Weekly Vulnerability Summary by CISA: Android, Microsoft, CMS Software, WordPress, Perl, and More
The Cybersecurity and Infrastructure Security Agency (CISA) has released a summary of the most recent vulnerabilities. Although the latest Vulnerability Summary by CISA has been released for the week of December 4, it covers the period from December 1 to December 9, 2023 based on the vulnerability publish dates.
With this blog post, we will dive into CISA weekly Vulnerability Summary and draw attention to significant high-severity vulnerabilities, emphasizing their potential impact on organizations.
In this overview of the weekly CISA Vulnerability Summary, we will explore instances such as Android, which grapples with numerous privilege escalation vulnerabilities. Microsoft Azure RTOS products face multiple vulnerabilities, while PrestaShop encounters yet another SQL injection vulnerability. New vulnerabilities also surface in WordPress plugins, and specific CMS (Content Management System) software. Alongside these, various other security concerns contribute to the complexity of the current landscape.
Android (by Google)
Several critical vulnerabilities have been discovered, impacting Android devices. These include privilege escalation vulnerabilities, a buffer overflow, an out-of-bounds write, and a memory corruption vulnerability, most with a CVSS score of 9.8. Additionally, two high-severity vulnerabilities (CVE-2023-40087 and CVE-2023-40088) have scores of 8.8.
Further details are available for two of the critical vulnerabilities:
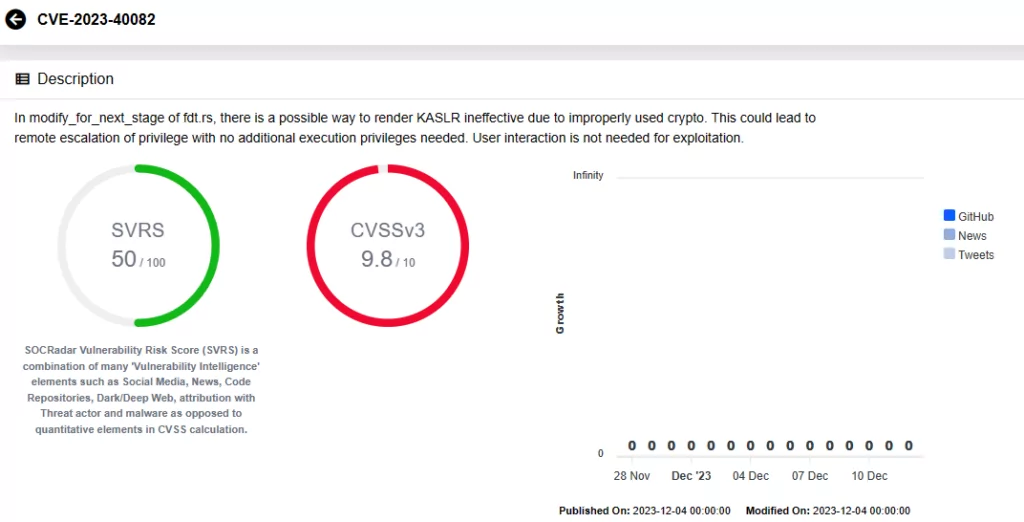
CVE-2023-40078: An out-of-bounds write due to a heap buffer overflow, resulting in potential escalation of privilege for paired devices without additional execution privileges. Exploitation does not require user interaction.
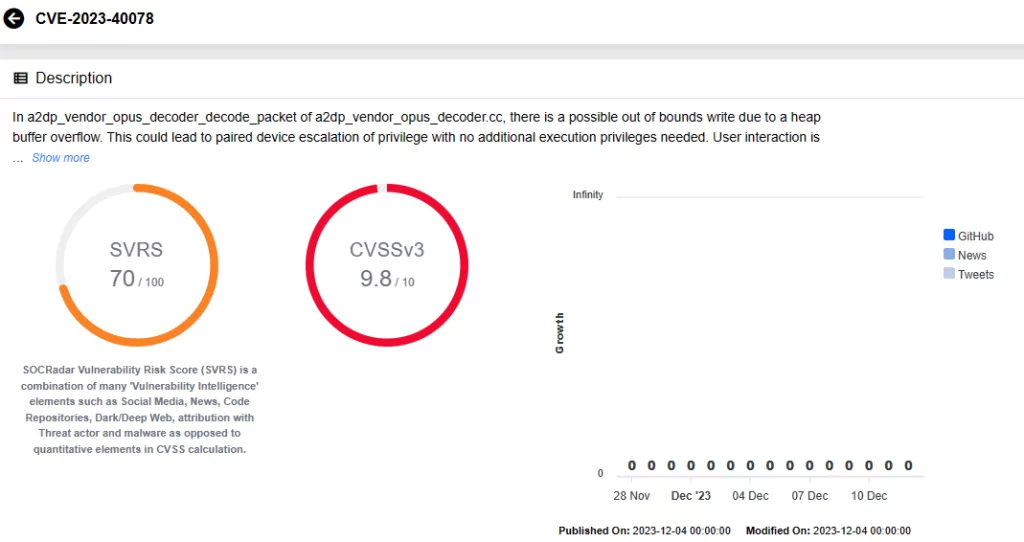
CVE-2023-40082: In modify_for_next_stage of fdt.rs, improper crypto usage may render KASLR ineffective, potentially leading to remote escalation of privilege without additional execution privileges. Exploitation does not require user interaction.
Details for the high-severity vulnerabilities are as follows:
CVE-2023-40087: An out-of-bounds write due to a missing bounds check, resulting in potential escalation of privilege for paired devices without additional execution privileges. Exploitation does not require user interaction.
CVE-2023-40088: The callback_thread_event of com_android_bluetooth_btservice_AdapterService.cpp may experience memory corruption due to use-after-free, potentially leading to Remote Code Execution (RCE) without additional execution privileges. Exploitation does not require user interaction.
The privilege escalation vulnerabilities listed as part of the latest Android updates include:
- CVE-2023-21162
- CVE-2023-21163
- CVE-2023-21164
- CVE-2023-21166
- CVE-2023-21215
- CVE-2023-21216
- CVE-2023-21217
- CVE-2023-21218
- CVE-2023-21228
- CVE-2023-21263
- CVE-2023-21401
- CVE-2023-21402
- CVE-2023-21403
- CVE-2023-35690
Microsoft
During the recent week, vulnerabilities associated with Microsoft have emerged, impacting products such as Azure RTOS NetX Duo, ThreadX, and USBX, all possessing severity scores of 9.8.
The Microsoft vulnerabilities, found in Azure RTOS v6.2.1 and below, have been addressed in the Azure RTOS NetX Duo, ThreadX, and USBX release 6.3.0.
Users are strongly advised to upgrade, as no known workarounds exist for these vulnerabilities.
Azure RTOS NetX Duo:
Azure RTOS NetX Duo, a TCP/IP network stack, tailored for deeply embedded real-time and IoT applications, faces the following vulnerabilities:
CVE-2023-48315: Allows an attacker to execute remote code due to memory overflow vulnerabilities in processes/functions related to FTP and SNTP.
CVE-2023-48316: Enables remote code execution through memory overflow vulnerabilities in processes/functions related to SNMP, SMTP, FTP, and DTLS.
CVE-2023-48691: Allows an attacker to perform an out-of-bounds write, leading to remote code execution, in processes related to the IGMP protocol.
CVE-2023-48692: Enables remote code execution due to memory overflow vulnerabilities in processes/functions related to ICMP, TCP, SNMP, DHCP, NAT, and FTP.
Azure RTOS ThreadX:
Azure RTOS ThreadX, an advanced Real-Time Operating System for deeply embedded applications, exhibits the following vulnerability:
CVE-2023-48693: Permits arbitrary read and write, potentially leading to privilege escalation, due to a vulnerability in the parameter checking mechanism.
Azure RTOS USBX:
Azure RTOS USBX, an embedded stack integrated with Azure RTOS ThreadX, faces the following vulnerabilities:
CVE-2023-48694: Allows remote code execution due to expired pointer dereference and type confusion vulnerabilities in functions/processes related to device linked classes, ASIX, Prolific, SWAR, audio, CDC ECM.
CVE-2023-48695: Permits remote code execution through out-of-bounds write vulnerabilities in functions/processes related to CDC ECM and RNDIS in host and device classes.
CVE-2023-48696: Enables remote code execution due to expired pointer dereference vulnerabilities in components of the host class related to CDC ACM.
CVE-2023-48697: Allows remote code execution due to memory buffer and pointer vulnerabilities in functions/processes related to PIMA, storage, CDC ACM, ECM, audio, hub, in pictbridge and host class.
Additionally, another identified vulnerability is CVE-2023-35618, an Elevation of Privilege vulnerability affecting Microsoft Edge with a CVSS score of 9.6.
WordPress
High-severity vulnerabilities have surfaced in various WordPress plugins:
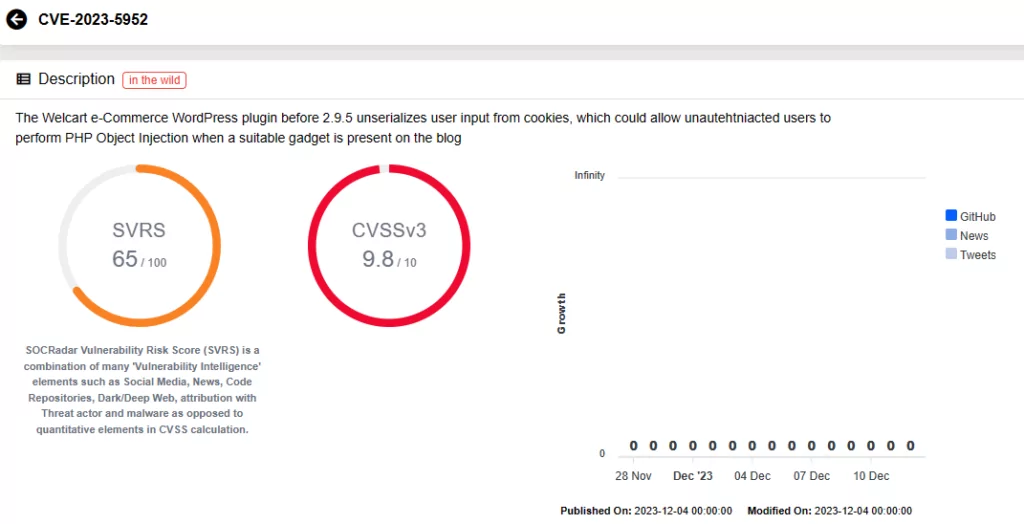
CVE-2023-5952 (CVSS Score: 9.8): The Welcart e-Commerce WordPress plugin, version 2.9.5 and earlier, mishandles user input from cookies, potentially allowing unauthenticated users to execute PHP Object Injection if a suitable gadget is present on the blog.
There is also a high-severity vulnerability (CVSS: 8.8) affecting the same plugin and version, tracked as CVE-2023-5953. This vulnerability arises from the absence of file validation for uploads, along with lacking authorization and CSRF in an AJAX action handling such uploads. As a result, authenticated users can upload arbitrary files, such as PHP, onto the server.
CVE-2023-5762 (CVSS Score: 8.8): The Filr WordPress plugin, version 1.2.3.6 and earlier, is susceptible to a Remote Code Execution (RCE) vulnerability. This flaw permits the execution of commands by the operating system, leading to a complete server compromise on behalf of a user with Author-level privileges.
Vulnerabilities Arise in CMS Software: JFinalCMS and October CMS
JFinalCMS, a Content Management System (CMS) software, exhibits a series of high-severity vulnerabilities (CVSS: 8.8) that can result in Cross-Site Request Forgery (CSRF) through various components. These vulnerabilities are identified in JFinalCMS v5.0.0, and the CVE identifiers for these issues are as follows:
- CVE-2023-49372
- CVE-2023-49373
- CVE-2023-49374
- CVE-2023-49375
- CVE-2023-49376
- CVE-2023-49377
- CVE-2023-49378
- CVE-2023-49379
- CVE-2023-49380
- CVE-2023-49381
- CVE-2023-49382
- CVE-2023-49383
- CVE-2023-49395
- CVE-2023-49396
- CVE-2023-49397
- CVE-2023-49398
- CVE-2023-49446
- CVE-2023-49447
- CVE-2023-49448
A vulnerability was also identified within another CMS software, named October.
CVE-2023-44382 (CVSS Score 9.1): An authenticated backend user possessing the editor.cms_pages, editor.cms_layouts, or editor.cms_partials permissions, who would typically be restricted from supplying PHP code for execution by the CMS due to the enabled cms.safe_mode, can circumvent this restriction by writing specific Twig code. This allows the user to escape the Twig sandbox and execute arbitrary PHP. This issue has been addressed in version 3.4.15.
Several Tenda Firmware Series Are Susceptible to Command Injection Vulnerabilities
Tenda firmware, series AX12, AX3, AX9, and W30E, in respective versions of V22.03.01.46, V16.03.12.11, V22.03.01.46, and V16.01.0.12(4843), are vulnerable to several stack overflow vulnerabilities, and vulnerabilities that lead to command injection and execution. All of the vulnerabilities are critical, with CVSS scores of 9.8.
Tenda AX12 V22.03.01.46:
- CVE-2023-49424
- CVE-2023-49425
- CVE-2023-49426
- CVE-2023-49428
- CVE-2023-49437
Tenda AX3:
- CVE-2023-49408
- CVE-2023-49409
Tenda AX9:
- CVE-2023-49429
- CVE-2023-49430
- CVE-2023-49431
- CVE-2023-49432
- CVE-2023-49433
- CVE-2023-49434
- CVE-2023-49435
- CVE-2023-49436
Notably, one of these vulnerabilities involves SQL command injection:
CVE-2023-49429: Tenda AX9 V22.03.01.46 contains an SQL command injection vulnerability in the ‘setDeviceInfo’ feature through the ‘mac’ parameter at /goform/setModules.
Tenda W30E:
- CVE-2023-49402
- CVE-2023-49403
- CVE-2023-49404
- CVE-2023-49405
- CVE-2023-49406
- CVE-2023-49410
- CVE-2023-49411
- CVE-2023-49999
- CVE-2023-50000
- CVE-2023-50001
- CVE-2023-50002
ArslanSoft
ArslanSoft’s Education Portal, prior to version 1.1, harbors two critical vulnerabilities, each with a CVSS score of 9.8. One of these vulnerabilities, identified as CVE-2023-5634, results in SQL injection due to Improper Neutralization of Special Elements. The second vulnerability, denoted as CVE-2023-5636, leads to command injection due to Unrestricted Upload of Files with Dangerous Types.
Other ArslanSoft vulnerabilities, also high-severity issues, have been highlighted in the weekly Vulnerability Summary by CISA in previous weeks.
Perl
CVE-2023-47100 (CVSS Score: 9.8): In Perl versions before 5.38.2, the S_parse_uniprop_string function in regcomp.c is susceptible to writing to unallocated space. This vulnerability arises due to mishandling a property name associated with a p{…} regular expression construct. The earliest affected version is 5.30.0.
PrestaShop
CVE-2023-46353 (CVSS Score: 9.8): The module “Product Tag Icons Pro” (ticons) before version 1.8.4 from MyPresta.eu for PrestaShop is vulnerable to SQL injection. In a specific method, sensitive SQL calls can be executed with a simple HTTP call, allowing exploitation.
TinyDir
CVE-2023-49287 (CVSS Score: 9.8): TinyDir, a lightweight C directory and file reader, was exposed to buffer overflows in the tinydir_file_open() function. This vulnerability has been addressed in version 1.2.6.
You can visit the weekly Vulnerability Summary by CISA through this link to review all the other vulnerabilities.
Elevate Your Security Defenses with SOCRadar’s Advanced Vulnerability Management Suite
Take command of your cybersecurity strategy with SOCRadar’s Vulnerability Management solutions. Leverage the Attack Surface Management (ASM) module to actively monitor emerging vulnerabilities across your digital assets, receiving timely threat alerts and streamlining your patching efforts.
Dive deeper into the realm of cybersecurity with our Vulnerability Intelligence feature, providing real-time updates, invaluable insights into hacker trends associated with identified vulnerabilities, and detailed information, including the SOCRadar Vulnerability Risk Score (SVRS), which offers a better understanding on vulnerability popularity and the potential for exploitation.