
CISOs Guide to External Attack Surface Management (EASM)
The year 2021 was started and ended with two major cyber security incidents: SolarWinds Attack and Log4j vulnerabilities. In between, ransomware rose to a level affecting the lives of ordinary people directly, thanks to the Colonial Pipeline Attack. As of March 2022, the spillage from the Russian-Ukrainian cyber conflict threatens all companies with digital assets.
External Threats Rising
According to CrowdStrike’s 2019 Global Threat Report, Russian state-sponsored hackers need less than 20 minutes to breach a network (1). It only took less than an hour for an undefended IoT device to be hacked in 2016 (2).
In 2021, almost 4 out of 10 businesses and organizations stated that they were hit by ransomware. The cost of recovery from a ransomware attack is $1.85 million on average, according to the Sophos Whitepaper (3).
As every undefended digital asset is becoming an entry point for threat actors, CISOs and information security teams can not afford to have vulnerable, unidentified, unmanaged, and unmonitored digital assets. That makes External Attack Surface Management (EASM) the first line of defense.
The Definition of External Attack Surface Management (EASM)
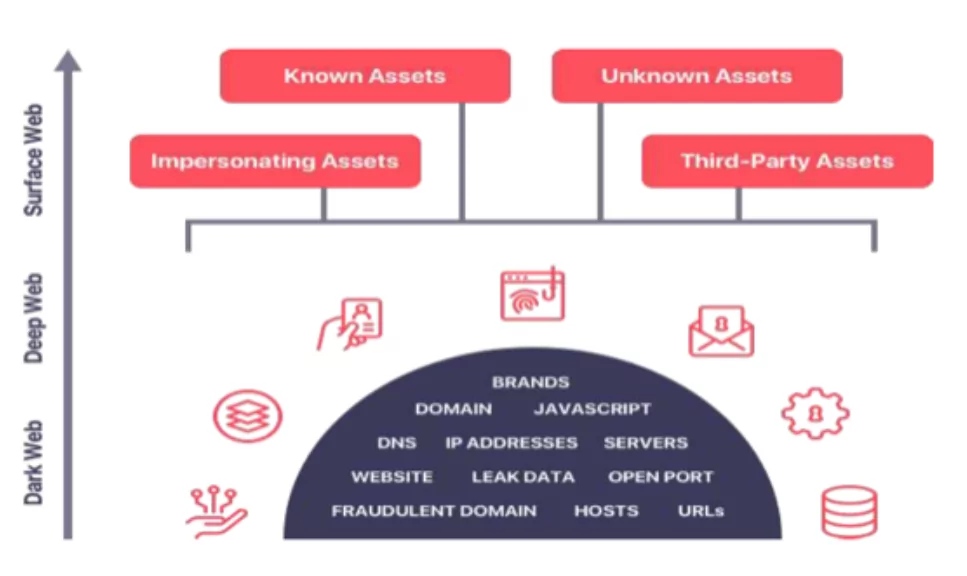
Gartner defines EASM as “a combination of technology, processes and managed services that provides visibility of known and unknown digital assets to give organizations an outside-in view of their environment” in their Market Guide for Security Threat Intelligence Products and Services published on December 10th, 2021.
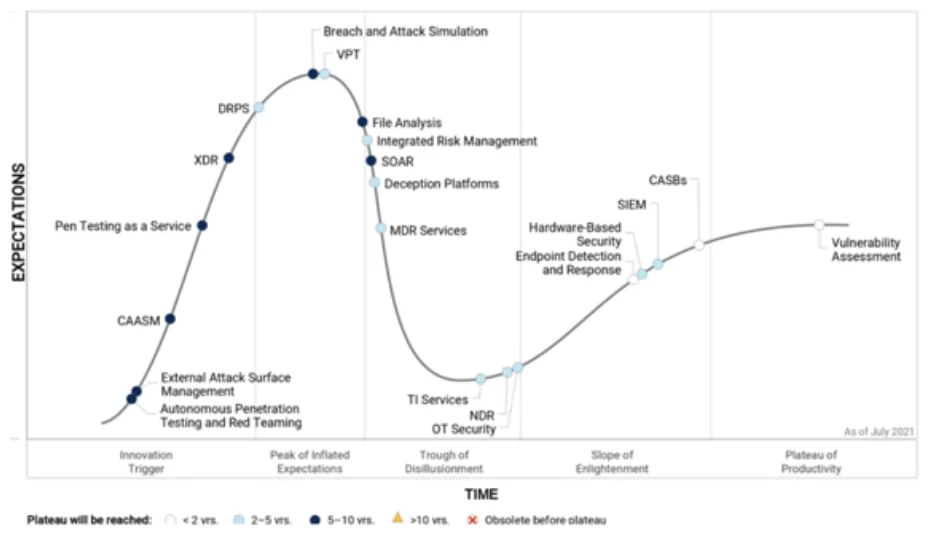
Another Gartner report published in July 2021, Hype Cycle™ for Network Security, also explains External Attack Surface Management (EASM) as “autonomous security testing, and threat intelligence services all provide an inward-looking viewpoint toward an organization’s infrastructure from the outside.”
It further explains that “this renewed approach to exposure provides better enrichment for organizations to decide what matters to them— without looking at the threat landscape in a more general way and wonder if they are affected.”
There are two crucial points in Gartner’s definition. First, the EASM should be an outsider’s, a threat actor’s, view into the organization. Second, it should be an autonomous view since the organizational lists are not adequate or complete most of the time.
A research study (4) done by Enterprise Strategy Group for JupiterOne shows that 73% of security professionals still depend on spreadsheets to manage their network’s security hygiene and posture. Therefore, attack surface management (ASM) became increasingly difficult for them in the period that started with the pandemic.
Almost 30% of all respondents discovered sensitive data in previously unknown locations, found websites with a path to their organizations, uncovered employee corporate credentials or misconfigured user permissions, and exposed once unknown SaaS applications in the same survey.
The Top 18 CIS Critical Security Controls
The SANS Critical Security Controls (SANS Top 20) became the CIS (the Center for Internet Security) Critical Security Controls (CIS Controls) (5). These controls are sets of best practices developed by security experts worldwide to stop the most dangerous recent threats. They are validated and prioritized every year.

The center explains the last revision as “Version 8 combines and consolidates the CIS Controls by activities, rather than by who manages the devices. Physical devices, fixed boundaries, and discrete islands of security implementation are less important; this is reflected in v8 through revised terminology and grouping of Safeguards, resulting in a decrease of the number of Controls from 20 to 18” (5).
The top two controls of Version8 are:
- Inventory and Control of Enterprise Assets
- List and Control of Software Assets
As the CIS approves, the logic behind the first line of cyber defense is simple: You can not protect what you do not know about.
How Can EASM Help with Vulnerability Management?
Vulnerability management is an ongoing process to identify, assess, manage vulnerabilities across the enterprise. The success of this process heavily depends on the maturity of the enterprise’s digital asset management and the allocated amount of workforce.
Even with enough capabilities and human resources, discovering the assets exposed to the internet might not be that easy since some of the assets of every company live on somebody else’s data center, the cloud. The discovery itself also is open to human error.
Therefore, asset records might not exist or be up to date in the enterprise assessment management system. As a result, some of the assets on the cloud could stay out of the scope of the vulnerability management program and becomes a pain point, a regular nightmare for every CISO that keeps them awake.
SOCRadar Can Help CISOs to Mitigate Digital Risks with EASM
SOCRadar is designed to be a user-friendly and convenient watchdog platform for any CISO to manage and mitigate the enterprise digital risks by employing artificially intelligent modular architecture producing maximum gain with minimum effort.
By providing just a single domain address to SOCRadar, powered by the AttackMapper module, it can enumerate all the internet-facing digital assets of the enterprise and offers continuous asset monitoring.
AttackMapper has a unique feature and capability to link, map and reveal all internet-facing technologies, including IP, DNS, domain address, and the cryptographic infrastructure. AttackMapper is not only limited to discovering critical ports, unpatched/vulnerable applications, vulnerable or expired digital certificates, and exposed personally identifiable information, but also it can monitor, detect and alert promptly.
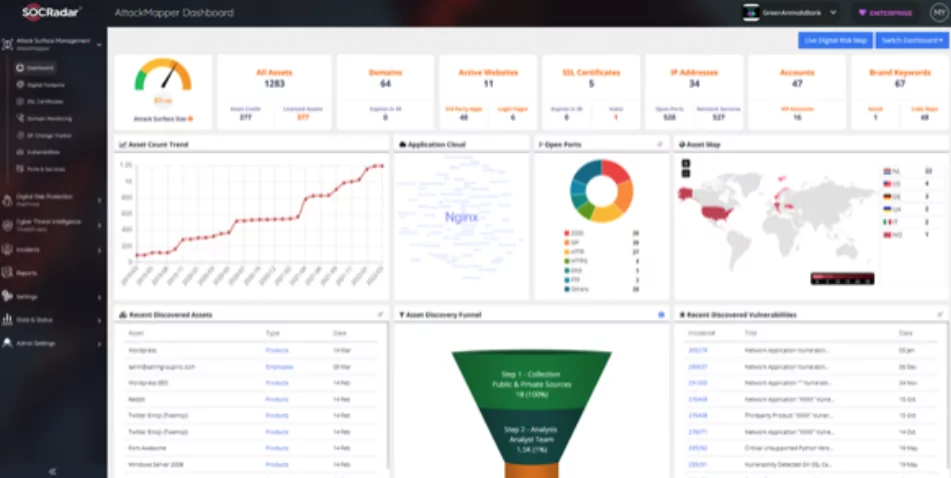
Most CISOs try to survive with limited cyber security budgets and workforces, and that’s where the SOCRadar makes the difference and comes to the rescue by automating all the daily security operations and reducing the workload of an employed person.
SOCRadar is a Gartner-recognized vendor for External Attack Surface Management (EASM), Digital Risk Protection (DRPS), and Cyber Threat intelligence. Modules and features of SOCRadar are mentioned in Market Guides and other Gartner documentation on more than one occasion as sample vendors.
Use Case: AttackMapper vs. Ransomware
CISA’s 2021 global ransomware report (6) points out that social engineering attacks (phishing), remote access hacking (RDP), and exploitation of application and software vulnerabilities are still the top three attack vectors abused by cyber threats actors and threat actors.
Defending the enterprise against common threats, including ransomware, staying one step ahead of cybercriminals begins by identifying internet-facing assets and the technologies and services that rely on them.
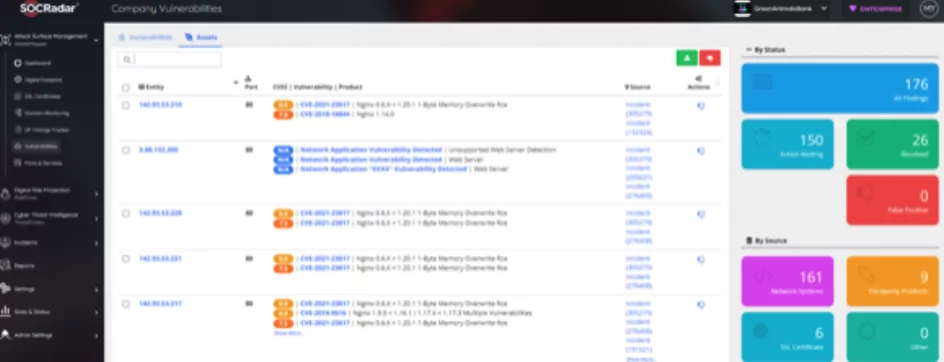
AttackMapper brings all open critical ports and vulnerabilities with CVSS scores to be monitored and mitigated before a threat actor becomes aware of them. Similarly, when a zero-day like Log4j comes, you will know all your vulnerable assets before everyone else.
Free Test to Check Your Security Posture
You can use free SOCRadar Labs` Tools to look at the external attack surface with a few clicks. Once the service is on, it begins the discovery of Internet-facing web assets along the surface, vulnerability testing to see what can be exploited.
Click here for SOCRadar LABS – “Tests on Your Security Posture”



































