
Top Critical Vulnerabilities Used by Ransomware Groups
As ransomware attacks have grown in popularity recently, researchers have begun compiling an easy-to-follow list of vulnerabilities exploited by ransomware groups. So organizations would be aware of which security flaws ransomware gangs use to gain initial access when breaching a network. This article will discuss the latest analysis of Ransomware Groups’ Vulnerabilities.
What is Ransomware?
Ransomware is software that may encrypt all of your data or prevent you from using your computer. Once the ransomware has been installed on your computer, it will demand a ransom — often in cryptocurrency — to decrypt your data or unlock your machine.
Types of Ransomware Attacks
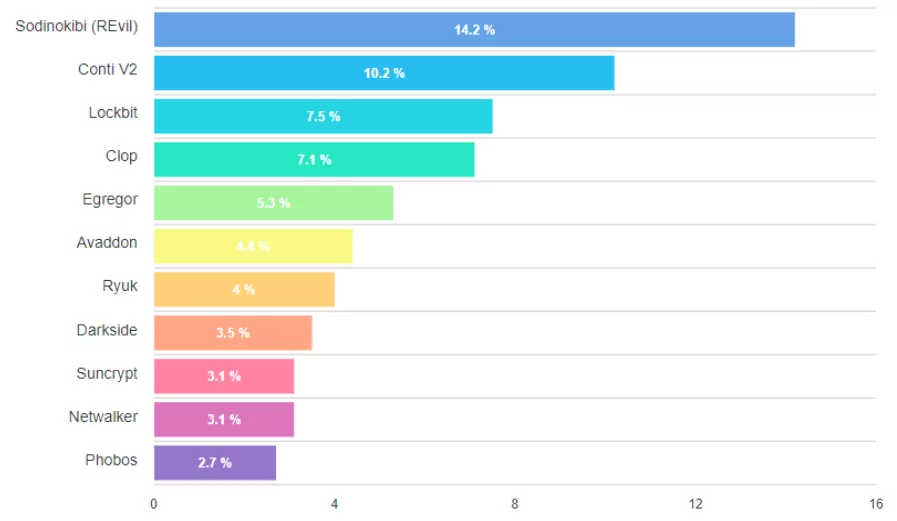
There are many types of ransomware, and with new ransomware threats developing regularly, it may be challenging to track them all. These are the most often reported ransomware families, according to recent information from cybersecurity company Coveware.
Ransomware as a Service
Ransomware–as–a–service (or RaaS) is a variant of the software-as-a-service (SaaS) business model. A ransomware organization licenses its ransomware program for another party or affiliate use.
The ransomware gangs that empower their virus often pocket most extortion money. However, some more active ransomware gangs, such as the Netwalker group, may take as little as 20% of the ransom, with affiliates receiving 80% of the money.
Experts’ Vulnerabilities List on Twitter
The member of Recorded Future’s CSIRT Allan Liska led to the idea and publicized his proposal on compiling a list of ransomware gangs’ exploited vulnerabilities.
Numerous people have begun to assist Allan Liska with his endeavor. The extensive in-progress list currently contains vulnerabilities that have been exploited in the past or are actively being targeted.
The list is organized diagrammatic, with brief descriptions of each vulnerability.

The Short Overview of Vulnerabilities Exploited by Ransomware Groups
- CVE-2021–0604 (SharePoint): A remote code execution vulnerability exists in Microsoft SharePoint when the software fails to check the source markup of an application package, aka ‘Microsoft SharePoint Remote Code Execution Vulnerability.
- CVE-2021–38647 (Microsoft Azure): Open Management Infrastructure Remote Code Execution Vulnerability
- CVE-2021–26084 (Atlassian): In affected versions of Confluence Server and Data Center, an OGNL injection vulnerability exists that would allow an unauthenticated attacker to execute arbitrary code on a Confluence Server or Data Center instance. The affected versions are before version 6.13.23, from version 6.14.0 before 7.4.11, from version 7.5.0 before 7.11.6, and from version 7.12.0 before 7.12.5.
- CVE-2021–31166 (Microsoft Windows): HTTP Protocol Stack Remote Code Execution Vulnerability
- CVE-2021–22893 (Pulse Secure VPN): Pulse Connect Secure 9.0R3/9.1R1 and higher is vulnerable to an authentication bypass vulnerability exposed by the Windows File Share Browser and Pulse Secure Collaboration features of Pulse Connect Secure that can allow an unauthenticated user to perform remote arbitrary code execution on the Pulse Connect Secure gateway. This vulnerability has been exploited in the wild.
- CVE-2018–13379: Cring ransomware encrypted Fortinet VPN equipment using the aforementioned unpatched vulnerability. This followed the FBI and CISA’s warning that fraudsters were scanning Fortinet devices for susceptible ones.
Which Vulnerabilities are Being Exploited by Conti and its Affiliates?
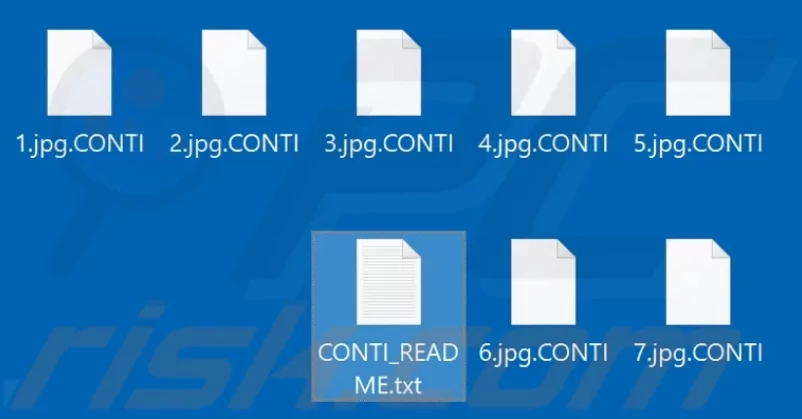
Conti is a kind of ransomware. Infected systems’ data is encrypted, and users are demanded to pay a ransom for decryption tools/software. All impacted files are appended with the “.CONTI” suffix during the encryption procedure.
For instance, after encryption, a file named “1.jpg” will display as “1.jpg.CONTI.” After the encryption procedure, the victim’s desktop is made with a text file (“CONTI README.txt”).
Decryption may be feasible if the malicious application is still under development and has weaknesses (flaws). In any event, you are strongly warned against engaging with and complying with cyber criminals’ demands. They cannot be trusted, and victims often do not obtain the promised decryption tools/software despite payment.
As a result, their information stays permanently protected, and they also suffer enormous financial losses. To prevent future encryption by Conti ransomware, you must delete CONTI ransomware from the operating system. However, this will not recover already encrypted data.
The only realistic option is to restore the system from a backup created before the infection and save it in a different place.
Conti has also been associated with the EXOTIC LILY set of initial access brokers (IABs). IABs primarily aim to gain harmful access to enterprises to sell such access to ransomware gangs and affiliates. However, ransomware attacks make extensive use of pre and post-authentication vulnerabilities.
As Tenable stated, Conti and its affiliates have started using the PrintNightmare and Zerologon vulnerabilities against targets as part of the disclosed affiliate playbook. However, ContiLeaks disclosed an additional 29 vulnerabilities that the gang exploited.
Additionally, there are indications that Conti and its affiliates exploited Fortinet FortiOS vulnerabilities detected in Fortinet’s SSL VPN devices to acquire initial access to target environments.
Conti and its associates exploit the following vulnerabilities:
Initial Access Vulnerabilities
|
CVE |
Description |
CVSS Score |
VPR |
|
Fortinet FortiOS Path Traversal/Arbitrary File Read Vulnerability |
9.8 |
9.8 |
|
|
Fortinet FortiOS Improper Access Control Vulnerability |
8.8 |
8.4 |
|
|
Windows SMBv3 Client/Server Remote Code Execution Vulnerability (“SMBGhost”) |
10 |
10.0 |
|
|
Windows Remote Desktop Gateway (RD Gateway) Remote Code Execution Vulnerability |
9.8 |
8.4 |
|
|
Microsoft Exchange Validation Key Remote Code Execution Vulnerability |
8.8 |
9.9 |
|
|
VMware vSphere Client Remote Code Execution Vulnerability |
9.8 |
9.5 |
|
|
VMware vSphere Client Remote Code Execution Vulnerability |
9.8 |
9.4 |
|
|
VMware vCenter Server Remote Code Execution Vulnerability |
9.8 |
9.6 |
|
|
Microsoft Exchange Server Remote Code Execution Vulnerability (“ProxyLogon”) |
9.8 |
9.9 |
Escalation of Privilege Vulnerabilities
|
CVE |
Description |
CVSS Score |
VPR |
|
Win32k Memory Corruption Elevation of Privilege Vulnerability |
6.9 |
9.6 |
|
|
Windows Win32k Elevation of Privilege Vulnerability |
7.8 |
9.7 |
|
|
Windows Elevation of Privilege Vulnerability |
7.8 |
9.7 |
|
|
Windows Win32k Elevation of Privilege Vulnerability |
7 |
9.8 |
|
|
Microsoft Windows Elevation of Privilege Vulnerability |
7.8 |
9.0 |
|
|
Windows Elevation of Privilege Vulnerability |
7.8 |
9.8 |
|
|
Windows Elevation of Privilege Vulnerability |
7.8 |
9.2 |
|
|
Windows Task Scheduler Elevation of Privilege Vulnerability |
7.8 |
9.0 |
|
|
Windows Elevation of Privilege Vulnerability |
7.8 |
8.9 |
|
|
Windows Elevation of Privilege Vulnerability |
7.8 |
6.7 |
|
|
Windows Elevation of Privilege Vulnerability |
7.8 |
9.5 |
|
|
Windows Elevation of Privilege Vulnerability |
7.8 |
9.7 |
|
|
Windows Error Reporting Manager Elevation of Privilege Vulnerability |
7.8 |
9.0 |
|
|
Microsoft Windows Elevation of Privilege Vulnerability |
7.8 |
9.0 |
|
|
Windows AppX Deployment Extensions Elevation of Privilege Vulnerability |
7.8 |
5.9 |
|
|
Windows Certificate Dialog Elevation of Privilege Vulnerability |
7.8 |
8.4 |
|
|
Windows UPnP Service Elevation of Privilege Vulnerability |
7.8 |
9.7 |
|
|
Win32k Elevation of Privilege Vulnerability |
7.8 |
9.7 |
|
|
Update Notification Manager Elevation of Privilege Vulnerability |
7.8 |
5.9 |
|
|
Windows Background Intelligent Transfer Service Elevation of Privilege Vulnerability |
7.8 |
9.7 |
|
|
Windows Netlogon Elevation of Privilege Vulnerability (“Zerologon”) |
10 |
10.0 |
|
|
Windows Print Spooler Remote Code Execution Vulnerability |
8.8 |
9.8 |
|
|
Windows Win32k Elevation of Privilege Vulnerability |
7.8 |
9.8 |
|
|
Windows Print Spooler Remote Code Execution Vulnerability (“PrintNightmare”) |
8.8 |
9.8 |
The Fight Against Ransomware
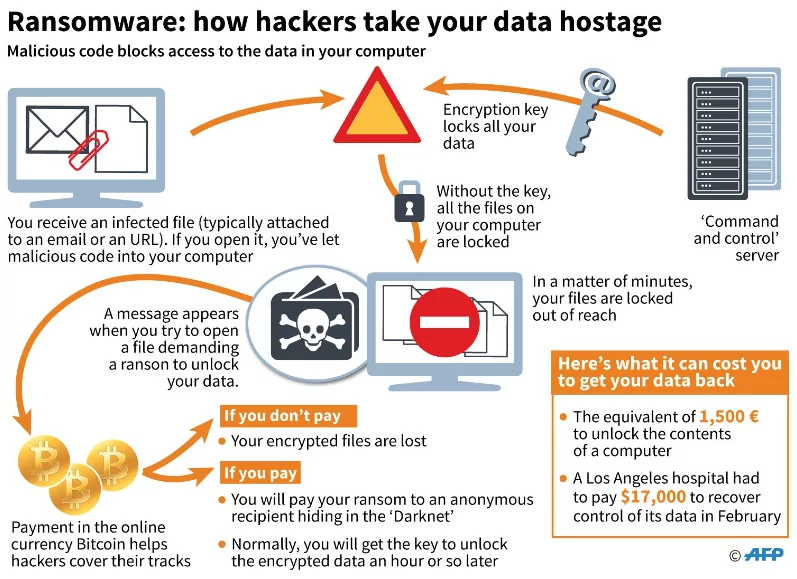
There are several instances where security measures may be used to thwart an assault. Combined, they provide a formidable defense that can defend you against a wide range of cyber security incidents, regardless of how they begin or the attacker’s eventual aim. Some of these restrictions may be straightforward for you to implement – for example, updating all your devices – while others may need assistance from an IT specialist.
Logging and alerting is a security feature that often arises along the journey. This is because detecting and investigating a security event is the first step in reacting to it. Effective logging and alerting are critical for your IT provider to identify an issue before it becomes too severe.
Initial Access
An attacker attempts to access your computer networks and systems during the first access phase. The most specific entry points for attackers are as follows:
- obtaining usernames and passwords for your computer’s login,
- exploiting flaws in internet-connected systems, such as email or remote access systems, and
- Distributed malware through malicious email attachments.
Increasing the difficulty of these approaches decreases the possibility that an attacker can access your machines and carry out their assault. The optimum time to avert an assault is before its onset. Here’s how to put an end to each of those techniques.
- Attackers get a valid username and password combinations via phishing or password guessing and then use that information to log in to systems such as email or remote access systems. To prevent an attacker from entering your remote access system, use lengthy, strong, unique passwords and enable two-factor authentication (2FA). This method significantly complicates an attacker’s access.
- Keeping all operating systems and applications up to date reduces the vulnerabilities an attacker may use to access your machines. You should identify any systems exposed to the internet and secure them; this may need assistance from an IT professional. Because attackers have a considerably easier time accessing internet-exposed systems, having your internet firewall prevent such access helps keep you secure.
- The third method attackers often use to transmit a document or spreadsheet that, when viewed, attempts to install malware on your machine without your knowledge. Stopping the assault at this stage is possible via contemporary endpoint security software; for instance, your IT provider may discuss the Endpoint Detection and Response (EDR) products they provide. This program takes the role of conventional anti-virus software and is more equipped to combat contemporary threats.
Consolidation and Preparation
The attacker will attempt to go from the original machine they infiltrated to gain administrator access to all computers and devices in your firm during this phase.
Taking control is how an attacker installs malware on a compromised machine. This enables them to keep access (for example, if the computer is restarted) and give instructions to the computer to access other network devices. Once again, EDR tools are one of the most effective defenses against assault.
Once the attacker has shown their capacity to take control and distribute further malware, they will attempt to broaden their access and get complete administrator access to all devices in your network. Securing administrative accounts and implementing network restrictions such as firewalls may help you prevent an attacker from moving from device to device. Limiting the attacker to a subset of your company devices may help reduce the harm and enable you to continue working if some devices are encrypted.
Impact on Target
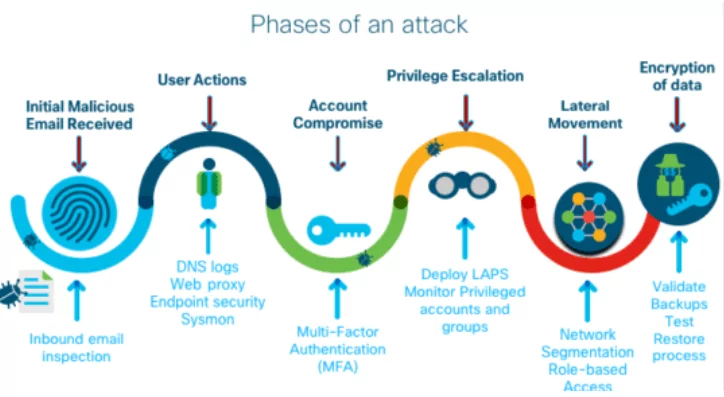
At this point, the attacker has obtained access to the various systems in your firm and is prepared to launch the attack’s most devastating phase.
Frequently, attackers will take essential data from your organization and demand money in exchange for not disclosing or selling the information.
Additionally, they destroy backup copies of your data and encrypt your data and systems to interrupt your operations.
If your network architecture (for example, firewall) has enough logging, you may be able to identify data being copied out of your network, which might indicate criminal activity.
Maintaining solid and validated backups is critical to restoring your company swiftly. These should be kept unplugged from your PCs and offline to prevent an attacker from deleting them; as essential as avoiding assaults is being prepared to recover from them if they occur. The most straightforward approach to prepare for a ransomware attack is to create an incident response plan that details what to do if anything goes wrong and your computers stop operating. Maintain a paper copy of this document beside important contacts so that you may refer to it even if your company documents are encrypted.



































