
A Rising Threat in Mobile: What is Banking Malware?
Mobile Banking malware is a malware family consisting of malicious apps and trojans designed to infect one’s system and collect financial data, personal information and potentially steal login credentials. Over %95 of mobile malware are banking trojans; in addition, around %98 of banking malware attacks target Android devices.
Shining Light On the Infection Vectors
The primary infection vector of mobile malware is malicious apps on third-party app stores impersonating other well-known apps. For example, FluBot, a prominent banking malware mainly targeting European countries and Japan, uses fake apps to infect an Android device and distributes itself to other devices through SMS.
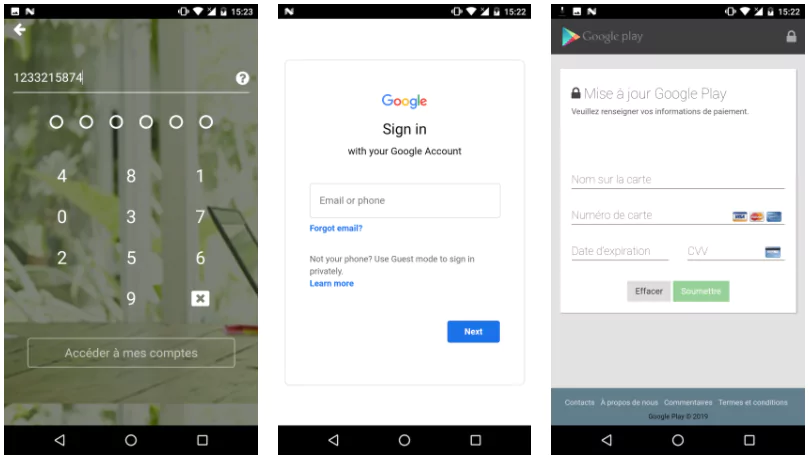
Once FluBot infects a mobile device, the malware collects the contacts and sends the data through Command and Control (C2) server. Then, a malicious SMS message is sent to all contacts to spread the malware further. If the recipient of the malicious SMS clicks the link and downloads the malware, the whole process is executed once again to infect more and more mobile devices.
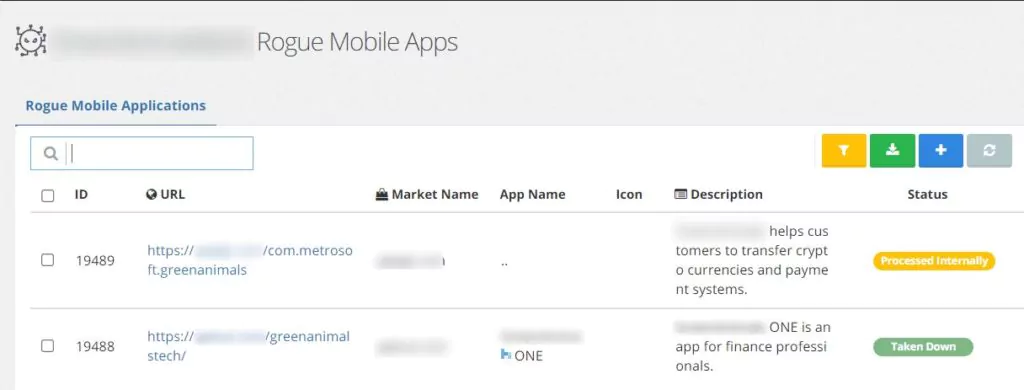
A significant drawback for well-known enterprises is that their official mobile application may be impersonated by banking malware. The victims of the attack may blame the company, damaging the company’s brand reputation. SOCRadar’s RiskPrime crawls through the web and finds impersonating mobile apps that might damage the company’s public image. Through SOCRadar’s RiskPrime, the security teams can initiate the takedown of the malicious apps in one click.
The second most used infection vector of mobile banking malware is malicious apps offering services and operating without the victim’s knowledge. These services include matchmaking, gaming, translation, and weather forecast. The victim downloads the app thinking it will carry out its purpose, but it will conduct malicious intentions.
Other infection vectors for mobile banking malware include malicious pop-ups and fake alerts, clickbait links, file-sharing services, and malicious emails.
Malware in Disguise: Is it a Weather Forecast App?
Impersonating mobile apps use phishing and social engineering to steal the victim’s data. The app usually has a user interface looking just like the app it imitates. When the user enters its credentials, the app copies the data and sends it over C2; moreover, it usually asks for permission to read and send SMS.
If the victim gives consent, the app can bypass two-factor authentication by accessing the message sent by the bank, and the app can have access to the victim’s bank account. From here on out, the app sends minor amounts of money to the threat actor’s bank account until the victim notices. If the victim does not notice the stolen money, the app can go on for a long, stealing vast amounts of money.
Other malicious mobile apps utilize a strategy that includes offering a specific service like matchmaking or weather forecast, including malicious code running without the victim’s knowledge. The apps do not usually carry out their service, but they only fake it to gain time for the malicious code to operate. The malicious app utilizes many different tactics to steal the victim’s data and evade detection from here on out.
For example, Cerberus, an android malware first found and analyzed in mid-2019, has implemented a procedure that tracks the user’s movement. The malware activates itself if the user moves around a lot and breaches a threshold determined by the threat actor. This procedure enables the malware to conceal itself in a malware analysis laboratory.
Most malicious apps ask for privileges and permission to install additional packages. If the user consents, the app grants more rights and hides, not enabling the victim to delete the malware. Some malware waits for commands from the threat actor over C2, while some execute an autonomous attack.
Capabilities of the malware include keylogging, collecting information about the system or personal information, accessing SMS and call data, sending SMS or making calls, downloading or deleting apps. Some malware utilizes banking web injection, the addition of malicious JavaScript code to an actual bank website, in their attacks.
Through banking injection, the malware can alter the contents of the actual bank website, collect information such as login credentials and credit card information, or even have complete control over the victim’s device.
Evading Mobile Banking Malware
Protecting oneself from mobile malware is necessary since some malware can be dangerous. A mobile banking malware named Zitmo (Zeus-in-the-mobile) stole more than 47 million dollars from victims in 2012. Another mobile malware, OpFake, imitates over 100 banking apps to fool its victims into collecting their credit card information.
To prevent mobile banking malware attacks, SOCRadar suggests:
- Browsing on sketchy websites is done with caution,
- Multi-factor authentication is implemented,
- Not installing apps from third-party app stores,
- Always being careful about granting permission to apps,
- Always be cautious while clicking links,
- Being mindful about malicious email attachments,
- Not clicking on malicious pop-ups and fake alerts.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































