
Critical Vulnerabilities in ConnectWise ScreenConnect, PostgreSQL JDBC, and VMware EAP (CVE-2024-1709, CVE-2024-1597, CVE-2024-22245)
[Update] March 5, 2024: “Kimsuky Takes Advantage of ScreenConnect Vulnerabilities”
[Update] February 28, 2024: “Black Basta and Bl00dy Exploit the Critical ScreenConnect Vulnerability in Ransomware Attacks,” “Phishing Campaign Leverages ScreenConnect Vulnerability, CVE-2024-1709”
[Update] February 23, 2024: “ScreenConnect Instances Targeted to Deploy LockBit Ransomware; CVE-2024-1709 Enters CISA KEV”
ConnectWise has addressed a CVSS 10 vulnerability in its ScreenConnect product, a desktop and mobile support software providing fast and secure remote access solutions.
In addition to the critical vulnerability, ConnectWise also patched a high-severity path traversal vulnerability (CVSS: 8.4) in the same product, which attackers with high privileges can exploit.
ConnectWise has stated that the vulnerabilities were reported on February 13; as of February 21, they have been assigned the CVE identifiers CVE-2024-1708 and CVE-2024-1709.
Details of the Latest ScreenConnect Vulnerabilities (CVE-2024-1708 and CVE-2024-1709)
The critical vulnerability, CVE-2024-1709, stems from an authentication bypass weakness, which attackers can exploit to obtain administrative access, gain access to confidential data, or perform Remote Code Execution (RCE), without requiring user interaction.
Researchers executed a patch diff to figure out the vulnerabilities, and came across a new check in a text file named “SetupWizard[.]aspx”. The new check ensures that the instance is set up before granting the user access to the setup wizard. In vulnerable versions, a specially crafted request could bypass the setup wizard’s verification, allowing unauthorized access independent of the instance’s setup status.
Using this vulnerability, a user could create a new admin account and take control of the ScreenConnect instance.
Users are warned that all servers running ScreenConnect 23.9.7 and prior are vulnerable and require patching.
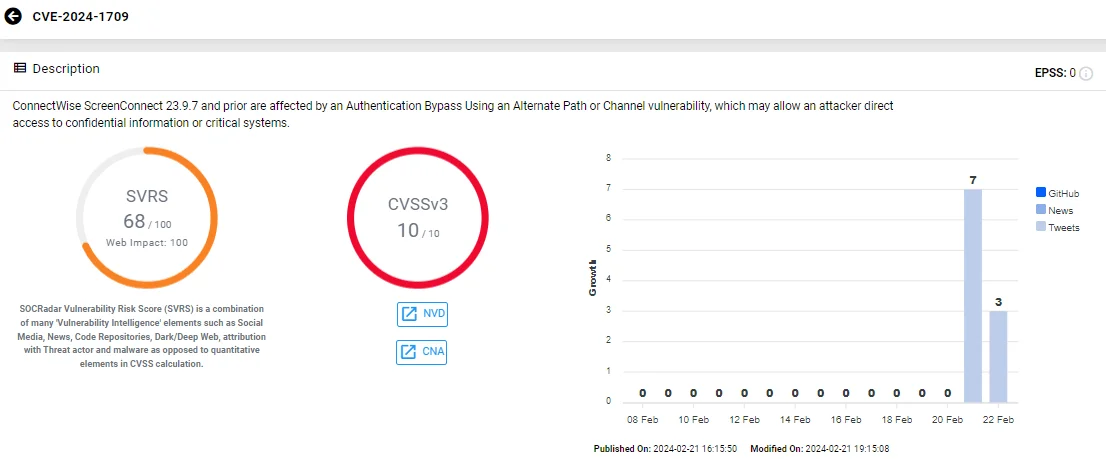
Vulnerability card of CVE-2024-1709 (SOCRadar)
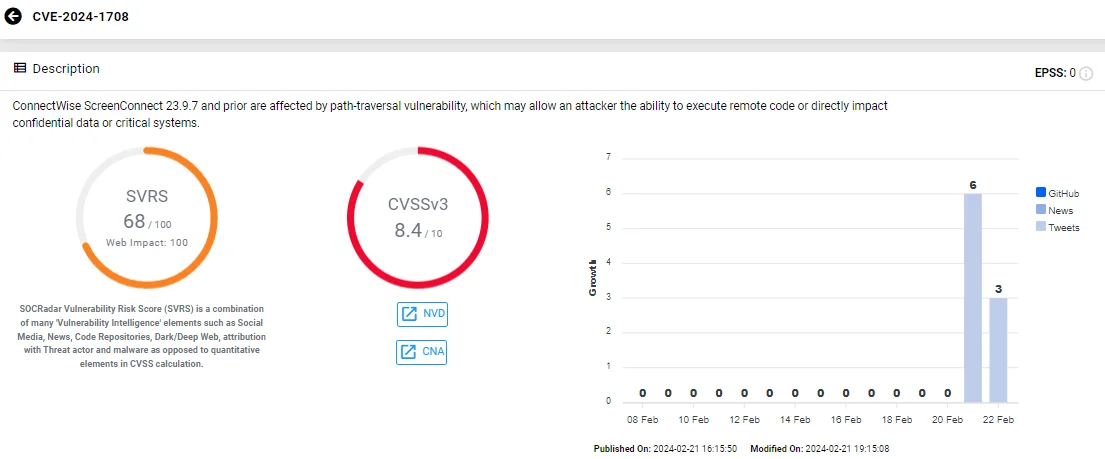
Vulnerability card of CVE-2024-1708 (SOCRadar)
Is There A PoC Available for the ScreenConnect Vulnerability? What Is the Scope?
Researchers have already developed a Proof-of-Concept (PoC) exploit capable of exploiting the vulnerabilities and bypassing authentication on ScreenConnect servers.
Further concerning, a Shodan search reveals over 8,000 results for ScreenConnect servers accessible over the internet.
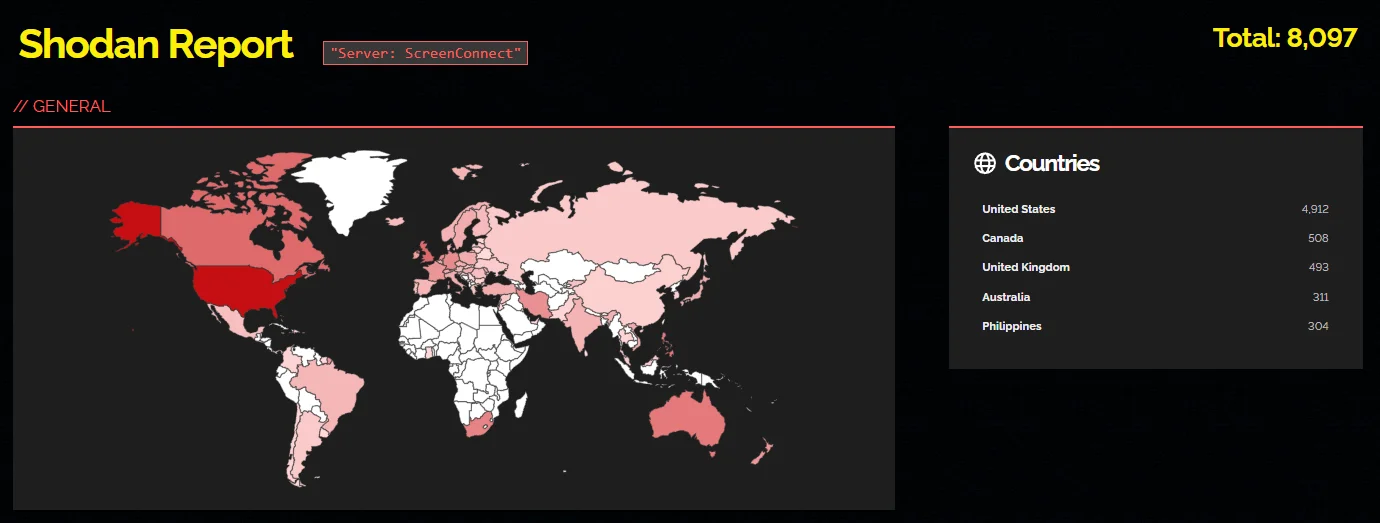
Shodan results for ScreenConnect servers
Given that ScreenConnect is a remote access solution, it is a highly sought-after target. With a PoC now available, exploitation attempts of the vulnerability are expected to occur imminently. In fact, ConnectWise, in its advisory, has most recently reported receiving updates of compromised accounts and shared Indicators of Compromise (IoCs) related to attempted exploitations of the ScreenConnect vulnerabilities.
Here are the IP addresses observed in attacks:
- 155.133.5[.]15
- 155.133.5[.]14
- 118.69.65[.]60
Administrators utilizing on-premise software are strongly advised to promptly update their servers to ScreenConnect version 23.9.8 to avoid exploitation of the vulnerabilities.
Use SOCRadar’s Vulnerability Intelligence to stay on top of hacker trends. Gain detailed information about identified vulnerabilities and easily determine whether any exploits have been detected for specific vulnerabilities.
SOCRadar’s Vulnerability Intelligence
ScreenConnect Instances Targeted to Deploy LockBit Ransomware; CVE-2024-1709 Enters CISA KEV
Vulnerabilities in ConnectWise’s ScreenConnect are being exploited, allowing attackers to deploy the LockBit ransomware, as well as AsyncRAT and other malicious tools.
Despite law enforcement’s efforts in “Operation Cronos” against LockBit, and the seizure of LockBit Ransomware’s leak site, some affiliates appear to continue operations.
Researchers have reported that the critical CVE-2024-1709 vulnerability has been used to breach the networks of several organizations and deploy malware associated with LockBit’s operations, along with other malicious tools.
CISA has added CVE-2024-1709 to its Known Exploited Vulnerabilities (KEV) Catalog, urging organizations to patch it by the deadline of February 29, 2024.
Black Basta and Bl00dy Exploit the Critical ScreenConnect Vulnerability in Ransomware Attacks
After being targeted to deploy LockBit ransomware, ScreenConnect servers now find themselves caught in the crosshairs of other ransomware operations. The Black Basta and Bl00dy ransomware groups have begun exploiting the critical vulnerability CVE-2024-1709 to infiltrate victims’ systems.
Researchers noted privilege escalation, reconnaissance activities, and the use of Cobalt Strike beacons on infected systems associated with Black Basta.
The Bl00dy ransomware gang used payloads developed with leaked Conti and LockBit Black builders. Researchers also identified the use of XWorm, a versatile malware with remote access capabilities that can also move across networks, steal sensitive data, and download other payloads.
Threat actors have also been observed using a second ConnectWise instance and other remote control tools like Atera and Syncro.
Phishing Campaign Leverages ScreenConnect Vulnerability, CVE-2024-1709
Just before additional ransomware groups exploited the ScreenConnect vulnerability, a sophisticated phishing campaign actively leveraging it was uncovered. The campaign presents severe risks, including ransomware attacks.
One of the campaign’s tactics is to employ websites that closely resemble legitimate cryptocurrency services, tempting visitors with promises of rewards while distributing ScreenConnect clients disguised with cryptocurrency-related names. A second strategy involves subdomain takeover via phishing sites masquerading as U.S. healthcare clinics.
Victims who download from these phishing sites will receive files with names such as Windows-Rollercoin[.]exe, which includes self-extracting archives and the ScreenConnect client. When run, a Microsoft Installer file called setup[.]msi is extracted to the %tmp% directory, and the ScreenConnect service is installed.
The service is configured with launch parameters; each ScreenConnect session is started using the Client Launch Parameters. These parameters allow threat actors to determine which targets have been infected and the source of the infection.
The malicious ScreenConnect software provides remote desktop access, file transfer, and administrative functions, granting it extensive control over infected devices.
Kimsuky Takes Advantage of ScreenConnect Vulnerabilities
As stated by BleepingComputer, The North Korean APT hacking group Kimsuky is taking advantage of vulnerabilities in ScreenConnect, specifically CVE-2024-1708, and CVE-2024-1709, to infect targets with a new variant of malware called ToddleShark.
Kimsuky is a state-sponsored hacking group from North Korea notorious for conducting cyber espionage against various organizations and governments globally.
Details on ToddleShark
According to analysts at Kroll, ToddleShark appears to be a fresh iteration of Kimsuky’s previously identified BabyShark and ReconShark backdoors, which have targeted government entities, research institutions, universities, and think tanks across the United States, Europe, and Asia.
The initial breach occurs through vulnerable ScreenConnect endpoints, leveraging vulnerabilities to bypass authentication and execute arbitrary code.
Once inside, Kimsuky utilizes legitimate Microsoft binaries like mshta.exe to run malicious scripts, including a heavily obscured VBScript, disguising its activities among normal system processes.
Subsequently, the malware alters Windows Registry settings to permit macros to run without alerting users on various versions of Microsoft Word and Excel.
Recent Vulnerability in PostgreSQL JDBC Driver Could Allow SQL Injection (CVE-2024-1597)
The PostgreSQL JDBC Driver, widely known as PgJDBC, is affected by a critical vulnerability with a maximum severity score of 10, for which a fix has been recently released.
The PostgreSQL JDBC Driver, written in Java, enables Java programs to establish connections to PostgreSQL databases using standard Java code that is independent of the database system.
CVE-2024-1597, the vulnerability affecting the driver, arises when the driver is used in a non-default configuration, allowing SQL injection attacks and even database takeovers.
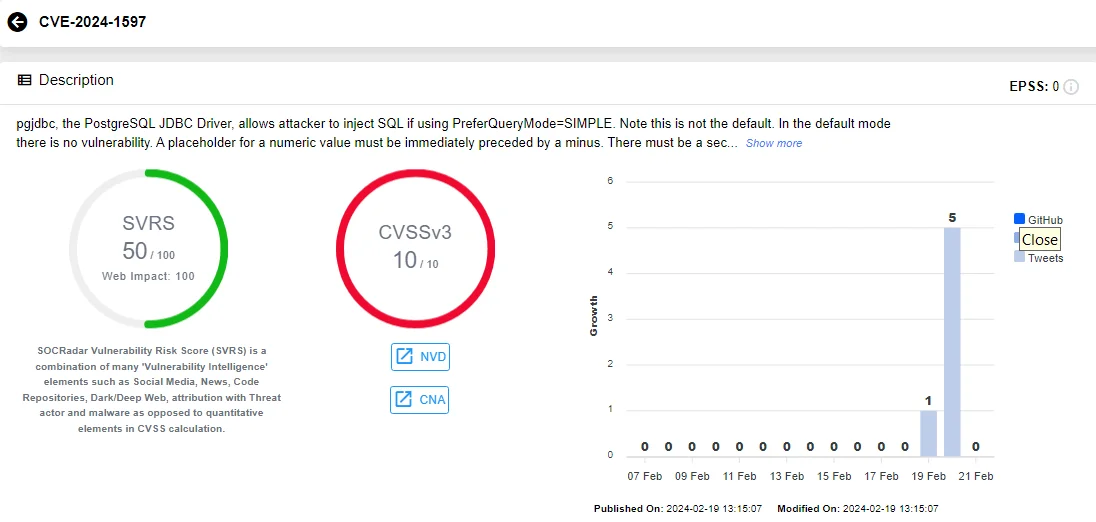
Vulnerability card of CVE-2024-1597 (SOCRadar)
The vulnerability in the PostgreSQL JDBC Driver arises when the driver is used in PreferQueryMode=SIMPLE, a non-default configuration susceptible to SQL injection attacks in versions prior to the ones listed below:
- 42.7.2
- 42.6.1
- 42.5.5
- 42.4.4
- 42.3.9
- 42.2.8
How Could Attackers Exploit the CVE-2024-1597 Vulnerability in the PostgreSQL JDBC Driver?
The exploitation of CVE-2024-1597 in the PostgreSQL JDBC Driver involves manipulating numeric and string placeholders in a query. An attacker can construct a payload that manipulates the parameterized query by inserting a numeric value placeholder, preceded by a minus sign, followed by a string value placeholder on the same line. This bypasses the protection mechanisms against SQL Injection, potentially allowing the attacker to gain control over a database.
This vulnerability poses a severe threat to the security of databases, potentially leading to the exposure and tampering of critical data, including customer and corporate information.
SOCRadar’s comprehensive vulnerability monitoring can proactively detect security issues in your organization’s assets and components.
The Attack Surface Management (ASM) module provides rapid insights into vulnerabilities that affect your assets, allowing you to take quick actions and better prioritize patching operations.
SOCRadar’s Attack Surface Management
VMware EAP Is Vulnerable to CVE-2024-22245 and CVE-2024-22250
VMware advised administrators to remove an authentication plugin that was deprecated in 2021. The reason for this development is that the plugin, named VMware Enhanced Authentication Plugin (EAP), was vulnerable to two unpatched vulnerabilities.
When using the VMware vSphere Client via a web browser, the VMware Enhanced Authentication Plugin (EAP) was used to enable direct login. VMware EAP is not a plugin for vCenter Server, ESXi, or Cloud Foundation, but rather a client plugin.
Details of the VMware EAP Vulnerabilities
Malicious actors can exploit the vulnerabilities, CVE-2024-22245 (CVSS: 9.6) and CVE-2024-22250 (CVSS: 7.8), to relay Kerberos service tickets and gain control of privileged EAP sessions.
VMware explains that attackers could deceive a target domain user with EAP installed in their web browser into requesting and relaying service tickets for arbitrary Active Directory Service Principal Names (SPNs).
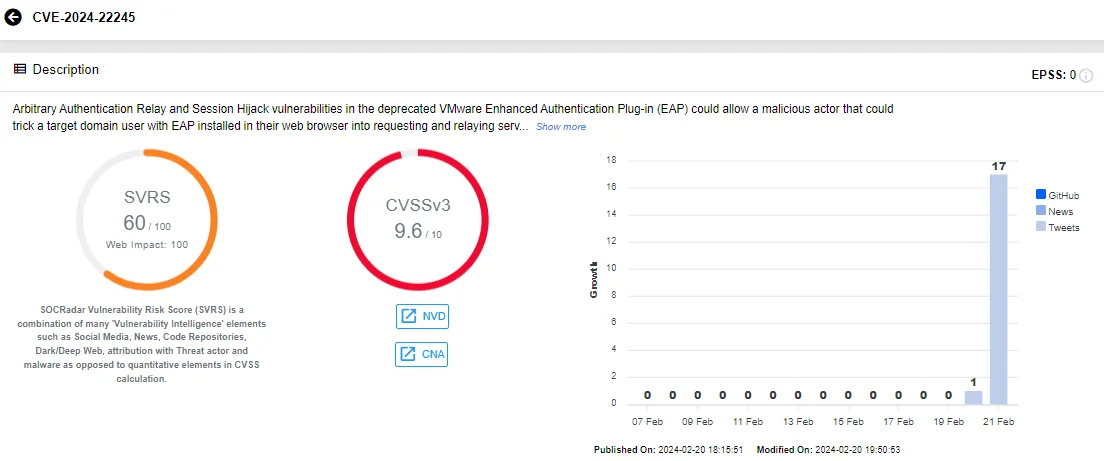
Vulnerability card of CVE-2024-22245 (SOCRadar)
Additionally, due to CVE-2024-22250, a malicious actor with unprivileged local access to a Windows operating system can hijack a privileged EAP session when initiated by a privileged domain user on the same system.
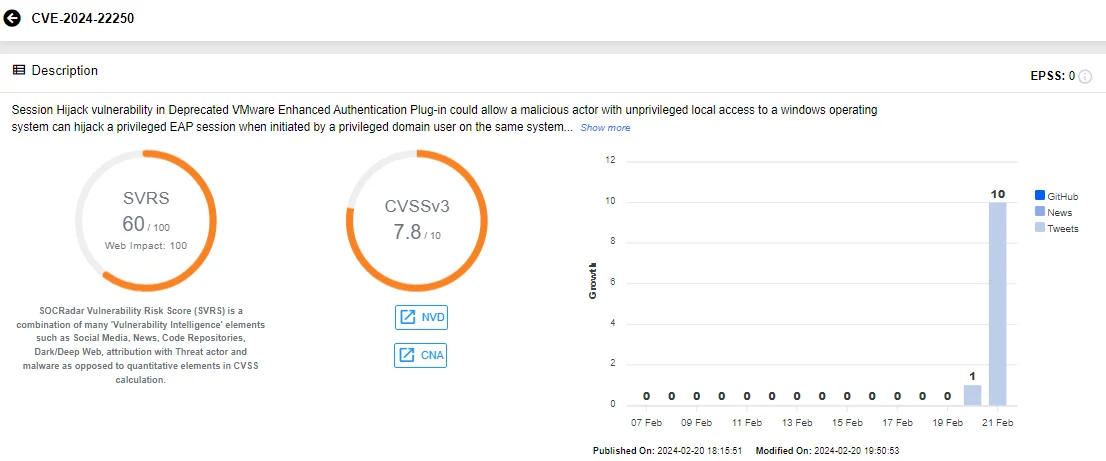
Vulnerability card of CVE-2024-22250 (SOCRadar)
VMware currently has no evidence indicating that the security vulnerabilities have been exploited in the wild.
How to Fix the Vulnerabilities in VMware EAP? Are There Alternatives to the Plugin?
While the deprecated VMware EAP is not installed by default, administrators with the plugin installed must remove both the in-browser plugin (VMware Enhanced Authentication Plugin 6.7.0) and the Windows service (VMware Plugin Service) to address the CVE-2024-22245 and CVE-2024-22250 vulnerabilities.
VMware has published a security article offering guidance on removing the deprecated VMware EAP plugin. Additionally, administrators are encouraged to explore alternative authentication methods, such as Active Directory over LDAPS, Microsoft Active Directory Federation Services (ADFS), Okta, and Microsoft Entra ID.
For more information on these vulnerabilities, visit VMware’s official advisory.




































