
Threat Landscape in the Aviation Industry for H1 of 2023
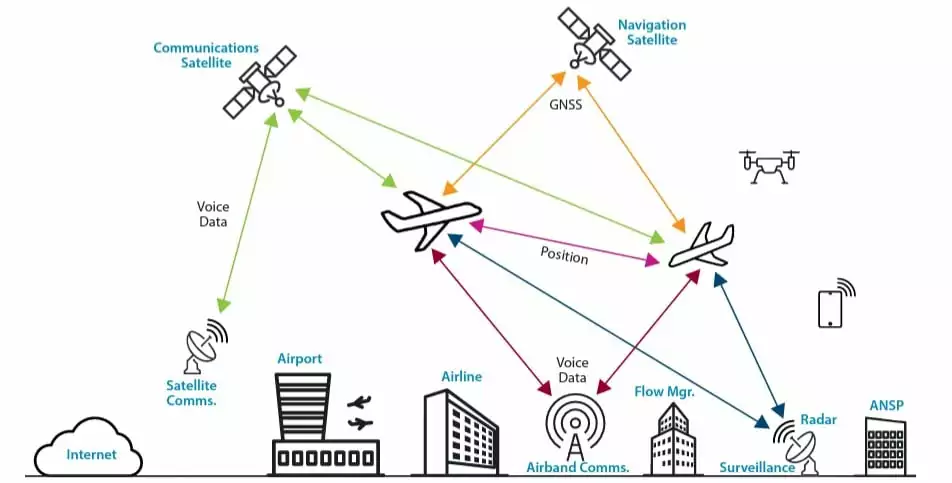
The aviation industry relies on interconnected networks and systems to facilitate seamless operations. Airlines, airports, manufacturers of aircraft, and numerous service providers are just a few of the many stakeholders in the complex ecosystem that makes up the aviation industry’s digital landscape. The nature of the complexity can create potential weak points or vulnerabilities that cybercriminals could exploit.
Furthermore, the aviation industry heavily relies on cutting-edge technologies, from ground operations to flight management. However, new technologies may also translate into new attack surfaces for cybercriminals.
High-value targets in the aviation industry handle a vast amount of valuable data, including passenger information, financial records, and proprietary technology. All highlighted topics cause threat actors to be drawn to this sector as a target, with motivations ranging from data and monetary theft to causing disruptions and harm.
Eurocontrol predicts that air traffic in Europe this summer will surpass last year’s levels by up to 15%, reaching a potential daily count of 37,000 flights. Considering this significant increase, analyzing the threat landscape of the aviation industry in the first half of 2023 will provide valuable insights for the year’s second half.
In a blog post published in September 2022 by SOCRadar, cyber incidents in the aviation industry were reviewed within the scope of the events monitored by Eurocontrol, a pan-European, civil-military organization. The analysis was based on data from the EATM-CERT (European Air Traffic Management Computer Emergency Response Team) Aviation Cyber Event Map, published by Eurocontrol.
For the cyber threat landscape evaluation conducted for the first half of 2023 in the aviation industry, the analyses made in the previous blog post were repeated, this time including data for the first half of 2023.
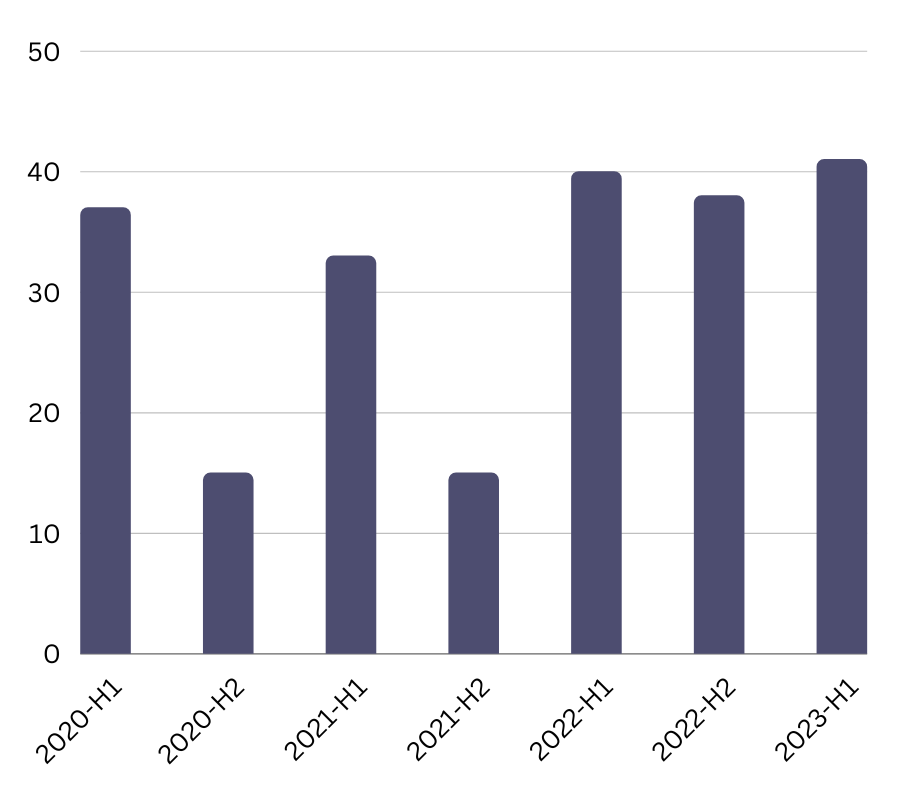
As seen on the graphic, based on the data from EATM-CERT Aviation Cyber Event Map, the consistent occurrence of attacks on the aviation industry over the last three periods underscores the sustained interest of threat actors in targeting this critical industry.
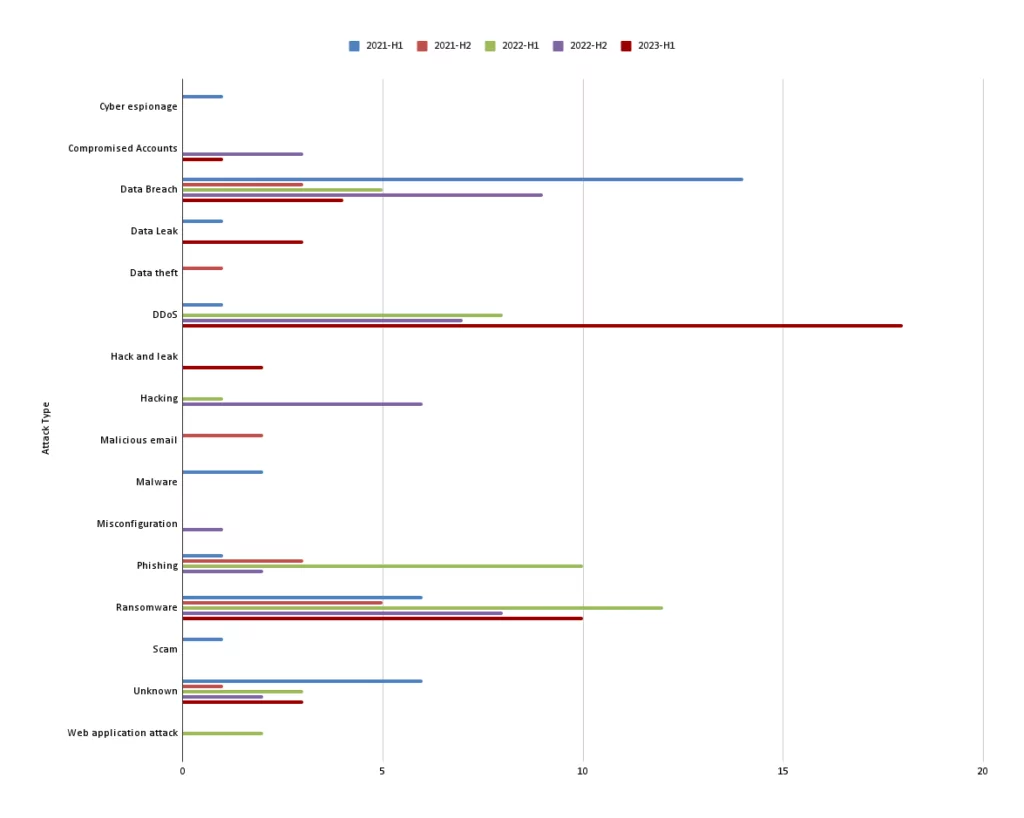
Upon evaluating the data considering the attacks type from the beginning of 2021 based on 6-month periods, a notable finding emerged for the first half of 2023: a significant rise in Distributed Denial of Service (DDoS)attacks.
DDoS Attacks on the Aviation Industry
The number of DDoS attacks in the aviation industry has increased significantly since the second half of 2022. The most notable attacks during this period were those carried out by the pro-Russian hacktivist group Killnet against several major US airports.
In October, KillNet claimed responsibility for massive Distributed Denial-of-Service (DDoS) attacks against several major airports, including Hartsfield-Jackson Atlanta International Airport (ATL), Los Angeles International Airport (LAX), Orlando International Airport (MCO), Chicago O’Hare International Airport (ORD), Phoenix Sky Harbor International Airport (PHX) and Denver International Airport (DIA) in the US.
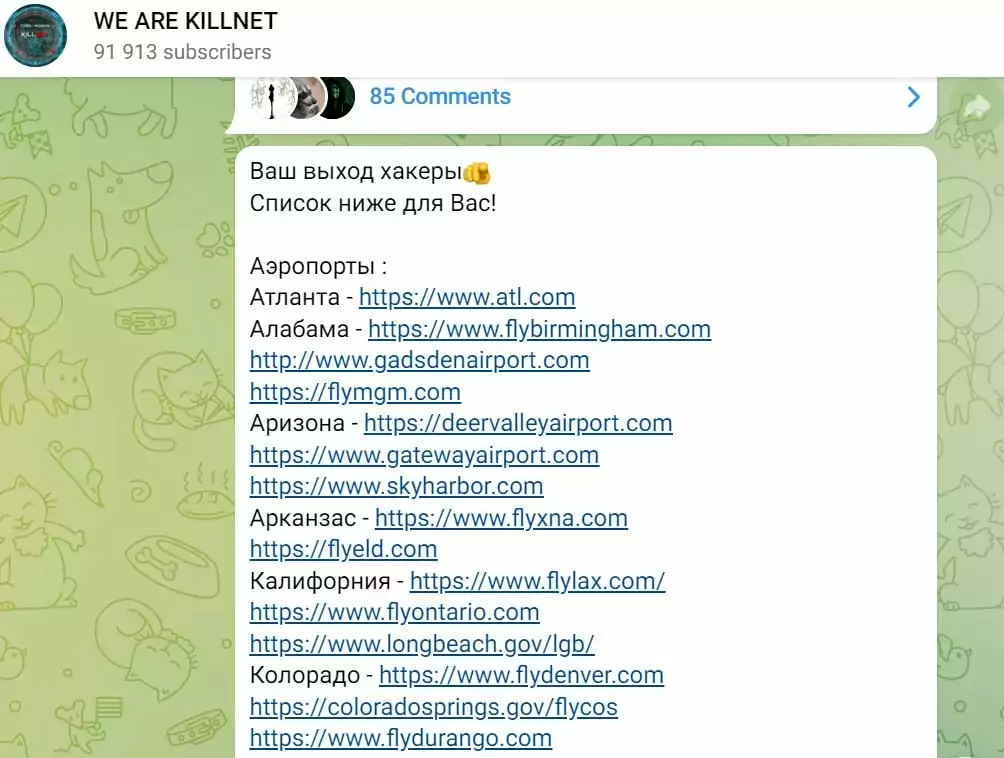
Killnet, which was only known as a DDoS attack service that subscribers could rent and employ before, evolved into an attacker group during the Russia-Ukraine conflict, known for its DDoS campaigns against countries who supported Ukraine. Killnet has conducted numerous attacks, targeting a wide range of organizations, including government agencies, media outlets, and businesses. Within the first few months following the Russian invasion, over 30 airports across Europe were victims of their attacks.
The Transport Security Administration (TSA) issued a statement clarifying that there was no impact on airport operations, and the attackers did not gain access to airport systems despite successfully taking the websites temporarily offline. However, these attacks highlight the growing threat of DDoS attacks to the aviation industry.
In light of these developments, SOCRadar Researchers focused on the growing issue of DDoS attacks targeting aviation entities and identified 124 DDoS attacks directed at airports, airlines, and international aviation authorities in the first half of 2023.
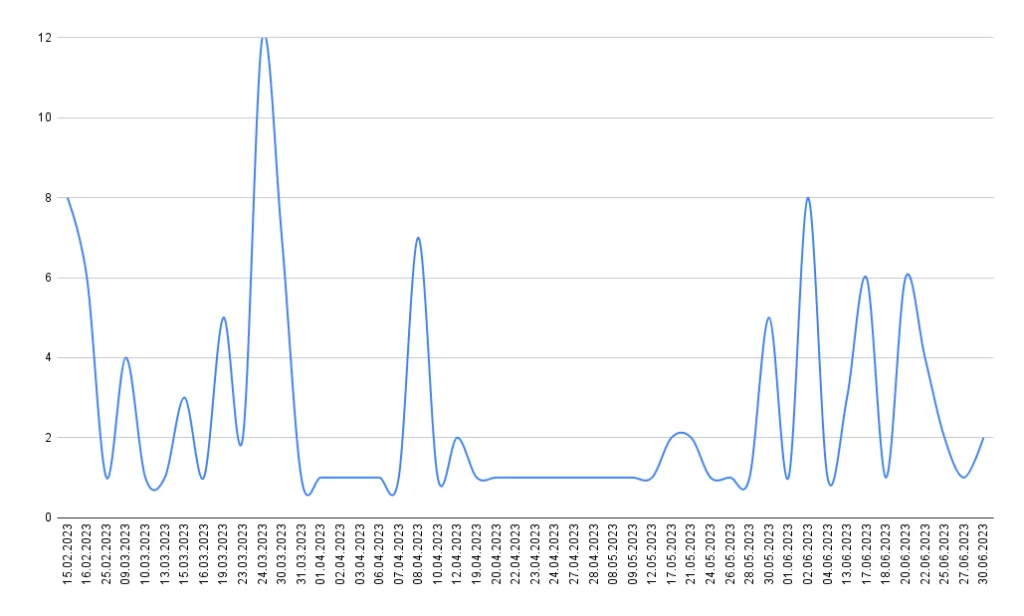
The daily distribution of DDoS attacks aligns with the patterns observed during large-scale hacktivism campaigns orchestrated by threat actors. For instance, Australia faced a campaign in March because of some clothing displayed at the Melbourne Fashion Festival. Australia reported being targeted by cyberattacks from multiple malicious groups.
Similarly, in February, Sweden experienced a campaign in response to the actions of far-right extremist Rasmus Paludan.
Additionally, throughout the whole analyzed period, the Ukraine-Russia conflict had a noticeable impact, with cyber-attacks occurring against various targets. For instance, Switzerland became a target of cyber attacks in mid-June following the country’s adoption of an EU sanction package against Russia.
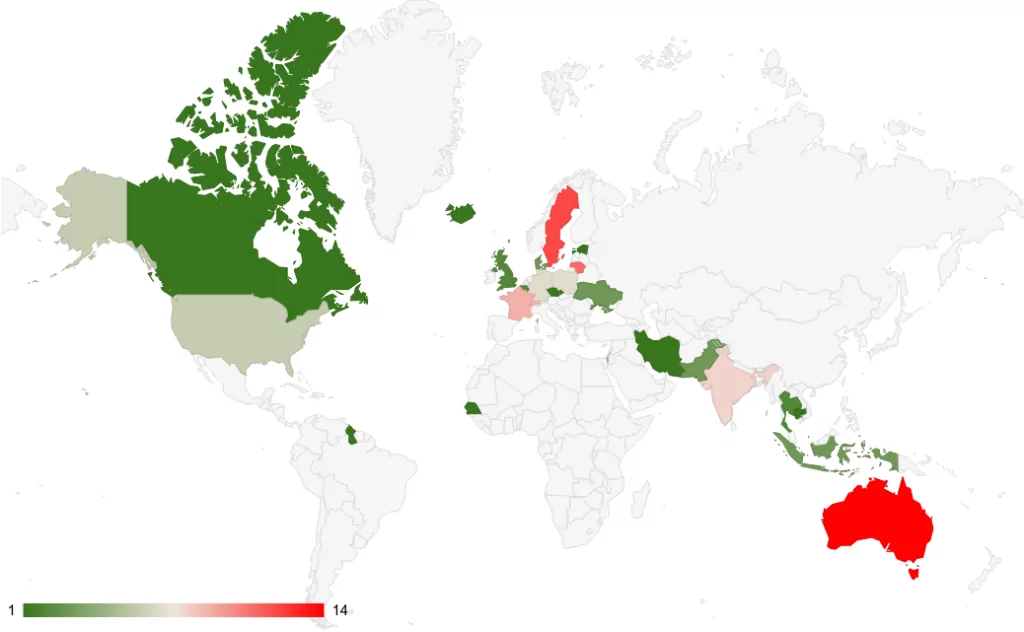
The attack counts on various countries provide valuable insights into the targeting priorities of threat actors and the potential motivations behind their actions.
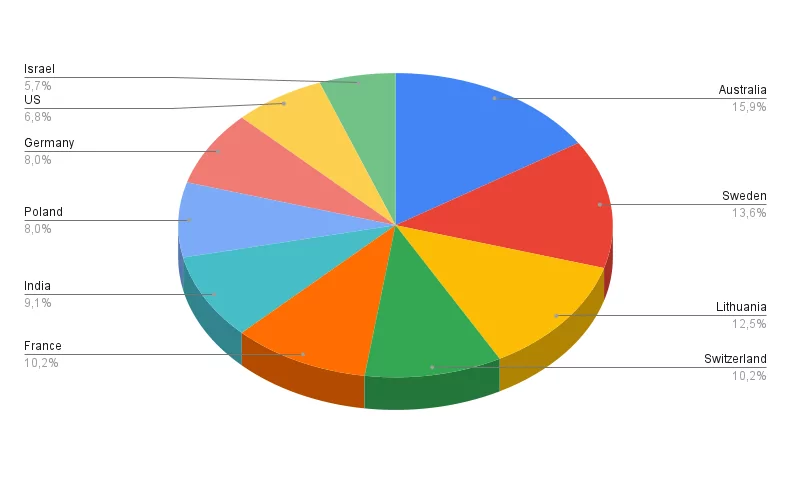
The top 10 targeted countries represent diverse regions and geopolitical contexts. Besides the top 10 targeted countries, it’s important to note that threat actors are not limited to large-scale attacks. They also target smaller countries like Malta, as well as international authorities such as Eurocontrol. This suggests that cyber threat actors operate globally and are not limited to a specific geographic area.
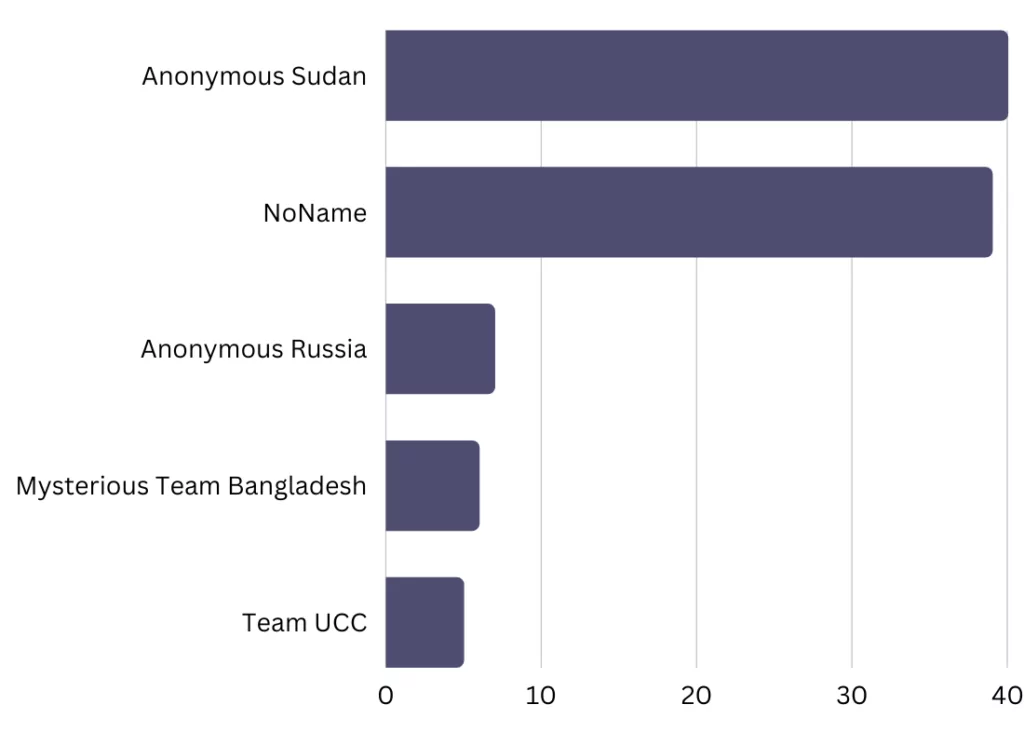
The top two threat actors, Anonymous Sudan and NoName, have gained prominence through their recent DDoS attacks, with the aviation industry being a notable target among their activities. Even if none of these threat actors specifically target the aviation industry, it is still a target along with the other critical infrastructures. And it is worth highlighting that the aviation industry often finds itself among the primary targets for these threat actors.
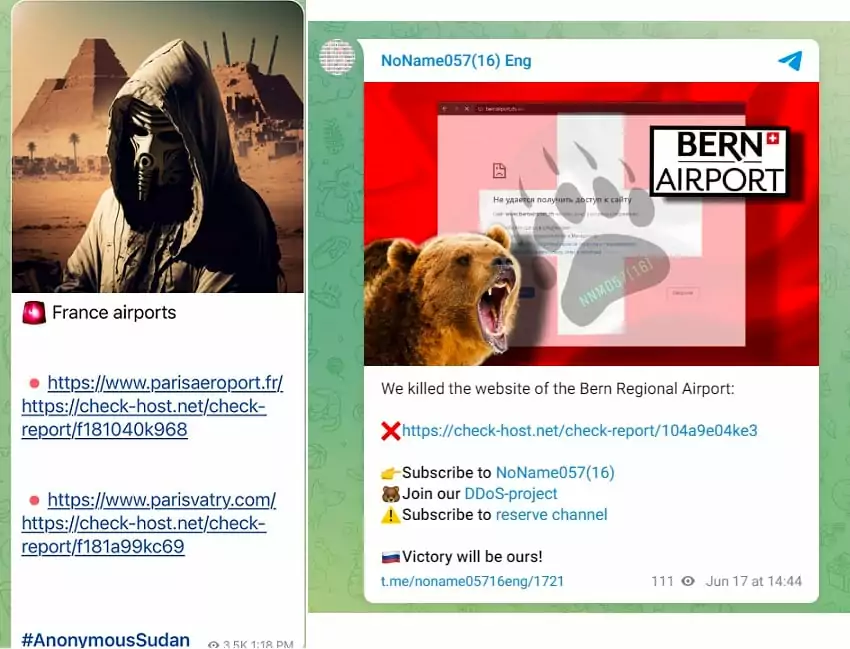
DDoS attacks, or Distributed Denial-of-Service attacks, are attempts to make a system unavailable by flooding it with traffic. These attacks can endanger passenger safety, disrupt air traffic by making it difficult for travelers to get updates about their scheduled flights or booking airport services, and cause economic issues.
Supply Chain Attacks on the Aviation Industry
The aviation industry is particularly vulnerable to supply chain attacks because it relies on a complex network of suppliers and vendors for everything from aircraft parts to software.
On June 23, American Airlines and Southwest Airlines announced a data breach that occurred through a third-party vendor called Pilot Credentials (pilotcredentials.com). The breach was reported to Maine’s Office of the Attorney General as part of the breach notification process. An individual gained unauthorized access to Pilot Credentials’ systems containing information provided by certain applicants during the pilot and cadet hiring process on April 30.
Both airlines were notified of the incident on May 3. It is important to note that the breach was limited to the third-party vendor’s systems and did not compromise or impact the airlines’ own networks or systems. The attackers could access sensitive information such as names, birth dates, Social Security and passport numbers, and driver’s and pilot-license numbers of applicants for pilot and cadet positions.
American Airlines stated that the data breach affected 5,745 pilots and applicants, while Southwest Airlines reported 3,009 individuals impacted by the breach.
![SOCRadar XTI Threat Hunting Module: ‘pilotcredentials[.]com’ search output](https://socradar.io/wp-content/uploads/2023/07/10pilotcredential-1024x391.jpg)
A massive supply chain attack in the first half of 2023, MOVEit, also affected the aviation industry. Dublin Airport Authority (DAA) was one of many global companies affected by the attack on the file transfer software tool MOVEit, used by Aon, a global professional services and management consulting firm.
A security flaw (CVE-2023-34362) in Progress Software’s MOVEit product, discovered at the end of May, allowed threat actors to gain unauthorized access to sensitive information.
Aon was the victim of a third-party data breach through the file-transfer platform MOVEit, which led to the online publication of information about its clients. As a result of the cyberattack on Aon, payment and benefits details of about 2,000 staff members at DAA were compromised.
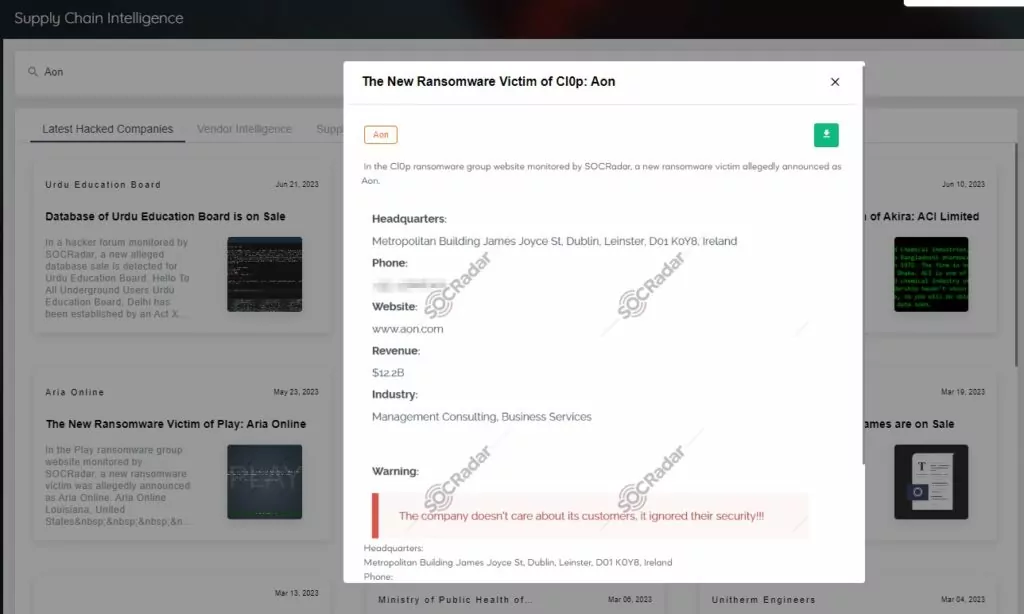
The MOVEit supply chain attacks affected a wide range of entities from different industries. British Airways, Allegiant Air (Las Vegas, USA), and Aer Lingus (Ireland) were victims of the aviation industry along with DAA.
Conclusion
The aviation industry is a critical infrastructure increasingly reliant on IT systems and holds substantial value in global connectivity, transportation, and national security. It makes the aviation industry an attractive target for those seeking to disrupt operations or gain unauthorized access to sensitive information.
The analysis of the 2023 H1 threat landscape for the aviation industry highlights the importance of supply chain security and the growing impact of DDoS attacks. The aviation industry must adopt a proactive and intelligence-driven approach to cybersecurity to deal with the evolving threat landscape. This includes leveraging threat intelligence sources, collaborating with industry peers, and staying updated on emerging trends and vulnerabilities.
Within this framework, the SOCRadar XTI platform presents an extended cyber threat intelligence solution enhanced by External Attack Surface Management (EASM) and Digital Risk Protection (DRP). Notably, considering the outputs of the 2023 H1 aviation threat landscape analysis, the platform can help companies with a Supply Chain Intelligence module featuring a “Vendor Intelligence” tab that delivers real-time news updates on vendors, as well as a “Supply Chain Report” feature providing comprehensive reports on user-specific supply chain companies.
Additionally, as part of the SOCRadar Labs’ free SOC toolset, the DoS Resilience Service enables users to assess the resilience of their domains or subdomains against DoS attacks. This service equips organizations with valuable insights to safeguard their digital infrastructure against disruptive denial-of-service threats.
Embracing a proactive cyber threat intelligence perspective will empower the industry to stay ahead of adversaries, protect its digital ecosystem, and maintain the trust and confidence of passengers, partners, and stakeholders. By integrating extended cyber threat intelligence solutions into risk management practices, the aviation industry can better anticipate and mitigate cyber threats, enhance its defenses, and ensure critical operations’ safety, reliability, and resilience.



































