CISA Launches “Secure by Design Alert” Series: Securing Web Management Interfaces
The Cybersecurity and Infrastructure Security Agency (CISA) has just introduced the Secure by Design Alert series, a proactive step to highlight instances where vulnerabilities or intrusion campaigns could have been prevented by the vendors, through secure design principles.
CISA recognizes that vendors make software and security choices as part of broader business decisions, and clarifies that the intent is not to assign blame to vendors. Rather than blaming, the series aims to shed light on the real harm resulting from what CISA terms “anti-security” decisions.

Unlike traditional discussions post-cyber intrusions, which often focus on victim actions, this series redirects attention to how vendor decisions impact harm reduction on a global scale. This shift in focus encourages a more proactive exploration of cybersecurity practices.
Web Management Interfaces: A Vulnerability Landscape
CISA highlights how web management interfaces remain a fertile ground for malicious cyber actors seeking and exploiting vulnerabilities. Notably, CISA notes that just this year, it has listed vulnerabilities affecting major web management interfaces under its Known Exploited Vulnerabilities (KEV) Catalog:
- Cisco IOS XE Zero-Day, Privilege Escalation Vulnerability (CVE-2023-20198)
- Zyxel EMG2926 Command Injection Vulnerability (CVE-2017-6884)
- Ivanti Sentry (MobileIron) Zero-Day, Authentication Bypass Vulnerability (CVE-2023-38035)
- D-Link DIR-859 OS Command Injection Vulnerability (CVE-2019-17621)
Despite the persistent threat, software manufacturers often question why customers fail to secure their products adequately. In response to this, CISA reminds that the essence of “Secure by Design” lies in how software manufacturers construct their products to reasonably safeguard against threat actors.
By integrating risk mitigation into the very fabric of their products, manufacturers can alleviate the cybersecurity burden on customers, fostering a more resilient defense against potential threats.
Two Key Principles of the Secure by Design Concept
With the release of the Secure by Design Alert series, CISA directs attention to the persistent threat of malicious cyber activity against web management interfaces.
CISA, drawing insights from continuous malicious cyber activities against these digital assets, advocates for a proactive approach among software manufacturers. By embracing and implementing two fundamental principles, manufacturers can fortify their products against potential threats, avert the threat at a global scale, and contribute to a more secure digital landscape.
1. Taking the Ownership of Customers’ Security Outcomes
This principle prioritizes strategic investments in key security areas like application hardening, application features, and default settings. To align with this core principle of Secure by Design, manufacturers are advised to scrutinize default settings, embedding established best practices directly into their products rather than relying on customers to do so.
Practical examples include disabling the product’s web interface by default, providing a “loosening guide” detailing associated risks, configuring the product to avoid vulnerable states (such as direct exposure to the public internet), and introducing acknowledgement pop-ups for risky configurations.
Furthermore, CISA advocates for manufacturers to conduct thorough field tests to comprehend how customers deploy products in diverse environments, bridging the gap between developer expectations and real-world product usage. These field tests serve as a valuable tool in identifying ways to construct products that align with secure customer practices.
Additionally, consistent authentication enforcement throughout the product, especially on critical interfaces like administrator portals, remains imperative to enhance overall security. By embracing and embodying the “take ownership” principle, software manufacturers, as recommended by CISA, can actively contribute to improved customer security outcomes.
2. Radical Transparency and Accountability
In pursuit of enhanced cybersecurity, software manufacturers are urged to prioritize transparency when divulging product vulnerabilities. Central to this effort is the meticulous tracking of vulnerability root causes and ensuring that CVE entries are comprehensive, incorporating the appropriate CWE field to denote the coding error class responsible for the vulnerability. This not only aids customers in comprehending and assessing risks but also fosters collective learning across the industry as other manufacturers glean insights from resolved mistakes.
The commitment to radical transparency extends to the identification and elimination of recurring vulnerability patterns in products. Navigating the intricate path of constructing products that embrace secure design principles proves to be a complex and time-intensive endeavor. However, by pinpointing the recurring pitfalls in software design and configuration that often result in compromises, we can strategically channel our efforts into areas requiring improvement.
Conclusion
In summary, the launch of Secure by Design Alert series acts as a catalyst, prompting software manufacturers to ponder their software development lifecycles and how they influence customer security outcomes. Embracing these principles not only strengthens individual products but also enriches the overall resilience of the software industry, fostering an atmosphere of ongoing enhancement and elevated security standards.
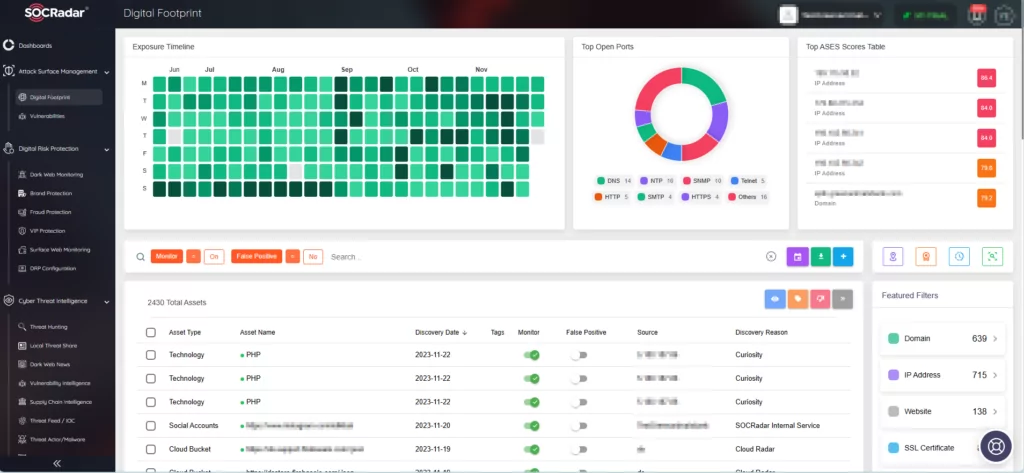
Discover Vulnerable Assets and Manage Your Digital Footprint with SOCRadar’s Attack Surface Management
SOCRadar’s Attack Surface Management (ASM) module ensures precision, promptly identifying and alerting you to potential threats cross-referenced with your digital assets. By continuously monitoring your digital perimeter from an external standpoint, SOCRadar identifies critical vulnerabilities before exploitation risks arise.
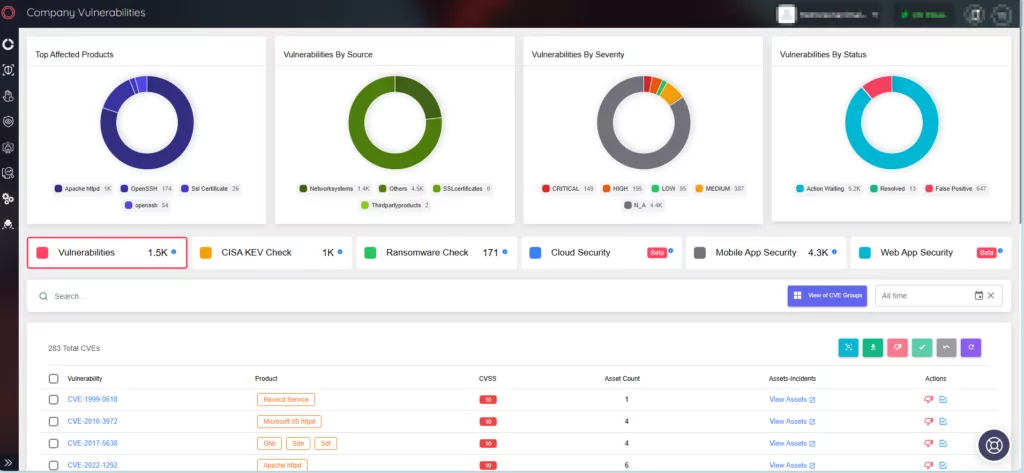
With the ability to track and notify of threats and vulnerabilities, including zero-day exploits, illuminate forgotten and unattended assets, maintain an auto-updated asset inventory, and deliver machine-speed alerting, SOCRadar empowers proactive action against emerging threats.