
ClickFix Campaign: Fake Google Meet Alerts Spread Malware Across Windo...
ClickFix Campaign: Fake Google Meet Alerts Spread Malware Across Windows and macOS The ClickFix campaign represents a sophisticated use of social engineering to deploy malware across both Windows and ...

Water Makara Campaign: A Sophisticated Spear-Phishing Attack on Brazil...
Water Makara Campaign: A Sophisticated Spear-Phishing Attack on Brazilian Enterprises The Water Makara campaign is a highly sophisticated spear-phishing attack aimed specifically at Brazilian organiza...

Chinese State-Sponsored Threat Actors Breach U.S. Treasury Department ...
Chinese State-Sponsored Threat Actors Breach U.S. Treasury Department in Major Cybersecurity Incident [Update] January 7, 2025: “CISA Provides Update on U.S. Treasury Breach” Chinese state-sponsored ...

Four-Faith Routers Exploited Through CVE-2024-12856 Vulnerability
Four-Faith Routers Exploited Through CVE-2024-12856 Vulnerability A newly discovered vulnerability, tracked as CVE-2024-12856, is actively being exploited in Four-Faith routers. This vulnerability all...
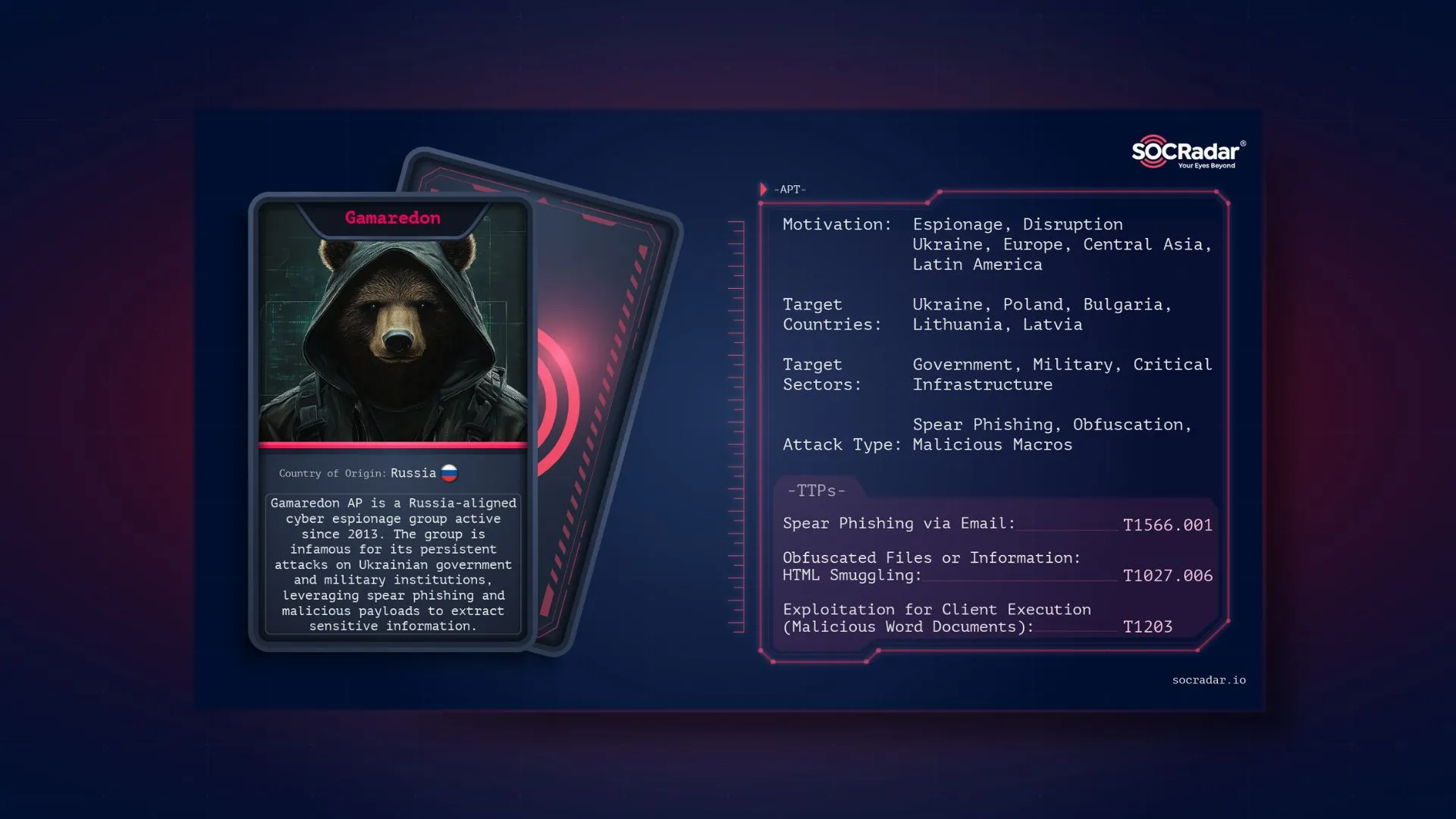
Dark Web Profile: Gamaredon APT
Dark Web Profile: Gamaredon APT Gamaredon APT is a notorious Russian cyber espionage group active since 2013. Closely linked to Moscow’s Federal Security Service (FSB), it has primarily targeted...

Exploring Telegram DDoS Groups: Threats, Tools, and Evolving Strategie...
Exploring Telegram DDoS Groups: Threats, Tools, and Evolving Strategies Telegram-based hacktivist groups have established themselves as a critical component of the modern cyber threat landscape. These...
Tracking Cybercriminals on the Dark Web: The Role of AI-Powered Threat...
Tracking Cybercriminals on the Dark Web: The Role of AI-Powered Threat Intelligence The Dark Web has long been a hub for illicit activities. It serves as a marketplace for stolen data, malware, and ha...

DUX Health Leak, Energy Sector Breaches, Chrome Exploit, Spotify Tool,...
DUX Health Leak, Energy Sector Breaches, Chrome Exploit, Spotify Tool, and More Dark Web Highlights Hacker forums are buzzing with alarming activity this week, with SOCRadar’s Dark Web Team uncovering...

Phishing Attack Compromises Cyberhaven’s Chrome Extension, Impacts Tho...
Phishing Attack Compromises Cyberhaven’s Chrome Extension, Impacts Thousands – What You Need to Know [Update] January 2, 2025: “New Details on the Chrome Extension Phishing Attack” A significant cyber...

The Threat of SIM Swapping Attacks on Financial Institutions
The Threat of SIM Swapping Attacks on Financial Institutions SIM swapping attacks have evolved into a growing threat in the digital age, affecting not only individuals but, through them, financial ins...

Top 10 Identity Attacks in 2024: Protecting Credentials in a Digital W...
Top 10 Identity Attacks in 2024: Protecting Credentials in a Digital World In 2024, identity attacks have advanced to new levels of sophistication, targeting credentials with ruthlessness. From wreaki...

Severe Vulnerability in Palo Alto Networks PAN-OS Exposes Firewalls to...
Severe Vulnerability in Palo Alto Networks PAN-OS Exposes Firewalls to Denial of Service (CVE-2024-3393) [Update] December 31, 2024: CVE-2024-3393 has been added to the CISA KEV catalog* Palo Alto Net...
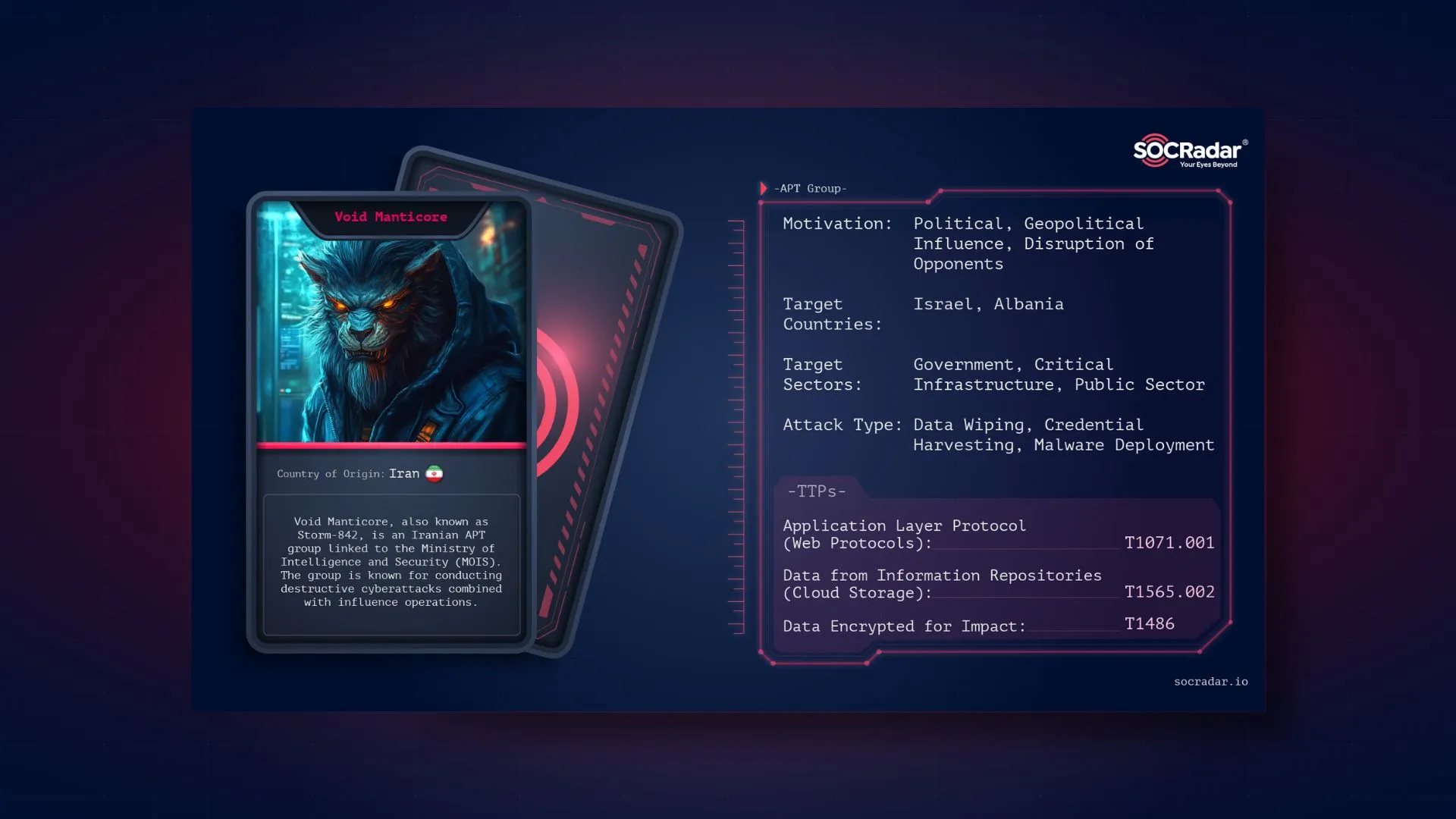
Dark Web Profile: Storm-842 (Void Manticore)
Dark Web Profile: Storm-842 (Void Manticore) On September 23, 2022, the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) released a joint advisory ...

Cyber Threat Intelligence for Supply Chain Security
Cyber Threat Intelligence for Supply Chain Security Modern supply chains are more connected than ever, forming the backbone of global commerce. However, this interconnectivity also makes them prime ta...
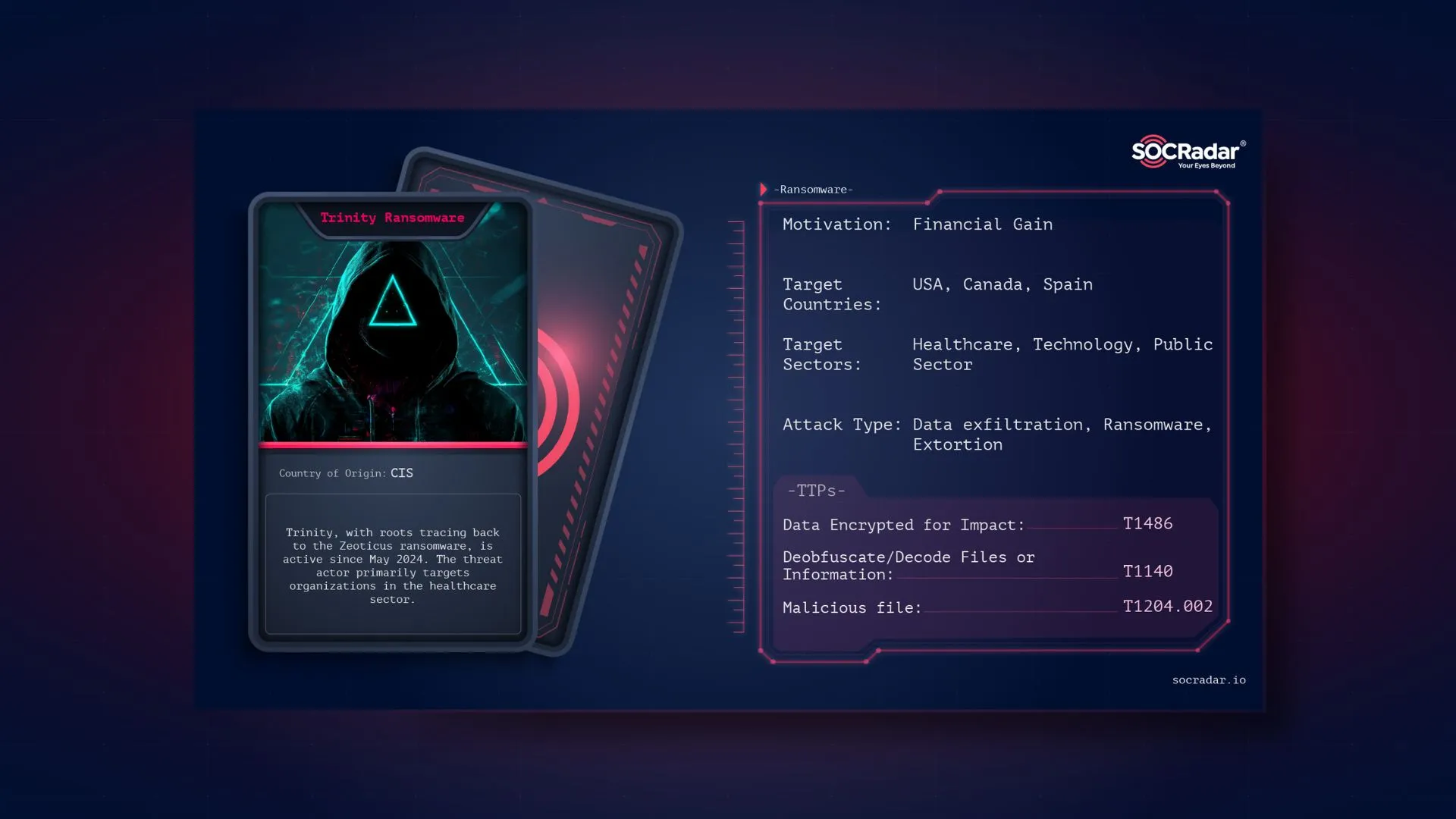
Dark Web Profile: Trinity Ransomware
Dark Web Profile: Trinity Ransomware First discovered in May 2024, the Trinity ransomware has quickly positioned itself as a significant actor in the threat landscape. Leveraging a double extortion ta...

DarkVision RAT: A Persistent Threat Delivered via PureCrypter
DarkVision RAT: A Persistent Threat Delivered via PureCrypter The DarkVision RAT malware campaign leverages the PureCrypter loader to infiltrate networks and compromise data across multiple sectors. D...

Top Phishing Tricks Attackers Use to Target Employees & The Recent ‘Yo...
Top Phishing Tricks Attackers Use to Target Employees & The Recent ‘You’re Fired’ Campaign Phishing remains one of the most prevalent and effective cyber attack methods, thriving on deceptio...

How to Protect Against Digital Risks in Three Steps
How to Protect Against Digital Risks in Three Steps threats to an organization’s digital assets are constantly evolving, cybercriminals are no longer solely focused on breaching your internal network;...
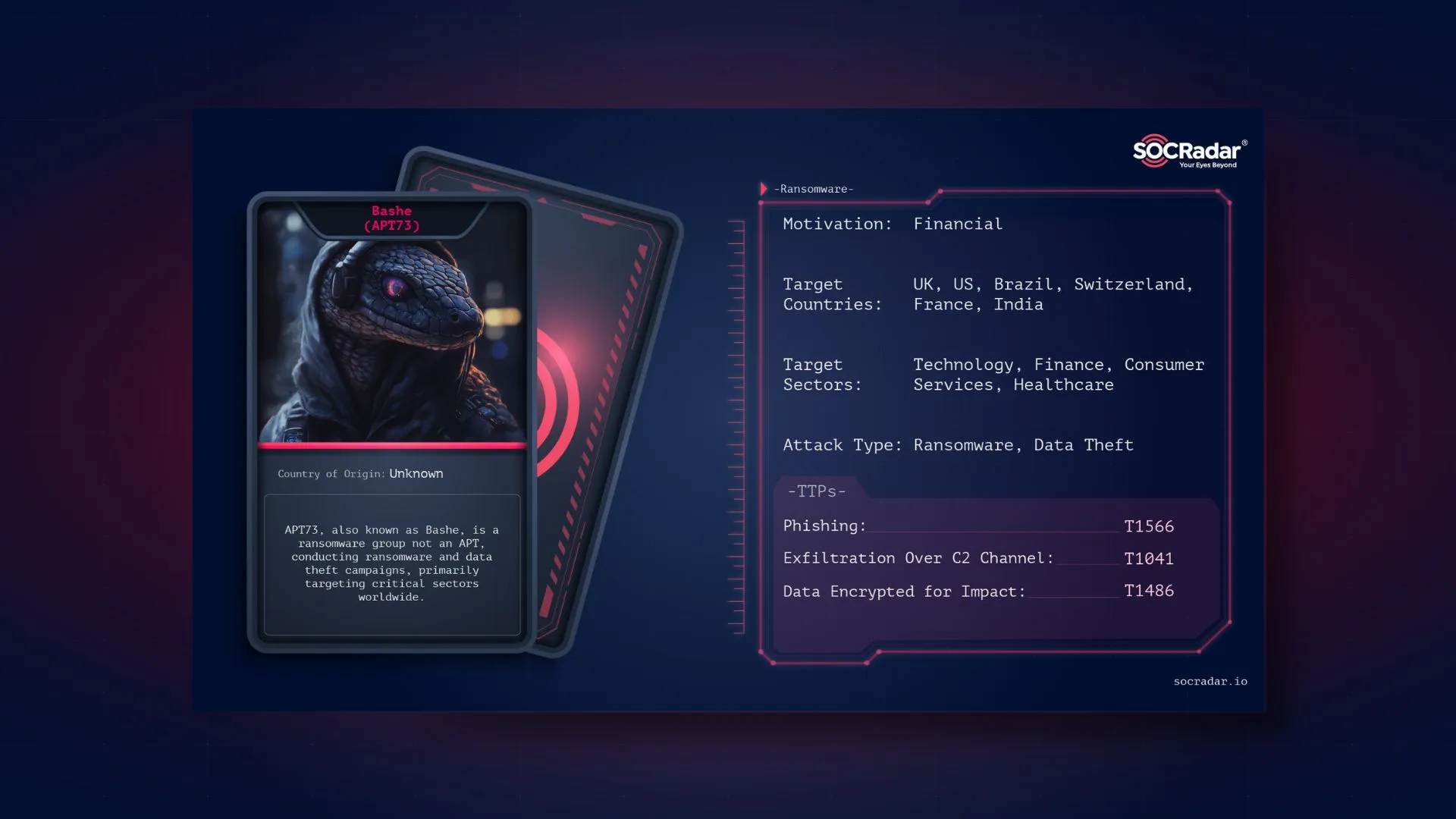
Dark Web Profile: Bashe (APT73)
Dark Web Profile: Bashe (APT73) Bashe, previously known as APT73 or Eraleig, is a ransomware group that emerged in 2024, employing tactics reminiscent of LockBit to target critical industries across d...

Severe Path Traversal Vulnerability in Adobe ColdFusion (CVE-2024-5396...
Severe Path Traversal Vulnerability in Adobe ColdFusion (CVE-2024-53961), Update Now A critical vulnerability in Adobe ColdFusion versions 2023 and 2021 has prompted urgent security updates. Alarmingl...
































