
Pre-Auth RCE Vulnerability in Apache OFBiz (CVE-2024-38856) Is Under A...
Pre-Auth RCE Vulnerability in Apache OFBiz (CVE-2024-38856) Is Under Active Exploitation, CISA Warns [Update] September 6, 2024: “New RCE Vulnerability (CVE-2024-45195) Discovered in Apache OFBi...

The Ransomware Playbook: Evolving Threats and Defense Strategies for 2...
The Ransomware Playbook: Evolving Threats and Defense Strategies for 2024 In 2024, ransomware will continue to rank as one of the most pervasive and effective threats to organizations globally. Attack...

Alleged Sales: AMD Breach, U.S. Tax Portal Access, and Fortinet Exploi...
Alleged Sales: AMD Breach, U.S. Tax Portal Access, and Fortinet Exploit Recent findings by the SOCRadar Dark Web Team highlight several significant cyber threats targeting various organizations. Among...
Tracking the Cookies: The World of Data Brokers
Tracking the Cookies: The World of Data Brokers Data brokers are companies that specialize in collecting, processing, and selling large amounts of personal and business data. They gather information ...

Navigating the Cybersecurity Landscape: Insights from José Carlos Hurt...
Navigating the Cybersecurity Landscape: Insights from José Carlos Hurtado Hernández This interview is part of our ongoing series with industry leaders who share their experiences and strategies in the...

Vulnerability in Python's pandas Library (CVE-2024-42992)
Vulnerability in Python’s pandas Library (CVE-2024-42992) [Update] August 27, 2024: CVE has been marked “REJECT” in the CVE List. Find more information in the blog post. Python’s popular data analysis...

How to Identify Spear Phishing Attacks
How to Identify Spear Phishing Attacks Spear phishing remains one of the most effective tactics cybercriminals use to breach enterprise networks. These highly targeted attacks have only increased in r...

The Dominant Role of Compromised Credentials in Data Breaches
The Dominant Role of Compromised Credentials in Data Breaches Compromised credentials are at the heart of modern cyber threats, driving a significant portion of data breaches across industries. Approx...

Examples of AI-Assisted Cyber Attacks
Examples of AI-Assisted Cyber Attacks AI-assisted cyberattacks, driven by the rapid advancements in generative AI, have become a significant concern in the cybersecurity landscape. Cybercriminals are ...

Secure the Credentials: How to Work With Breach Datasets
Secure the Credentials: How to Work With Breach Datasets Data breaches have become an increasingly common and devastating threat to businesses of all sizes. The need for proactive measures to secure y...

Best Threat Detection and Response (TDR) Practices
Best Threat Detection and Response (TDR) Practices The ability to detect and respond to threats swiftly is more critical than ever. Organizations must adopt a robust Threat Detection and Response (TDR...

Advanced Strategies for Effective Network Security Monitoring
Advanced Strategies for Effective Network Security Monitoring Network Security Monitoring (NSM) is critical for safeguarding an organization’s IT infrastructure against cyber threats. It involves coll...

What is IOC Management?
What is IOC Management? IOC Management is a critical aspect of cybersecurity that involves identifying, handling, and responding to data points indicating potential security breaches or malicious acti...

IBM’s Cost of Data Breach Report 2024: Unveiling the True Cost of Cybe...
IBM’s Cost of Data Breach Report 2024: Unveiling the True Cost of Cybersecurity Failures Managing a data breach goes beyond simply addressing the financial impact; it involves tackling a crisis that c...

What is Pretexting? Definition and Examples in Cybersecurity
What is Pretexting? Definition and Examples in Cybersecurity Pretexting is a social engineering tactic in which attackers fabricate a scenario or a “pretext” to trick people into disclosin...

Hackers Claim a Zoom Breach, Alleged FedEx Accounts and Government Log...
Hackers Claim a Zoom Breach, Alleged FedEx Accounts and Government Logs on Sale Over the past week, the SOCRadar Dark Web Team has uncovered several alarming cyber threats targeting various sectors. N...

Shedding Light on Indonesia Threat Landscape Report 2024
Shedding Light on Indonesia Threat Landscape Report 2024 In the rapidly evolving digital age, Indonesia, Southeast Asia’s largest economy, has emerged as a focal point for cyber threats. As the countr...

Annual Europe Threat Landscape Report 2024
Annual Europe Threat Landscape Report 2024 In an era where cyber threats evolve rapidly, staying ahead of the curve is essential. Our latest Annual Europe Threat Landscape Report 2024 offers a compreh...

August 2024 Patch Tuesday Highlights: 89 CVEs, 6 Zero-Day Vulnerabilit...
August 2024 Patch Tuesday Highlights: 89 CVEs, 6 Zero-Day Vulnerabilities Under Exploitation [Update] September 4, 2024: “Details of CVE-2024-38106 and PoC Exploit” [Update] August 20, 2024: “Lazarus ...
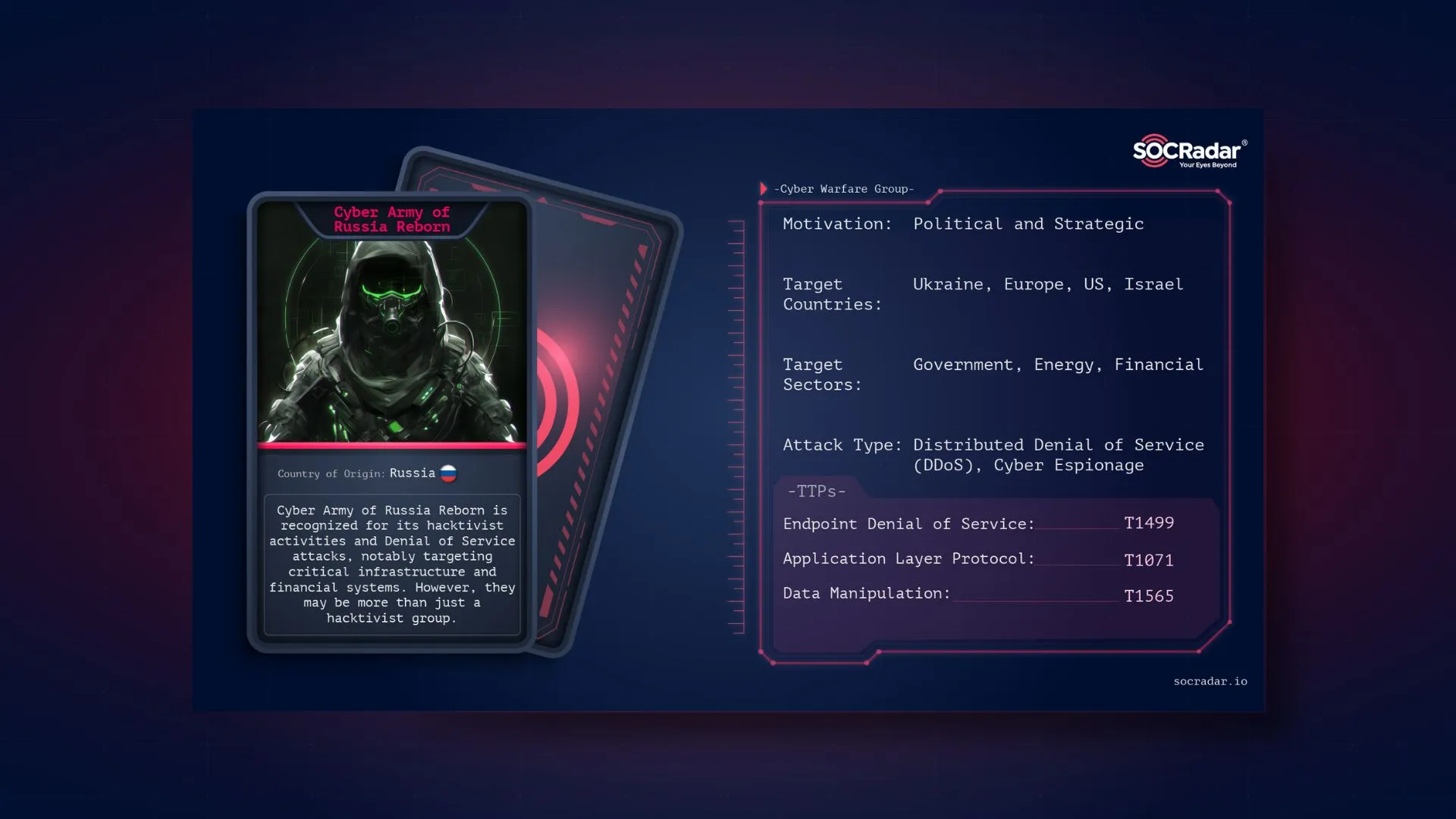
Dark Web Profile: Cyber Army of Russia Reborn
Dark Web Profile: Cyber Army of Russia Reborn In Russian Народная CyberАрмияa (People’s CyberArmy) is a prominent hacktivist group involved in disruptive attacks on critical infrastructure and financi...































