
A New Rising Social Engineering Trend: Callback Phishing
Callback phishing emerged as a hybrid social engineering technique that combines phishing and vishing. The phishing technique used to steal sensitive data or transmit harmful packages via email and vishing, which applies phishing over the phone, was frequently used by threat actors. However, when recent incidents are examined, Callback Phishing stands out as the popular initial access method.
Malicious attachments cannot always evade security solutions. The sent email does not contain a malicious file or URL in Callback Phishing. Instead of these, a phone number left for the victim to call dramatically reduces the possibility of being considered spam. Victims follow instructions over the phone and get infected with their actions in this process.
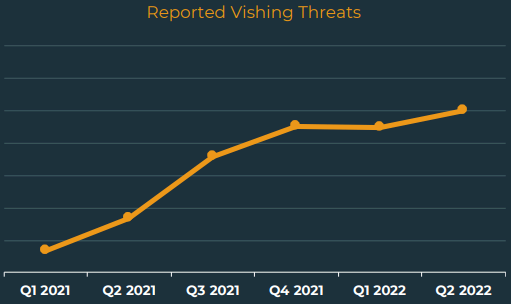
According to Agari’s report, the volume of phishing attacks increased by %6, but a more than 600% increase was observed in Callback Phishing attacks just in the second quarter of 2022. Moreover, according to another report, vishing attacks thus far increased by 550% from 2021 to the beginning of 2022. When we take this data into account as well, we can notice a considerable increase.
How do They Operate?
Callback Phishing usually starts with an email; threat actors can follow various tactics to attract the victim’s attention. These can be specific issues that have been studied specifically for the victim, or they can be issues that will attract the attention of all kinds of people, like a discount or a heavy debt bill.
They may also impersonate trusted companies, partners, and other organizations to increase their credibility. Moreover, a point that can increase the level of danger is security companies are often impersonated in these attacks, resulting in an additional tendency to trust. They may also claim that your institution has approved this action and is within the knowledge of the IT department.
Some threat actors are social engineering experts, and their well-crafted phishing emails may not arouse suspicion. They may create a sense of urgency and push the victim to take quick action. When the given number is called, it may lead the victim to download malware or redirect to a dangerous site. If the attack succeeds, threat actors can spread throughout the system. Furthermore, they can deploy ransomware or extort data for profit.
Which Threat Actors are Using it?
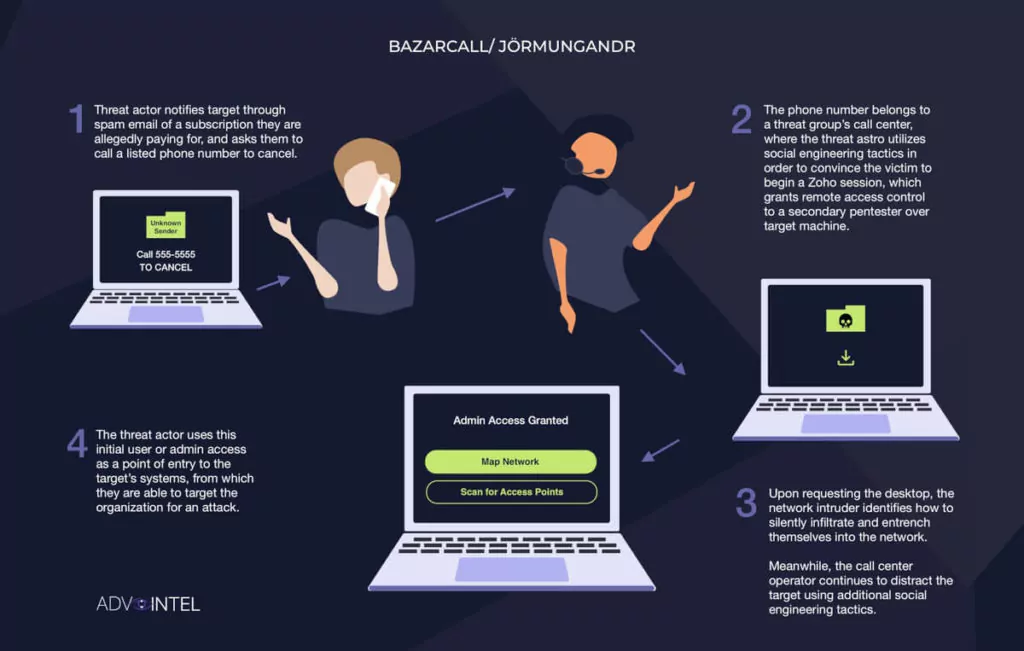
In the last years, an APT group, Trickbot (which was taken over by the Conti), ran a campaign called BazarCall to install the backdoor malware BazarLoader. They were connecting their victims to a call center whose number was forwarded via email and then redirecting them to a malicious website to download malware. This campaign, which has attracted attention since March 2021, pioneered the social engineering attack we call Callback Phishing and is now used by many threat actors.
Although the Conti ransomware group officially terminated operations on May 19, 2022, its members have continued their activities under different names and brands. Three successor groups, Silent Ransom, Quantum, and Zeon, have inherited similar initial access methods from Conti.
SOCRadar ascertained that the Quantum ransomware group created its versions of BazarCall, which they named Jormungandr. In addition, it is known that they recruit social engineering experts for their teams. In recent incidents, threat actors targeted over a hundred organizations, gained access to over 20 high-profile points just in the first half of 2022, and demanded millions as ransom.
Callback Phishing Campaigns
In July 2022, a threat intelligence company alerted its customers about Callback Phishing. According to this notification, presumably, the Quantum group tried to carry out a Callback Phishing campaign on victims by impersonating the cybersecurity organization.

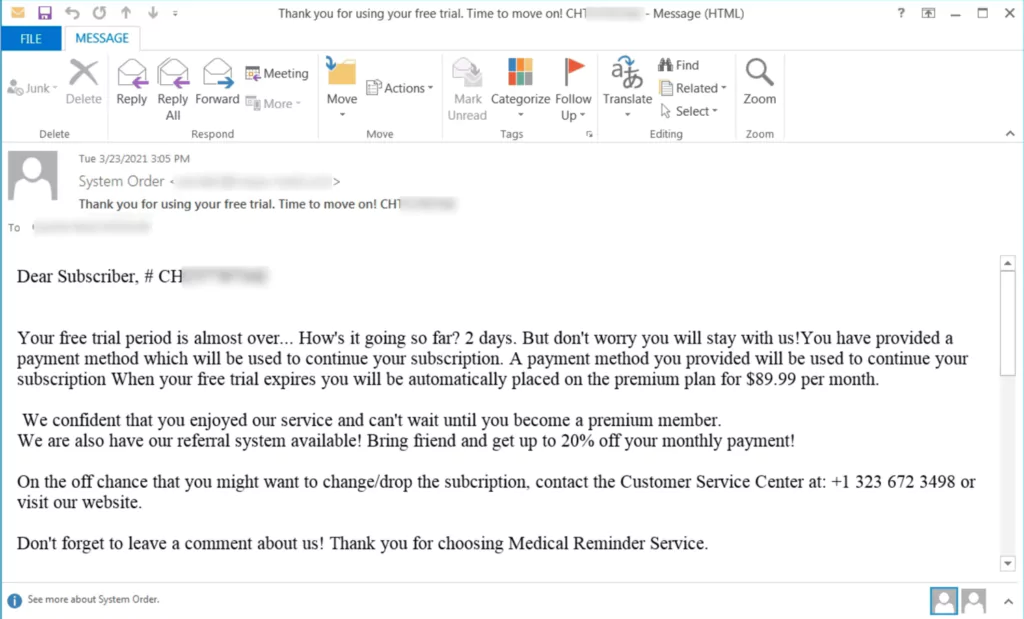
On the other hand, Silent Ransom Group or Luna Moth carried out Callback Phishing campaigns by sending fake subscription emails by impersonating companies such as Zoho, Duolingo, and Masterclass.
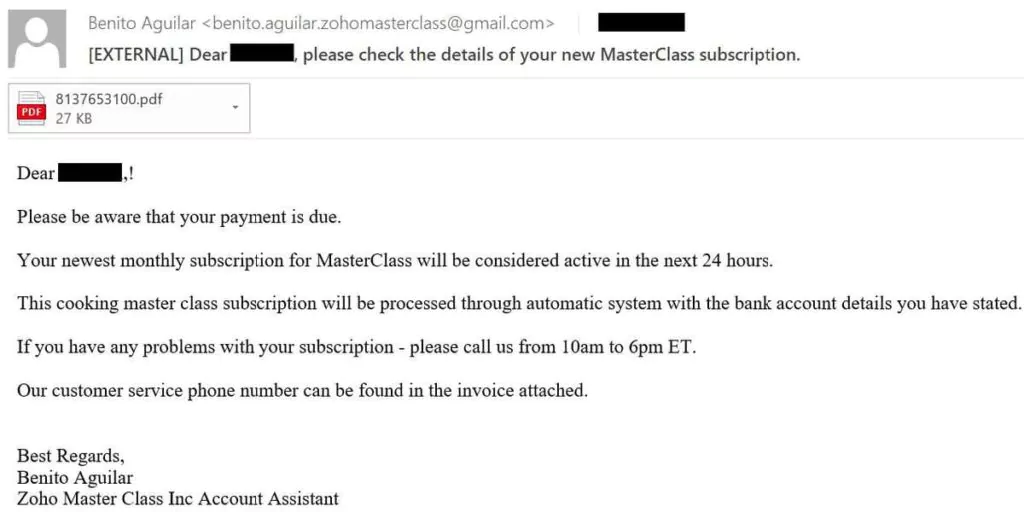
In this real-life scenario, an invoice file is sent for further communication.
Quantum, SRG, and Zion groups targeted over a hundred organizations and countless people, gained access to over 20 high-profile points just in the first half of 2022 and demanded millions as ransom.
Callback Phishing is Still Relevant
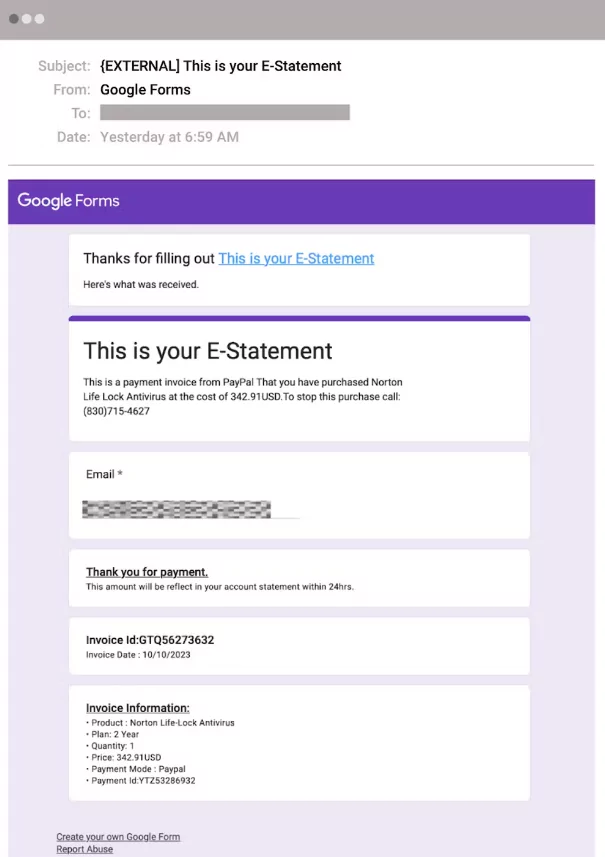
Recent developments in cyber threats reveal a sophisticated use of Google Forms in callback phishing, making it increasingly challenging to detect these attacks. As highlighted in a recent Abnormal Security blog, attackers are impersonating reputable brands in emails and directing victims to call a phone number, under the pretense of disputing charges in a new campaign. This technique cleverly bypasses traditional security measures by not containing malicious links or attachments directly in the emails. Instead, the attackers leverage Google Forms for confirmation emails.
This evolving tactic aligns with Callback Phishing. The ongoing campaign involves a sophisticated phishing scheme where attackers send emails impersonating well-known brands. These emails urge recipients to call a provided phone number to dispute false charges. When the victim calls, they’re directed to a fake customer service representative who manipulates them into providing remote access to their device or divulging sensitive information. The attackers also use Google Forms to send confirmation emails, adding a layer of legitimacy and bypassing traditional email security measures due to Google’s trusted domain.
How to Protect from Callback Phishing Attacks?
- The essential point of protection is detecting malicious email quickly and, if possible, deleting it without opening it.
- If you are unsure of the legitimacy of the incoming mail, you should have it checked by your organization’s IT Department or the appropriate authority.
- Even if the authenticity of the incoming email is not suspected, check the content, and reassess an email that asks you to take urgent action.
- We strongly recommend that employees receive security awareness training to create this awareness.
- In addition, organizations should inform their employees about Callback Phishing and identify organizational shortfalls by performing inspections that simulate the attack.
- Callback Phishing campaigns can bypass email filters, though attack surface management solutions allow you to know and control everything attackers can learn about your organization from the external web and enable you to take proactive measures against possible attack vectors.



































