APT Profile: Sandworm
Threat actors range from teenagers eager to earn quick cash to state-sponsored actors with agendas behind their operations. The agendas of these state-sponsored groups may include espionage activities on neighboring countries or attacks against critical infrastructures of opposing nations. Russia is one of the nations with a high number of APT (Advanced Persistent Threat) groups to mobilize against their targets. Among them is Sandworm, which was involved in the Russia-Ukraine war. Sandworm is one of the more active and dangerous APTs in cyberspace. Just like their namesake from the famous Dune series by Frank Herbert, they pose a significant danger to the safety of people, especially with their objective of targeting critical infrastructures.
Who is Sandworm?
Sandworm, also known as ELECTRUM, Black Energy, and VOODOO BEAR, is a pernicious APT that has been attributed to Russia’s General Staff Main Intelligence Directorate (GRU) Main Center for Special Technologies (GTsST) military unit 74455 by the US. They have been actively playing a role in cyberspace for Russia’s strategic benefits since at least 2009, conducting many major attacks against multiple countries and causing billions of dollars in damage. They mostly rely on spear phishing to deliver malware and leverage from zero days.

Who are Sandworm’s Targets?
Researchers observed the Sandworm conducting malicious activities across Europe, North America, and Asia. They primarily target Industrial Control Systems (ICS) in critical areas such as energy & utilities, national security, international affairs, and telecommunications around the globe. However, since their emergence, under Russia’s strategic objectives, their main target seems to be Ukraine. In the last decade, they have performed multiple high-impact attacks against Ukraine on critical infrastructures.
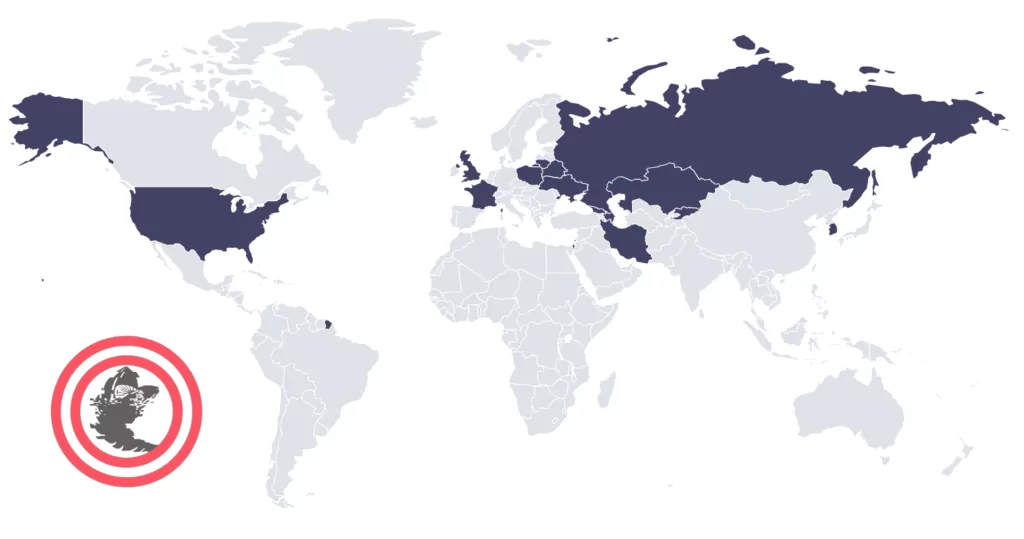
What are the Motivations Behind Sandworm’s Attacks?
With the Russian invasion of Ukraine, there was a substantial increase in cyberattacks in the region. Critical infrastructures were affected, and the Russian cyber forces targeted top-secret information. The cyber forces used to diminish the morale of Ukrainian citizens through defacements or other destructive attacks on Ukraine’s critical infrastructures, such as DDoS attacks on government portals.
The war was not the beginning of cyber attacks on Ukraine by Russia. The origins of the Russian attacks can be pinpointed to even a decade earlier. The first recorded Russian cyberattacks against Ukraine happened during the mass protests in 2013. The war amplified the attacks in number and magnitude. Sandworm was one of the front runners of the Russian cyber forces targeting Ukraine during this decade, and they still are.

SOCRadar tracks the Russia-Ukraine Cyberwar as a campaign. In SOCRadar Labs, you can find and track the events.
How does Sandworm Operate?
Sandworm, through its operation lifetime, has multiple records of attacks on ICS. The group is affiliated with two of the first four types of known ICS-targeting malware, “BlackEnergy” and “Industroyer.” Both targeted Ukrainian critical infrastructures. They did not stop there and developed “Industroyer2” ICS-targeting malware and used it against Ukraine. However, this time they added another layer with the inclusion of “CaddyWiper,” “ORCSHRED,” “SOLOSHRED,” and “AWFULSHRED.” The aim was to hamper the recovery process and destroy disks on the targeted machines. In another attack in 2017, they deployed “NotPetya” as a wiper on Ukraine, which is considered a skewed version of “Petya” ransomware.
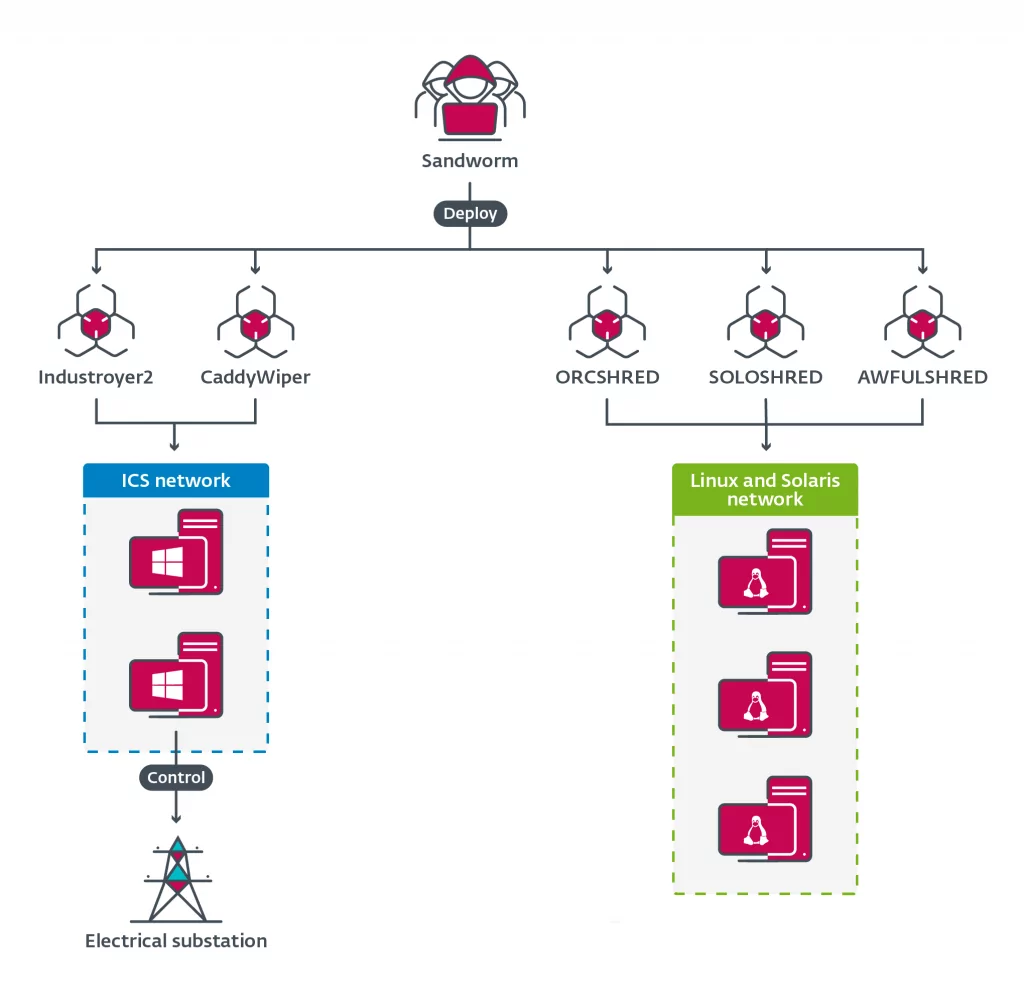
Even though it is their main area, Sandworm does not only manage ICS attacks with malware and altered versions of ransomware as wipers. They started to deploy legitimate ransomware such as the “RansomBoggs” and “Prestige” against organizations in Ukraine and other countries. These attacks are attributed to Sandworm because RansomBoggs’ PowerShell script is nearly identical to the deployment of Industroyer2. The same script, POWERGAP, was also used to deliver CaddyWiper.
Which Tools Does Sandworm Use?
BlackEnergy
BlackEnergy is a malware toolkit used by criminal and APT actors since 2007. Although initially designed to create botnets to conduct Distributed Denial of Service (DDoS) attacks, its use has evolved over the last decade to support various plug-ins. It is a well-known malware leveraged by Sandworm in multiple attacks. Variants include BlackEnergy 2 and BlackEnergy 3.
Industroyer
Industroyer is a sophisticated malware framework designed to disrupt ICS, particularly components used in power grids. Sandworm used Industroyer and its variants in multiple attacks targeting power grids in Ukraine. This is the first publicly known malware specifically designed to target and impact operations in the electric grid. Variants include Industroyer2.
KillDisk
KillDisk is a disk-wiping tool designed to overwrite files with random data to render the OS unbootable. Sandworm first used it in attacks against Ukraine in 2015 as a component of BlackEnergy. Since then KillDisk has evolved into stand-alone malware used by Sandworm and other threat actors.
NotPetya
NotPetya is an altered variant of Petya encryption malware. NotPetya acts as ransomware. It irrecoverably destroys data and disk structures on compromised systems. Sandworm used it in the 2017 worldwide attacks causing 10$ billion in damage. NotPetya also contains worm-like features to spread itself across a computer network using the SMBv1 exploits EternalBlue and EternalRomance.
Olympic Destroyer
Olympic Destroyer is malware that renders infected computer systems inoperable. It acts as a worm spreading across networks to maximize its destructive impact. Sandworm used it against the 2018 Pyeongchang Winter Olympics.
CaddyWiper
CaddyWiper is a wiper malware designed to damage target systems by erasing user data, programs, and hard drives. Sandworm used it in attacks on Ukrainian government agencies before the Russian invasion.
Other tools that are potentially associated with Sandworm can be found on SOCRadar.
Conclusion
When the Russian invasion of Ukraine began on February 24, 2022, many security researchers predicted that Russia would use all of its cyber capabilities to complete its mission. In light of all the information in the article, it is clear that Russian cyber warfare capabilities are undeniably devastating and have been used in the war. Yet, they were not as effective as the previous attacks. If we look at the attacks attributed to Sandworm, such as the 5 year-long cyber espionage activity, we can see that their previous attacks were more sophisticated and harmful. This situation might be the result of two main factors. One is that Ukraine received tremendous help outside its nation to prevent Russian cyberattacks. The other one is that large-scale destructive attacks require extensive preparation and patience, which means time is needed. But in war, the time is short for these sophisticated attacks.
What are the Security Recommendations Against Sandworm?
- ICS is the main target of the Sandworm APT group. So, ICS should have minimal internet dependency. They must be put behind firewalls and isolated from the external network.
- SOCRadar tracks threat actors continuously and gathers IOCs for the tracked actors. You can feed security devices like firewalls, IPSs, or SOAR solutions for better security against potential threats.
- Cybersecurity researchers detected that Sandworm leverages phishing to gain initial access in some cases. Train your staff to raise security awareness to prevent potential phishing attacks.
- Sandworm used ransomware or wipers in some of its attacks. Back up your data to prevent further damage and reinstate the affected systems rapidly.
Keep an eye on the external attack surface of your environment. Make sure to patch all the critical vulnerabilities and not leave any vulnerable ports open. SOCRadar can aid you in this endeavor with its External Attack Surface Management.
MITRE ATT&CK Techniques
| Techniques – Enterprise | ID |
| Reconnaissance | |
| Active Scanning: Vulnerability Scanning | T1595.002 |
| Gather Victim Host Information: Software | T1592.002 |
| Gather Victim Identity Information: Email Addresses | T1589.002 |
| Gather Victim Identity Information: Employee Names | T1589.003 |
| Gather Victim Network Information: Domain Properties | T1590.001 |
| Gather Victim Org Information: Business Relationships | T1591.002 |
| Phishing for Information: Spearphishing Link | T1598.003 |
| Search Open Websites/Domains | T1593 |
| Search Victim-Owned Websites | T1594 |
| Resource Development | |
| Acquire Infrastructure: Domains | T1583.001 |
| Acquire Infrastructure: Server | T1583.004 |
| Compromise Infrastructure: Botnet | T1584.005 |
| Develop Capabilities: Malware | T1587.001 |
| Establish Accounts: Social Media Accounts | T1585.001 |
| Establish Accounts: Email Accounts | T1585.002 |
| Obtain Capabilities: Tool | T1588.002 |
| Obtain Capabilities: Vulnerabilities | T1588.006 |
| Initial Access | |
| External Remote Services | T1133 |
| Phishing: Spearphishing Attachment | T1566.001 |
| Phishing: Spearphishing Link | T1566.002 |
| Supply Chain Compromise: Compromise Software Supply Chain | T1195.002 |
| Trusted Relationship | T1199 |
| Valid Accounts: Domain Accounts | T1078.002 |
| Execution | |
| Command and Scripting Interpreter: PowerShell | T1059.001 |
| Command and Scripting Interpreter: Windows Command Shell | T1059.003 |
| Command and Scripting Interpreter: Visual Basic | T1059.005 |
| Exploitation for Client Execution | T1203 |
| User Execution: Malicious Link | T1204.001 |
| User Execution: Malicious File | T1204.002 |
| Windows Management Instrumentation | T1047 |
| Persistence | |
| Account Manipulation | T1098 |
| Create Account: Domain Account | T1136.002 |
| Server Software Component: SQL Stored Procedures | T1505.001 |
| Server Software Component: Web Shell | T1505.003 |
| Defense Evasion | |
| Deobfuscate/Decode Files or Information | T1140 |
| Impair Defenses: Disable Windows Event Logging | T1562.002 |
| Indicator Removal: File Deletion | T1070.004 |
| Masquerading: Match Legitimate Name or Location | T1036.005 |
| Obfuscated Files or Information: Software Packing | T1027.002 |
| System Binary Proxy Execution: Rundll32 | T1218.011 |
| Credential Access | |
| Brute Force: Password Spraying | T1110.003 |
| Credentials from Password Stores: Credentials from Web Browsers | T1555.003 |
| Input Capture: Keylogging | T1056.001 |
| Network Sniffing | T1040 |
| OS Credential Dumping: LSASS Memory | T1003.001 |
| Discovery | |
| Account Discovery: Domain Account | T1087.002 |
| Account Discovery: Email Account | T1087.003 |
| File and Directory Discovery | T1083 |
| Remote System Discovery | T1018 |
| System Information Discovery | T1082 |
| System Network Configuration Discovery | T1016 |
| System Network Connections Discovery | T1049 |
| System Owner/User Discovery | T1033 |
| Lateral Movement | |
| Lateral Tool Transfer | T1570 |
| Remote Services: SMB/Windows Admin Shares | T1021.002 |
| Collection | |
| Data from Local System | T1005 |
| Command and Control | |
| Application Layer Protocol: Web Protocols | T1071.001 |
| Data Encoding: Standard Encoding | T1132.001 |
| Ingress Tool Transfer | T1105 |
| Non-Standard Port | T1571 |
| Proxy | T1090 |
| Remote Access Software | T1219 |
| Web Service: Bidirectional Communication | T1102.002 |
| Exfiltration | |
| Exfiltration Over C2 Channel | T1041 |
| Impact | |
| Data Destruction | T1485 |
| Defacement: External Defacement | T1491.002 |
| Disk Wipe: Disk Structure Wipe | T1561.002 |
| Endpoint Denial of Service | T1499 |
| Techniques – ICS | ID |
| Initial Access | |
| Exploit Public-Facing Application | T0819 |
| External Remote Services | T0822 |
| Spearphishing Attachment | T0865 |
| Remote Services | T0886 |
| Execution | |
| Graphical User Interface | T0823 |
| Command-Line Interface | T0807 |
| Scripting | T0853 |
| Persistence | |
| System Firmware | T0857 |
| Valid Accounts | T0859 |
| Evasion | |
| Masquerading | T0849 |
| Lateral Movement | |
| Lateral Tool Transfer | T0867 |
| Command and Control | |
| Connection Proxy | T0884 |
| Inhibit Response Function | |
| Block Command Message | T0803 |
| Block Reporting Message | T0804 |
| Device Restart/Shutdown | T0816 |
| Impair Process Control | |
| Unauthorized Command Message | T0855 |
References
- https://www.justice.gov/opa/press-release/file/1328521/download
- https://www.welivesecurity.com/2022/04/12/industroyer2-industroyer-reloaded/
- https://www.dragos.com/wp-content/uploads/CrashOverride-01.pdf
- https://attack.mitre.org/groups/G0034
- https://attack.mitre.org/groups/G0034/