
Top Threat Intelligence Use Cases for the Finance Sector-II
Top Threat Intelligence Use Cases for the Finance Sector-II Security departments in the financial industry are facing a daunting mission. They have to defend the company from an immense amount of indi...

Using Google Dorks for Threat Intelligence Operations
Using Google Dorks for Threat Intelligence Operations Enterprises have to deal with a range of mass campaigns as well as advanced attacks that target a specific industry or company. Threat actors use ...

Top Threat Intelligence Use Cases for the Finance Sector-I
Top Threat Intelligence Use Cases for the Finance Sector-I Security departments in the financial industry are facing a daunting mission. They have to defend the company from an immense amount of indis...

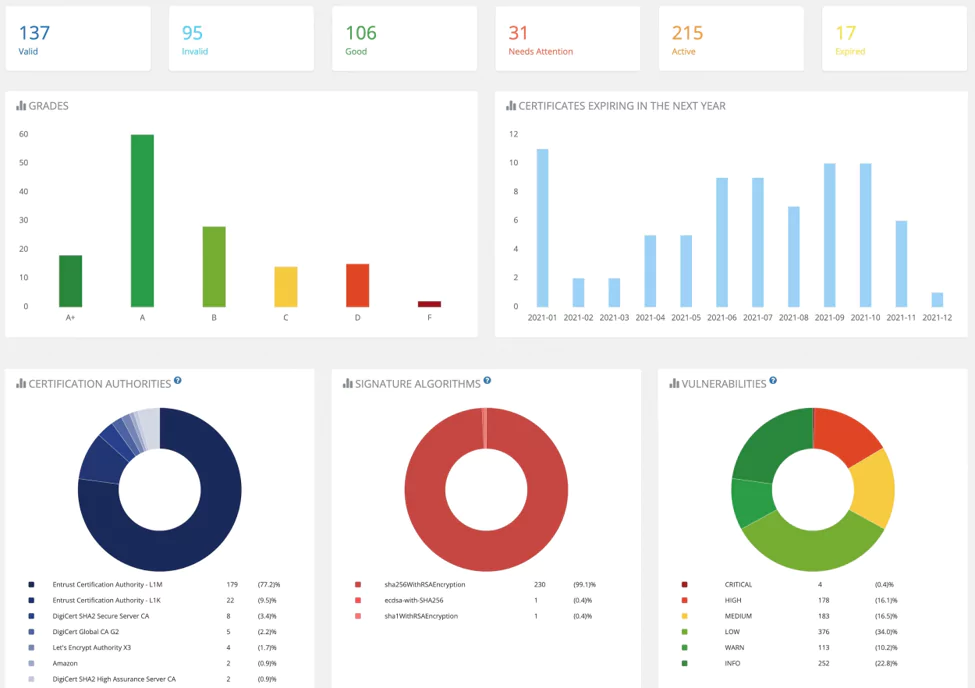
How Expired Digital Certificates Can Be a Nightmare?
How Expired Digital Certificates Can Be a Nightmare? The need to protect corporate data from increasing cyberattacks continues to be the top priority of every organization. One of the most important w...

How to Find Subdomains Using Free Online Services?
How to Find Subdomains Using Free Online Services? Subdomains are critical assets of your software applications and server infrastructure. They contain numerous details that can be useful to threat ac...

What’s External Attack Surface Management? Absolute Beginner Guide
What’s External Attack Surface Management? Absolute Beginner Guide External attack surface management (ASM) is the process of discovering, listing, classifying, analyzing, prioritizing, and monitoring...
Oops! Microsoft Lets Its SSL Certificate Expire Causing a Major Outage
Oops! Microsoft Lets Its SSL Certificate Expire Causing a Major Outage On February 3rd, Microsoft Teams suffered outages following the expiration of one of its SSL certificates. Microsoft’s collabora...

First Step to Zero Trust Strategy: Gain Visibility
First Step to Zero Trust Strategy: Gain Visibility Understanding the importance of Digital Asset Monitoring (DAM) is critical. Your adversaries spend the majority of their time doing discovery and map...

































