

Excel's Blind Spot: The Strategic Deployment of Agent Tesla Malware by...
Excel’s Blind Spot: The Strategic Deployment of Agent Tesla Malware by Cyberattackers In the ever-evolving landscape of cyber threats, a notable trend has emerged: the exploitation of a longstan...

Latest Zero-Day Vulnerabilities: UNC4841 Targets Barracuda ESG with CV...
Latest Zero-Day Vulnerabilities: UNC4841 Targets Barracuda ESG with CVE-2023-7102, Apache OFBiz Authentication Bypass (CVE-2023-51467) The UNC4841 group, linked to China, is targeting Barracuda Email ...

Dark Web Profile: Haghjoyan
Dark Web Profile: Haghjoyan The Haghjoyan hacker group, self-identifying as the Iranian cyber army, emerged at the forefront of cyber warfare during the Israel-Hamas conflict. Their presence, prominen...

Executive Interview: A Deep Dive into Mel Migrino's Insights and Cutti...
Executive Interview: A Deep Dive into Mel Migrino’s Insights and Cutting-Edge Innovations” In the dynamic landscape of cybersecurity, staying abreast of emerging trends is essential for ef...

Weekly Vulnerability Summary by CISA: Ivanti Avalanche, Apache Dubbo, ...
Weekly Vulnerability Summary by CISA: Ivanti Avalanche, Apache Dubbo, OpenSSH, and More The Cybersecurity and Infrastructure Security Agency (CISA) has released a new vulnerability summary for the lat...

Challenge of Protecting PII, Hunters Become the Hunt: OpenAI Vulnerabi...
Challenge of Protecting PII, Hunters Become the Hunt: OpenAI Vulnerability, Blackmailing of Bounty Hunters A paradox emerges: those who protect us from cyber threats are themselves becoming the hunted...

Navigating the Cybersecurity Landscape: An Interview with Santiago J. ...
Navigating the Cybersecurity Landscape: An Interview with Santiago J. López Galanes The cybersecurity landscape continually evolves in an era where technological advancements are transforming industri...
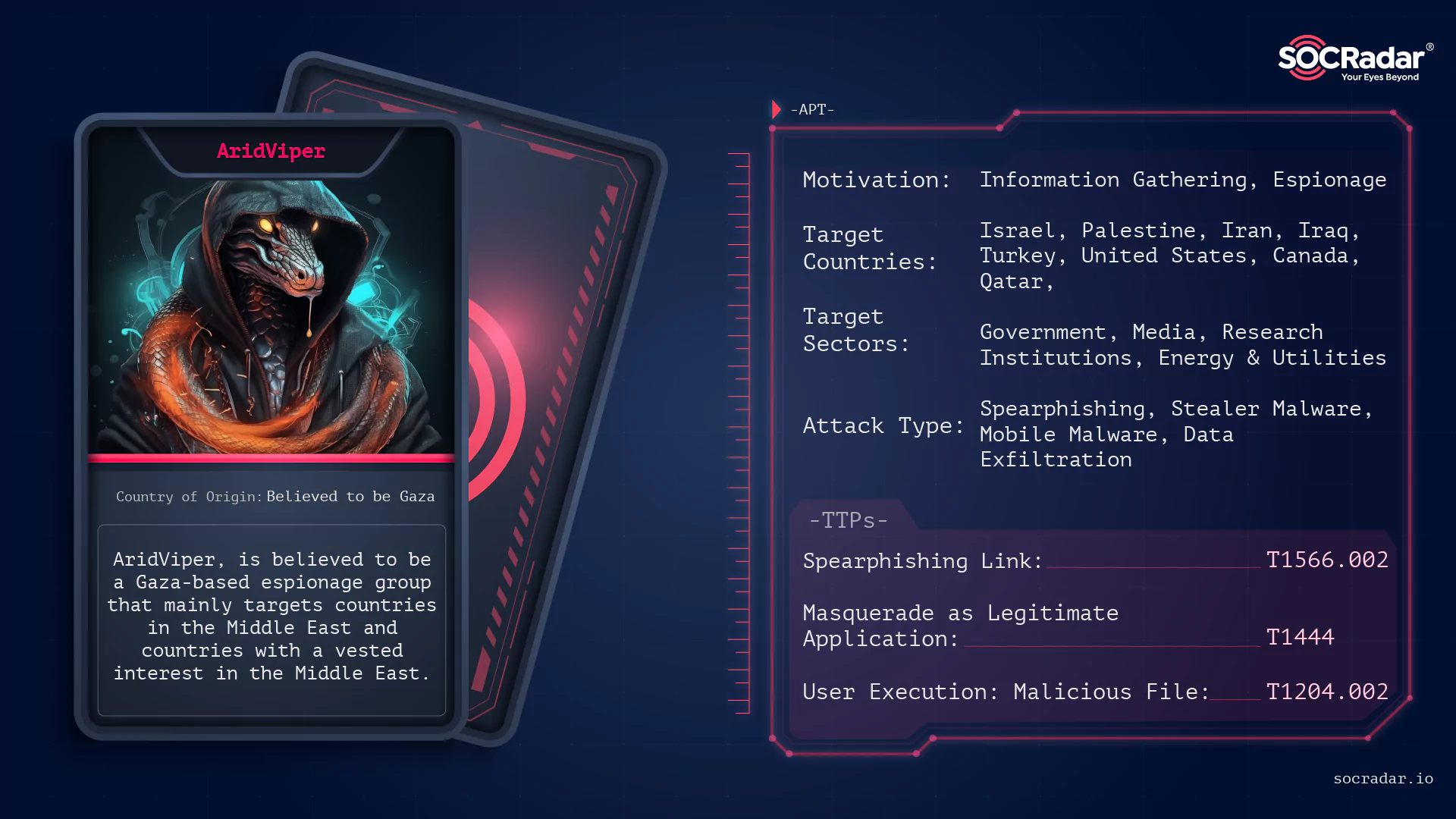
Threat Actor Profile: AridViper
Threat Actor Profile: AridViper A stealthy predator lurks in the vast, unforgiving digital desert, known as AridViper. Like a snake silently slithering through the sands, this state-sponsored cyber th...

Disney Data Leak, Meduza Stealer Sale, Nissan Australia and The Econom...
Disney Data Leak, Meduza Stealer Sale, Nissan Australia and The Economist Targeted in Cyberattacks Last week’s findings by the SOCRadar Dark Web Team include a substantial 1.9 million credit car...

Dark Peep #7: Shadows of Betrayal and Leadership in Flux
Dark Peep #7: Shadows of Betrayal and Leadership in Flux Shrouded in the mysterious alleys of the dark web, “Dark Peep #7” delves into a world where betrayals happen as often as tiny secre...

Dark Web Profile: Cyber Av3ngers
Dark Web Profile: Cyber Av3ngers The Cyber Av3ngers, reportedly connected to Iran’s Islamic Revolutionary Guard Corps, have become known for attacking critical infrastructure, especially in the ...

CISA Updates: Microsoft 365 Guidance, SCuBAGear Tool, Mozilla Alert, Q...
CISA Updates: Microsoft 365 Guidance, SCuBAGear Tool, Mozilla Alert, QNAP & FXC Vulnerabilities Enter KEV CISA has officially released the Microsoft 365 Secure Configuration Baselines, aiming to a...

Massive Data Leak by BidenCash: 1.9M Credit Card Details Exposed on Ha...
Massive Data Leak by BidenCash: 1.9M Credit Card Details Exposed on Hacker Forum The SOCRadar Dark Web Team detected a significant data breach on a hacker forum, revealing the leak of 1.9 million cred...

Over a Dozen Critical RCE Vulnerabilities in Ivanti Avalanche; Activel...
Over a Dozen Critical RCE Vulnerabilities in Ivanti Avalanche; Actively Exploited Chrome Zero-Day, CVE-2023-7024 Ivanti has issued security updates to address a total of 22 vulnerabilities identified...

Dark Web Profile: Cyber Toufan Al-aqsa
Dark Web Profile: Cyber Toufan Al-aqsa On November 16 2023, a new group emerged in the intricate web of modern cyber warfare: Cyber Toufan. This group, shrouded in the digital shadows, has recently ga...

ALPHV Seized, Unseized, Decrypted; Pandora's Box May Be Reopened
ALPHV Seized, Unseized, Decrypted; Pandora’s Box May Be Reopened Emerging as a significant player in the ransomware landscape, ALPHV (BlackCat) has established itself through sophisticated ranso...

Enhancing IoT Security with Cyber Threat Intelligence (CTI)
Enhancing IoT Security with Cyber Threat Intelligence (CTI) The Internet of Things (IoT) represents a significant technological advancement that is widely utilized in various aspects of our lives, inc...

Insights from CISO Michael Hamilton: Navigating the Ever-Evolving Cybe...
Insights from CISO Michael Hamilton: Navigating the Ever-Evolving Cybersecurity Landscape Cybersecurity constantly evolves in today’s fast-paced digital world, with new threats and technologies ...



































