
5 Lessons Learned from Data Breaches in 2022
By SOCRadar Research
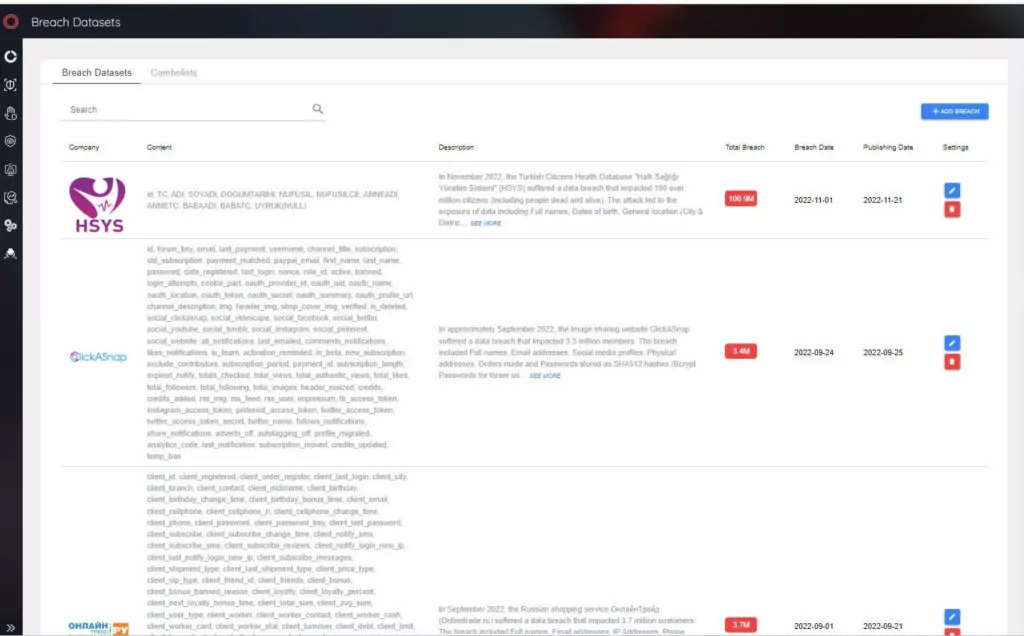
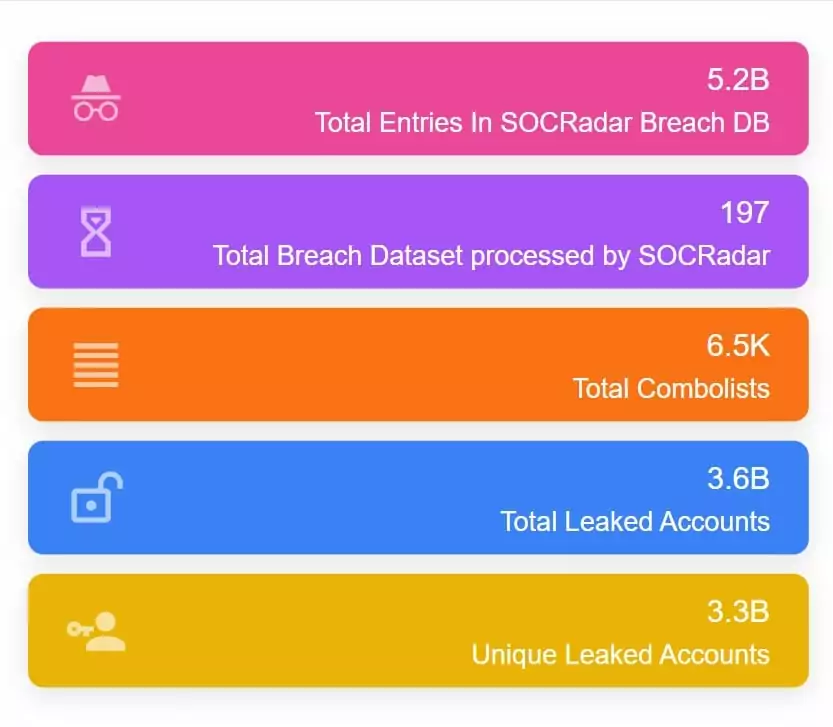
Online products and services are growing daily. Consumers are entrusting more personal information to online databases, and businesses are taking responsibility for more sensitive data. Cyberattacks to obtain data and associated data breaches are expanding in parallel with the volume of online data. According to Statista, during the first three quarters of 2022, approximately 23.65 (Q1:3.33, Q2:5.54, Q3:14.78) million data records were exposed worldwide through data breaches. SOCRadar, the Extended Threat Intelligence (XTI) platform, processed 13 datasets that contained 132.8 million records leaked in 2022.
Download SOCRadar’s 2022 End-of-Year Report to gain insights into major data breaches.
Indicators of a Data Breach
A data breach is any security incident that allows unauthorized access to an organization’s data. While it can happen unintentionally, it is usually the consequence of planned and financially driven attacks. Internal or external actors can be responsible. Depending on the type of incident, data breaches can be categorized as follows:
- Confidentiality Breach: Unauthorized internal or external access to confidential data.
- Availability Breach: The loss or destruction of data or data access restriction due to an attack.
- Integrity Breach: It is the unintentional or intentional change of confidential data.
In this context, indicators of a data breach can be summarized as follows:
- compromise account
- compromise access
- unauthorized access
- unauthorized exposure
- loss of control of personal data
Data Breaches in 2022 According to SOCRadar
Data breaches are typically discovered through:
- Third-party breach statements
- Alarms from the monitoring service
- Routine security checks on systems
- Threat actors’ posts on the dark web
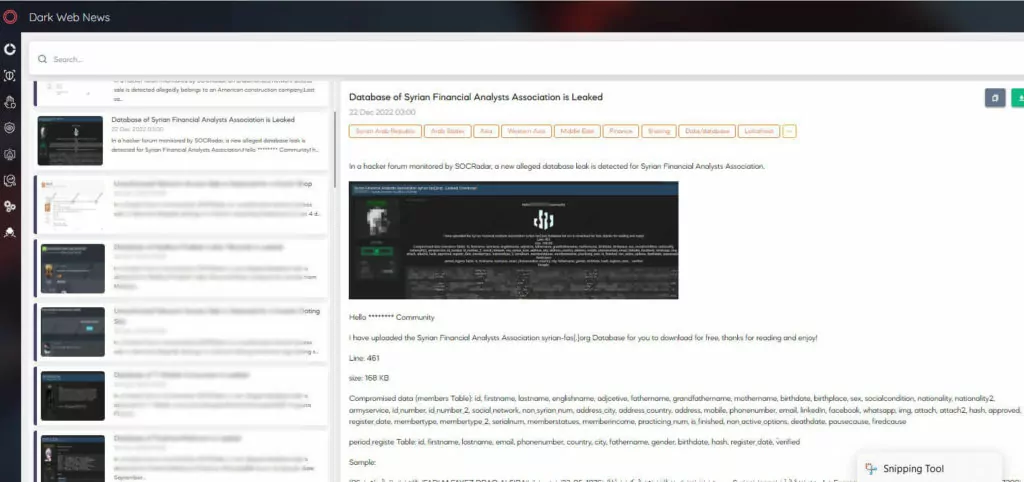
SOCRadar XTI platform continuously monitors underground forums and instant messaging services on the dark web and detects leaked databases with SOCRadar’s automated dark web scan feature. In 2022, approximately 9500 data breach-related posts were reported in SOCRadar XTI Platform dark web news module.
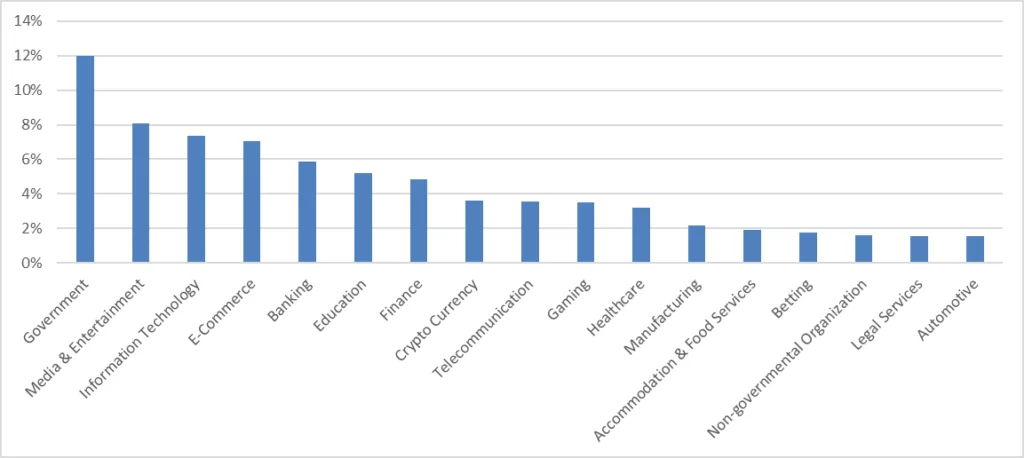
According to the analysis of data breach-related dark web posts, governmental organizations are at the top of the list with a rate of 12%. Media & entertainment, information technology, and e-commerce are among the top targeted industries.
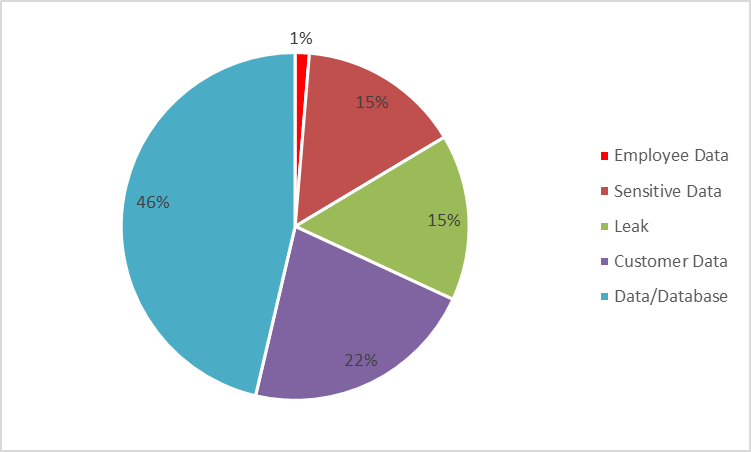
Based on an analysis of data breach-related dark web posts, 22% of the posts are tagged as customer data, 15% as sensitive data, and 1% as employee data.
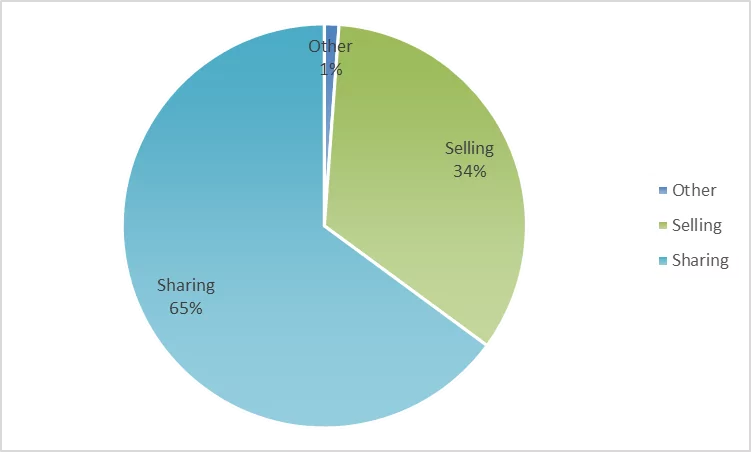
The analysis also indicated that 65% of the posts are about “sharing” and 34% are about “selling” compromised data. The fact that sharing (data for free) data statistics is more than selling (data for sale) data demonstrates a widespread culture of sharing among threat actors. The data obtained from sharing motivates threat actors for future attacks. Threat actors can later share the sold data to gain interaction and popularity.
Lessons Learned from Data Breaches in 2022
Lesson 1: Importance of Regular Security Reviews
On July 21, 2022, Nelnet Servicing, a technology services provider to student loan companies, notified clients about an incident impacting their website used by borrowers to access account information. The Nelnet cybersecurity team discovered a vulnerability that is believed to have led to this “suspicious activity.”
On August 17, 2022, the forensics investigation revealed that student loan account registration information was available to an unknown third party for almost 50 days due to the vulnerability. The data breach impacted approximately 2.5 million borrowers.
Lesson learned: Regular data security reviews help to identify potential exposures promptly and efficiently. In this context, reviewing and updating security measures should be one of the priorities to avoid vulnerabilities.
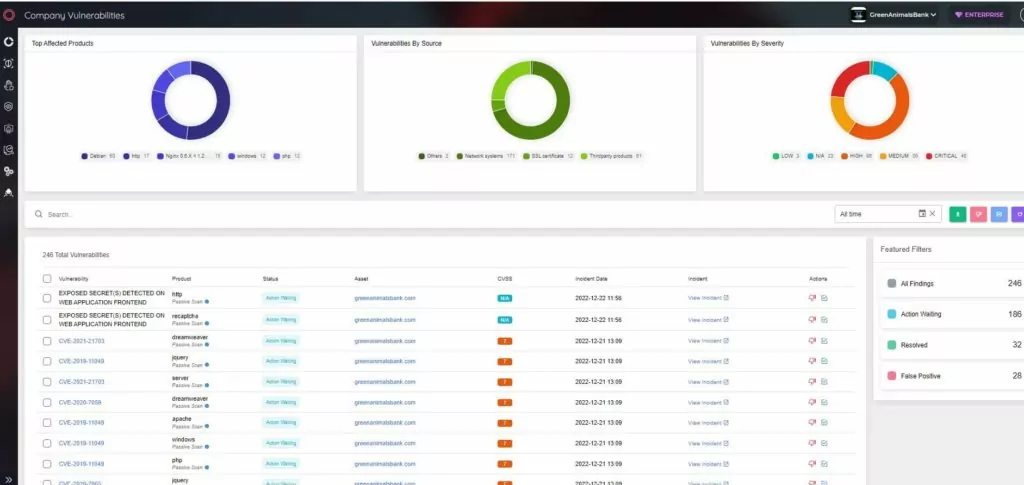
SOCRadar XTI actively monitors customers’ perimeter from an external perspective to spot critical internet-facing vulnerabilities that can be exploited. Companies can have continuous visibility into vulnerable software, exposed networks, third-party software, expired SSL certificates, DNS records, undiscovered cloud assets, and more with SOCRadar External Attack Surface Management.
Lesson 2: How Critical Third-Party Security Is
On December 12, 2022, Uber announced threat actors gained access to 70K+ uber employees’ data and posted stolen corporate data. Uber stated this data breach occurred because of a third-party vendor who had Uber’s mobile device management.
On August 25, 2022, DoorDash, an online food ordering and delivery platform, announced that a third-party vendor was the target of a phishing campaign, and personal information maintained by DoorDash was affected.
Lesson Learned: Companies that share data with a third-party organization must ensure they have at least the same cybersecurity awareness. Third-party vendors and service providers should be closely monitored, conduct due diligence, and provide necessary security protocols to prevent abuse of data exchanges between them by threat actors.
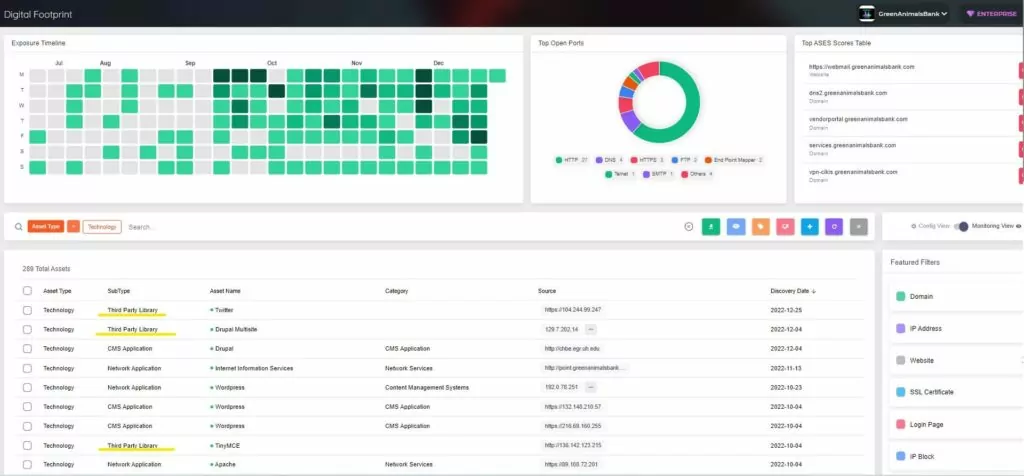
SOCRadar XTI provides organizations with 360-degree visibility across the entire digital ecosystem by including third-party/supply chain partners in their digital footprint.
Lesson 3: Human Error is Still Critical
In November 2022, a threat actor gained access to some Dropbox source codes within 130 GitHub code repositories after a successful phishing attack. The phishing attack occurred when the threat actor impersonated CircleCI, the code integration and distribution platform, to obtain employee login credentials and authentication codes. The threat actor accessed some of the code stored on the platform, including API keys used by developers.
On September 18, 2022, Rockstar Games was the victim of unauthorized third-party illegal access. The threat actor, nicknamed Teapoyuberhacher, leaked confidential data, including early development footage of the Grand Theft Auto (GTA) VI game. The breach was thought to occur when the threat actor gained access to an employee’s Slack account through social engineering.
Lesson Learned: Organizations need to educate employees about identifying and avoiding cyber threats. Also, it is crucial to deploy multi-factor authentication for employee access.
Lesson 4: Insider Threats are Increasing
On April 4, 2022, Block (CashApp’s parent company) confirmed the CashApp data breach affecting 8.2 million customers with a report to the US Securities and Exchange Commission. The CashApp data breach was caused by a former employee who accessed customer financial reports as revenge against the company.
In February 2022, a whistleblower exposed account information for about 18,000 customers valued at $100 billion at Swiss-based Credit Suisse bank. It was one of the most significant customer data exposures of 2022.
Lesson Learned: Companies must ensure that access to critical data corresponds to an employee’s specific role in the company. Also, authorities should review all critical users’ access levels. When an employee leaves, the company must revoke access to systems immediately. Additionally, implementing a zero-trust framework will improve organizational security.
Lesson 5: Importance of Monitoring Surface/Dark Web
Twitter confirmed a data breach affected 5.4 million Twitter accounts in August 2022. Threat actors claimed to gain access to the personal information of Twitter accounts through a previously reported vulnerability. The vulnerability allows third parties to obtain the Twitter accounts of users by submitting a phone number/email without any authentication, even though the user has prohibited this action in the privacy settings.
On July 21, 2022, SOCRadar dark web researchers detected a sale post titled ‘5.4 million Twitter Users’ Data is on Sale ‘on an underground forum.

Lesson Learned: Organizations should use Extended Threat Intelligence solutions that provide to identify and mitigate threats across the surface and dark web.
Conclusion
Threat actors focusing on data breaches seek to capture, exploit, and even weaponize sensitive data about customers, partners, intellectual property, or corporate trade secrets. The most vigilant and disciplined organizations also can experience data breaches. Attackers can bypass the most effective cyber defenses by exploiting weaknesses, which might be technological or human. In this context, a comprehensive cybersecurity solution that includes employee training, robust security rules and protocols, regular security audits, and incident response (IR) planning might be effective in preparing for potential data breach attacks.
An incident response (IR) plan is one of the crucial ways that guides security teams in detection, investigation, remediation, and recovery to mitigate the damage of a data breach.
SOCRadar XTI helps to maximize incident response efficiency by closely monitoring overall cyber threats and vulnerability trends tailored for the organization’s industry, geolocation, TTPs, or customized keywords.



































