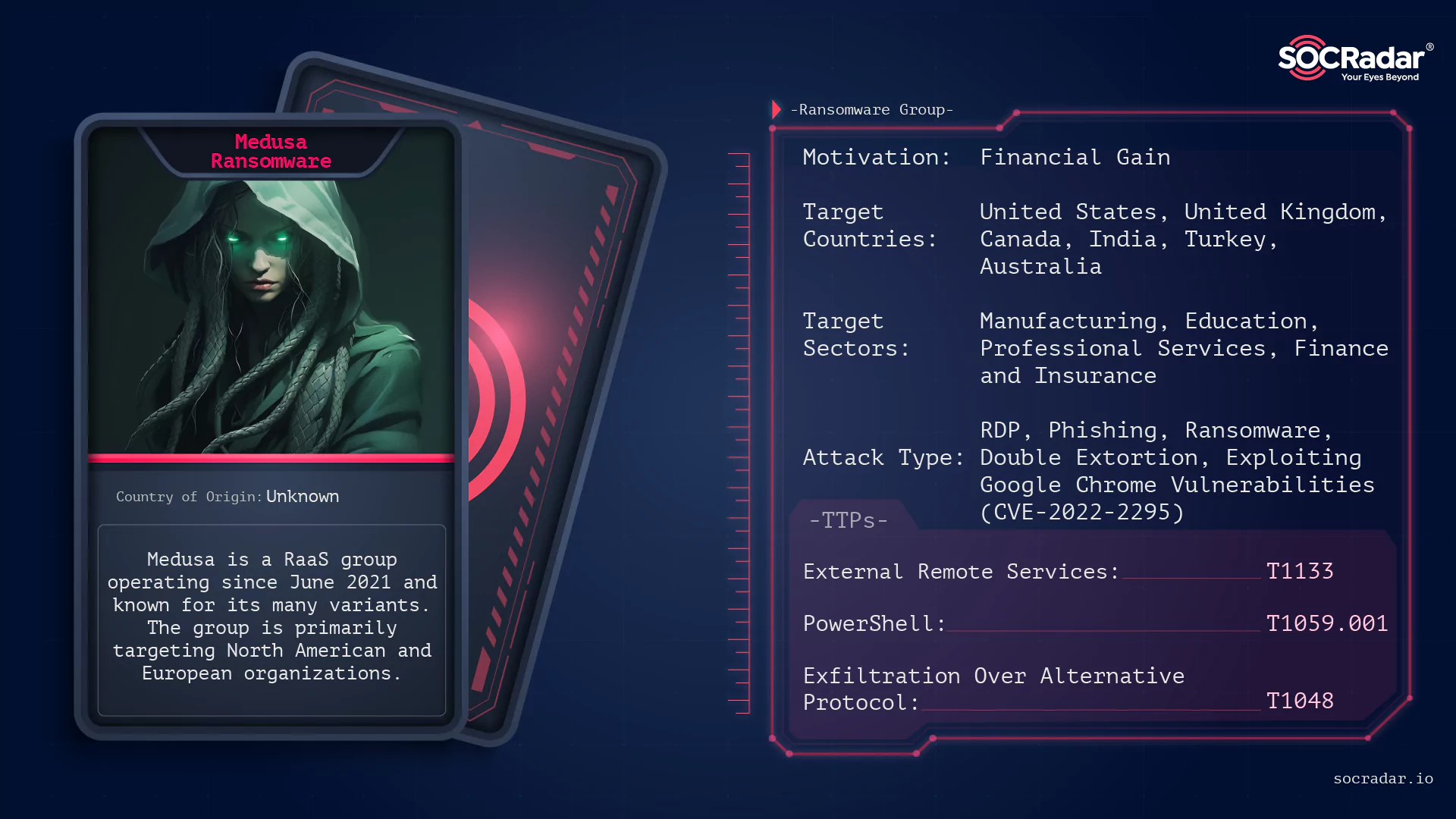
Dark Web Profile: Medusa Ransomware (MedusaLocker)
[Update] March 13, 2025: CISA, FBI, and MS-ISAC Warn of Medusa Ransomware Threats in New Advisory
In ancient Greek mythology, Medusa stands as one of the most iconic and feared figures. With a head full of venomous snakes in place of hair, she had the power to turn anyone who gazed upon her into stone. This Gorgon, once a beautiful maiden, became synonymous with terror and dread.
Fast forward to 2023, and the name Medusa has resurfaced, not in tales of mythology, but in the realm of cybersecurity. Medusa Ransomware, much like its mythological counterpart, paralyzes its victims, holding their data hostage and turning digital systems into metaphorical stone.
This article aims to shed light on the intricacies of this ransomware, offering a comprehensive understanding of its attacks, targets, and malicious endeavors.
Who is Medusa Ransomware Group?
Since its first sighting in June 2021, Medusa Ransomware (or MedusaLocker) has been on the radar of cybersecurity experts. Operating under the Ransomware-as-a-Service (RaaS) model, the Medusa Ransomware group collaborates with global affiliates, making its reach and impact even more widespread.

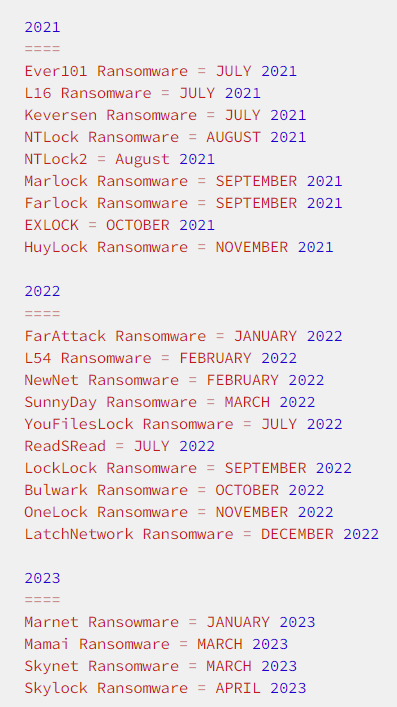
Medusa Ransomware is not just another name in the long list of ransomware threats; it is a multifaceted menace, much like the many serpentine tendrils of Medusa’s hair. Each encrypted file, bearing a variety of extensions, reminds us of the numerous snakes that crowned the Gorgon’s head. The most prominent among these is the unmistakable “.MEDUSA” extension, a signature mark of this ransomware’s venomous touch.
Some of the encrypted file extensions of Medusa Ransomware are:
The reason why there are so many file extensions is probably because there are many more variants of Medusa Ransomware, or MedusaLocker, than other ransomware:
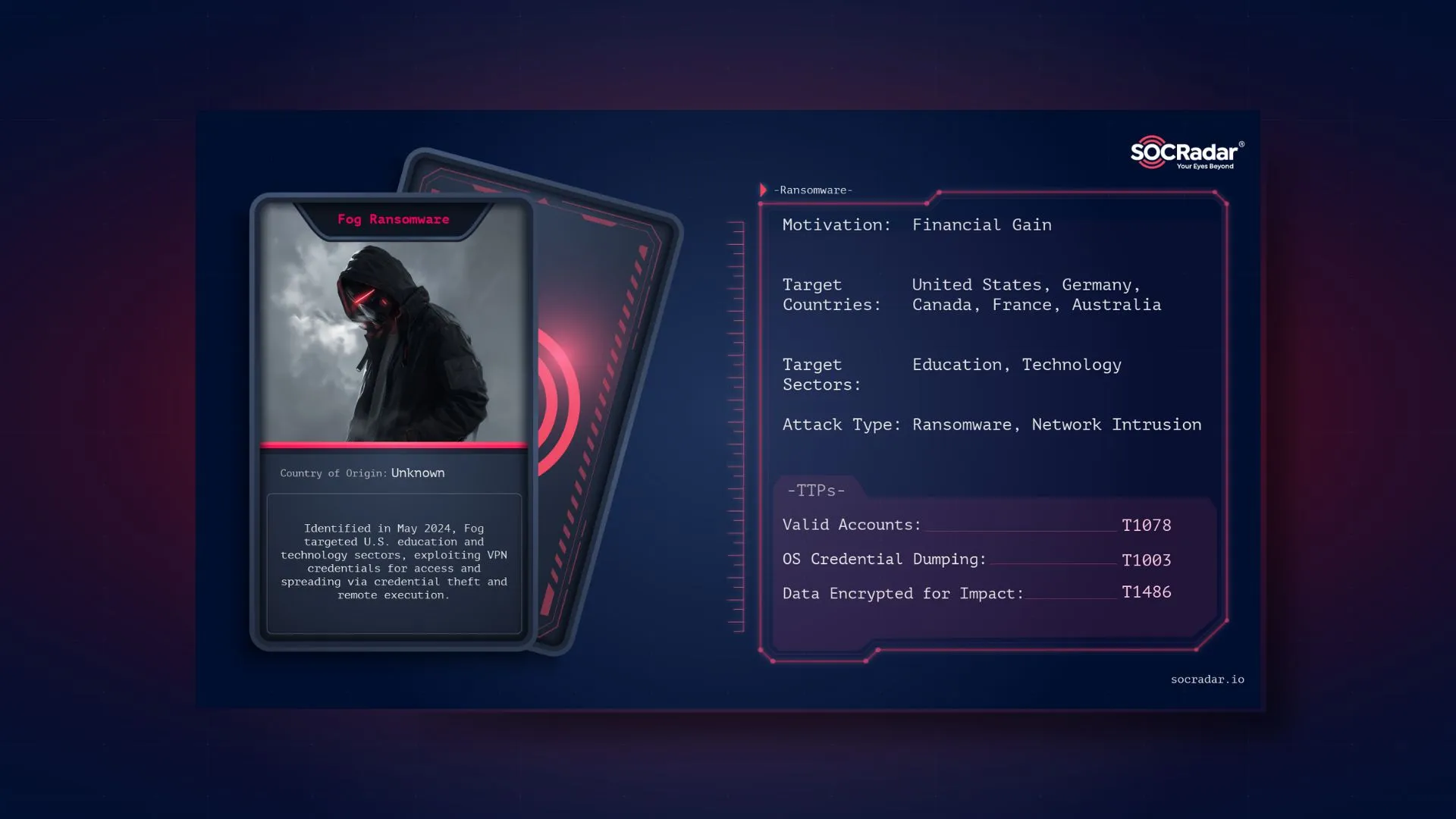
How does Medusa Ransomware Group attack?
Understanding Medusa’s attack strategy is crucial to devising countermeasures. The ransomware predominantly gains access to systems through vulnerable Remote Desktop Protocols (RDP) and deceptive phishing campaigns. Once it breaches a system, Medusa employs PowerShell for command execution, systematically erasing shadow copy backups to prevent data restoration. It does not stop there; the ransomware escalates its system privileges, deactivates defense mechanisms, and spreads its tentacles across the network. The culmination of its attack is the encryption of data and the presentation of a ransom note demanding payment in exchange for decryption.
Medusa Ransomware is observed using a few exploits from 2022:
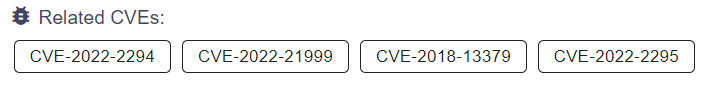
To give an example, Medusa Ransomware exploited the “Type Confusion in V8 in Google Chrome” vulnerability, known as CVE-2022-2295 to launch its malicious attacks, which has high severity.
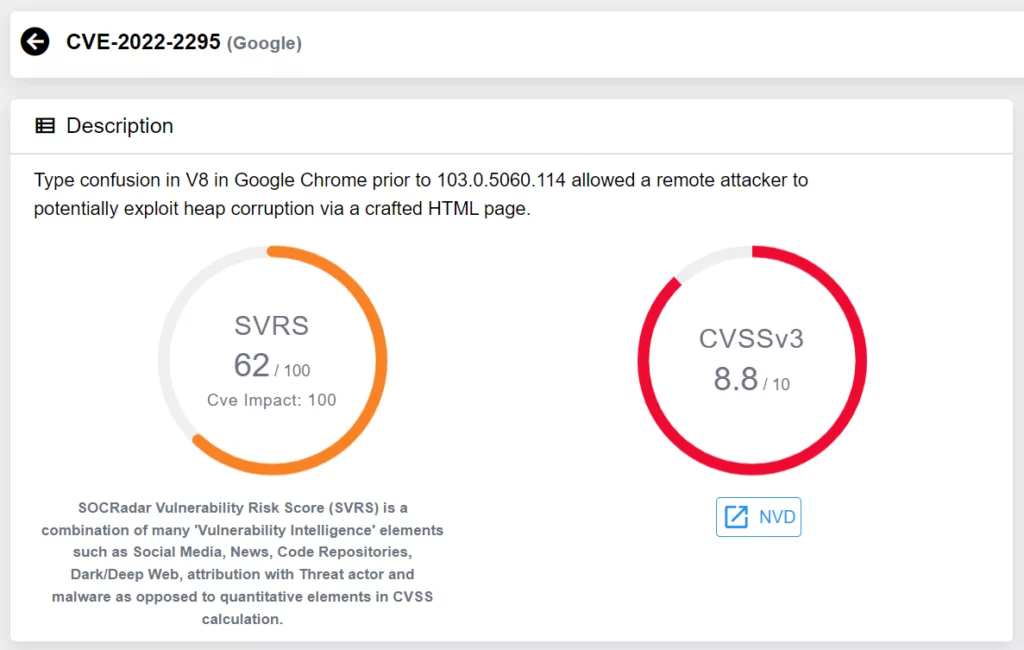
There are multiple variants of Medusa, and the main difference between these variants is the ransom note.
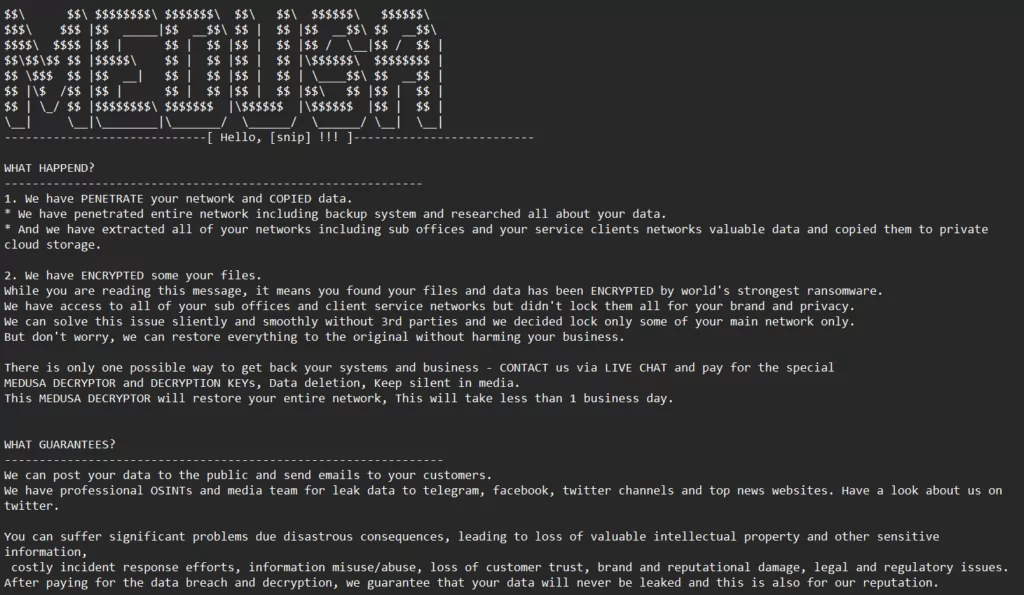
While some ransom notes are in TXT format, others can be found in HTML files, it can be said that we have observed that the most current variants have HTML files.
Looking at the various variants of Medusa, we observed that they have the same process trees:
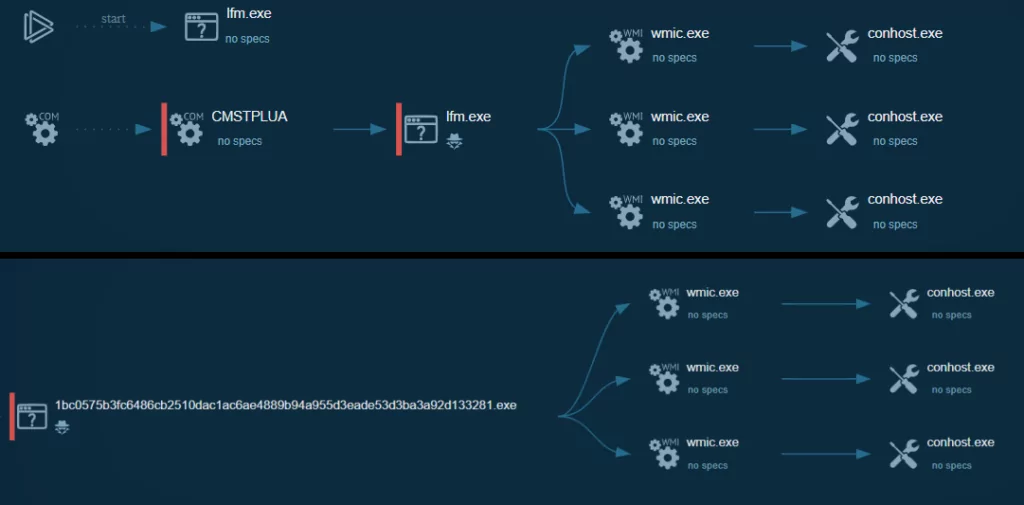
A Quick Look into Medusa Blog
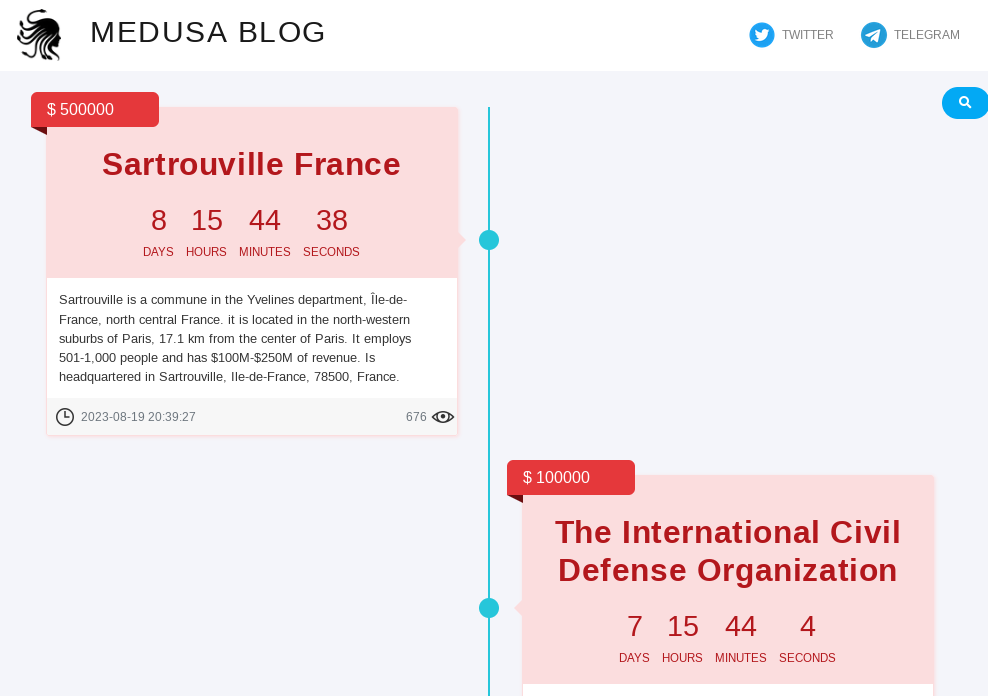
Medusa Ransomware group shares their victim announcements via Medusa Blog. The header of the page shows Telegram and Twitter links in addition to their logos.
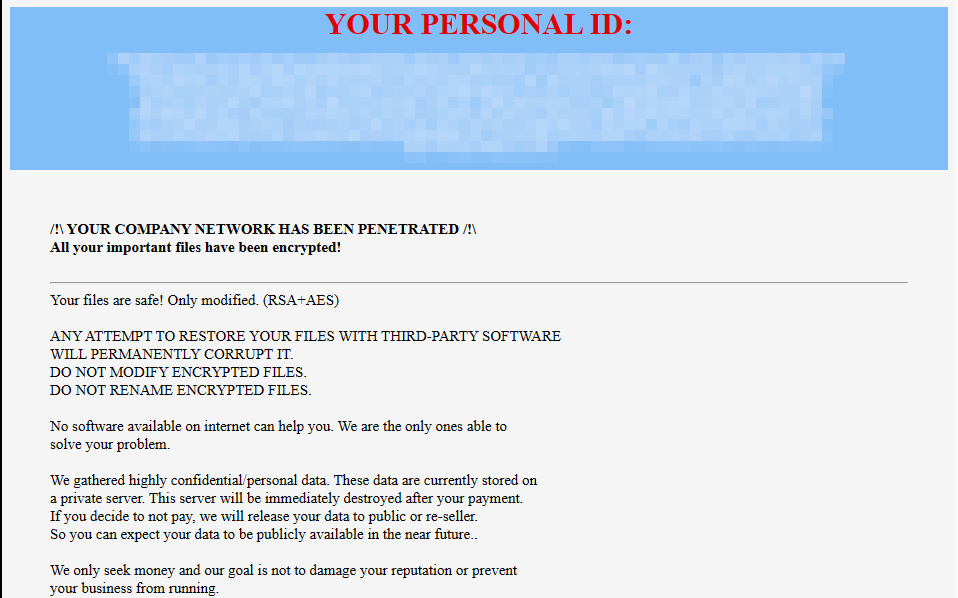
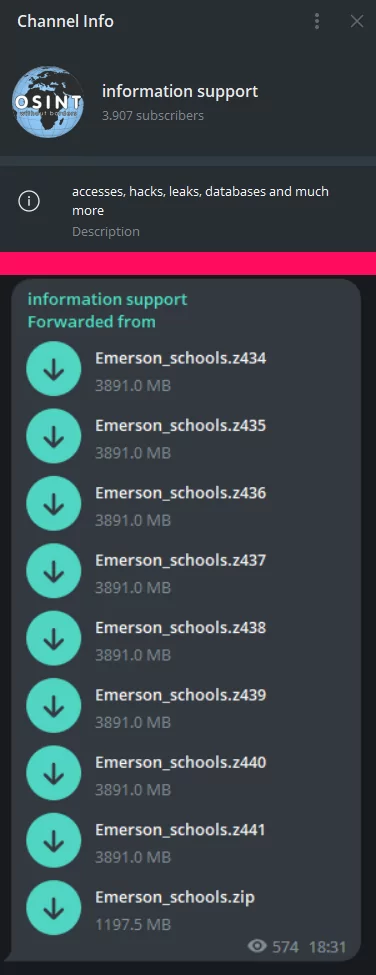
Some variants have contact information in their Ransom note, which includes an email called “information support”, as well as a Telegram channel with the same name, through which they share the leaked data of their victims:
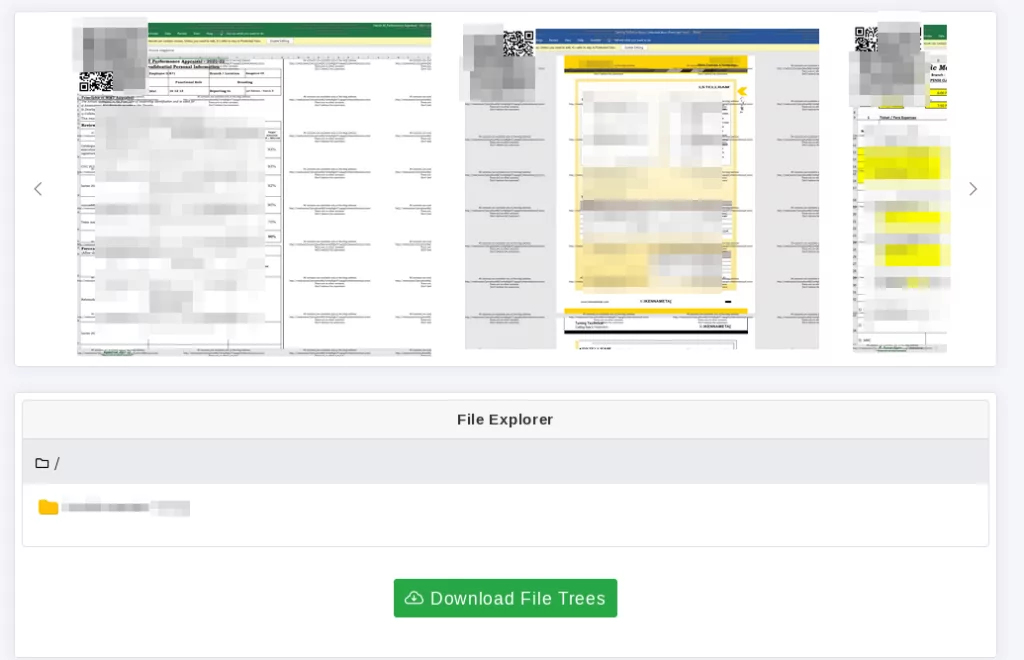
When clicking on the victim announcement, the victim’s announcement page opens. At the top of the page there is a countdown timer if the data has not been leaked, otherwise it says “PUBLISHED”.

The rest of the page contains screenshots of the data Medusa added as evidence and an interactive file explorer.
What are the targets of Medusa Ransomware?
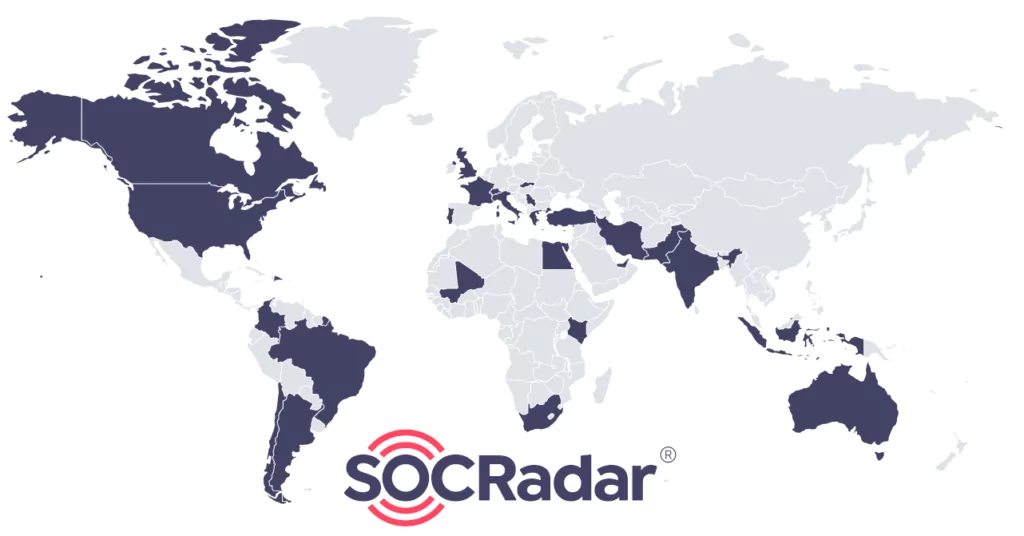
Countries
Considering the countries where the companies attacked by Medusa are located, we infer that the majority of the attacks are in North and South America and Europe.
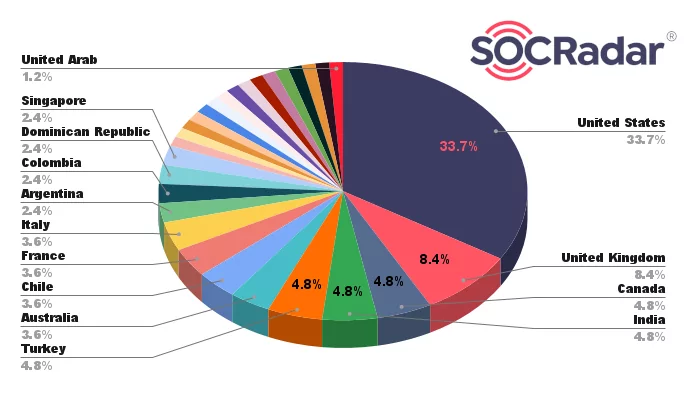
Among the countries where the companies targeted by Medusa are located, the majority is the United States, followed by the United Kingdom, which is targeted more than any other country.
Industries
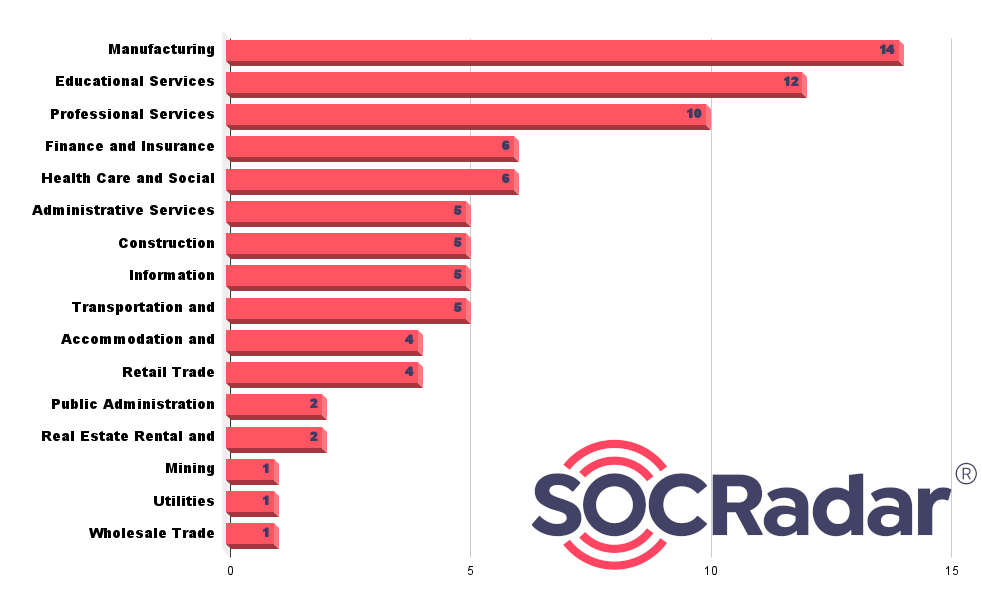
It should also be known that Medusa’s targets are not random; they are carefully chosen for maximum impact. One of its most audacious attacks was against the Minneapolis school district in March 2023. The ransomware group demanded a staggering $1 million, and when the district refused, they retaliated by releasing the stolen data on their TOR site. This incident is a testament to Medusa’s strategy of targeting corporate entities and institutions, ensuring that its attacks create ripples in the global community.
What are the recent activities of Medusa Ransomware?
According to observations, it is possible to say that the Medusa Ransomware group has recently targeted organizations operating in the sector that we can define as Public Administration in Europe.
The International Civil Defense Organization:

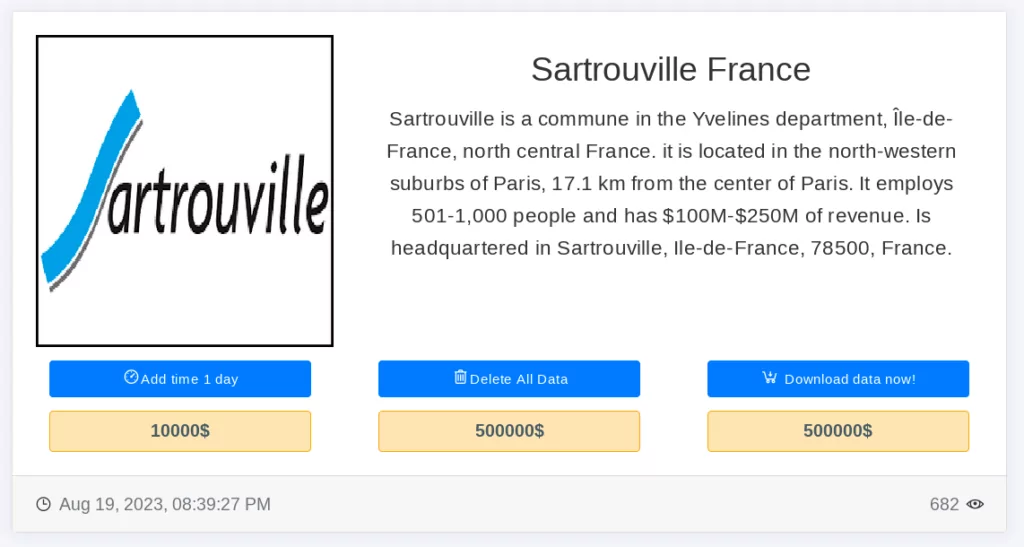
Sartrouville France:
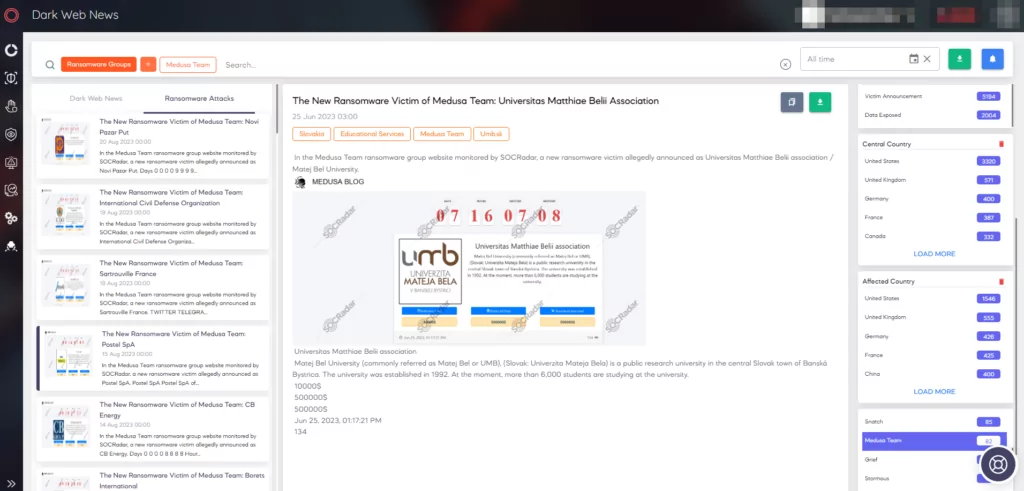
With the Dark Web News page in SOCRadar’s CTI Module, you can access the latest news about the Medusa Ransomware.
CISA, FBI, and MS-ISAC Warn of Medusa Ransomware Threats in New Advisory
On March 12, 2025, the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) issued a joint cybersecurity advisory detailing the threat posed by Medusa ransomware. The advisory provides updated intelligence on the ransomware’s tactics, techniques, and procedures (TTPs) while highlighting mitigation strategies for organizations at risk.
Medusa, active as a ransomware-as-a-service (RaaS) model since at least June 2021, has targeted over 300 victims across multiple critical infrastructure sectors as of February 2025. The group is known for its double-extortion tactics, demanding multimillion-dollar ransoms while threatening to leak stolen data. The advisory emphasizes the use of legitimate remote administration tools in Medusa attacks, making detection more difficult.
CISA and its partners recommend strengthening network defenses by implementing multi-factor authentication (MFA), segmenting networks, and regularly updating software to reduce vulnerabilities.
Organizations are urged to follow the advisory’s recommended best practices to mitigate the risk of Medusa ransomware attacks. For more information and IoCs visit CISA’s advisory.
Conclusion
The rise of Medusa Ransomware underscores the evolving nature of cyber threats. Its sophisticated attack vectors, combined with a collaborative RaaS model, make it a significant concern for organizations. As it continues to target and compromise corporate entities, the need for robust cybersecurity measures has never been more paramount.
Security Recommendations against Medusa Ransomware
- Robust Authentication: Implementing strong, unique passwords and multi-factor authentication can act as the first line of defense.
- Regular Audits: Periodically review user accounts, deactivating unused ones, and ensuring that access controls are stringent.
- Software Vigilance: Keeping all software updated can shield against vulnerabilities that ransomware often exploits.
- Data Backups: Regular backups, especially offline ones, can be a lifesaver, ensuring data availability even after an attack.
- Proactive Cybersecurity: Whether it’s an in-house IT team or an outsourced cybersecurity service, continuous monitoring and vulnerability assessments are crucial.
- Emergency Response Blueprint: A well-documented plan detailing the steps post a ransomware attack can expedite recovery and minimize damage.
- Continuous Education: Keeping employees informed about the latest ransomware threats and safe online practices can prevent inadvertent breaches.