
Top 10 Free Cybersecurity Solutions for SMB
Cybersecurity technologies are now necessary for all types and sizes of organizations, not just enterprises. Since threat actors no longer target just the largest companies, everyone must have effective solutions and a thorough cybersecurity strategy. Whether a company has an in-house security team or outsources these services, it needs cybersecurity professionals to identify and address any vulnerabilities in computer systems. This fact may have a negative impact on the bottom line, but fortunately, a variety of free cybersecurity technologies are accessible.
Here is a list of some free vulnerability identification tools that cybersecurity pros use daily.
1. Aircrack-ng

Aircrack-ng, a suite of wireless security tools that focuses on various areas of Wi-Fi security and may be used for Wi-Fi penetration testing, must be included on any list of the finest free tools for cybersecurity experts.
This collection of tools can record, analyze, and export packet data, impersonate access points or routers, and decipher complex Wi-Fi passwords. The Aircrack-ng suite of tools consists of Airdecap-ng (decrypts WEP or WPA-encrypted capture files), Airodump-ng (packet sniffer), Airtun-ng (creates virtual tunnel interfaces), and Packetforge-ng (creates encrypted packets for injection).
2. Burp Suite
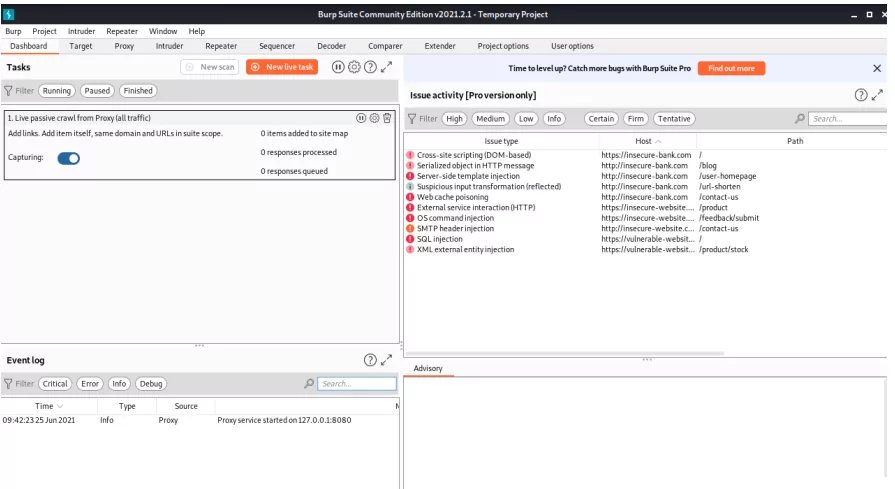
Burp is a high-tech collection of cybersecurity tools for debugging and testing the security of online applications. Burp Suite consists of a spider for exploring web application content, a randomization tool for testing session tokens, and an advanced request repeater for resending altered requests.
The true strength of Burp Suite is the proxy intercepting tool, which allows Burp to intercept, analyze, change, and transfer browser-to-target communication.
This capability makes it easy to assess the attack vectors of a web application from all aspects, which is a fundamental reason why it is often regarded as one of the top free cyber security tools.
A commercial edition of Burp Suite for corporate customers and a free community version.
3. SOCRadar Free Edition
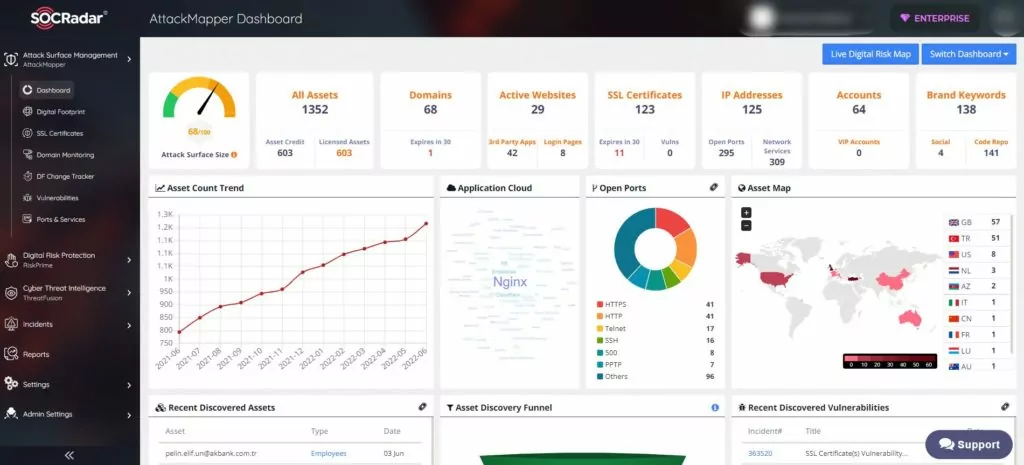
SOCRadar Free Edition is a platform-as-a-service with a maximum of two users per organization. The entire list of features is as follows:
- Digital Footprint Identification
- Basic Incident Alerting
- Basic Exam of Compromised Credentials
- Monitoring of Fraudulent/Phishing Domains
- IP Monitoring
The only required input information is the primary domain address of your organization. SOCRadar detects your internet-facing digital assets, including domains, IP addresses, SSL certificates, websites, employee email addresses, network services, and apps, within an hour of subscribing to the platform.
4. Wireshark
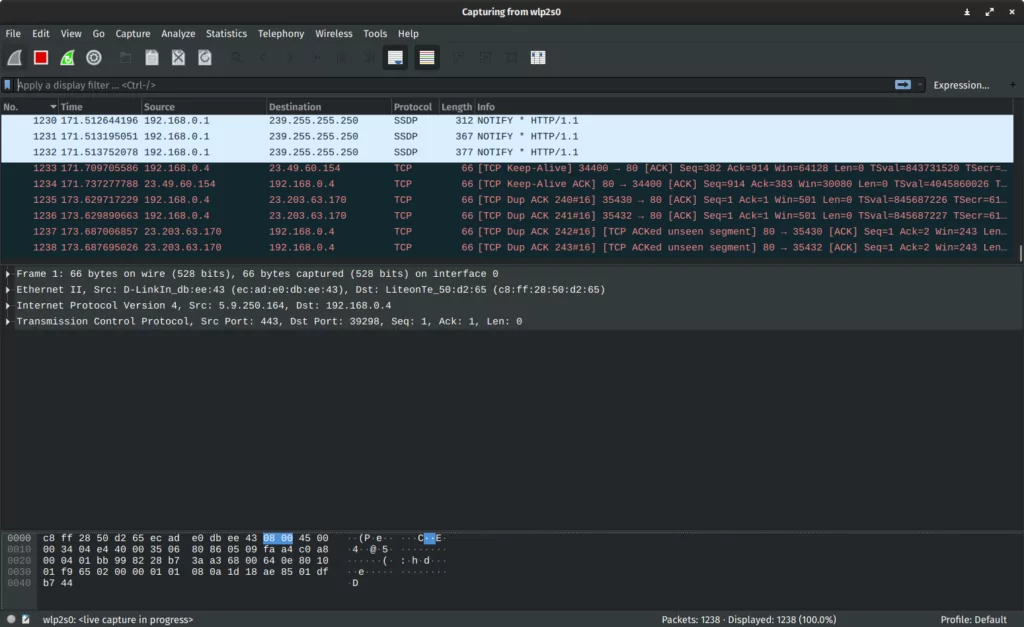
Wireshark captures data packets traversing a network and displays them in a human-readable format for the end user. It enables users to collect data using Ethernet, Wi-Fi, Npcap adaptor, Bluetooth, and token ring, among others.
5. Nmap

Nmap, also known as Network Mapper, is used for penetration testing and security audits since it uses NSE scripts to find network service vulnerabilities, misconfigurations, and security concerns. It may be used by network administrators to manage network inventories, service update timetables, and uptime monitoring.
It functions by mapping networks and ports before a security audit begins so that it may then utilize scripts to identify any identifiable security issues. The application collects raw data and then identifies the host type, operating system (OS), and all available hosts on the network.
It operates on Linux, Windows, and macOS X and is meant to scan big networks, while it may also be used to monitor individual servers.
6. Metasploit Framework
There is no better free tool than the open-source Metasploit software, which automates vulnerability and penetration testing for scanning networks and apps for faults and weaknesses. Metasploit framework, which is now owned by the security firm Rapid7, can test computer system vulnerabilities and breach into remote computers. In other words, it is a network penetration “Swiss Army knife” used by ethical hackers and criminal gangs to locate a system’s weak areas. Both free and paid versions are available (known as the Pro edition).
The framework comes with over 2,000 exploits and over 592 payloads to assist users in executing well-planned attacks. Metasploit is pre-installed on Kali Linux.
7. OpenVAS
OpenVAS is an all-inclusive vulnerability scanner with many modules that make it simple for cybersecurity experts to test for security vulnerabilities, misconfigured systems, and obsolete software. A significant portion of the program’s effectiveness derives from its built-in programming interface, which allows developers to design specialized scans.
OpenVAS is offered free as open-source software under the GNU General Public License, and the business that maintains it also offers a premium version for corporate customers who want extra product support.
8. AlienVault

The worldwide intelligence community uses Open Threat Exchange as a neighborhood monitor. AlienVault allows commercial enterprises, independent researchers in the area of security, and government agencies to openly collaborate and exchange the most recent information about new threats, malicious actors, and more, enhancing community-wide security.
9. Security Onion
Security Onion consists of three components: a comprehensive packet capture function, intrusion detection systems that correlate host-based events with network-based events, and a large number of additional toolkits, including Snort, Bro, Sguil, and Suricata.
If you want to set up a Network Security Monitoring (NSM) platform quickly and simply, Security Onion is the best option.
It does not support Wi-Fi for network management and does not automatically back up settings beyond rules.
10. Snort
Snort is a network intrusion prevention and intrusion detection system that is open source and capable of real-time traffic analysis and recording. It employs a set of rules to recognize malicious network behavior, locate the packets, and create alarms.
This Cisco-managed packet sniffer actively scans and analyzes networks to identify probes, assaults, and intrusions. Snort combines a packet sniffer, a packet logger, and an intrusion detection engine into a single package.



































