
Why Brand Protection Matters: 5 Cases Every Business Should Know
Businesses need to remain cautious in order to protect their assets from the increasing sophistication of hostile actors and the development of cyber threats. These threats are not only coming from hackers. Your brand’s online visibility in the modern digital environment is more important than ever and that is exactly what SOCRadar’s Brand Protection (you can access for free) module is intended to protect. We find and alert our customers to possible risks by monitoring their assets.
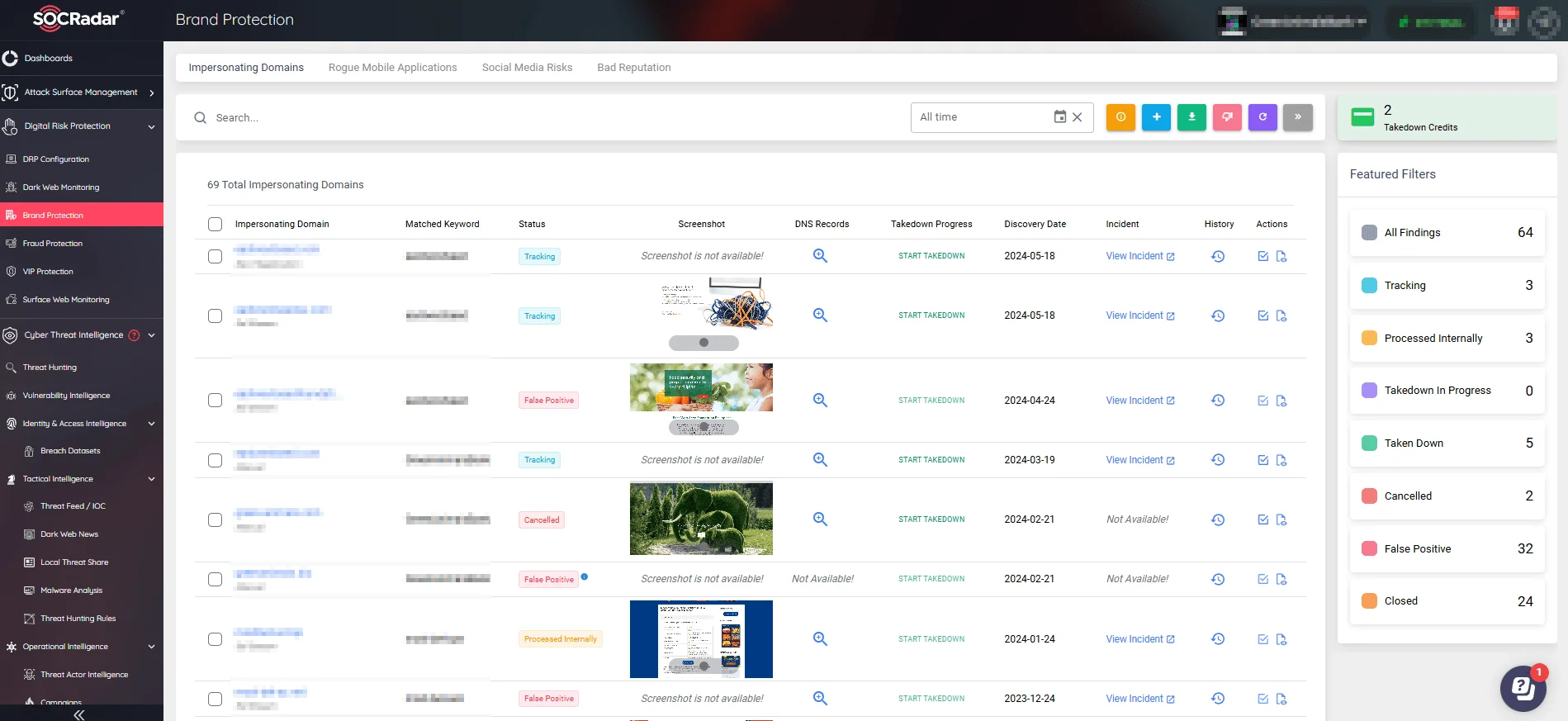
SOCRadar’s Brand Protection Module
There are several areas in which your brand can get damaged. Threat actors can register fake domains impersonating your company, publish applications filled with malware using your brand, hurt your image on social media with fake accounts, and steal credentials from various sources which allows them to access your systems with ease. In addition to these attempts by threat actors, you might be unaware of the fact that your brand is blacklisted by various sources which will create negative outcomes for your brand value.
These dangers can manifest in a number of ways, and in this article, we will go over each of these risks in-depth and highlight the significance of thorough brand protection with instances from real-world situations.
Impersonating Domains
The deployment of fake domains is one of the most widely used tactics by threat actors to deceive users. These fake domains resemble actual ones quite a bit, often with slight but easily overlooked differences. The goal is to trick customers into believing they are using a reputable business, which may lead to phishing scams, financial losses, and data breaches.
Consider a big financial company that discovers many domains that mimic its primary website. These domains use little changes, such as adding a hyphen or replacing a “l” with a “1”. Upon visiting these websites, individuals might be requested to provide their login credentials, which are then acquired by threat actors.

Bebeto Matthews | AP
We have a case from 2013 with this particular risk. Via an email-based phishing scheme, threat actors deceived a worker at Fazio Mechanical, an HVAC contractor and one of Target’s third-party vendors, into disclosing their credentials. The threat actors then used the credentials they had acquired to enter Target’s network and infect several machines with malware. The fraudsters were able to successfully execute their strategy since Fazio Mechanical lacked malware detection software and Target failed to properly segregate their networks. Target, on the other hand, has several protection measures in place to avoid these kinds of incidents, but since attackers reached out to Target via a trusted party, they were able to pass those measures.
Threat actors ultimately gained access to about 40 million customers’ credit and debit card details as well as 70 million customers’ personal data, including names, addresses, and phone numbers.
In this case, the employee of that third party was tricked by the threat actors. Are you sure about the security posture of your supply chain? When you are operating your business, you receive a lot of emails from your business partners. But what if they are compromised? Even if you get an email from a legitimate source, can you be sure that the content of the email is clean? SOCRadar’s Supply Chain Intelligence module helps you see your business partners’ security risks and helps you take the necessary steps before threat actors reach out to you via entities you trust.
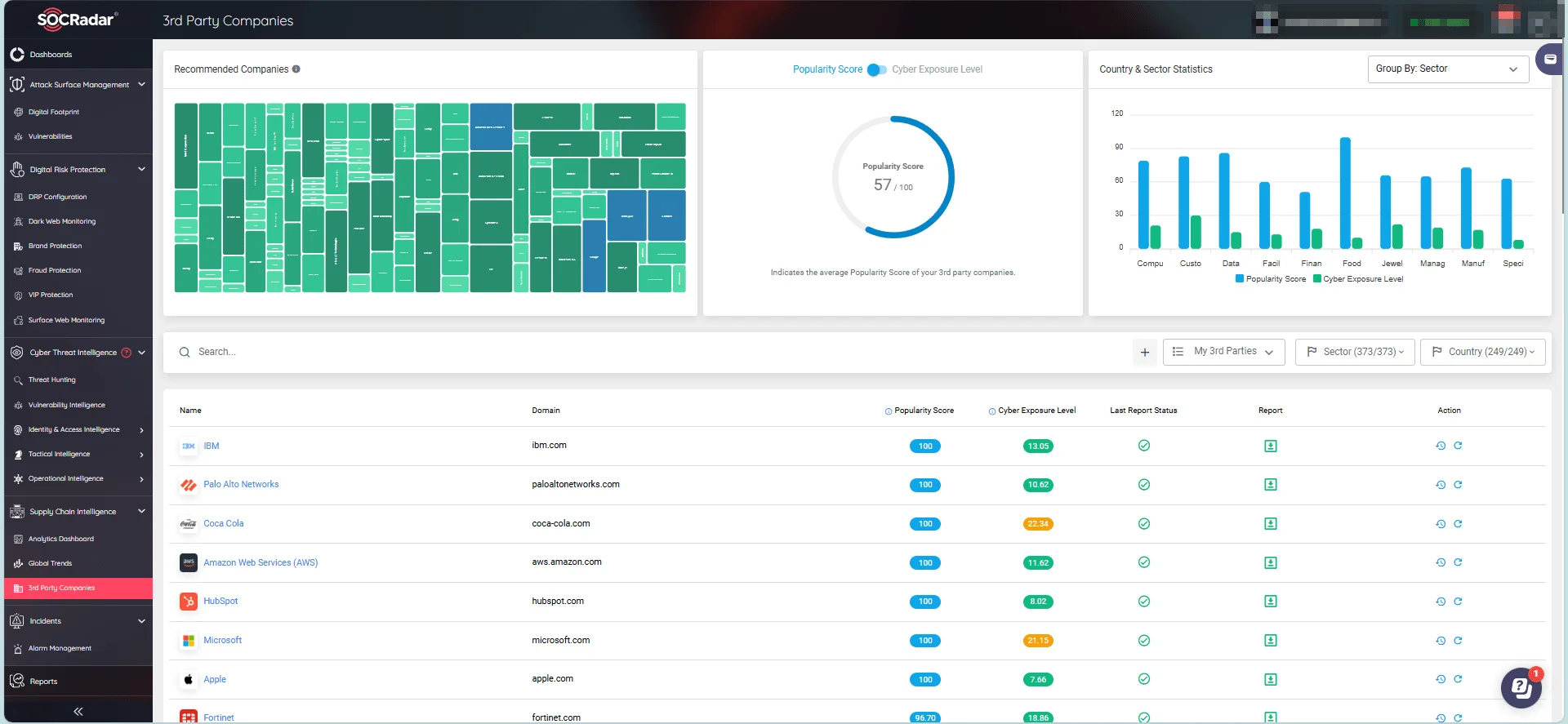
SOCRadar’s Supply Chain Intelligence 3rd Party Companies
Rogue Mobile Applications
Rogue mobile applications pose a significant threat to brand reputation and user security. These dangerous apps frequently pose as trustworthy ones in order to trick users into downloading them. Once installed, they have the ability to commit fraud, infect malware, and steal confidential data.
In this case, threat actors tricked many individuals and generated revenue from the ads they presented in their fake application.

Generated by Imagen
In 2017, Reddit users discovered a malicious app disguised as the official WhatsApp application. Although the app appeared identical to the legitimate WhatsApp client when opened, it was filled with advertisements. This counterfeit application gave the impression that it was created by WhatsApp Inc.. However, subtle changes in the app’s code allowed this fake version to seem legitimate.
According to a Reddit user, the fake app required only basic internet access but was filled with ads. It also attempted to download an additional .apk file, which tried to hide itself after downloading.
Did you know that the SOCRadar Integrated Takedown module can help you detect fake applications imitating as if they are released by your company? By our extensive scanning capabilities, you will be notified as soon as a threat actor tries to impersonate your brand and we will take that fake application down for you.
Impersonating Accounts on Social Media Platforms
Social media is now a crucial channel for communicating with customers. But it also exposes brands to a range of hazards, including fake reviews, bad mentions, or leaked credentials. Keeping an eye on social media channels or clear-net for these possible hazards can help companies detect related risks swiftly. Brands can preserve their image and protect their systems while building a strong relationship with their audience by quickly recognizing and resolving these problems.
It might be hard to keep an eye on every reference and comment made about your brand or company online. It’s a tiring task to keep track of these exchanges and check innumerable websites for such risks. Effective tools are necessary to maintain a healthy online presence and safeguard your brand against hostile activity and false claims.
We will check a case from X, previously known as Twitter. The renewed membership service, one of Elon Musk’s major changes since taking over Twitter, has produced serious issues for a number of businesses, including Musk’s SpaceX.
In the past, Twitter was the authority for awarding blue checks to celebrities to prevent impersonation. But now, you can get one as long as you have the necessary funds, which is only $8. This change allowed imposters to easily take advantage of the website.
Numerous companies were impersonated, but one of the significant cases of this development was about Eli Lilly & Co. A phony account tweeted that insulin was free, forcing the large pharmaceutical corporation Eli Lilly & Co. to apologize. The tweet also damaged their shares in the stock market.
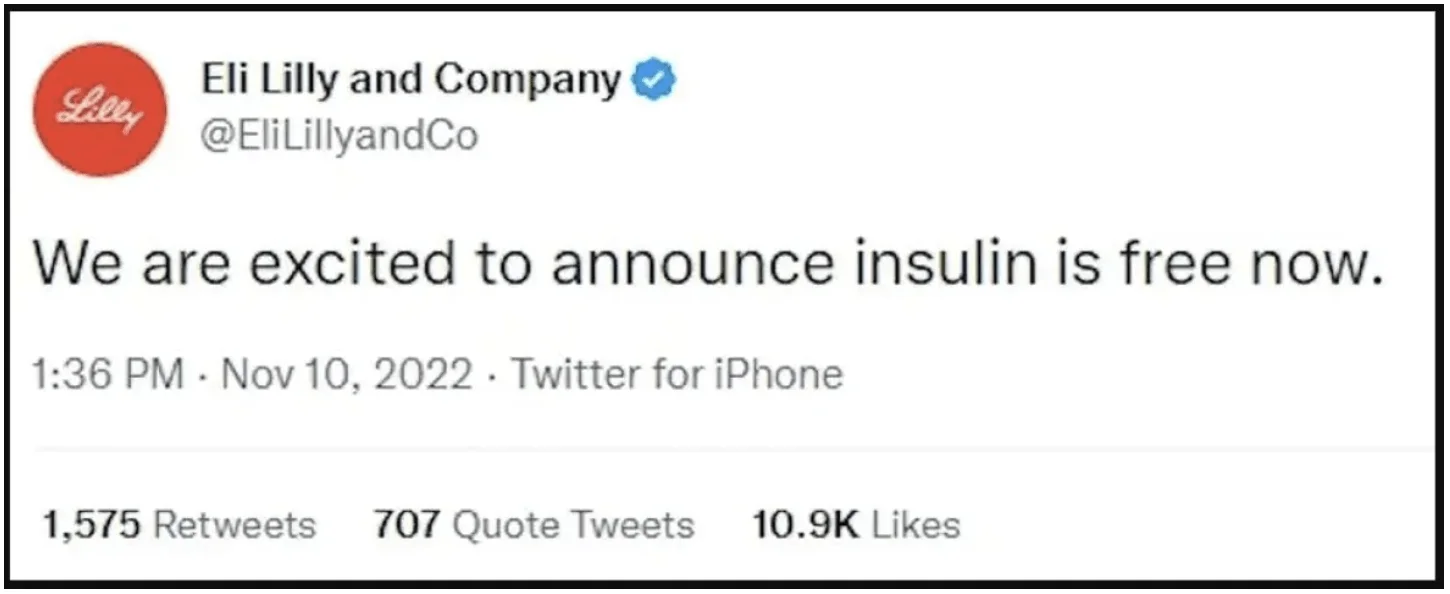
A misleading tweet from the fake Eli Lilly & Co account, source: Lown Institute
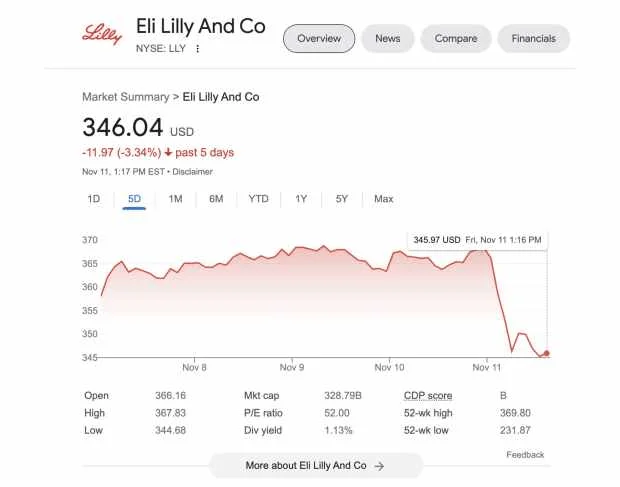
Shares of the pharmaceutical company Eli Lilly & Co, source: Tech Startups
Bad Reputation
Having a negative reputation can have a big effect on a brand’s credibility and customer trust in the digital sphere. When it comes to brand protection, “bad reputation” refers to circumstances in which a brand’s email addresses, domain names, or IP addresses are blocked or reported as spam. Malicious actions, including phishing attempts that come from accounts that have been compromised or inadequate security protocols, may be the cause of this. Maintaining a spotless reputation for your brand’s digital assets is crucial for company operations and continuous communication with your customers.

vx-underground X banner
In June 2024, vx-underground’s website, a group focused on malware and cybersecurity, was flagged by Cloudflare. This organization is a group dedicated to sharing malware samples with the infosec community, allowing researchers to analyze them and gain insights into threat actors and various malwares in general.
However, some individuals occasionally misunderstand the group’s purpose and mistakenly accuse them of having malicious intentions. One day, Cloudflare, a service known for enhancing web application security and performance, flagged the vx-underground’s website as a phishing site. As a result, users attempting to access the site encountered difficulties. However, the problem was solved swiftly.
SOCRadar Labs offers many free tools that you can use to gain insights into the vast threat landscape. The IP Reputation Service specifically allows you to make a search to find out if your IP or IP block is among any blacklist.
Compromised Credentials Risk
Compromised credentials are causing a huge danger for organizations and individuals since you are literally handing over the keys of your account or company to random people on the internet. These compromises can have far-reaching effects on an organization’s security. Especially developers’ repositories on GitHub are good sources of information for threat actors looking for credentials or API keys that will lead them to various organizations and that’s exactly the topic of our case.

Generated by Imagen
Uber experienced a data breach in 2014 and 2016, and the attackers in both cases exploited keys that were located in GitHub repositories. An access key was discovered by the attacker in a public repository in 2014. And an AWS key in an engineer’s private repository was accessed by hackers in 2016 using credentials they had acquired from GitHub.
In the 2014 case, an attacker had access to user data stored in an Amazon S3 bucket in plain text. By using GitHub, the attacker was able to locate an engineer who had shared an access key to a public GitHub repository. The attacker was able to gain access to the company’s Amazon S3 buckets by using this access key.
In 2016, Uber suffered a breach in a similar way. The attackers used a script designed to ingest emails and passwords and attempt to log into GitHub. The script identified valid logins and the associated organizations. Upon discovering Uber in the results, the attackers used these credentials to access Uber’s repositories. They then searched for access keys to Uber’s company servers and found an AWS key, which provided them access to an S3 bucket containing sensitive data of 57 million users.
SOCRadar XTI constantly scans various dark web and clear net sources to detect if its customers’ credentials are leaked. Additionally, SOCRadar provides its customers with an advanced Identity and Access Intelligence tool. This allows you to see if any of your employees’ personal or business-related information is out there. Stealer malware can steal credentials and then threat actors will sell them on dark web forums. It’s important to make sure that your company is not on those lists.
Conclusion
In this blog post, we saw the 5 most troublesome risks that can impact your brand online. Security is not only about protecting your systems but also your image.
A threat actor who wants to damage your business can also do that by other means than infiltrating your systems. They can create fake email addresses, obtain domain names, create fake accounts, or publish malware-filled applications to trick your customers and steal their information. We also analyzed a case where a phishing attack can cause huge disruptions even to the biggest players in the market.
Not taking care of these instances can lead to poor customer satisfaction and damage your business badly. SOCRadar XTI provides intelligence in various domains to protect its customers because we know that extended security measures are necessary to protect your organization and protecting only one front is not enough.





































