
APT Profile: APT-C-35 / DoNot Team
[Update] June 20, 2023: A new espionage campaign attributed to APT-C-35 (DoNot Team) targets users in Pakistan with trojanized apps on Google Play, added the subheading: “New APT-C-35 Campaign Targets Pakistan Users with Rogue Google Play Apps.”
Advanced Persistent Threat groups are known for their sophisticated attacks and ability to stealthily stay in a system for a long time. These groups are commonly nation-state-sponsored, and they carry out various espionage or sabotage attacks for the interests of their nations.
Russian, Iranian, Chinese, and North Korean APT actors usually play a role in major incidents globally, such as Russian APT group Sandworm‘s attack during the 2018 PyeongChang Winter Olympics or the Wannacry ransomware attack of North Korean APT group Lazarus. However, some groups are not as sophisticated as other groups that have a global impact but carry out major operations for their national interest. As an example of this, APT-C-35 will be discussed in this article.
Who is APT-C-35?
APT-C-35, Brainworm or DoNot Team, is an Advanced Persistent Threat (APT) believed to be linked with the Indian government. The group is known to have been active since 2016. Also, APT-C-35’s primary motivation seems to be espionage for the interests of the Indian government, and cybersecurity researchers observed that they carried out various campaigns with this aim. When we consider Operation Hangover, a campaign believed to be linked to the group, it is possible to say that they have been active since 2013 or even 2010.
Some sources also suggest that another Indian state-sponsored APT group Patchwork and APT-C-35’s attack patterns overlap and may be the same actor. It is possible to say that their attack patterns are similar, but their targets seem different. There is a possibility that they are the same threat actor, yet there is no certain proof of that claim.
Who Are APT-C-35’s Targets?
The group’s first observed attack was against a telecom company in Norway; however, since the group’s primary motivation seems to be espionage for the interests of the Indian government and backed by observations, the APT-C-35 mainly targets South Asia.
Looking at the majority of its observed attacks, it is possible to say that the group mostly targets the Kashmir region due to the Kashmir Conflict. The Conflict is a long-standing territorial dispute between India and Pakistan over Kashmir. India and Pakistan claim sovereignty over the entire region, but each controls only a part. The issue remains unresolved, and efforts to find a lasting solution through negotiations and diplomatic channels have so far been unsuccessful.
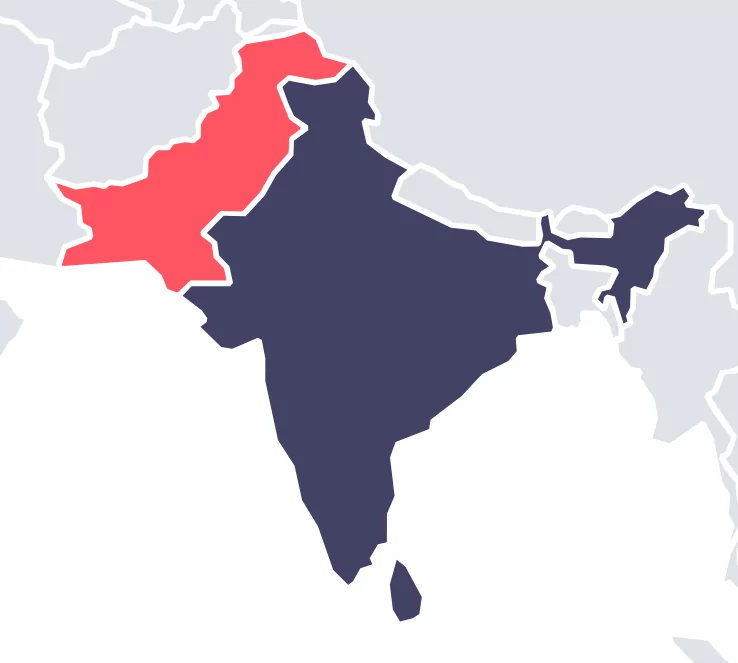
The sectors listed below in the observations on affected countries increase the likelihood of attacks due to the Kashmir dispute. The group targets:
- Governments,
- Military organizations,
- Ministries of Foreign Affairs,
- Embassies.
How Does APT-C-35 Attack?
Based on the observed attacks, the group is conducting spear phishing campaigns. During spear phishing campaigns, they deliver their malware as documents containing malicious macros.

The group utilizes Macros to gain remote access to their target, which is found in various Microsoft Office programs such as Word, Excel, and PowerPoint. They achieve this by using Windows Framework RTF files with .doc extensions, which include links that allow them to download malware and ultimately gain control over the system.
As observed from various attacks, the group has seen carried out its operations by exploiting CVE-2018-0802 (Microsoft Office Memory Corruption Vulnerability), CVE-2017-0199 (Microsoft Office Remote Code Execution Vulnerability), and CVE-2017-8570 (Microsoft Office Remote Code Execution Vulnerability.) But, the group has seen exploiting CVE-2017-11882 vulnerability in most of its attacks. This vulnerability is a memory corruption issue seen in Microsoft Office. When the malicious document is opened, it enables the attacker to execute remote code on the victim’s machine without needing any user interaction.
The malicious document, running as a dropper, drops and executes a downloader. Then it downloads plugins such as keylogger, screenshot taker, etc., to the victim’s machine for espionage purposes. For example, one of the components of DarkMusical malware enumerates all files in %public%MusicSymphony and uploads those that match the extensions: doc, docx, eml, inp, jpeg, jpg, msg, odt, pdf, pps, ppsx, ppt, pptx, rtf, txt, xls, and xlsx.
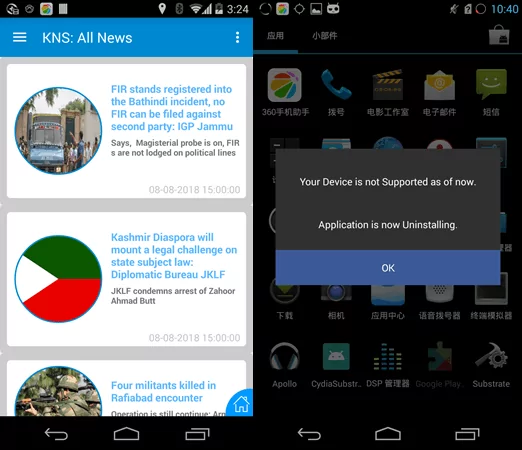
In addition to malicious documents, the group also appears to have Android malware, such as Android RAT malware found as a rogue Kashmir News Service Lite app and more like that.

The group’s Android malware disguises itself in two different ways. Fake app icons and error messages. Observations show that after the software runs, it sends a deception message to make it look like the software is deleting itself. In the meantime, the software deletes its shortcuts but continues its espionage activities in the background.
New APT-C-35 Campaign Targets Pakistan Users with Rogue Google Play Apps
Recent findings indicate that the group has been focusing on targeting individuals in Pakistan using malicious Android apps, which the threat actors made available via a Google Play account they established under the publisher name “SecurITY Industry” and the “All your secure applications at once” motto.
The attack employs a stager payload to gather information and prepare for a second-stage attack utilizing advanced malware.
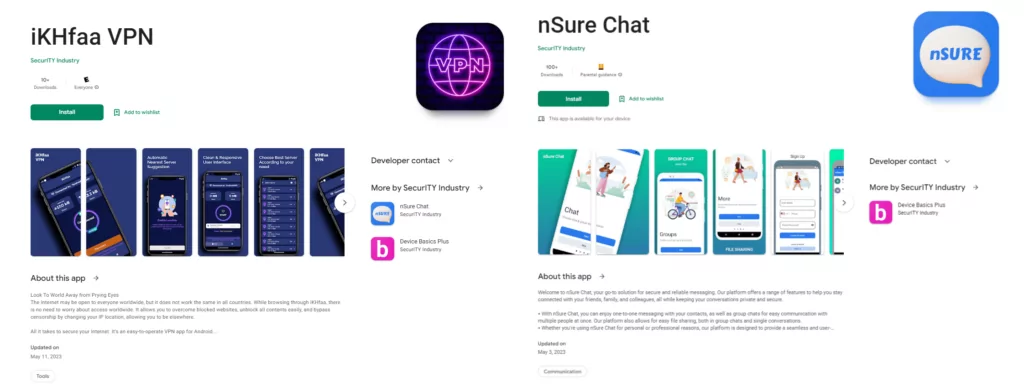
One prominent red flag associated with rogue apps is the notably low number of downloads. In this instance, the apps that APT-C-35 used in its campaign had a small download count.
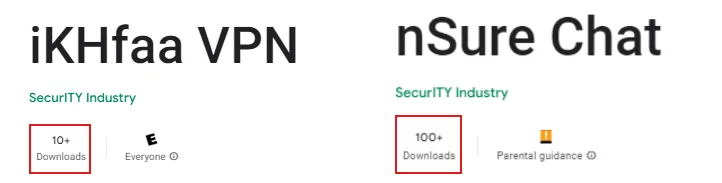
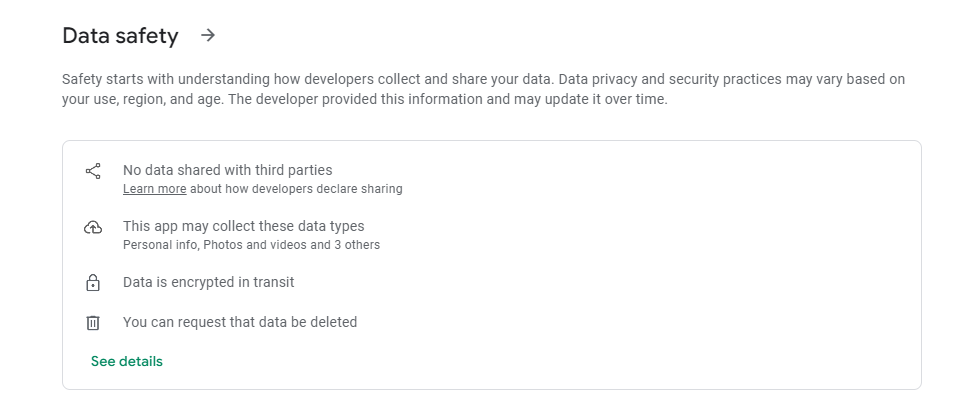
Information about what data the apps are storing or what kind of methodology they follow is one of the indicators of the apps’ purpose. For example, nChat explicitly states that it can store personal information, photos, videos, and three other data types:
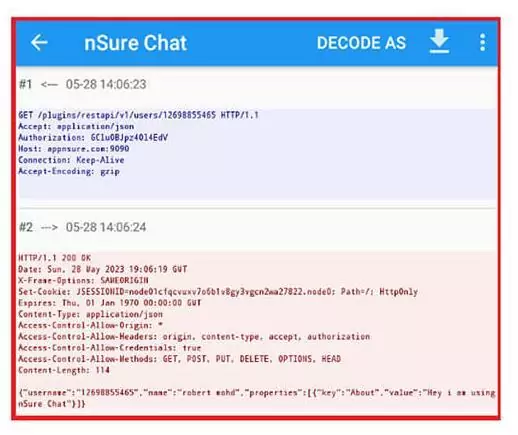
Analyzing how the app works through source code and behavior analysis will also shed light on whether the app was created for malicious purposes. As a result of an analysis conducted by the researchers, the captured live HTTP request reveals data being transmitted to appnsure[.]com:9090 in the JSON format with an authorization key. This data indicates that the command and control server is also recording information about new users who install this app, including their usernames and passwords, which are sent in encrypted text by using letsencrypt.
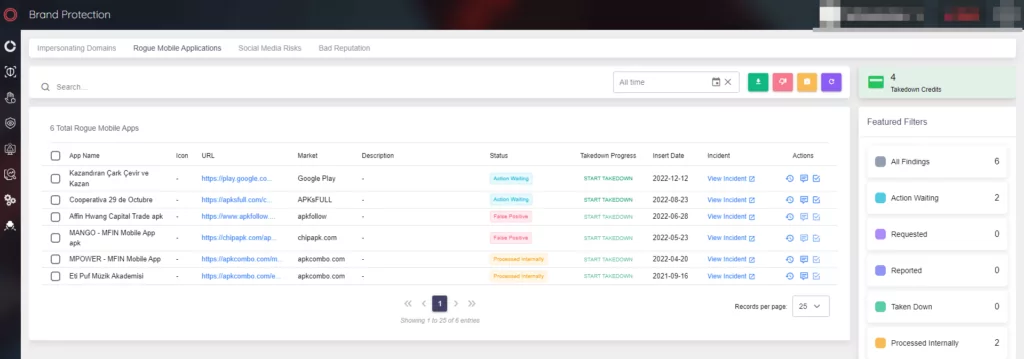
How to Track a Rogue App with SOCRadar?
SOCRadar XTI continuously scans the app stores for rogue apps that may imitate the company and lists the suspicious ones under the Rogue Mobile Applications heading under the Brand Protection page of the Digital Risk Protection module:
Which Tools and Malware Does APT-C-35 Use?
The group created some malware for espionage activities and developed them over time. Examples of these include EHDevel, which the group created itself, and the recently updated version of the EHDevel, the YTY malware framework. Also, the malware developed by the group seems to focus on file collection, screenshots, and keylogging.
YTY Framework
The YTY is a modular, plugin-based malware framework that gathers and transmits data. The framework is comprised of a series of downloaders that ultimately install a backdoor. Once the backdoor is installed, threat actors can use it to retrieve and execute other components of the Donot Team’s tools, including applications that collect files, take screenshots, capture keystrokes, create reverse shells, and perform other actions.
According to the 2023 advisory published by the Cabinet Division of Pakistan, the timeline of the malware used by the group is as follows:
- Between 2020 to 2021, the group delivered Jaca malware in a PowerPoint document and Gedit malware in an RTF document.
- In February 2021, Henos malware was delivered as an RTF document,
- In June 2021, DarkMusical malware was delivered as an Excel file.
Recent Cyber Attack Allegedly Linked to APT-C-35
In January 2023, a cyber-attack occurred during voting in the Khalistan referendum in Brisbane, Australia. The Khalistan referendum is an unofficial and non-binding vote organized by the Sikhs for Justice group across various countries. Its purpose is to gauge support for establishing an independent Sikh state called Khalistan. However, the Indian government has refused to allow such a referendum, considering it threatens national unity and integrity.
According to Pakistani newspaper The Nation, it was reported that the electronic online voting system faced a significant cyber-attack from suspected Indian hackers, disrupting the voting process three times.
Although it is claimed that APT-C-35 carried out the cyber attack, it is unlikely that APT-C-35 performed this defacement based on their past attacks. However, according to Sikhs For Justice (SFJ), this is not the first time this has happened, so it is possible that another Indian state-sponsored APT group could be carrying out this series of attacks, or another possibility that APT-C-35 could have planned an attack specifically for this situation.
Conclusion
It cannot be easy to protect against APTs because their advanced techniques allow them to avoid detection for extended periods. APTs also update their attack strategies and technologies to perform more successful attacks. Because it carries out most of its attacks by exploiting a specific vulnerability, such as CVE-2017-11882, it may not be said for the APT-C-35; however, this does not mean that the group will not change its method. And it is helpful to know that the group is a significant risk, like any threat actor, considering its successful operations.
Recommendations Against APT-C-35
- The group’s target is mainly governments, military organizations, and embassies of South Asian countries, specifically the Kashmir region. Organizations working in these industries or this area should be extra vigilant, and their employees should have a high level of cybersecurity awareness whenever possible.
- The group is conducting its attack by delivering malicious documents. Avoiding downloading documents attached to emails from unknown sources could be preventive.
- Organizations must consider that the group’s malicious documents often exploit the CVE-2017-11882, so IT teams should take measures against this vulnerability.
- Organizations must monitor and detect the executables to avoid the execution of files such as PsExec[.]exe, Netcat[.]exe, and Socat[.]exe. Also, it is vital to block the executables being executed from %temp% and AppData directory.
- The group has been observed distributing Android apps from various phishing domains and being cautious about installing apps from external sources should be preventive against this threat.
SOCRadar’s Company Vulnerabilities module in the External Attack Surface Management (EASM) service allows organizations to observe the vulnerabilities in their IT structures and take necessary actions to eliminate the risk factors in light of this information.
MITRE ATT&CK TTPs
TTPs of yty framework used by the group:
|
Technique ID |
Technique Name |
Resources:
- https://propakistani.pk/2023/03/08/indian-govt-backed-hacking-group-donot-is-targeting-pakistan/
- https://www.zdnet.com/article/donot-team-apt-will-strike-govt-targets-for-years-until-they-succeed/
- https://www.rewterz.com/rewterz-news/rewterz-threat-alert-apt-c-35-aka-donot-apt-group-active-iocs/
- https://niiconsulting.com/checkmate/2013/05/indian-apt/
- https://www.welivesecurity.com/2022/01/18/donot-go-do-not-respawn/
- https://mp.weixin.qq.com/s?__biz=MzUyMjk4NzExMA==&mid=2247486186&idx=1&sn=efafc115ec7c9e8f589725de2c73cf69
- https://web.archive.org/web/20170825010151/http://enterprise-manage.norman.c.bitbit.net/resources/files/Unveiling_an_Indian_Cyberattack_Infrastructure.pdf
- https://www.bitdefender.com/files/News/CaseStudies/study/171/Bitdefender-Whitepaper-EHDevel-A4-en-EN.pdf




































