
5 Supply Chain Intelligence Use Cases with SOCRadar Module
Numerous high-profile incidents have evidenced that cyber threats to the supply chain can have catastrophic consequences. To mitigate these risks, organizations require advanced tools and strategies that provide comprehensive visibility, proactive monitoring, and rapid response capabilities.
SOCRadar’s Supply Chain Intelligence Module provides a set of solutions designed to effectively address these challenges. Here, we look at five critical use cases for this module and demonstrate how it can help organizations defend against supply chain attacks.
Comprehensive Third-Party Risk Management
Third-party risk management has emerged as a crucial component of an organization’s cybersecurity strategy. The complexity and scale of modern supply chains mean that vulnerabilities can arise from any link in the chain, exposing businesses to significant threats.
The Top.gg Discord bot attack is a stark reminder of the dangers lurking within third-party dependencies, where malicious actors infiltrate repositories and spread malware through widely-used packages.
A LinkedIn post about the Top.gg incident (Source)
A supply chain attack compromised the Top.gg bot community on Discord, affecting over 170,000 users. The attackers inserted malicious code into a GitHub repository, taking advantage of the Top.gg platform. They used typosquatting and code obfuscation techniques to make the malware more difficult to detect. The malicious code was hidden within a rogue version of the Colorama package, which was then used to infect developers’ systems.
The attackers attempted to steal sensitive information by deploying a trojan program via the compromised Colorama package. The malware extracted login information and authentication tokens from browsers and applications installed on compromised systems.
The attackers used a variety of distribution methods, including publishing rogue packages on PyPI and creating fake GitHub repositories. This multi-stage attack involved downloading and running Python scripts from attacker-controlled servers to steal a variety of data, including browser information, cryptocurrency wallets, and Discord tokens.
Manage third-party risks with confidence using SOCRadar, and gain complete visibility across your entire ecosystem. The 3rd Party Companies feature empowers you to closely monitor high-priority companies with your watchlist and gain insights into all third-party companies within our extensive database. You can leverage advanced insights through risk scores for each company, and download past assessments while initiating new ones to ensure a robust defense against supply chain attacks.
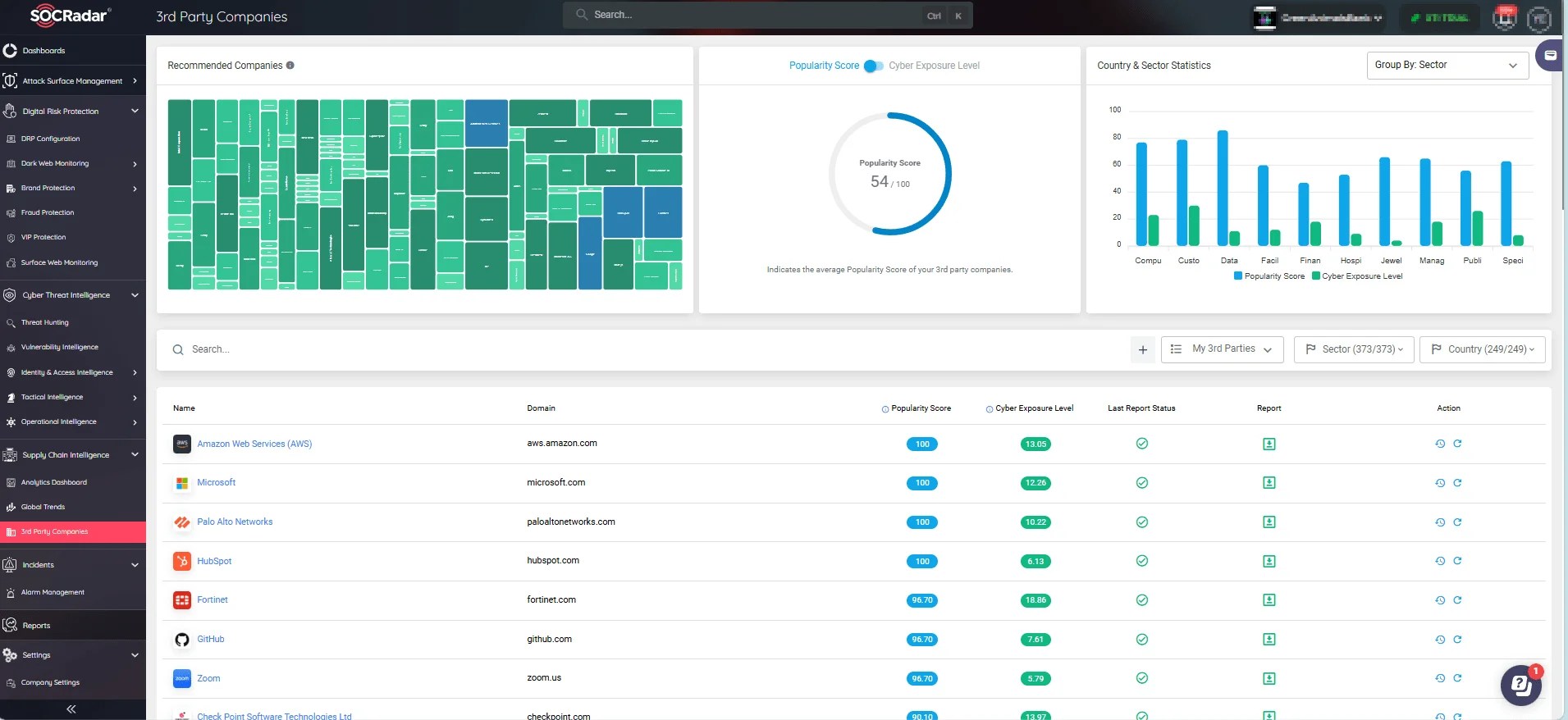
SOCRadar’s 3rd Party Companies module
Proactive Monitoring and Response
As the digital ecosystem evolves, proactive monitoring and rapid response become critical. The breach at Sisense, a leading business analytics software provider, highlights the vulnerabilities in software supply chains. With over 2,000 global companies relying on Sisense, the attack demonstrated the importance of ongoing monitoring and quick action to protect sensitive data.
Sisense, a business analytics software company, recently experienced a breach, prompting the Cybersecurity and Infrastructure Security Agency to advise customers to reset their credentials and monitor for suspicious activity.
The attack’s impact and compromised information highlight the vulnerabilities in software supply chains. This breach shows how attackers use access to popular platforms to infiltrate multiple networks.
Sisense’s breach serves as a reminder of the growing threat to software-as-a-service platforms. With high-profile clients including Verizon, Air Canada, and Nasdaq, the potential consequences of compromised data are significant. Vigilant monitoring, strong security practices, and proactive response measures are critical in mitigating such risks.
SOCRadar’s Supply Chain Intelligence Analytics Board provides real-time visibility into the ever-changing global cyber threat landscape. With features like Attack Timeline visualization, you can stay instantly aware of worldwide attacks, be informed about emerging threats, and implement proactive security measures within your supply chain, ensuring the integrity and protection of your valuable digital assets.
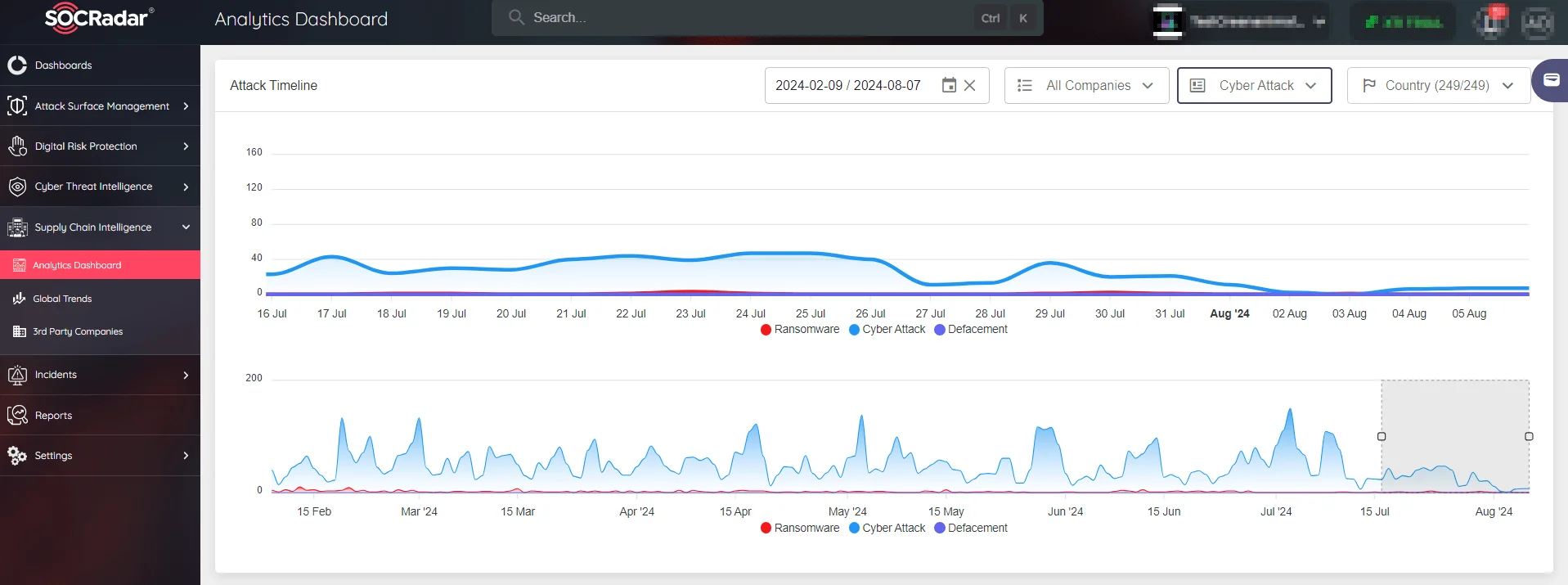
SOCRadar’s Analytics Dashboard real-time analytics of cyber attacks timeline
Enhancing Internal Security Protocols and Employee Awareness
Effective cybersecurity extends beyond technology and requires a comprehensive approach that includes strong internal protocols and ongoing employee training. Organizations can significantly reduce the risk of human error-related breaches while also ensuring a strong defense against potential cyber threats by improving internal security protocols and cultivating a cybersecurity awareness culture.
In 2023, Okta’s customer support system was compromised after an employee used their personal Google account on a company laptop, allowing hackers to steal session tokens and access customer files. This breach exposed vulnerabilities in Okta’s security, emphasizing the need for robust internal protocols and rapid response mechanisms. The stolen HAR files contained sensitive data, highlighting the importance of employee training on secure internet practices and the use of Multi-Factor Authentication (MFA).

The Okta incident served as a stark warning, highlighting the significant risks inherent in supply chains.
The incident underscores the critical need for continuous monitoring and swift action in detecting cybersecurity threats. Okta’s delayed response increased potential risks, emphasizing the importance of enhancing security practices such as rapid response and post-incident analysis. The breach demonstrated that effective cybersecurity involves not only technological tools but also employee awareness and organizational policies.
By leveraging SOCRadar’s insights into Global Trends, companies can ensure their employees are well-informed about the latest threats and best practices. Continuous learning from global trends empowers employees to recognize and respond to potential security risks, enhancing the overall security posture and resilience of the organization.
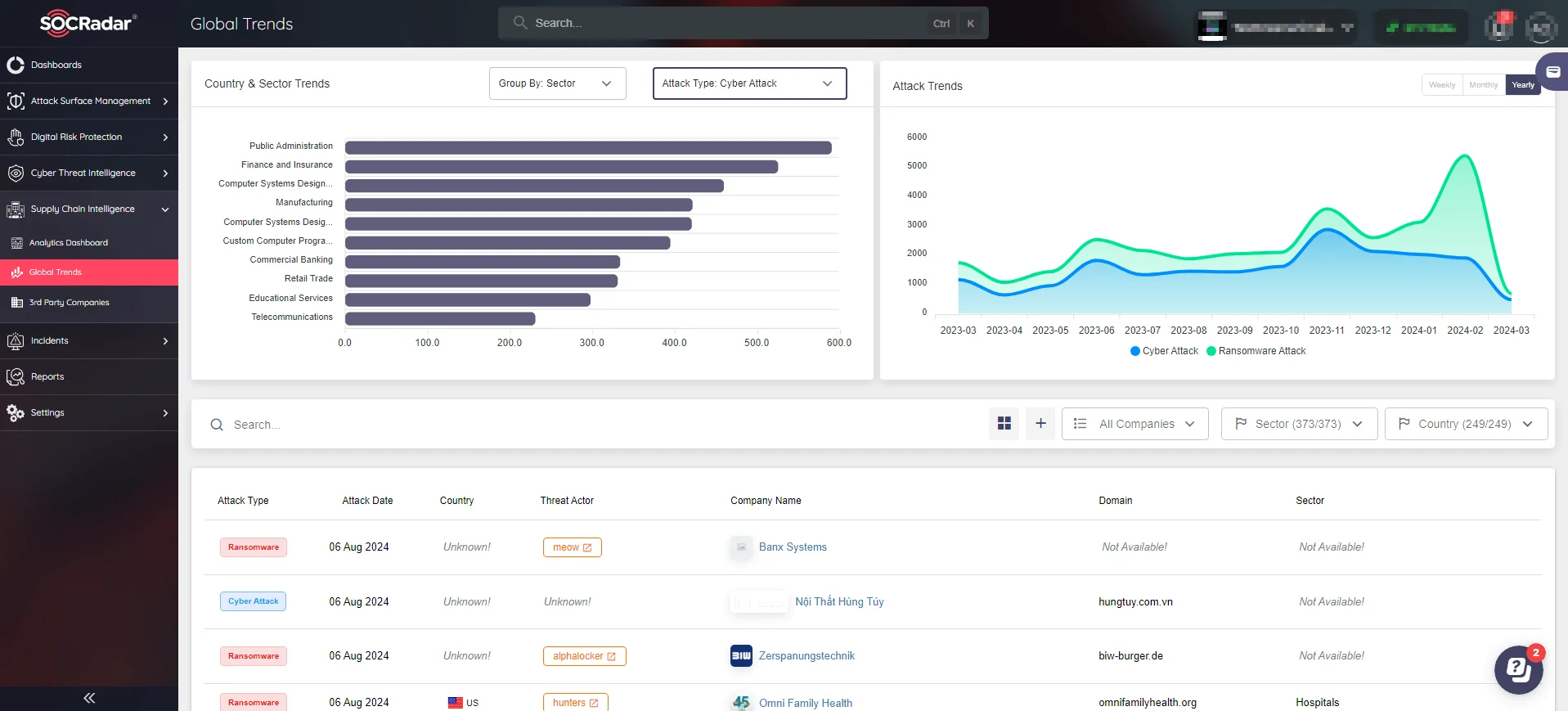
SOCRadar’s Supply Chain Intelligence Global trends
Mitigating Ransomware Threats
Ransomware attacks continue to pose a significant threat to organizations worldwide, exploiting vulnerabilities to gain unauthorized access and install malicious software. To protect critical systems and data from ransomware threats, effective vulnerability management and timely patch deployment are required.
In March 2024, two critical vulnerabilities, CVE-2024-27198 and CVE-2024-27199, were found in JetBrains TeamCity On-Premises, a popular CI/CD tool. These vulnerabilities could allow attackers to gain full control over TeamCity projects, posing a significant risk of supply chain attacks. Specifically, CVE-2024-27198 allows remote attackers to control the TeamCity server with administrative permissions, while CVE-2024-27199 involves path traversal that could lead to system modification and unauthorized HTTPS certificate replacement.
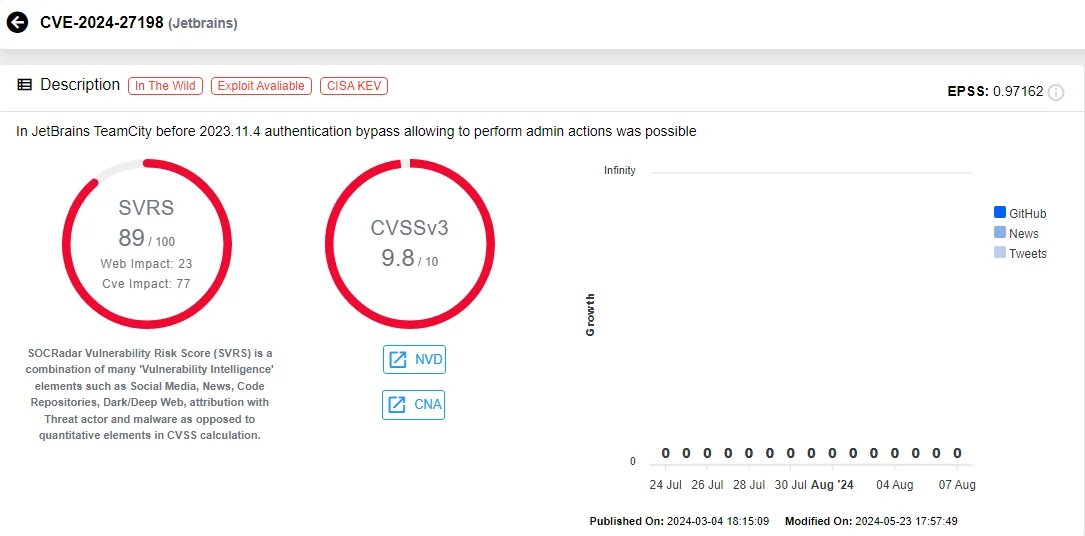
Vulnerability card of CVE-2024-27198 (SOCRadar)
The BianLian ransomware group exploited these vulnerabilities, particularly CVE-2024-27198, to deploy a PowerShell backdoor and conduct extortion. This incident underscores the necessity for administrators to promptly apply security updates to mitigate risks. Upgrading to TeamCity On-Premises version 2023.11.4 or applying available security patches can protect against these vulnerabilities.
Optimize your Supply Chain Intelligence with SOCRadar’s Analytics Board. Gain real-time visibility into cyber threats with the Attack Timeline visualization, which provides instant awareness of worldwide attacks and emerging ransomware threats. By focusing on critical information and proactive measures, you can safeguard your entire supply chain ecosystem against ransomware attacks.
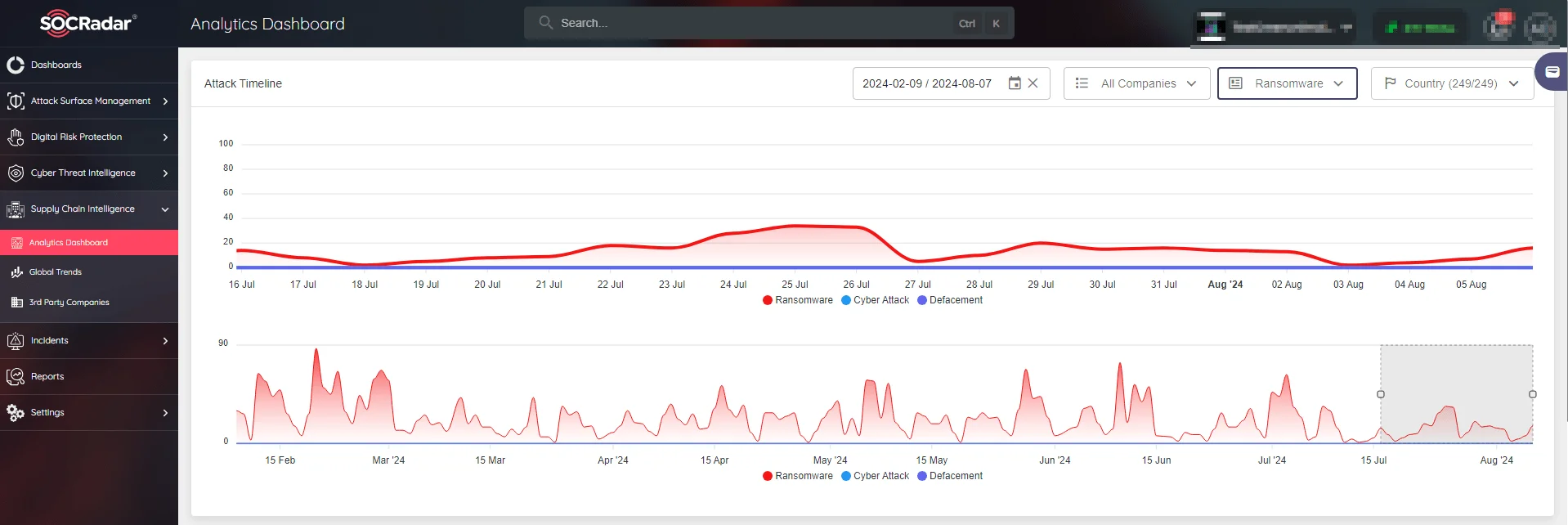
SOCRadar’s Analytics Dashboard real-time analytics of ransomware attacks timeline
Continuous Security Validation and Penetration Testing
In an age when cyber threats are constantly changing, maintaining a strong security posture necessitates more than just initial defenses; it also necessitates ongoing scrutiny and testing. Regular penetration testing and vulnerability assessments are required to detect and address security flaws before they are exploited.
In 2018, ASUS experienced a sophisticated supply chain attack targeting their Live Update Utility. Attackers injected a backdoor into the utility using stolen digital certificates, allowing the distribution of trojanized updates from official ASUS servers. This affected up to a million systems globally. The attack primarily impacted ASUS’s vast user base but targeted specific users.
SOCRadar’s supply chain intelligence simplifies tracking the global cyber threat landscape, including specific attack types like defacement attacks. With our Attack Timeline visualization, you can gain instant awareness of worldwide defacement attacks, stay informed about emerging threats, and enable proactive security measures within your supply chain. This proactive approach not only protects against sophisticated supply chain attacks but also enhances overall cybersecurity resilience.
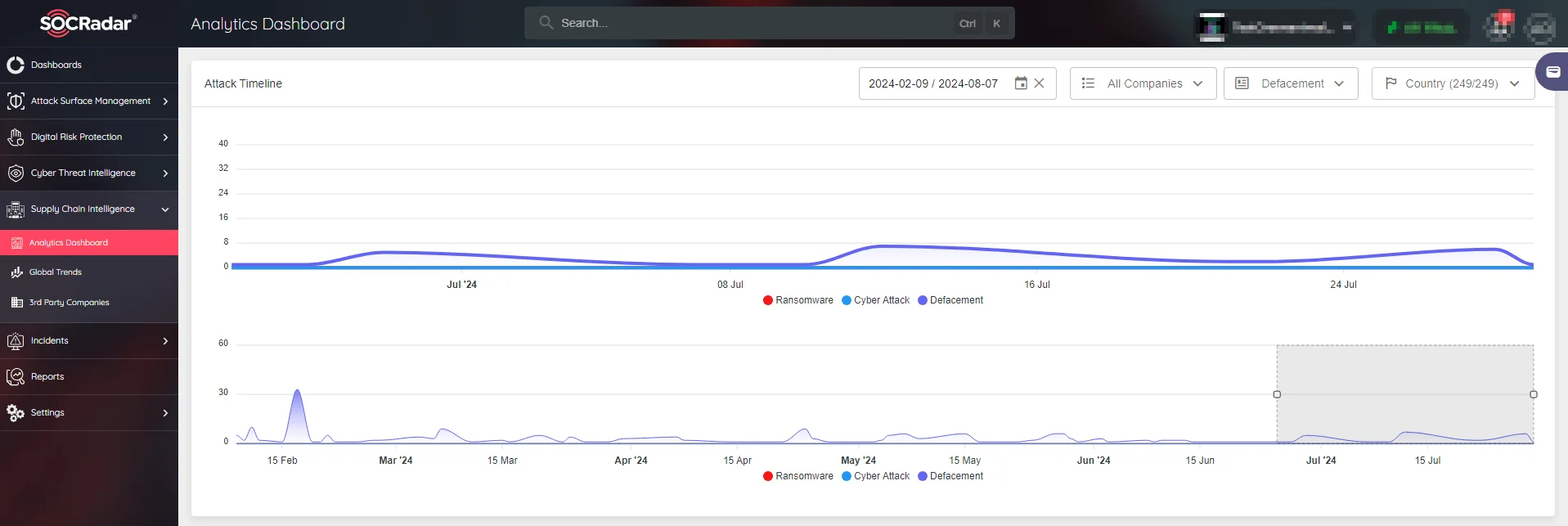
SOCRadar’s Analytics Dashboard real-time analytics of defacement attacks timeline
Conclusion
Supply chain security is an ongoing challenge that necessitates a multifaceted strategy. Organizations can use SOCRadar’s Supply Chain Intelligence Module to gain the insights and tools they need to effectively protect their ecosystems. These use cases, which range from managing third-party risks to mitigating ransomware and continuously validating security, emphasize the importance of proactive and comprehensive strategies.
As cyber threats evolve, the ability to stay ahead of potential attacks and ensure supply chain integrity will become increasingly important for business continuity and sensitive information protection. SOCRadar enables organizations to navigate the complex landscape of supply chain security with confidence and resilience.




































