Major Cyberattacks in Review: July 2022
Today’s world has many cyberattack targets, including large organizations, small businesses, and individuals. Any action, no matter how small, can put you in danger. Most of the cyber incidents from last month involved situations in which the threat actors had to impersonate legitimate or reliable services.
Actively Exploited Vulnerabilities in Atlassian Confluence
Confluence Servers enabled the Questions for Confluence app to be exposed to a hardcoded credentials vulnerability tracked as CVE-2022-26138. After the patches were made available and the hardcoded credentials were made public on Twitter, more instances of exploitation were noticed in the wild.
Other frequent attack scenarios included CVE-2021-26084 and CVE-2022-26134, which were used by attackers to RCE and deploy malware such as web shells and crypto miners.
Cisco Released Patches for Multiple Nexus Dashboard Vulnerabilities

Cisco’s Nexus Dashboard had several flaws, including a high severity arbitrary command execution flaw. It could be exploited to allow remote attackers to log in and launch a cross-site request forgery attack as root.
Another network may become a target for exploits if one network’s vulnerability is exposed. Attackers can try to attack a vulnerable API by sending specially crafted queries to it.
Juniper Networks Released Fixes For Critical Vulnerabilities

CISA advised applying recently released fixes in Juniper Networks products due to several critical vulnerabilities that could lead to system take-over. The most critical vulnerability was found in Junos Space products, as CVE-2021-23017 with a 9.4 CVSS score.
An attacker who can forge UDP packets from the DNS server could cause 1-byte memory to overwrite and crash the worker process, successfully exploiting the vulnerability. Other affected products were CentOS 6.8, NorthStar Controller, and Juniper Networks Contrail Networking.
Checkmate Ransomware Targets QNAP SMB Services
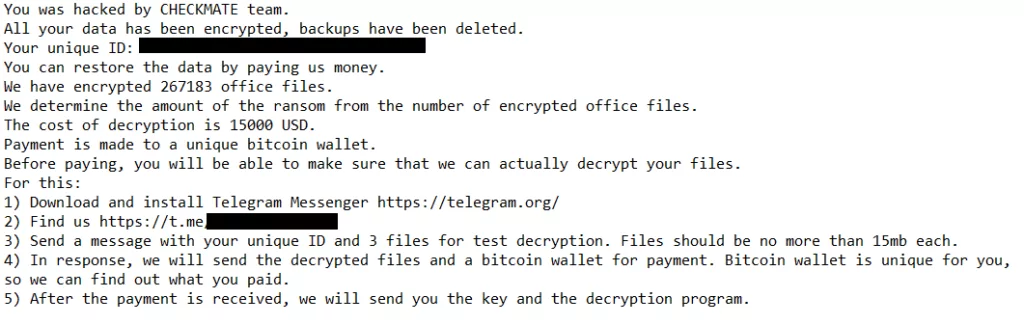
The new version of Checkmate ransomware was discovered targeting QNAP NAS devices, attacking through SMB services accessible via the internet.
A dictionary attack is used by Checkmate to find weak passwords. After successfully compromising the system, data is encrypted. QNAP has had numerous ransomware groups attacking its products in recent years. The company has concluded its investigation into the DeadBolt ransomware campaign, and Checkmate is no longer a threat to QNAP. Additional details are available in the company’s security advisory.
NPM Packages Used In A Supply Chain Attack
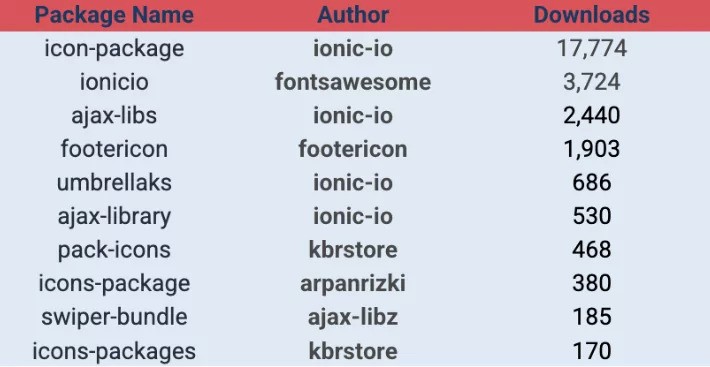
Using malicious NPM packages with Javascript code disguised, an NPM supply chain attack that started in December 2021 impacted hundreds of desktop applications and websites.
It was discovered that the attackers (known as IconBurst) employed the typosquatting technique to spoof widely used NPM packages such as umbrellas and icons. Later, more packages from different profiles were discovered.
The malicious packages used jQuery’s ajax() capabilities to steal form data. Some of these packages exfiltrated the data to malicious domains using modified components. Below is a list of the research packages.
Hundreds of Windows Networks are Infected with Raspberry Robin Worm

Raspberry Robin has evidence of being active since 2019 and has compromised hundreds of business networks. It acts like a worm and is installed via external devices such as USBs. It gains access through msiexec.exe and installs malicious DLL files.
Raspberry Robin frequently compromises QNAP NAS devices by using HTTP requests containing the victim’s hostname and using them as C2 servers. Raspberry Robin was also using TOR output nodes as an extra C2 infrastructure.
Microsoft linked this malware to Evil Corp operations due to their payload similarities.
More than a Million Users Affected by HiddenAds Malware
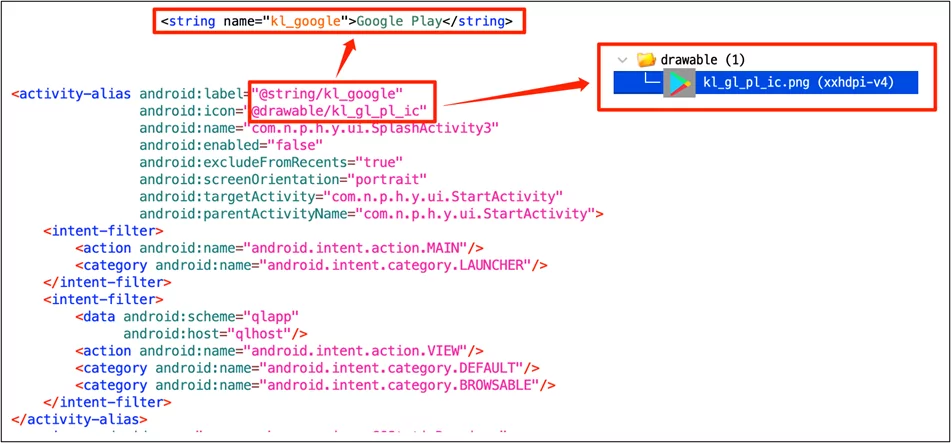
HiddenAds had over a million downloads on Google Play Store. All downloads are another infected device as the malware executes itself without user interaction. Upon installation, HiddenAds conceals itself to avoid deletion by changing its icon to Settings managers or well-known apps like Google Play. Affected devices are constantly sent advertisements and notifications.
DawDropper Campaign Distributes Malware on Google Play

Security experts have discovered an operation to spread banking trojans on the Google Play Store. Identifying threat actors when using these “Droppers” is challenging, and they are successful at spreading malware. Some threat actors on the dark web also offer this software, becoming increasingly commonplace daily, for sale as dropper-as-a-service (DaaS). DawDropper is a malicious program that poses as a trustworthy program to access victims’ mobile devices.
The distribution of banking trojans like Octo, Hydra, Ermac, and TeaBot to mobile devices through variations of DawDropper is one of the research’s discoveries. To escape detection, these variations put their payloads in GitHub repositories as the dynamic download URL and use Firebase Realtime Database as a C2 server. Once on the target device, the dropper connects to the C2 server and begins downloading the malware payload from the GitHub repository.
CosmicStrand Malware Infecting Operating Systems Through Firmware
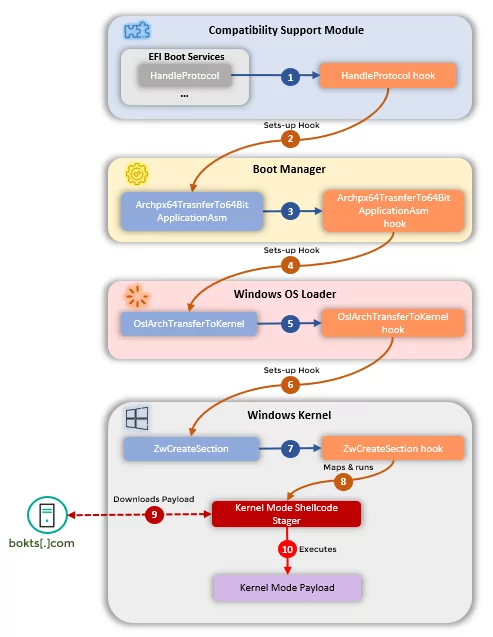
Kaspersky Researchers found the CosmicStrand rootkit in a modified UEFI. When your computer turns on, this firmware virus loads up and starts the OS boot process. The importance of this problem can further be increased by the fact that this malware loads from a chip on the motherboard rather than your hard drive because it loads before the operating system boots up. In other words, malware is so strong that if your computer becomes infected, you must throw your entire PC’s hardware out.
Hacker Steals Half Million Euros from Lisbon Hotel with Fake Bookings

The Marino Boutique Hotel in Lisbon was the victim of a cyber attack. A Russian hacker accessed the hotel’s Booking.com account and took over €500,000.
More than a thousand clients unintentionally booked false reservations between June 12 and June 16, according to CNN Portugal. The hacker used a payment link to trick customers into sending money to his account.
Instead of the usual 200–300 euros, the hacker changed the room prices to €40 per night. Over 1,000 reservations were made in just four days due to this scam, as many people took advantage of the false offer.
The US Federal Tax Payment System Website was Targeted by Killnet
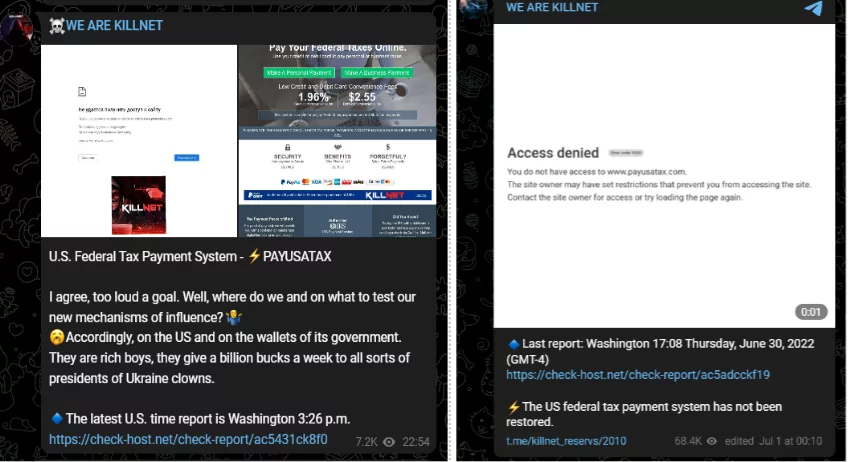
The US Federal Tax Payment System website was targeted by the Russian hacking group Killnet. This was mentioned on July 1 on the hackers’ Telegram channel.
“Payusatax.com” has been unavailable for five hours. The message states that this indicates the end of their new method’s test.
The hackers pointed out that the attack was launched in reaction to a “gangster and illegal” notification of a technical default on a fake pretext in the interests of the US-led banking system.
The freeze of Russian assets in the accounts of US and EU banks also prompted this response from hackers.
Nearly 40 GB Data of Covid Platform Exposed


A data leak was found connected to the Proud Makatizen website run by the Makati City administration in the Philippines.
The website started as an online platform for Covid-19 relief services, including registering for immunizations, financial support, and more.
Over 620,000 files were exposed due to Proud Makatizen’s misconfiguration of an Amazon Web Services S3 bucket. Along with confidential financial and medical data, the files also contained images of ID cards.
Around 300,000 Makati residents were made vulnerable to potentially damaging cyber attacks, including identity theft and privacy violations, as a result of the 39.7GB Proud Makatizen data leak.
Mangatoon Data Breach Exposed 23M Accounts

An insecure Elasticsearch database was breached by a hacker, exposing information from 23 million user accounts on the comic reading platform Mangatoon. Millions of users read online Manga comics using the popular iOS and Android app Mangatoon.
The data breach notification service Have I Been Pwned (HIBP) tweeted about the incident. On May, 23M accounts at Mangatoon were compromised. Names, email addresses, genders, social media account information, auth tokens from social logins, and salted MD5 password hashes were leaked due to the hack.
An Elasticsearch server with weak credentials was used to conduct the data breach, according to well-known hacker “pompompurin,” who claimed responsibility.
Users of Mangatoon can now look up their email address on HIBP to see if their account was compromised.
Huge Database of 69M Records Stolen from Neopets
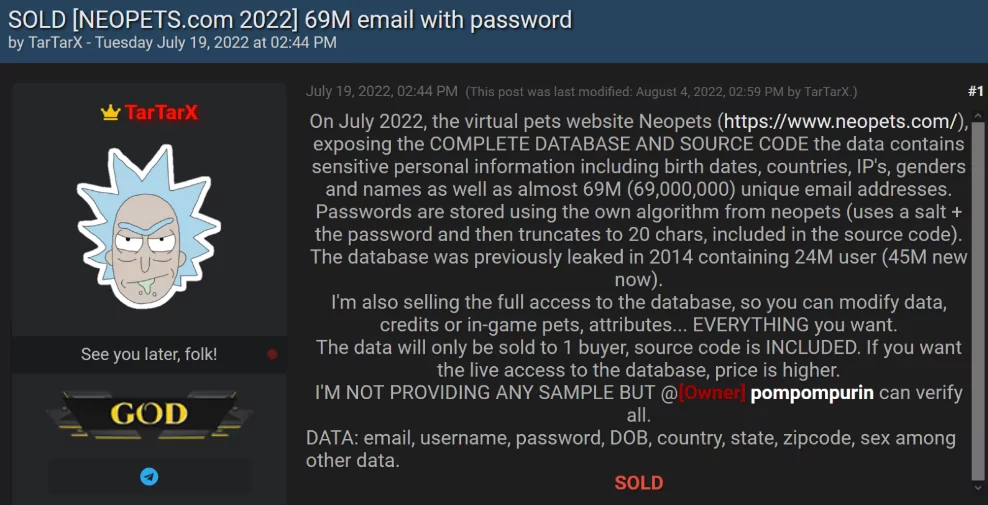
The source code and database of the virtual pet website Neopets, which contained the personal information of over 69 million users, were stolen as a result of a data breach. Recently, Neopets introduced its own NFTs for use in a Metaverse game. The stolen database contained usernames, names, email addresses, passwords, zip codes, dates of birth, genders, activation codes, and other additional information. The stolen data was offered for 4 bitcoins on a breach forum by a hacker named TarTarX, now tagged sold.
5.4M Twitter User Accounts Are Being Sold by a Hacker for $30K
Threat actors used a flaw to collect contact information for 5.4 million Twitter accounts, including phone numbers and email addresses. The information was sold on a hacker site for $30,000 after Twitter experienced a data breach.
Even though the user has blocked this action in the privacy settings, the vulnerability enables any party without any authentication to obtain a Twitter ID (practically equivalent to acquiring the username of an account) of any user by providing a phone number or email.
The Twitter Android client’s permission process, especially the step when an account’s duplicate is checked, is where the bug is found.



































