
What is a Rootkit and How to Detect It
What is a Rootkit and How to Detect It A rootkit is a software that allows hackers to gain access to and control a computer. Although most rootkits attack software and the operating system, some can a...
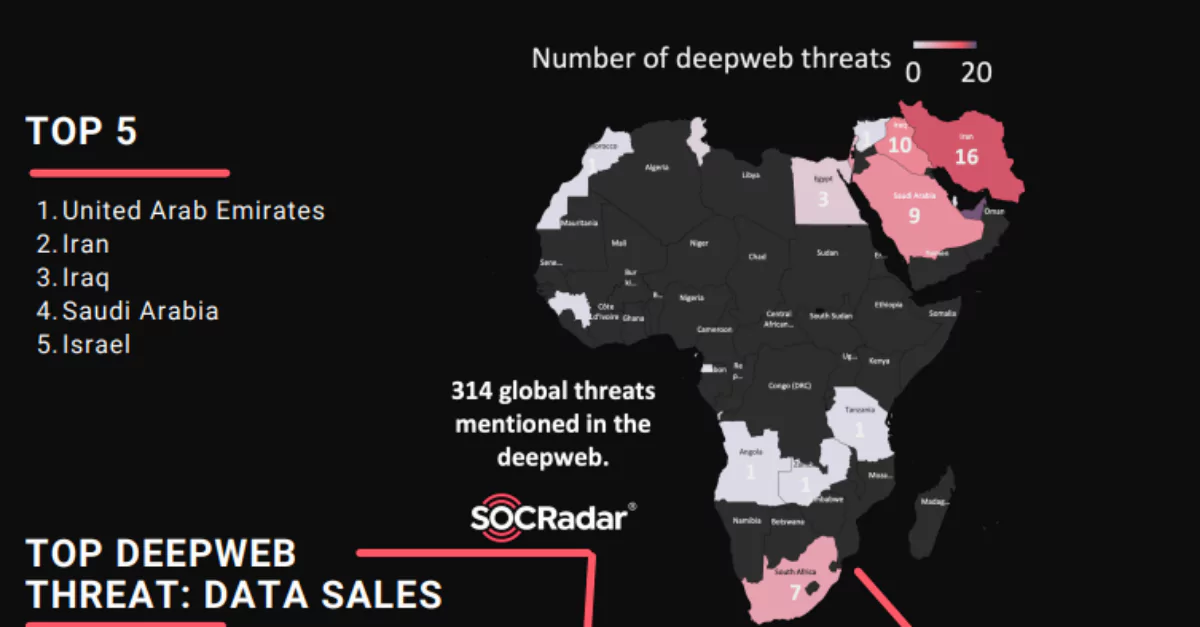
Data Sales Are The Biggest Deep Web Threat In MEA Region
Data Sales Are The Biggest Deep Web Threat In MEA Region The MEA Regional DeepWeb Report, which emerged with the research of the SOCRadar analyst team, is now available. Dark web incidents, hack...

Countries More Affected by Cyber Attacks in September: China and Thail...
Countries More Affected by Cyber Attacks in September: China and Thailand The APAC Regional DeepWeb Report, which emerged with the research of the SOCRadar analyst team, is now available. Dark web inc...
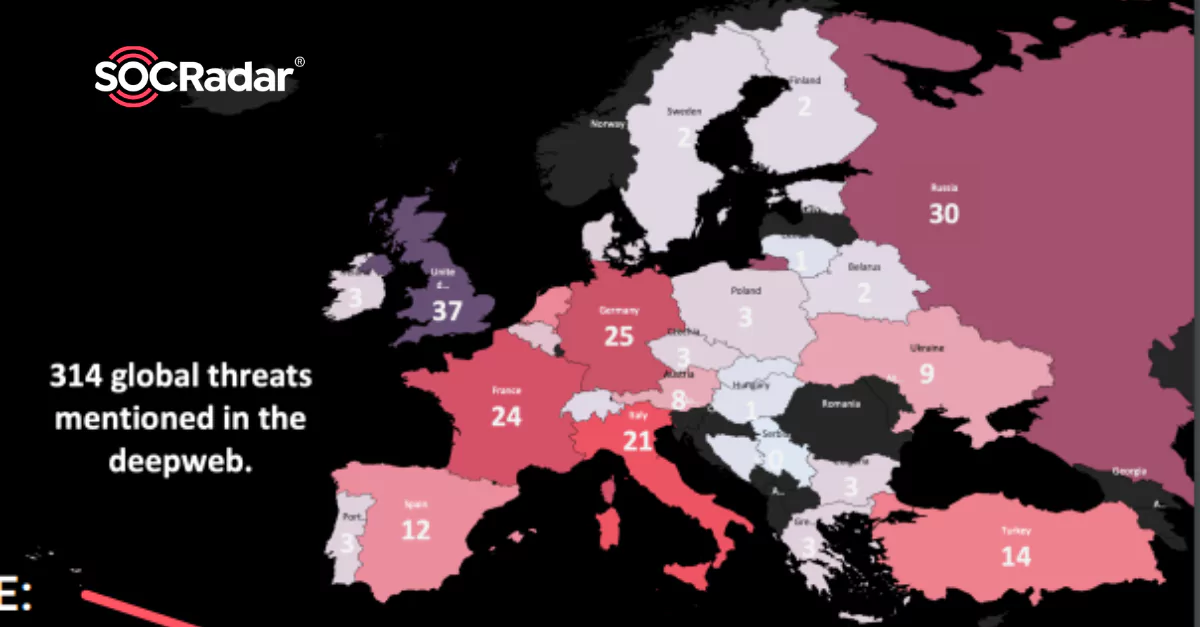
Ransomware Attacks on the Rise Around Europe
Ransomware Attacks on the Rise Around Europe The Europe Regional Deep Web Report, which emerged with the research of the SOCRadar analyst team, is now available. Dark web incidents, hacker forum...
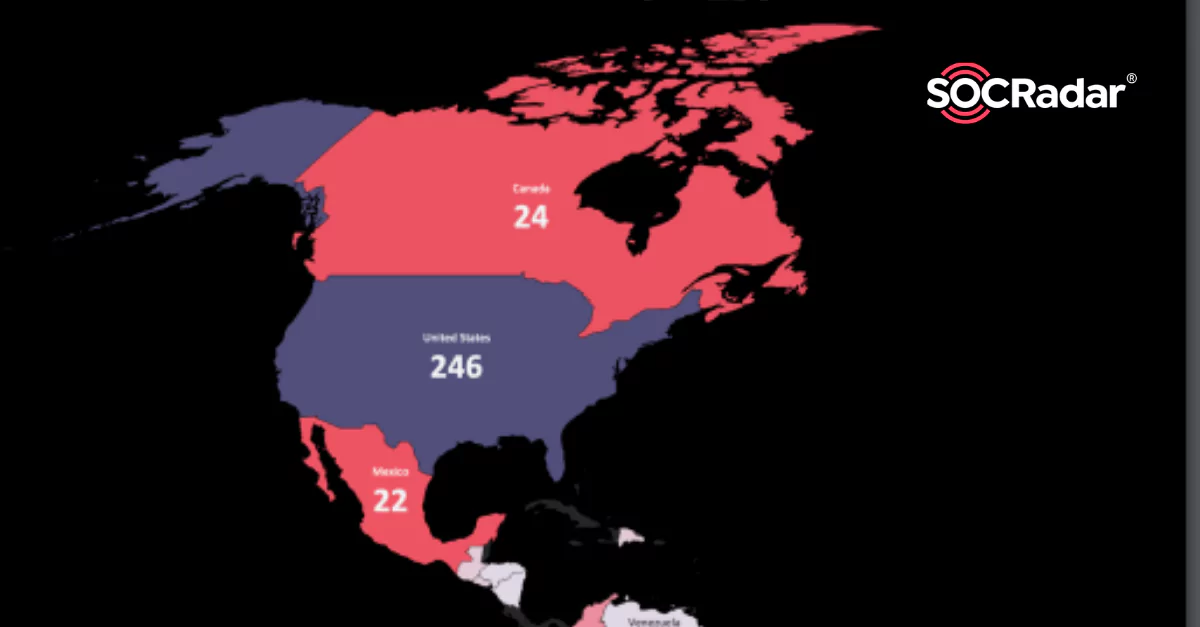
Top Ransomware Group is LockBit 2.0 in the Americas
Top Ransomware Group is LockBit 2.0 in the Americas The Americas Regional DeepWeb Report, which emerged with the research of the SOCRadar analyst team, is now avaible for the first time. Dark we...
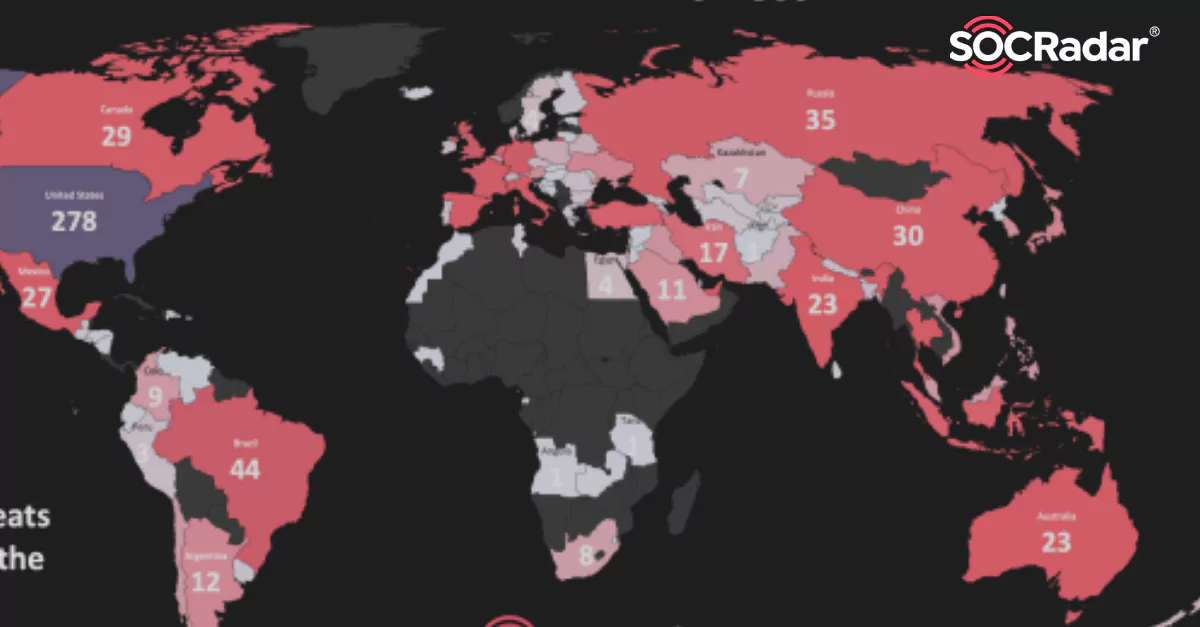
“Data Sales” is in the Lead at the Global Threat Landscape
“Data Sales” is in the Lead at the Global Threat Landscape The Global Regional DeepWeb Report, which emerged with the research of the SOCRadar analyst team, is now available for the first time. ...

The Most Dangerous of Their Kind Remote Code Execution (RCE) Attacks
The Most Dangerous of Their Kind Remote Code Execution (RCE) Attacks Remote Code Execution (RCE) is a class of software vulnerabilities. An RCE vulnerability allows a malicious actor to execute code o...

How to Detect Your Network is Used by Botnets Without Touching Your Sy...
How to Detect Your Network is Used by Botnets Without Touching Your Systems? Malicious bots called “bad bots” not only evolve continually, but are very specific to certain applications, su...

Best OSINT Resources to Follow
Best OSINT Resources to Follow One of the benefits of the cyber security is its openness to sharing. There is a good sense of community in the industry with people freely creating and sharing tools. I...
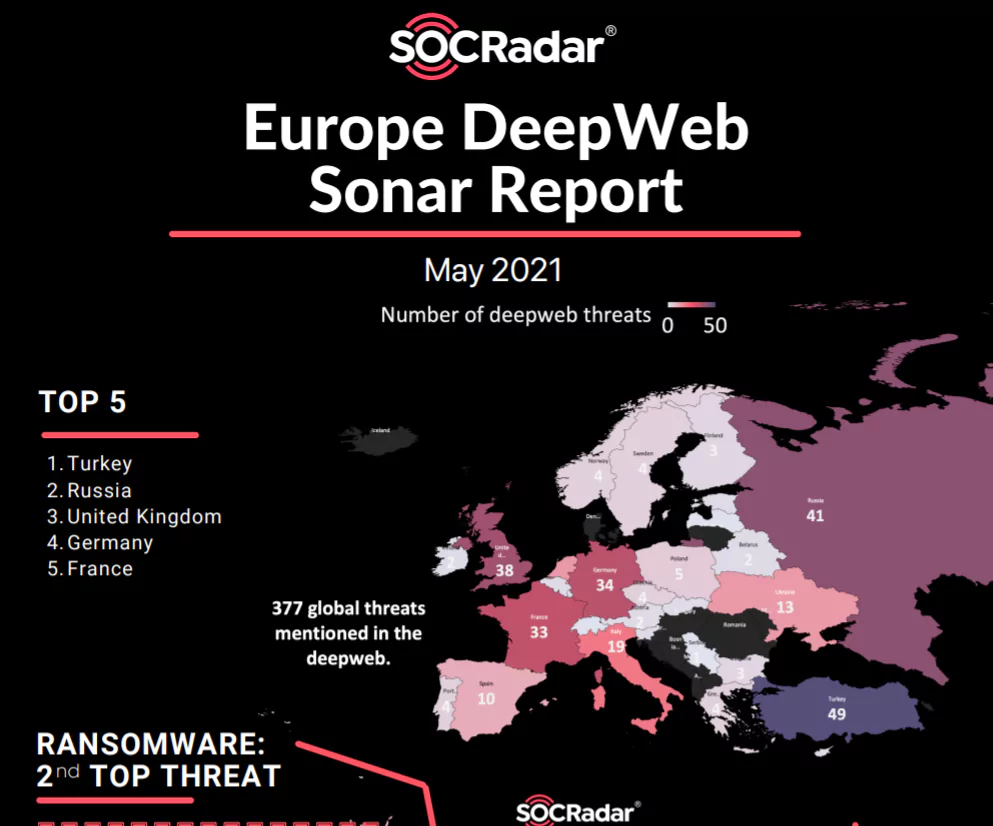
Comparing MEA (Middle East and Africa) and Europe against the Dark Web...
Comparing MEA (Middle East and Africa) and Europe against the Dark Web Threats Companies that wish to safeguard customers and employees typically invest in Dark Web monitoring solutions to warn them i...
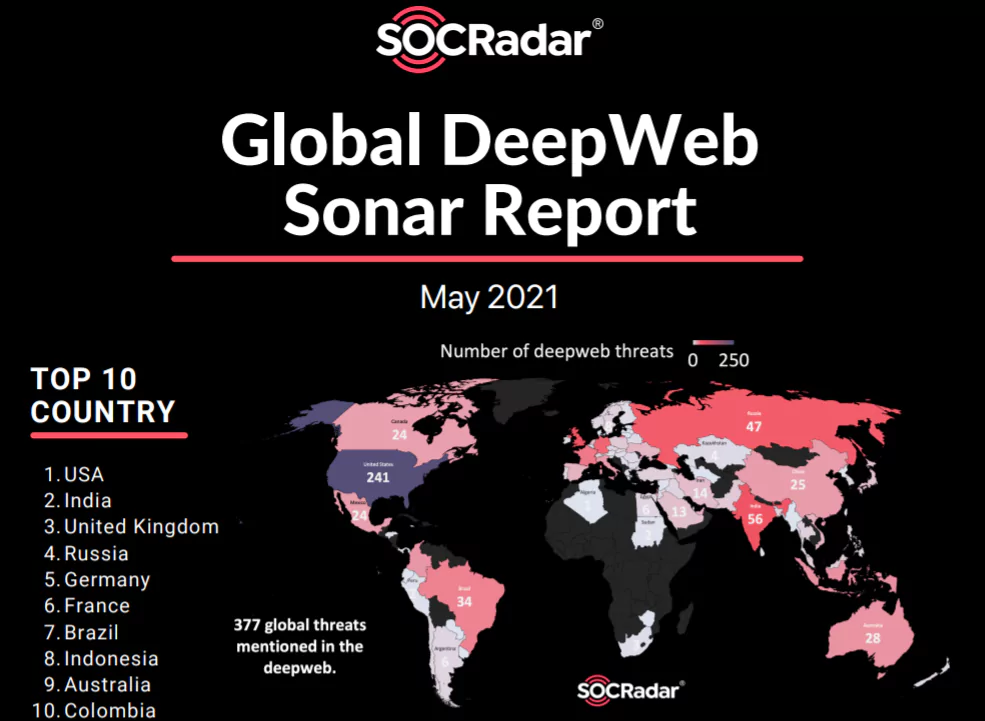
Did You Try SOCRadar Global DeepWeb Sonar Report Yet?
Did You Try SOCRadar Global DeepWeb Sonar Report Yet? Unidentified attackers have apparently unlimited resources, pressuring security authorities to regularly evaluate all aspects of their security st...

Best Practices for External Attack Surface Management (ASM) with Use-C...
Best Practices for External Attack Surface Management (ASM) with Use-Cases Gartner has predicted that by 2021, one-third of successful attacks on the enterprise will be through shadow IT resources and...

Shadow IT Explained: What Are the Risks and How Can You Mitigate Them?
Shadow IT Explained: What Are the Risks and How Can You Mitigate Them? A recent study from EMC suggests that data loss and downtime result in losses of $ 1.7 trillion each year.[1] Since shadow IT is ...

Create More Effective SOC With the Mitre ATT&CK Framework
Create More Effective SOC With the Mitre ATT&CK Framework The ATT&CK framework is a powerful tool to improve cyber defence and to create a more effective SOC. According to the SANS report, the...

How Hackers Find Your CEO’s Password and Abuse It
How Hackers Find Your CEO’s Password and Abuse It Poor password habits are found everywhere, even in big companies despite the password policies required. The credential leak is one of the most common...
Top Vulnerabilities Exploited in VPNs in 2020
Top Vulnerabilities Exploited in VPNs in 2020 In several VPN products worldwide, APTs target vulnerabilities. This is an ongoing activity directed at multinational organizations. Including government,...

How To Learn Which 3rd Party Libraries Your Website Is Using?
How To Learn Which 3rd Party Libraries Your Website Is Using? Websites are the most critical assets and most important components of your business. They are a linking bridge between your products and ...

How To Find Domain Ownership in the GDPR Era
How To Find Domain Ownership in the GDPR Era ...

Top Threat Intelligence Use Cases for the E-commerce Industry-II
Top Threat Intelligence Use Cases for the E-commerce Industry-II Prevention of the landscape is no longer enough in today’s cybersecurity. All have never faced such high and concrete threats from adva...

Top Threat Intelligence Use Cases for the E-Commerce Industry-I
Top Threat Intelligence Use Cases for the E-Commerce Industry-I The prevention of the landscape is no longer enough in today’s cybersecurity. All have never faced such high and concrete threats from a...

































