
What is IOC Management?
IOC Management is a critical aspect of cybersecurity that involves identifying, handling, and responding to data points indicating potential security breaches or malicious activity. These indicators can range from IP addresses and domain names to file hashes and other digital breadcrumbs left by threat actors. Effective IOC management is critical to detecting and mitigating cybersecurity threats, allowing organizations to safeguard their digital assets and maintain robust security postures.
Access to accurate and actionable threat intelligence is vital. Cybersecurity teams must be equipped with the right tools to stay ahead of emerging threats, and SOCRadar’s Threat Feed & IOC Search tool is one of them. Our product is meticulously crafted to provide security teams with enriched and comprehensive data, making it an indispensable resource for cyber threat research and risk mitigation.
The platform also allows for customization, enabling cybersecurity professionals to tailor their threat feeds to their specific needs. This personalization ensures that teams are always informed about the most relevant threats. With the ability to swiftly search for Indicators of Compromise (IOCs), professionals can integrate these critical insights seamlessly into their existing security systems via the TAXII protocol. This integration not only streamlines threat management processes but also enhances the overall effectiveness of your CTI program.
Customizable Feeds
Besides the customizable feed, SOCRadar offers a highly detailed threat collection, providing real-time insights into daily threat trends and indicators linked to the latest malicious activities. Users can filter feeds by various categories such as Attackers, Advanced Persistent Threats (APTs), Bad Reputation, Hacked Websites, Honeypots, Phishing, Botnets & Malware, Ransomware, and Distributed Denial of Service (DDoS) attacks. This categorization allows teams to focus on specific threats most relevant to their needs.
SOCRadar IOC Search
What is Vulnerability Intelligence?
Vulnerability intelligence is a critical process that enables organizations to proactively identify, assess, and address security vulnerabilities across their software, hardware, and network systems. By gathering, analyzing, and disseminating information about potential weaknesses, vulnerability intelligence helps businesses to make informed decisions and strengthen their overall security posture.
As technology becomes increasingly integral to business operations, the sophistication of cyberattacks has grown, making it essential for organizations to proactively address potential vulnerabilities before they get exploited by threat actors. Therefore, staying ahead of the rapidly evolving cyber threats in today’s digital landscape is crucial. The current threat landscape forces organizations to have strong vulnerability intelligence to ensure their systems remain secure against potential exploitation by threat actors. SOCRadar’s Vulnerability Intelligence provides a sophisticated solution to safeguard complex digital assets through timely alerts and actionable insights.
But the important thing here is to find the vulnerabilities before the threat actors. In cybersecurity, staying ahead of the curve is essential because threat actors always look for weaknesses to exploit. That’s where SOCRadar comes in, offering timely alerts about vulnerabilities, especially those in your publicly accessible technologies and services. This early warning system allows organizations to fix issues before they become serious problems.
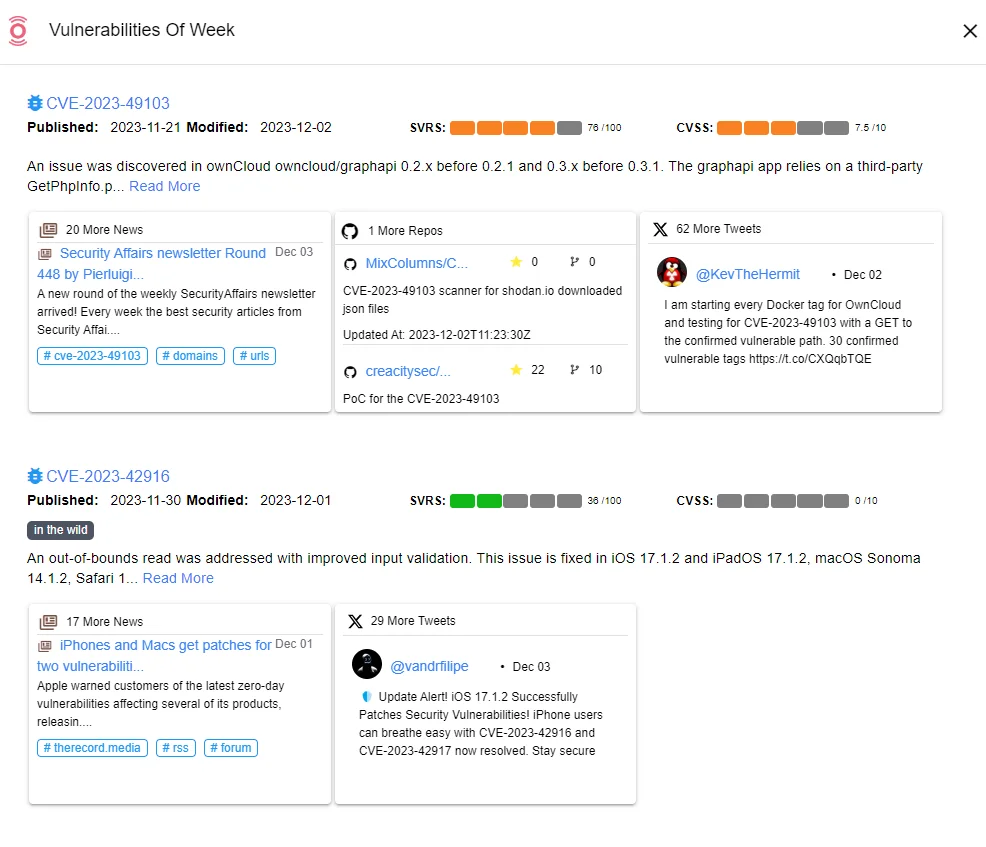
SOCRadar Vulnerability Intelligence
Security researchers and vulnerability intelligence teams actively monitor the threat landscape to detect vulnerabilities. Upon discovery, organizations can prioritize their response by implementing necessary patches and updates, mitigating risks before the vulnerabilities are widely exploited. This proactive approach fosters collective security, allowing the benefits of early detection to extend across the industry rather than leaving individual organizations to address threats in isolation.
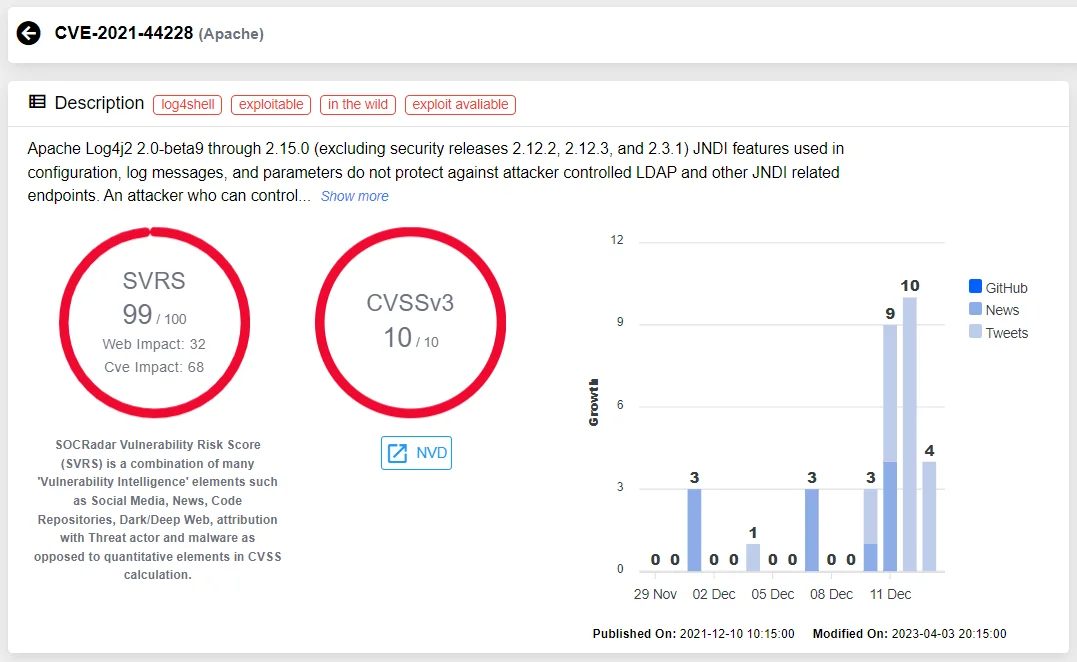
Detailed Vulnerability Analysis
How to Use IOC Intelligence?
At Zen Finance, a leading firm in the financial sector, cybersecurity was paramount. The company had recently invested in advanced tools to enhance its security operations, knowing that the stakes were high in their industry.

Zen Finance HQ – Generated by ImageFX
One afternoon, an automated alert appeared on the security team’s dashboard. It was from the IOCs they gathered from SOCRadar’s Tactical Intelligence module. The suspicious activity was an outbound connection to a known malicious IP address. Their systems automatically blocked the connection and isolated the affected endpoints, preventing the threat from spreading further.
Maria, the lead security analyst, immediately began investigating. She conducted a thorough search across the entire network using the information she got from the SOCRadar IOC Search tool. With the data they gathered from SOCRadar, she scoured network traffic, log data, and endpoint activity, hunting for any other indicators that initial defenses might have missed. Sure enough, it uncovered several dormant files on a few machines—artifacts linked to a sophisticated phishing campaign that had bypassed the company’s firewalls weeks earlier due to misconfigured detection rules.
Realizing the gravity of the situation, Maria didn’t stop there. She initiated a deeper investigation, using the IOC Search tool to cross-reference the newly discovered IOCs. To her dismay, the data revealed that the phishing campaign was part of a broader, coordinated attack targeting multiple financial institutions.

Maria – Generated by ImageFX
Without hesitation, Maria shared her findings with the related bodies. This collaboration allowed other organizations to quickly update their defenses, preventing the attackers from gaining a foothold elsewhere.
How to Use Vulnerability Intelligence?
At LeafGuard Solutions, a cybersecurity firm responsible for managing the security of multiple clients, the day started like any other. However, a recent surge in cyberattacks targeting similar companies had the team on edge.

LeafGuard Solutions HQ – Generated by ImageFX
Sam, the head of the security team, was in a morning meeting when he received an urgent notification. A newly discovered critical vulnerability was reported, affecting a widely used software within their client’s environment. The team needed to act fast, but they had to prioritize their efforts carefully, with hundreds of systems to manage.
Sam immediately turned to their intelligence provider SOCRadar’s Vulnerability Intelligence module. They used this tool previously to help the team prioritize patch management based on vulnerabilities’ criticality and potential for exploitation in the wild. This time, it highlighted that this flaw was highly likely to be exploited, given its exposure in the wild, the discourse on the web, and its relevance to their customer’s industry.
With this information, the team focused their patching efforts on the most critical systems, reducing the risk of exploitation before the patch could be fully deployed across all environments. This strategic prioritization minimized the attack surface effectively.
But Sam knew that patching was just one part of the solution. He instructed his team to correlate the vulnerability intelligence with known threat actor Tactics, Techniques, and Procedures (TTPs). Using SOCRadar’s Threat Actor Intelligence tool, they identified that a notorious threat actor group had been actively exploiting similar vulnerabilities. The group was known for its specific TTPs, and the tool provided a comprehensive view of which systems were most at risk from this particular actor.
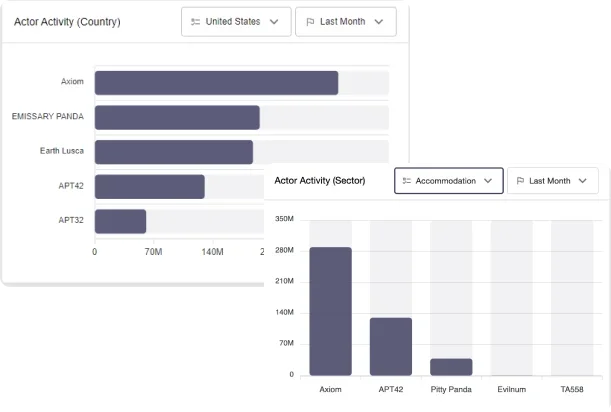
SOCRadar Threat Actor Intelligence
The team implemented additional security measures with this targeted intelligence to counter the threat actor’s known techniques. They reinforced defenses on the most vulnerable systems and deployed monitoring tools to detect signs of the threat actor’s typical behavior.

Sam – Generated by ImageFX
Conclusion
In conclusion, Vulnerability Intelligence and IOC management are critical components of a robust intelligence program. They basically allow organizations to see what dangers they are facing with.
By understanding and addressing vulnerabilities proactively, organizations can mitigate potential threats before they escalate. That’s the importance of knowing.
Similarly, effective IOC management enables swift detection and response to emerging threats, minimizing damage and maintaining the integrity of systems. Since threat actors use similar approaches to various organizations, detecting their tools once can help everyone.
Together, these practices enhance security and empower organizations to stay ahead in an ever-evolving threat landscape.



































