIC. While entities are not automatically penalized for breaches, they are expected to take reasonable steps to safeguard personal information, as required under the Privacy Act 1988. This includes complying with the Australian Privacy Principles (APPs) and addressing systemic privacy risks when identified.
Notably, the Medibank ransomware incident, a major 2022 breach impacting 9.7 million Australians, continues to shape regulatory responses. The OAIC initiated civil penalty proceedings against Medibank, alleging failures in implementing adequate security measures – a reminder of the increasing scrutiny on data privacy practices across industries.
Moving forward, we will outline the report’s key themes, share critical statistics, and discuss insights that will illuminate the current state of the landscape and shape the future.
1. 38% of Data Breaches Result from Cyber Incidents
To tackle the growing threat of cyberattacks, organizations need to be proactive, especially since 38% of all data breaches (and 57% of malicious attacks) in H1 2024 are caused by cybersecurity incidents.
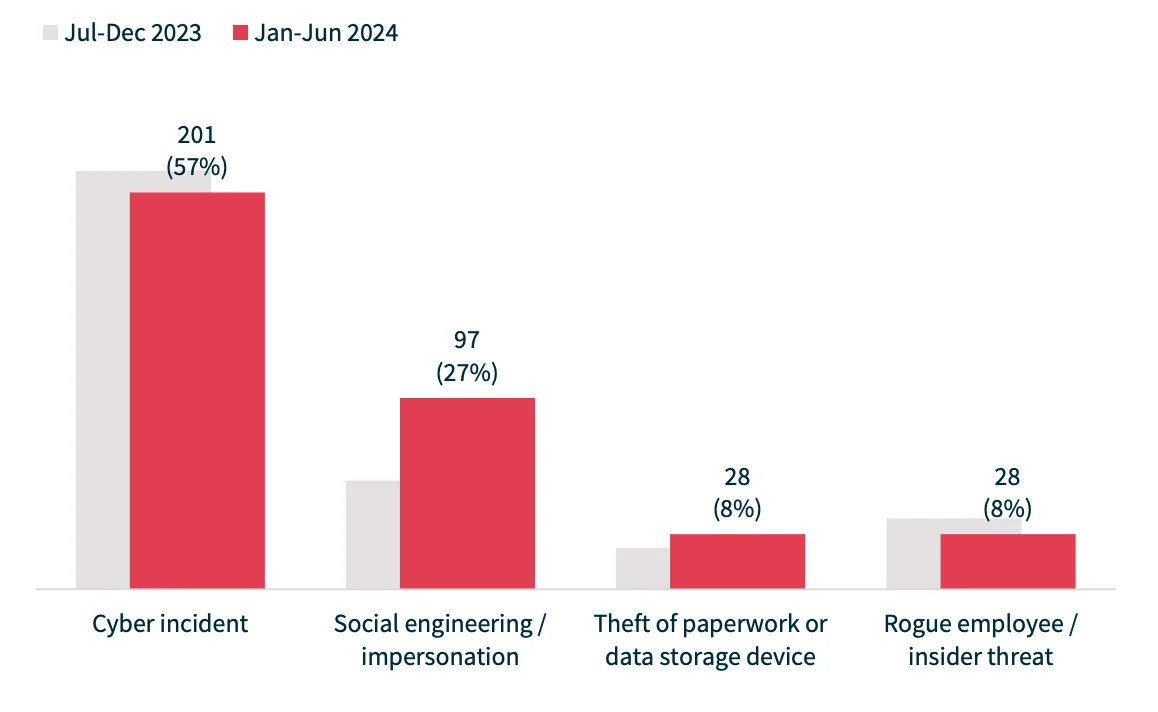
In H1 2024, cyber incidents constituted 57% of malicious or criminal attacks, followed by social engineering/impersonation attacks at 27%. (Statistics by H1 2024 NDB Report)
One of the key steps recommended by the OAIC is implementing Multi-Factor Authentication (MFA), ideally using phishing-resistant methods to guard against credential theft. Where MFA isn’t available, enforcing strong password policies, such as making passwords complex and preventing their reuse, is essential.
It’s also critical to layer security measures to avoid relying on a single defense. This means that if one protection fails, others can still keep systems secure. Managing access is another vital practice. Employees should only have access to what they need for their roles, and higher-privileged accounts should be regularly reviewed to prevent misuse.
Monitoring for suspicious activity is just as important. Detecting and responding to threats early can make all the difference in minimizing damage. The OAIC suggests aligning with well-established frameworks like the Australian Signals Directorate’s Essential Eight and the NIST Cybersecurity Framework to strengthen defenses.
Finally, embracing a “privacy by design” mindset, where security is built into every step of handling information, helps ensure that organizations stay protected in the face of future cyber risks.
SOCRadar’s Breach Datasets offer detailed, searchable records of known data breaches, enabling organizations to quickly identify if they’ve been affected. With access to this extensive database, organizations can assess the severity of a breach and take immediate action to mitigate its impact, ensuring no time is wasted in addressing security gaps.
SOCRadar’s Breach Datasets module search page
2. Multi-Party Supply Chain Breaches, Reported by 34 Entities
The OAIC report highlights the growing risks of outsourcing personal data handling to third-party suppliers, especially in light of recent breaches like those involving MediSecure and Outabox. Supply chain breaches often impact multiple entities, leading to numerous notifications for the same incident. According to the latest Notifiable Data Breaches (NDB) Report, 34 such cases were recorded during H1 2024.
The OAIC took proactive steps, engaging with 35 entities affected by multi-party breaches to ensure they complied with the Notifiable Data Breaches (NDB) scheme. These incidents illustrate that risks extend beyond direct suppliers into broader supply chains, making vigilance essential at every level. Notification delays were also a common issue, further worsening the impact of breaches when affected individuals weren’t informed in a timely manner.
Examples from the Notifiable Data Breaches (NDB) report show how vulnerable supply chains can be:
- In one case, a subcontracted developer’s compromised laptop gave unauthorized access to a legacy database, leading to sensitive data being sold on the dark web.
- Another incident involved a cloud service provider experiencing a breach over several days, and the entity couldn’t confirm the extent of the data compromised due to poor data management practices.
To manage these risks, organizations must implement robust supplier risk management frameworks, evaluate suppliers’ security controls before engagement, and conduct regular cybersecurity audits of third-party providers. This ensures compliance with security standards and legal obligations. The report stresses that addressing supply chain risks early in procurement processes and maintaining constant oversight of third-party relationships is crucial to mitigating potential breaches.
When dealing with supply chain breaches, it’s important to have complete visibility into your third-party providers and their potential risks. SOCRadar’s Supply Chain Intelligence provides real-time insights into your supplier network, ensuring you remain informed about potential exposures affecting third-party providers. This feature goes beyond basic monitoring, offering a detailed view of interconnected risks, such as weak security practices or known breaches within your supply chain.
SOCRadar’s Supply Chain Intelligence
3. Human Error Accounts for 30% of Breaches
The Notifiable Data Breaches (NDB) report emphasizes the critical role human error plays in data breaches, accounting for 30% of all incidents during the reporting period. This is often due to mistakes like sending personal information to the wrong recipient, with 60 notifications linked to this issue. Also notably, 12% were the result of phishing, where employees unknowingly clicked on malicious links or downloaded harmful attachments, while 5% involved insider threats or rogue employees.
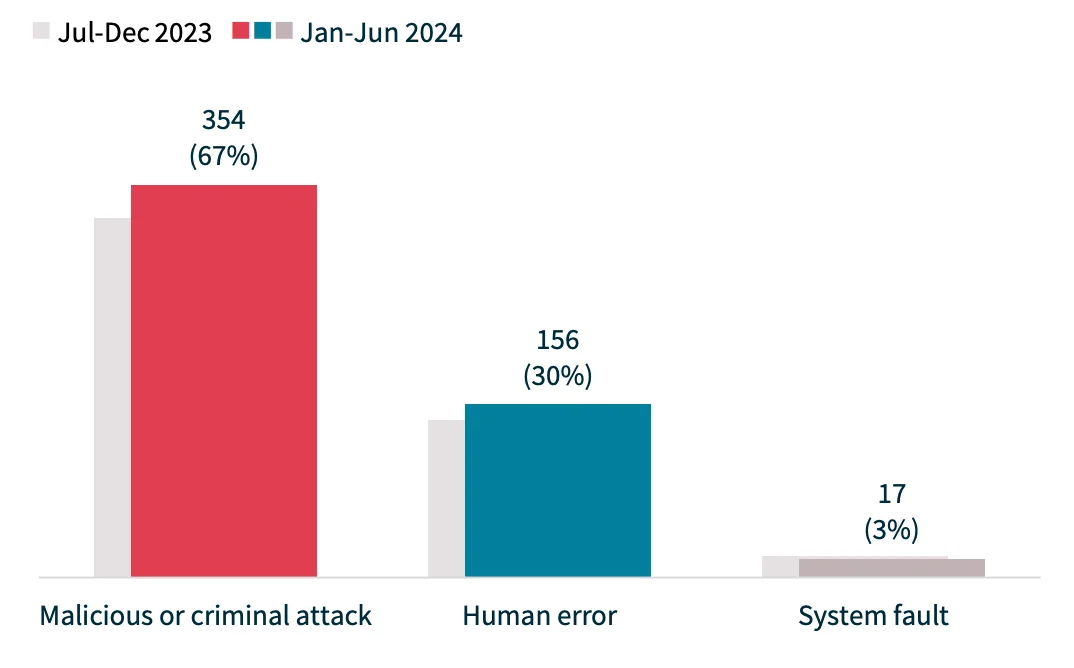
Malicious attacks continue to dominate the sources of breaches, accounting for 67% of incidents, while human errors account for 30%, and system faults for only 3% (Statistics from H1 2024 NDB Report)
These examples show how human factors can weaken even the most secure systems:
- One illustrative case involved a health service provider where a former employee accessed and disclosed the personal information of over 20,000 individuals for financial gain. In response, the organization enhanced monitoring capabilities to spot unusual access patterns.
- In another case, an employee fell victim to a QR code phishing (quishing) attack, which compromised their email and bypassed multi-factor authentication. The company responded by increasing cybersecurity training and implementing stronger defenses against phishing.
To mitigate the human factor in breaches, the OAIC recommends a combination of technical measures and employee education. This includes regular training sessions focused on secure data handling and evolving phishing techniques, limiting access to sensitive data based on roles, and proactively monitoring for suspicious activity. OAIC urges organizations to design systems that anticipate human error and to foster a culture of privacy and security awareness. By doing so, organizations can significantly reduce the likelihood of breaches caused by human mistakes.
SOCRadar LABS offers free tools like Phishing Radar for quick phishing attack detection. Our AI-powered Digital Risk Protection platform scans millions of domains, alerting you to malicious registrations and suspicious activities in real time.
Phishing Radar service on SOCRadar LABS
4. Misconfigured Cloud Settings as a Major Breach Risk
The Notifiable Data Breaches (NDB) report highlights the growing risks around misconfiguration of cloud-based data holdings, stressing that while cloud computing can improve security, protecting personal information is a shared responsibility between the cloud service provider and the entity using the service.
Misconfigurations are a common cause of breaches, often leaving sensitive data vulnerable to unauthorized access or public exposure due to human error:
- One key example mentioned in the report involved an organization that mistakenly set a cloud storage bucket to public instead of private, exposing customer documents until a cybersecurity researcher notified them.
- Similarly, a health service provider faced a breach when an employee inadvertently changed security settings, making sensitive information publicly accessible.
While system faults only made up 3% of breaches, misconfigurations such as unintended data exposure were a significant contributor to data breaches.
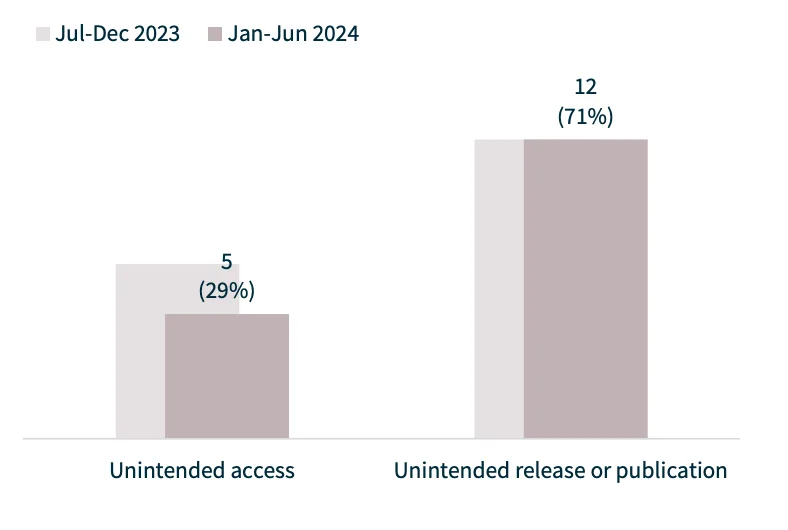
71% of system fault notifications involved the unintended release of publication of data (Statistics by H1 2024 NDB Report)
To prevent such incidents, OAIC recommends organizations implement strong access controls, such as multi-factor authentication and encryption, to safeguard cloud environments. It’s also essential to establish clear policies and procedures for managing cloud data storage and regularly conduct security assessments to audit cloud configurations for compliance with security standards.
Misconfigurations often go unnoticed until it’s too late. SOCRadar’s Attack Surface Management provides continuous visibility over your cloud assets, alerting you to potential risks like exposed data or misconfigurations before they become a breach. SOCRadar’s Alarms provide real-time alerts on security incidents, helping organizations respond faster and prevent further damage.
SOCRadar’s Attack Surface Management, Digital Footprint
For additional recent insights on cloud security, visit the SOCRadar blog: Top 50 Cloud Statistics in 2024 (Essential Insights on Investments, Breaches, Misconfigurations, and More).
5. Trusting Threat Actors’ Motivation Doesn’t Prevent Harm
The OAIC report stresses the importance of not relying on a threat actor’s motivation when assessing data breaches, particularly in ransomware cases where some entities believed paying a ransom would prevent further harm.
According to the Notifiable Data Breaches (NDB) Report, phishing and ransomware remained the top causes of cyber incidents in H1 2024, with phishing accounting for 31% of malicious attacks, and ransomware for 24%.
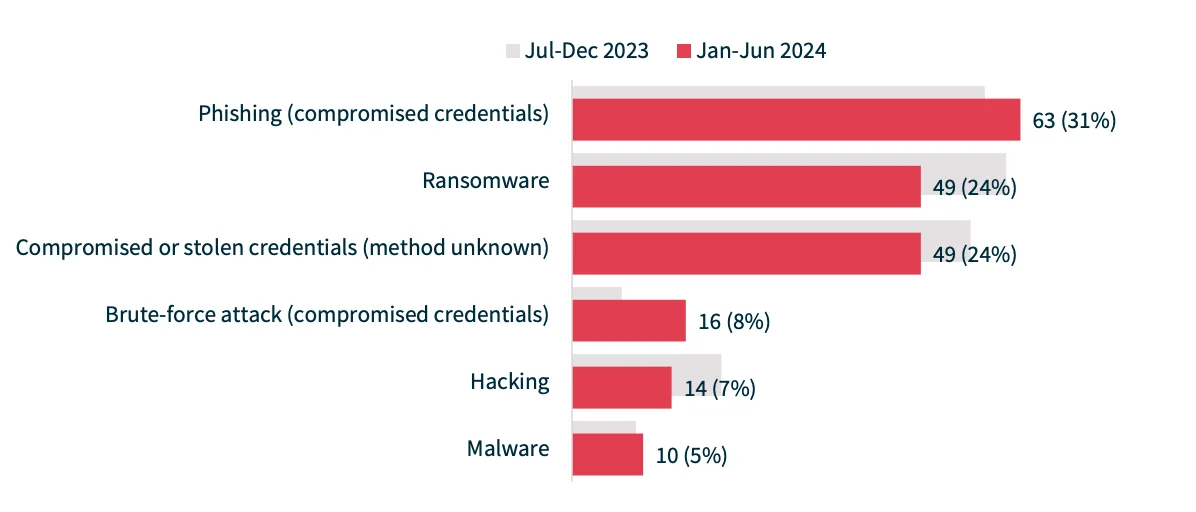
Breakdown of cyber incident types (Statistics by H1 2024 NDB Report)
The OAIC warns against making decisions based on attackers’ claims, urging entities to consider all factors when evaluating potential harm.
For example:
- A rogue employee accessed personal data but claimed no malicious intent. The entity chose not to notify individuals, assuming no harm, but the OAIC found the risk of harm increased due to the employee’s relationship with those affected.
- In another case, an entity paid a ransom, believing it mitigated the breach, but the OAIC reminded that paying ransoms doesn’t guarantee data recovery or stop further misuse.
The OAIC advises organizations to prioritize transparency and notify affected individuals when warranted, rather than relying on the motivations or promises of threat actors. This ensures a thorough and responsible breach assessment process.
With threats like ransomware and phishing at the forefront, organizations can benefit from SOCRadar’s Threat Actor Intelligence module, which monitors and provides detailed insights on threat actors, malware, and campaigns targeting your organization, sector, or country, helping to stay ahead of potential attacks. With SOCRadar’s Threat Actor Tracking feature, you can easily detect attackers’ footprints, find out their tactics, as well as access critical Indicators of Compromise (IOCs).
SOCRadar’s Threat Actor Intelligence module
6. Australian Government Reports 63 Breaches, Notification Delays Exceed 30 Days
The final key theme in the Notifiable Data Breaches (NDB) report focuses on the data breaches within the Australian Government, underscoring the pressing need for public agencies to lead by example in safeguarding personal information.
Unlike private companies, individuals have no choice but to provide their data to access essential government services, making it a must that these agencies uphold the highest standards of data protection.
During the reporting period:
- The breaches reported by the Australian Government (63) represent 12% of all notifications, marking it as the second most breached sector.
- A notable vulnerability was social engineering, with 42% of incidents involving impersonation, where threat actors posed as customers to gain unauthorized access to sensitive information.
- Alarmingly, 78% of breach notifications were delayed by over 30 days, often due to slow escalation processes within government agencies.
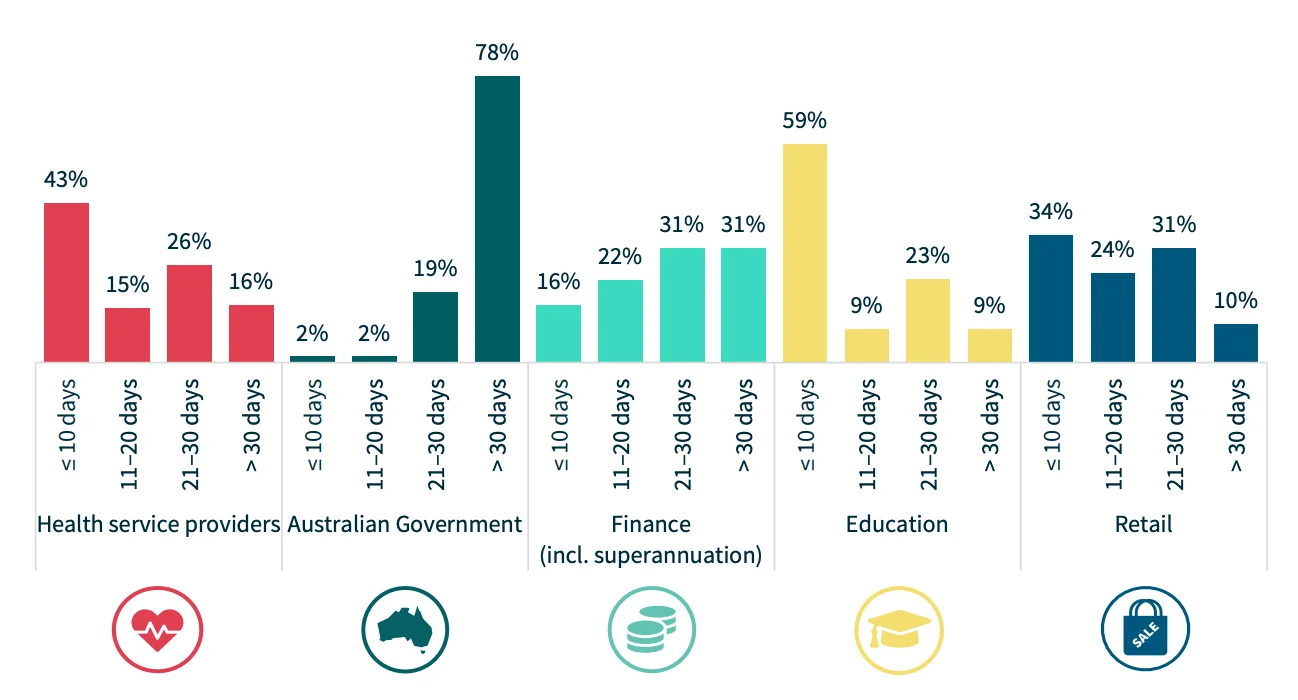
Time taken for each industry to notify breaches (Statistics by H1 2024 NDB Report)
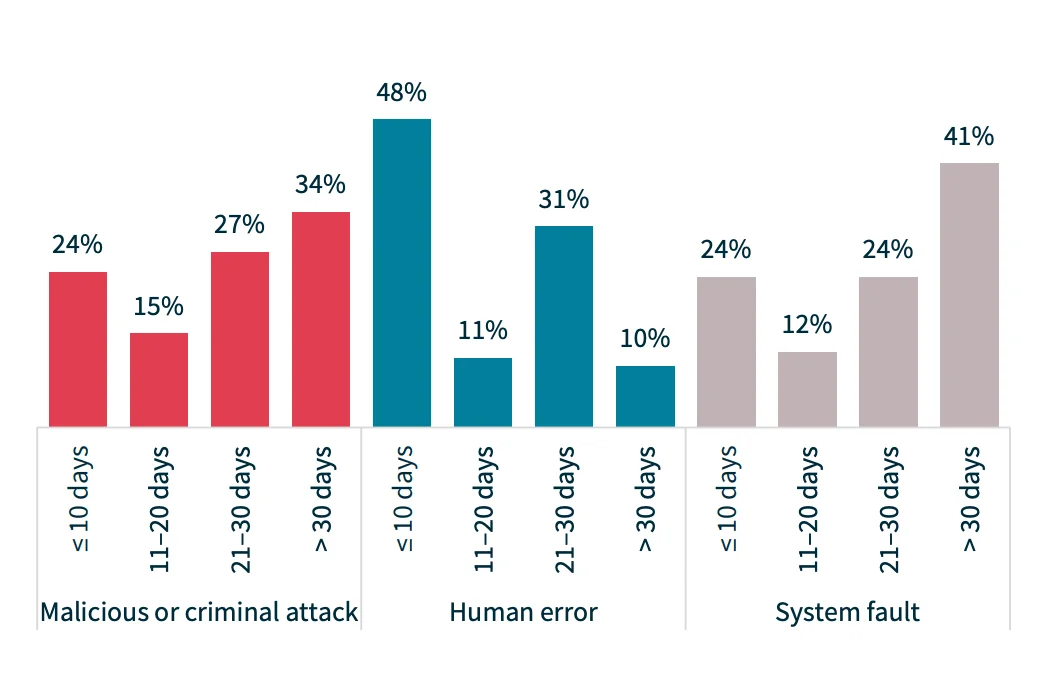
Time taken to notify the OAIC of breaches, by sources such as malicious attack, human error, and system fault (Statistics by H1 2024 NDB Report)
The OAIC recommends that government agencies update their breach response plans and ensure all departments are well-versed in promptly identifying, assessing, and notifying relevant parties about data breaches.
Ultimately, strengthening security practices is essential, and to improve security, the OAIC strongly recommends Multi-Factor Authentication (MFA). This approach adds layers of protection by requiring:
- Something you know (a password or PIN),
- Something you have (a token or smartcard),
- Something you are (biometrics such as a fingerprint or facial recognition).
A Breakdown of 2024 Data Breaches Across Top 5 Industries
The Australian Notifiable Data Breaches (NDB) Report of H1 2024 also provides a closer look at how different sectors are impacted. Each industry faces unique challenges in managing and protecting personal information, and the report’s findings make it clear that no sector is immune.
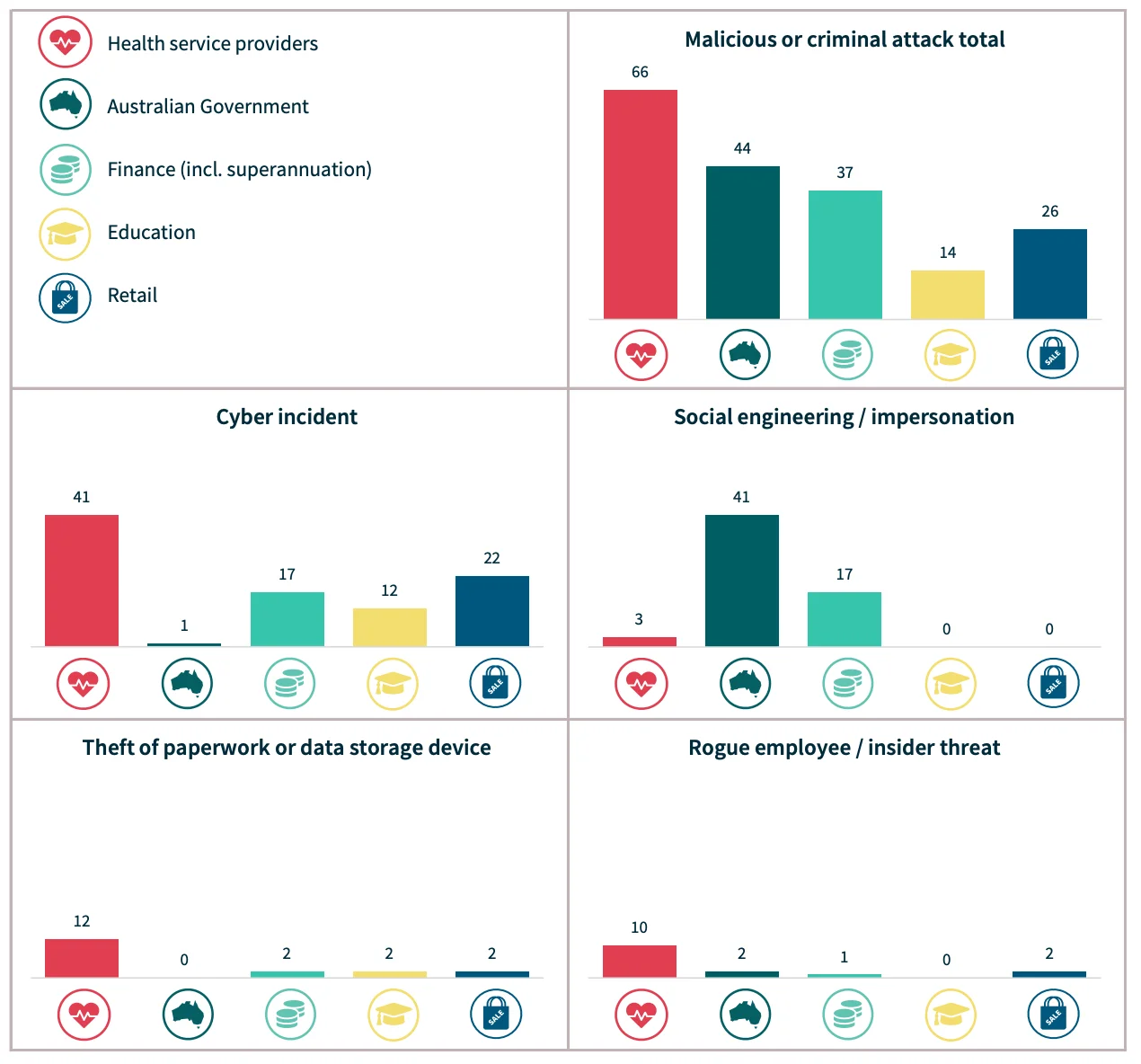
Malicious/criminal attacks breakdown for the top 5 sectors: Health service providers, Australian Government, Finance, Education, and Retail (Statistics by H1 2024 NDB Report)
Health service providers emerged as the most affected, receiving 102 breach notifications between January and June 2024. The Australian government followed with 63 notifications, while the finance sector reported 58. These numbers highlight where vulnerabilities are most concentrated.
Zooming in on malicious attacks, health services also led with 66 total incidents, largely driven by 41 cyber attacks. The Australian government was hit by 44 attacks, primarily involving social engineering and impersonation. Meanwhile, the finance sector saw 17 social engineering cases and 12 cyber incidents.
Interestingly, the retail sector experienced 22 cyber incidents, despite having fewer overall notifications, while theft of physical data was more common in health services, with 12 incidents involving paperwork or data storage devices.
These insights underscore that sectors like health and government remain prime targets across multiple attack vectors, making proactive data protection critical for these industries.
For detailed insights into the latest threats across industries, access free, instant Industry Threat Landscape Reports through SOCRadar LABS.
Conclusion
The January – July 2024 Notifiable Data Breaches Report (NDB) by the Office of the Australian Information Commissioner (OAIC) highlights the growing cybersecurity challenges, faced by both public and private sectors.
With 527 data breach notifications reported and 38% linked to cyber incidents in the first half of the year, the health and government sectors were the hardest hit, facing numerous malicious attacks.
This report shows that breaches can occur anywhere, making it essential for organizations to adopt practical, proactive steps, such as multi-factor authentication and improved supply chain security, to better protect sensitive data and reduce their vulnerability to attacks





































