
What is BEC Attack and How to Prevent it?
BEC attack is a type of social engineering attack that takes place over email and the attacker aims for financial gain. Often, attackers aim to trick employees into sending money or valuable personal data (PII) to them by pretending to make a legitimate request from a compromised email account, an email account impersonating an employee/manager, or a stakeholder.
As defined in FBI reports, BEC Attack has four stages, independent of its type.
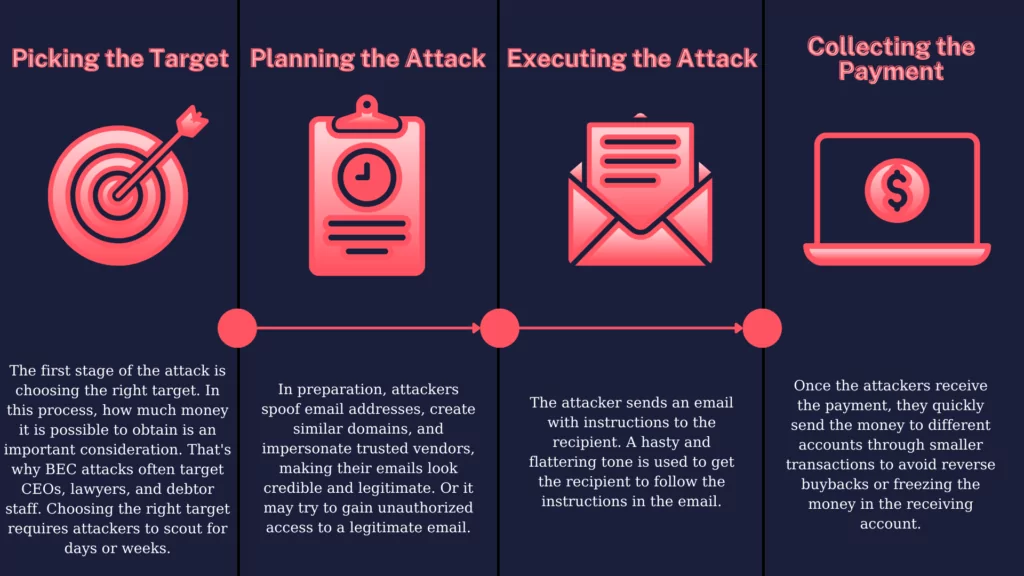
Types of BEC Attack
CEO Fraud
The attackers pose as the manager of the target firm and demand that an employee with authority manage the financial operation send him money. Usually, in the content of such emails, a few sentences go through with pleasant thoughts about the money needing to be sent soon and the employee for whom the money is requested.
Email Account Compromise (EAC)
EAC covers various tactics attackers use to gain unauthorized access to the employee account. After gaining unauthorized access, the attacker can do many harmful actions such as using sensitive data, distributing ransomware, and social engineering for fake money transfers, using a legitimate source. In BEC, an email scam is from a fake source, while in EAC, it is from a legitimate source.
EAC specifically includes techniques that hackers use to gain unauthorized access to a legitimate email account. Most BEC attacks are from compromised email accounts. Although the EAC and BEC are fundamentally different, the FBI has shown these two types of crimes together in its reports since 2017, as the attackers often carry out these two attacks together.
False Invoice Scheme
This attack often begins with the breach of the email address of an employee authorized to manage companies’ finances. When the attacker finds a legitimate invoice in this email account, they make some changes, such as changing the number of the account to which the money will be deposited. The attacker then sends the manipulated invoice to the firm, allowing the money to be transferred to their own account.
Attorney Impersonation (Impersonating Lawyer)
By posing as a lawyer or any representative of a law firm or by gaining unauthorized access to their accounts, attackers seek to transfer funds to their own accounts. The target companies preferred in these attacks are usually at the litigation stage or have experienced a situation in the past where they had to pay. The targeted employees are those who do not have the knowledge to question the validity of this money transfer request.
One of the biggest dangers in this attack is the perception that lawyers and law firms have a right to ask for answers to personal questions. When attackers impersonate lawyers, they can use this perception to force employees to disclose information that needs to be protected. Scams can start with a professional-looking email or with a phone call.
Most Popular Attack for Financial Gain – BEC
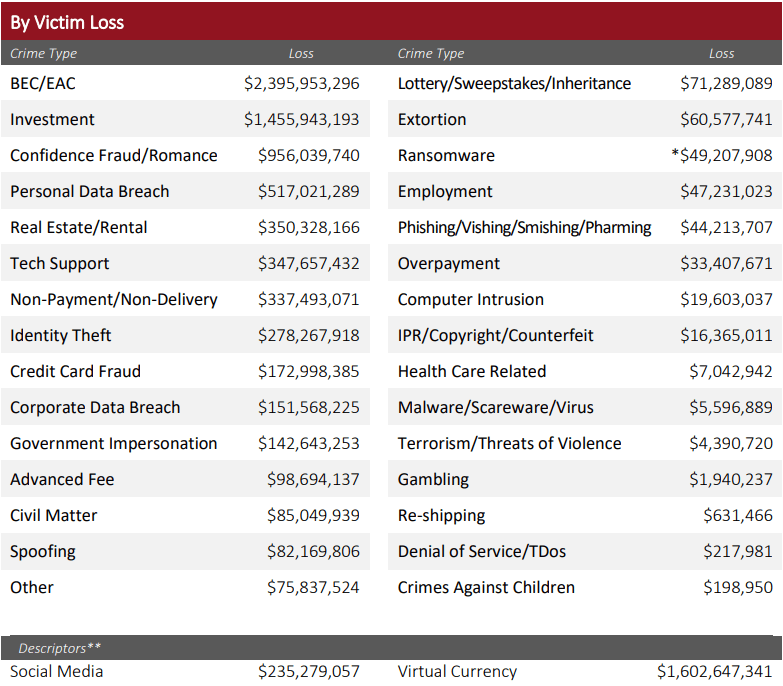
The FBI reported receiving 19,954 complaints for 2021, causing $2.4B damage. According to the data, it ranks first among attacks regarding financial loss, the ninth most preferred type of attack among crime types in 2021.
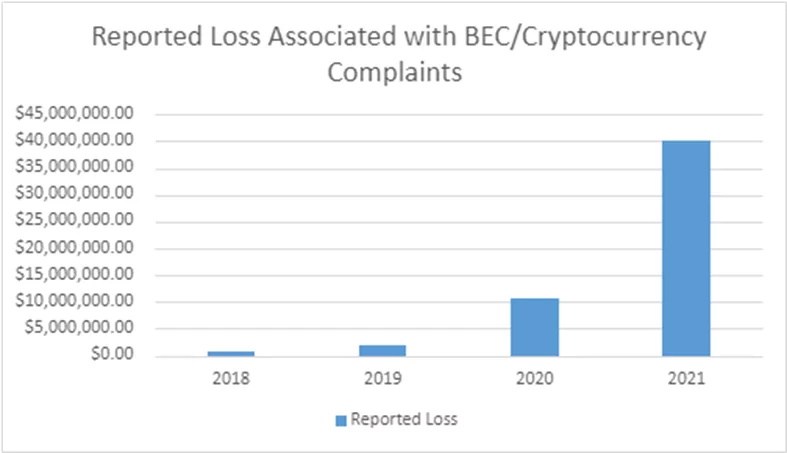
With the widespread use of crypto money, it became the target of attacks and was used among attackers. IC3 announced in a statement on May 4, 2022, that there has been a significant increase in BEC attacks using cryptocurrencies. Until 2018, it did not identify these attacks as BEC. In the announcement, he stated that fraud cannot always be associated with money transfers, and sometimes crypto wallets can be requested under the name of sensitive information.
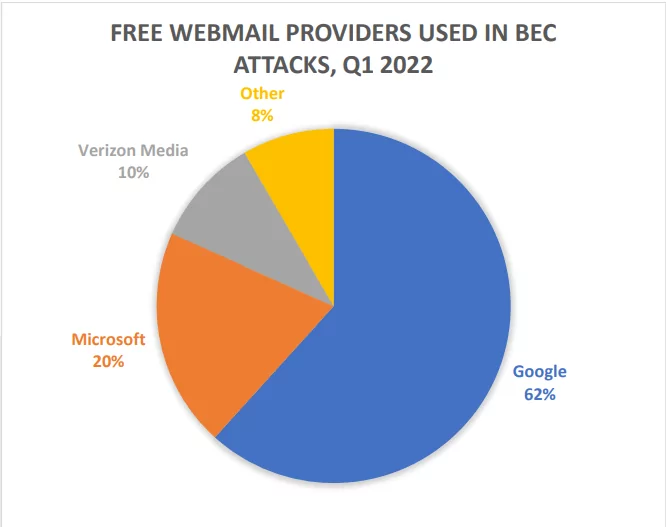
According to the Phishing Activity Trends Report 1st Quarter 2022 published by APWG, 63% of BEC attacks are from gift card requests, 16% from payroll diversion attempts, and 9% from bank transfer plans. The remaining 12% consists of various cash flows. The average amount requested in BEC remittance attacks in the first quarter of 2022 was $84,512, a 69% increase from the $50,027 average for the 4th quarter of 2021. According to the report, in the first quarter of 2022, 82% of BEC messages are sent from free webmail accounts. 60% of them used Gmail. According to the research, NameCheap was the most popular registrar for 18% of BEC messages sent from domains controlled by attackers. One-third of all maliciously registered domains used for BEC attacks were registered through NameCheap.
BEC Attack Examples
Established Trading Firm Loses $17.2M Due to CEO Fraud
A senior employee at Scoular, a commodities trader with a long history of 120 years, caused the company to lose $17.2M by following instructions in fake emails. The emails were sent to the company’s senior financial and accounting controller, apparently by the company’s CEO, Chuck Elsea. The mail requested that money be sent to a bank account because a Chinese company was to be purchased secretly. As a striking detail, the emails came from a different address than the email address used by the company’s CEO for communication. The attacker stated that the money was urgent, that it should be transferred to his account in a short time, and that this favor would not go unrequited, and he put on a hasty and praising style to the finance controller.
Moreover, in an email, s/he contacted a lawyer from KPMG, an accounting and tax audit firm, telling him that the transactions should be done under supervision and given the lawyer’s contact information. Financing reached the lawyer using the contact information in the email. The lawyer approved the money transfer, and the senior financer complied with this instruction, sending $780,000, $7M, and $9.4M 3 days in a row, all to different banks, for a total of $17.2M.
Unfortunately, the email address the CEO used for communication and the contact details of the KPMG lawyer were fake accounts created by scammers. Following the instructions in the email, the funding sent $17.2M to the scammers’ bank account.
Save The Children Scammed by Fake Bill
Save the Children, one of the leading charities, suffered a BEC Attack in 2017 after an employee’s email account was compromised. The attacker gained access to a compromised employee email account, created fake invoices and documents, and sent them from the employee email account from which s/he gained unauthorized access. The attackers did excellent research, and the charity didn’t suspect this, as the bills were created for the health center in Pakistan, where the organization had its base for years. The fraud was detected in May 2017, and the FBI and Japanese law enforcement coordinated to investigate the case. The $1M lost funds were not recovered, but the organization recovered most of the money thanks to insurance.
Treasure Island Succumbs to Manipulation

In June 2021, Treasure Island, a San Francisco-based nonprofit organization, lost $625,000 after threat actors hacked the email account of one of its accountants.
The attackers hacked into a third-party accountant’s email system and added email addresses to existing email chains, making them appear as if they were people associated with the organization. First, they imitated the organization’s manager, Ms. Williams, and said there would be a deferral of a payment that the organization had agreed upon. Then, in a legitimate invoice that falls into the email chain they entered, they manipulated the account number and sent the manipulated invoice to Ms. Williams. Unsuspecting Ms. Williams sent $625.000 to the attackers’ bank account.
BEC from an Attacker’s Perspective
The threat actor performing a BEC attack does not need advanced technical knowledge as it will perform an attack based on social engineering. It is one of the most preferred methods by attackers as it offers the opportunity to earn a large amount of money with a basic/intermediate level of knowledge and a well-planned scenario.
EAC attack, which includes techniques used to gain unauthorized access to a legitimate email address, may require advanced technical knowledge. Still, the EAC attack is referred to as BEC because they are intertwined. The attacker can transfer money to the account of the compromised email account with the help of social engineering or obtain sensitive information about the company. This sensitive information can then be used in a potential BEC attack.
The attacker needs some information to identify suitable targets for the BEC attack and to shape the scenario s/he will set up to deceive the targets. In attacks using invoices and payments, targeting companies that are in litigation or in the payment process, and using some personal information of managers or other employees to increase credibility in emails are frequently encountered in BEC attacks. Attackers often target HR employees of companies to obtain this type of information.
In this attack type, attackers use manipulation techniques to gain the other party’s trust. It carefully examines the keywords and tone used in the legitimate emails it receives and sends an unsuspecting email to its target. Suppose the attacker sends the email by impersonating one of the top executives. In that case, the email praising the employee will motivate the employee and promptly follow the instructions in the email with the desire to be worthy of this praise in a hasty manner.
How to Prevent BEC Attacks
- Avoid using free web-based email accounts. Create a domain name for your organization and use it to create company email accounts.
- Enable multi-factor authentication for work email accounts. Implementing multi-factor authentication makes it difficult for cybercriminals to access employee emails, making it harder to launch a BEC attack.
- Double check the sender’s email address. A fake email address usually has an extension similar to a legitimate email address. For example, using a fake [email protected] address instead of the legitimate [email protected]. Configure email programs to external label emails as external.
- Always verify before sending money or data. Make it standard for employees to approve bank transfers or email requests for confidential information. Confirm by making a phone call using previously known numbers, not the phone numbers provided in person or in the email.
- The correct email address must be entered manually or selected from the address book by forwarding the email rather than replying. Forwarding allows you to use the valid email address of the intended recipient.
- Know your customers and seller habits. Be careful if there is a sudden change in business practices. For example, the request may be bogus if a business person suddenly asks you to use their personal email address when all previous correspondence has been done via company email. Authenticate the request through a different source.
- Train your employees to be more cautious about the payment requested in the email, such as “please make this payment to me quickly,” “I need this money within 24 hours” from the other party, and to verify who the incoming email was sent from.
SOCRadar Solutions for BEC Attacks
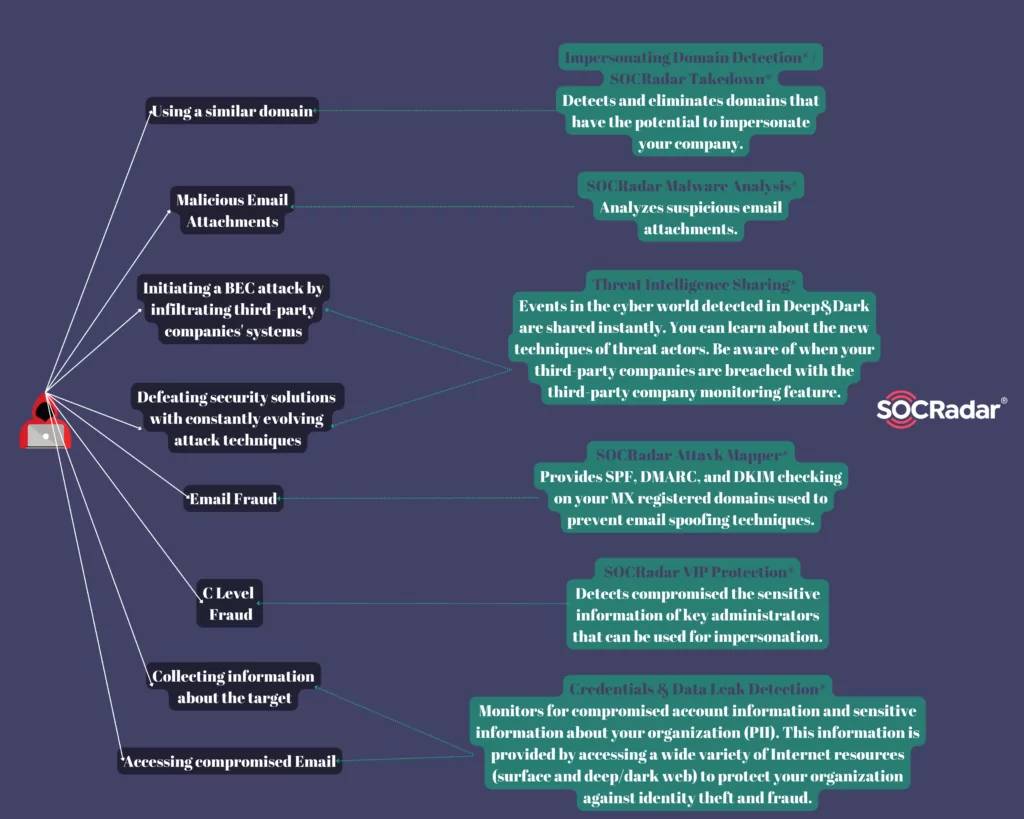
Attackers collect information about the target company before the attack. Security solutions can hardly prevent BEC attacks in familiar ways because most security solutions offer solutions for detecting malicious attachments and fake connections. In this attack type, based on social engineering, measures can be taken to prevent the attacker from creating scenarios with high deception power so that the attacker cannot capture sensitive data that can be abused inside and outside the company. SOCRadar searches the surface web and deep & dark web resources for all kinds of information about your company that may be useful to the attacker (employees’ sensitive information and contact information, internal working structure, payment scheme, etc.) and notifies you of them and ensures that the data is removed upon request.
Attackers can use a compromised email address or impersonation technique in a BEC attack. SOCRadar detects compromised email addresses in your organization.
Threat actors create email addresses impersonating senior executives. To make the fake email address they designed to look like the manager’s personal email, they can include private information of the administrators in the email, or they can use many deceptions such as referencing fake social media accounts. With the VIP Protection module, SOCRadar detects the compromised sensitive information of your senior administrators on the surface web and deep & dark web resources and ensures that this information is removed. Social media accounts where your senior managers are imitated are detected and removed.
While creating fake email addresses, the company’s domain is also imitated. The SOCRadar Impersonating Domain Detection module detects and notifies you of domains that have the potential to impersonate your company before an attack occurs. It has comprehensive control options such as content change and expiration time in case of mx record discovery against BEC attacks. In addition, these domains are eliminated with the SOCRadar Takedown service.
To prevent BEC attacks using email spoofing techniques, your domains with mx records and SPF, DMARC, and DKIM protocols are audited, which are used to authenticate the sender and verify the legitimacy of email communications.
The attack can be carried out from a fake email account as well as from a compromised email account. EAC, referred to as BEC, covers techniques to gain unauthorized access to an attacker’s legitimate email account. These techniques include adding malicious attachments to emails. With the SOCRadar Malware Analysis service, you can analyze whether your suspicious-looking email attachments are safe and take action.



































