Dark Web Profile: Babuk/Babuk2
Babuk, originally emerging in 2020, became infamous for its ransomware attacks on large organizations and government agencies. After internal conflicts led to the leak of its source code, the group disbanded, giving rise to Babuk V2, which shifted to data theft and extortion.
In 2025, a new iteration, Babuk2, resurfaced under the alias Bjorka, a notorious hacker known for targeting the Indonesian government. While claiming massive data breaches and extortion, Babuk2’s true capabilities are unclear, with many of its leaks seeming to be recycled from previous incidents. Despite doubts, Babuk2 continues to capitalize on fear and reputation, pushing its ransomware operation for profit.
Who is Babuk/Babuk2
Babuk, Babyk, Babuk V2, Babuk2, Vasta Locker and more, there have been many different names for the same-old(?) ransomware operation from 2020. However, researchers aren’t to blame for the naming convention this time.
Here is the logic behind its naming, in early 2020 a novel yet amateur ransomware operation named Babuk has surfaced, in early 2021 the group gained fame by targeting many corporate networks, thus the same year its code leaked by one of its developers probably due to internal fighting.
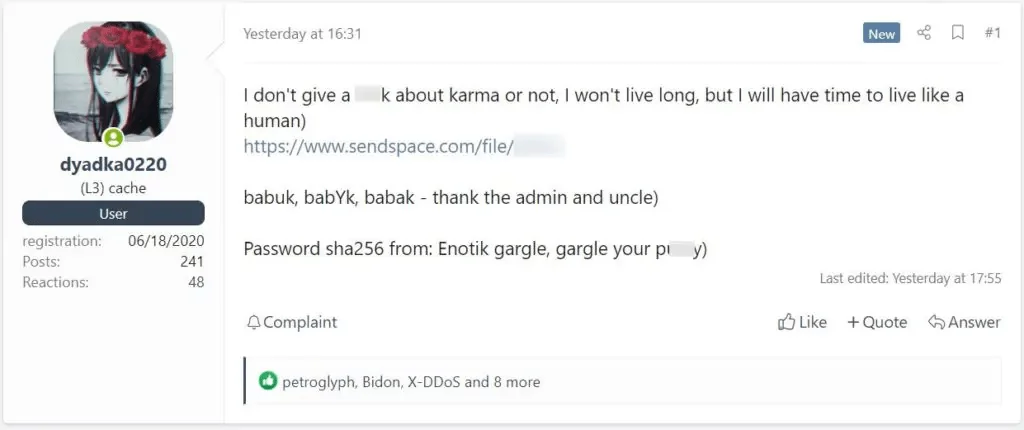
The leak of the source code posted in a Russian hacker forum by allegedly an original developer of the Babuk strain
The Babuk ransomware group was first identified as active in January 2021, but investigations by U.S. government agencies revealed that they had been active since 2020. They primarily targeted high-profile entities, including large corporations and government agencies across Europe and North America. These targets spanned a variety of industries, such as transportation, government, healthcare, and industrial equipment suppliers, among others. Babuk operated under the Ransomware as a Service (RaaS) model, offering its malware to affiliates who carried out attacks.
The group employed a dual-threat strategy, combining file encryption and data theft to maximize pressure on victims. Babuk was known to favor high-value targets with substantial financial capabilities, increasing the likelihood of ransom payments. Its malware was particularly effective against Windows, ESXi, and NAS devices, enabling the group to exploit vulnerabilities across a range of systems.
Babuk’s Demise
In April 2021, the Babuk ransomware group targeted Washington D.C.’s Metropolitan Police Department (MPD), threatening to leak sensitive data stolen from its systems unless a $4 million ransom was paid. The attackers claimed to have exfiltrated 250 GB of data and warned they would expose information about police informants to criminal organizations. They also threatened continued attacks on U.S. government entities, including the FBI and the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA).
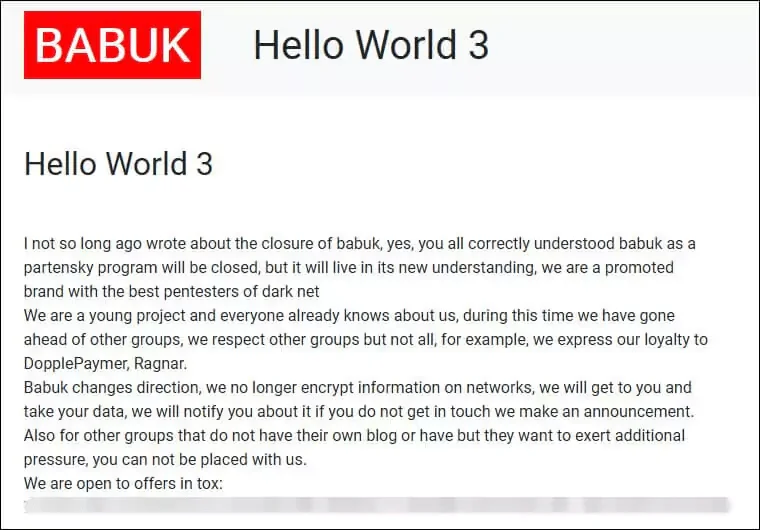
Evidently, Babuk didn’t have a strong internal structure, and after the MPD attack, growing pressure from U.S. authorities and internal conflicts made things worse. The group soon announced it was shutting down. But just a month later, some members split off and brought it back under the name Babuk V2, changing their approach from Ransomware-as-a-Service (RaaS) to extortion through data theft.
It’s known that the other members of the group transitioned to managing “RAMP” (Russian Anonymous Marketplace). The forum was launched on the same domain that was previously used for the Babuk ransomware data leak site and later the Payload.bin data leak site.
Lastly, in early 2023, a Russian national suspected of being the leader of Babuk and was charged with ransomware attacks on critical infrastructure, with one of the charges being the deployment of Babuk alongside other strains, final verdict came this year.
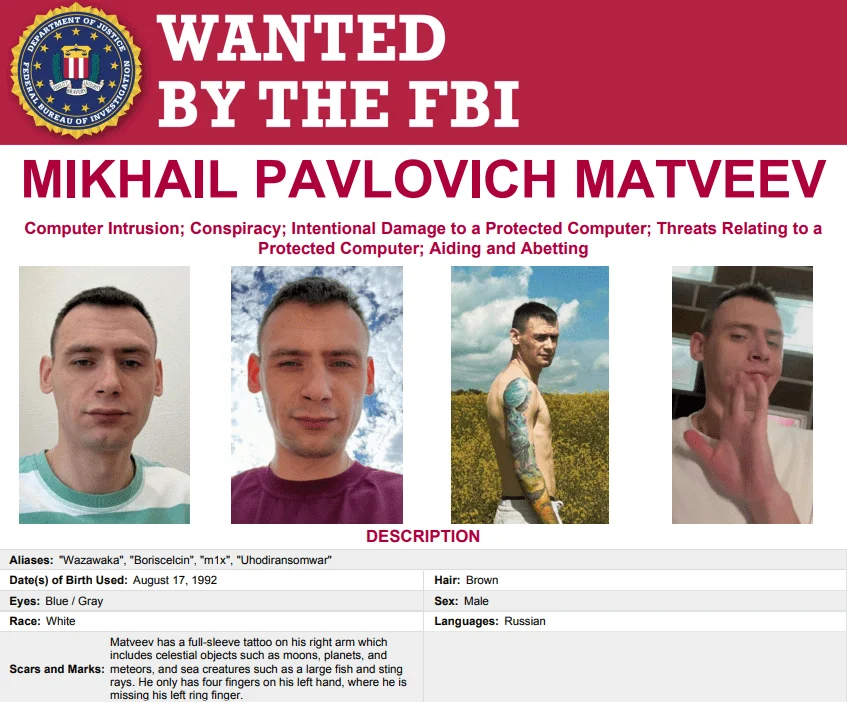
In 2025, Mikhail Matveev, former leader of the Babuk ransomware group before its shutdown, was sentenced after being linked to several notorious ransomware groups, including Lockbit, Conti, HIVE, and BlackMatter. Known for his involvement in high-profile attacks, Matveev targeted police departments and critical infrastructure both in the United States and its European allies.
Mikhail Pavlovich Matveev, wanted poster by the FBI
Matveev, also known as Wazawaka and featured on the FBI’s Most Wanted list, received a sentence of 18 months of “limited freedom” under Russian law, which is similar to house arrest in the U.S. His restrictions include a curfew, travel limitations, required check-ins with a probation officer, and bans from places like bars, nightclubs, and protests.
Mutation Effect
This brief ransomware operation wasn’t the only cause of worry—the leak of Babuk’s source code may have led to the demise of one ransomware operation, but it paved the way for many others.
The strain was adopted by numerous cybercriminals, likely making the ransomware landscape more dangerous than ever at the time. This phenomenon has been referred to as the “mutation effect.” As a result, the name Babuk continued to surface repeatedly over the years.
The leak led to what’s called the mutation effect. This means cybercriminals were able to take the original code, change it, and create their own versions of ransomware. As a result, many new strains appeared, each with different features and tricks.
These groups didn’t just make small changes—they altered key parts like encryption, evasion methods, and attack strategies. In some instances, these tweaks made the ransomware stronger and harder to detect, creating serious challenges for security teams.
Who is Babuk2?
A group now using the Babuk name has been trying to reestablish itself since early this year. They’ve claimed to steal massive amounts of data, up to 100 terabytes, from each company and threatened to release it if ransoms aren’t paid. According to the group, some of the data has already been sold, and they suggest that leaks could destroy companies’ reputations and lead to bankruptcy.
However, there’s growing doubt around these claims. Many of the victims Babuk says it breached were previously targeted in other high-profile ransomware campaigns, making it unclear whether Babuk was truly involved or simply taking credit. This kind of bluff is common in the ransomware scene, where groups often exaggerate their impact to appear more threatening and pressure victims into paying.
Adding to the confusion, Babuk recently announced a new affiliate program called Babuk 2.0 or Babuk-Bjorka inviting others to use their tools in exchange for a share of ransom profits. Despite these announcements and claims of recent attacks, there seems to be no concrete evidence of new activity. Most of the data they’re leaking appears to be recycled from past incidents, casting further doubt on the group’s capabilities.
In summary, with high confidence, Babuk2 is not a direct continuation of the original Babuk ransomware group. It is an independent hacker or a group named Bjorka and its affiliates that uses the Babuk name and methods.
The story’s final twist is Bjorka’s return with Babuk2
Who is Bjorka?
Bjorka is a well-known but still anonymous cyber threat actor, infamous for targeting the Indonesian government and leaking sensitive data. After going quiet in 2023, Bjorka resurfaced in early 2025, now pushing a ransomware project called Babuk2 as we mentioned.
While early theories suggested ideological motives, recent actions such as data sales, hospital leaks, and suspicious giveaways indicate that profit is the main driver for Bjorka. The identity of the actor, whether individual or group, remains unclear, but collaborations with others, such as Skywave, seem evident.
Since February 2025, Skywave has controlled several Telegram channels, posting daily updates about victims. Babuk 2.0 content was often shared by Bjorka on their channel, suggesting a possible connection due to overlapping victims reported as a Bjorka victim in 2023 and a Babuk2 victim in 2025.
Further signal of collaboration appears in Babuk2’s data leak site (DLS) ‘Contact Us’ section, where the logos of Skywave, Bjorka, and another affiliate, GD Locker Sec, were displayed together.
The ‘Contact US’ tab on the DLS of Babuk, showing the logos of Bjorka and Skywave (rapid7)
With Babuk2, Bjorka turning into a ransomware operation, anything profitable is fair game. Bjorka now seems intent on staying in the spotlight, using their past reputation to fuel new money-driven “attacks.”
What are Babuk/Babuk2’s Tactics?
The Babuk2 operation seems to be mainly a scam. However, if we were to attribute more to it for precaution, we could say that Babuk/Babuk2 focuses less on launching new, advanced ransomware attacks and more on using the reputation of a well-known brand to create a false narrative. Their tactics mainly involve rebranding, recycling data, and manipulating the market.
Rebranding and Impersonation
Instead of being a continuation of the original Babuk ransomware group, Babuk2 uses the Babuk name and branding to appear more credible. By copying the design and interface of the original group and LockBit, including victim post layouts, the operators create the illusion of continuity while relying on tactics that are mostly copied. Their DLS shows a clear effort to rebrand, aiming to make victims and partners feel familiar with them.
Analysis of the victim lists reveals that many organizations listed as “new” victims were in fact already targeted by other ransomware groups. In some cases, the exact same texts and typos from previous leaks! The trend is further reinforced by the posting of nearly identical “ransom notes” and recycled data fragments, making it evident that the group is banking on recycled content to back up its claims.
Social Engineering
Beyond the non-existing technical aspects, Babuk/Babuk2 leverages social engineering to lure victims. By emphasizing high-profile names and mimicking the language and style of established ransomware operations, they create a sense of urgency and credibility, like many other ransomware groups. Their “extortion demands” are built on false claims that are designed to pressure organizations into paying ransoms or investing in defensive measures—even when no fresh breach has taken place. Tiered ransom pricing strategies further indicate a calculated approach to extracting maximum profit while maintaining a semblance of legitimacy.
Code Reuse and Misleading Attribution
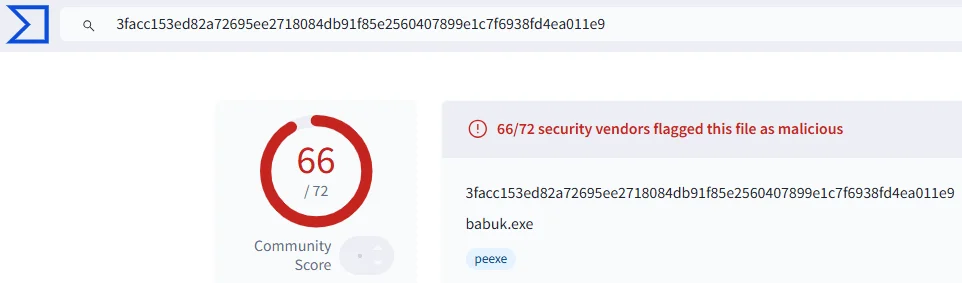
An example of their rebranding tactics is the case of a sample named babuk.exe, showcased by rapid7. Initially shared on the Babuk 2.0 Ransomware Affiliates Telegram channel, detailed analysis revealed that the sample is in fact not original but is based on LockBit 3.0 (also known as LockBit Black).
LockBit Black sample “3facc153ed82a72695ee2718084db91f85e2560407899e1c7f6938fd4ea011e9” in VirusTotal
Despite being packaged under the Babuk name, its underlying code, encryption methods, and routines (such as API harvesting and ransom note generation) are identical to those used in LockBit 3.0.
Some say this deliberate misattribution serves to obscure the true source of the ransomware while exploiting the Babuk brand’s notoriety.
Since Babuk’s original code was seen as amateurish, using LockBit’s leaked builder seems like a logical choice.
However, the confusion and deception surrounding the group should indicate that their operations are based on lies, not only targeting victims but also misleading their affiliates and others involved.
Overall Operational Strategy
In conclusion, Babuk2’s operations appear to be driven by deception rather than innovation. Instead of creating new, sophisticated ransomware, the group relies on rebranding the Babuk name and leveraging the reputation of established ransomware brands like LockBit to create a false sense of legitimacy.
So far, their tactics focus on recycling data, misattributing ransomware code, and using social engineering to manipulate both victims and affiliates. While the use of LockBit’s builder may be a pragmatic choice given the original Babuk’s shortcomings, the overall strategy centers on confusion and misdirection. Ultimately, Babuk2’s operations reveal a calculated attempt to exploit the notoriety of the Babuk name and manipulate the ransomware landscape for profit, with little concern for innovation or technical advancement.
What are Babuk/Babuk2’s Targets?
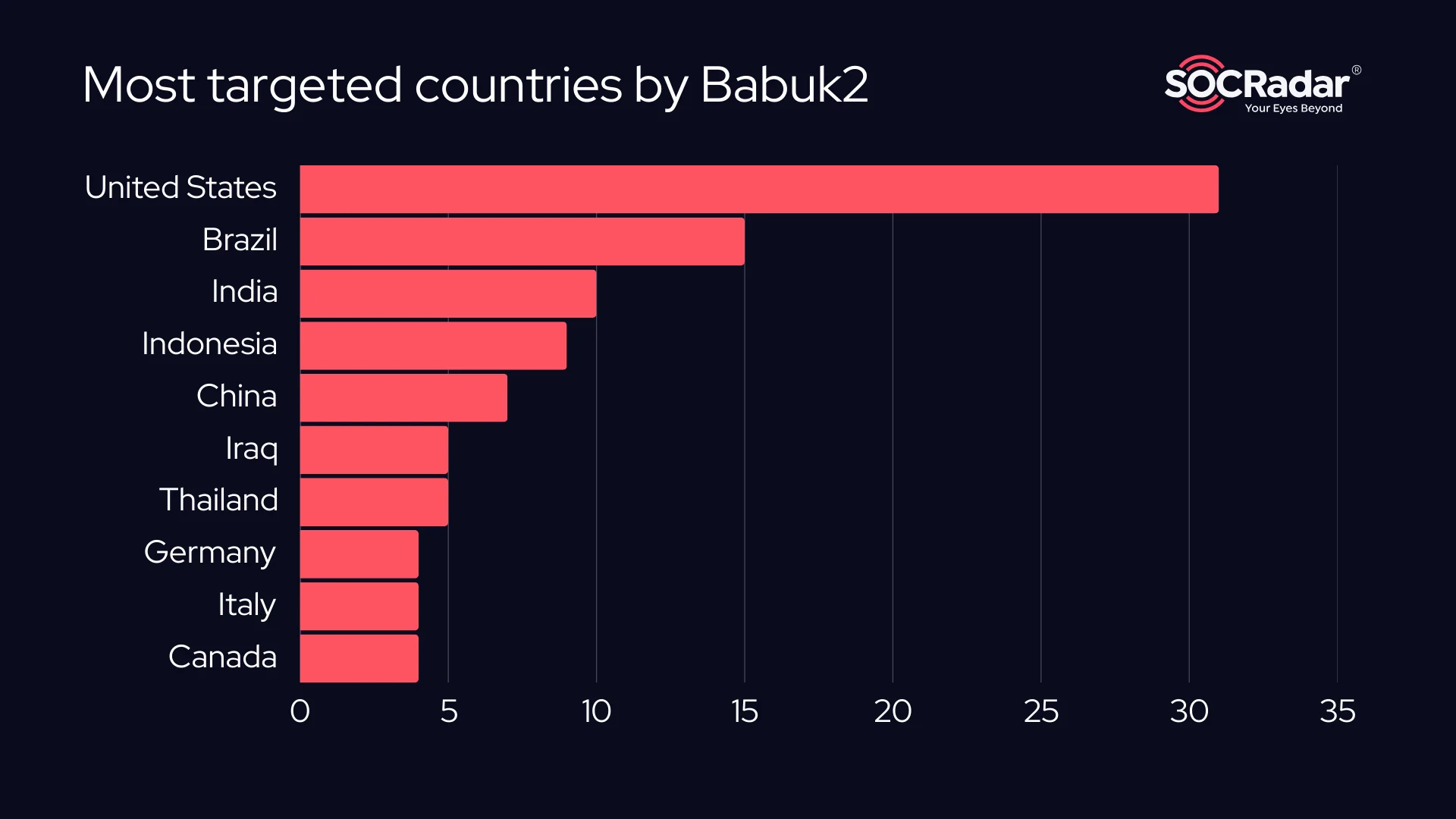
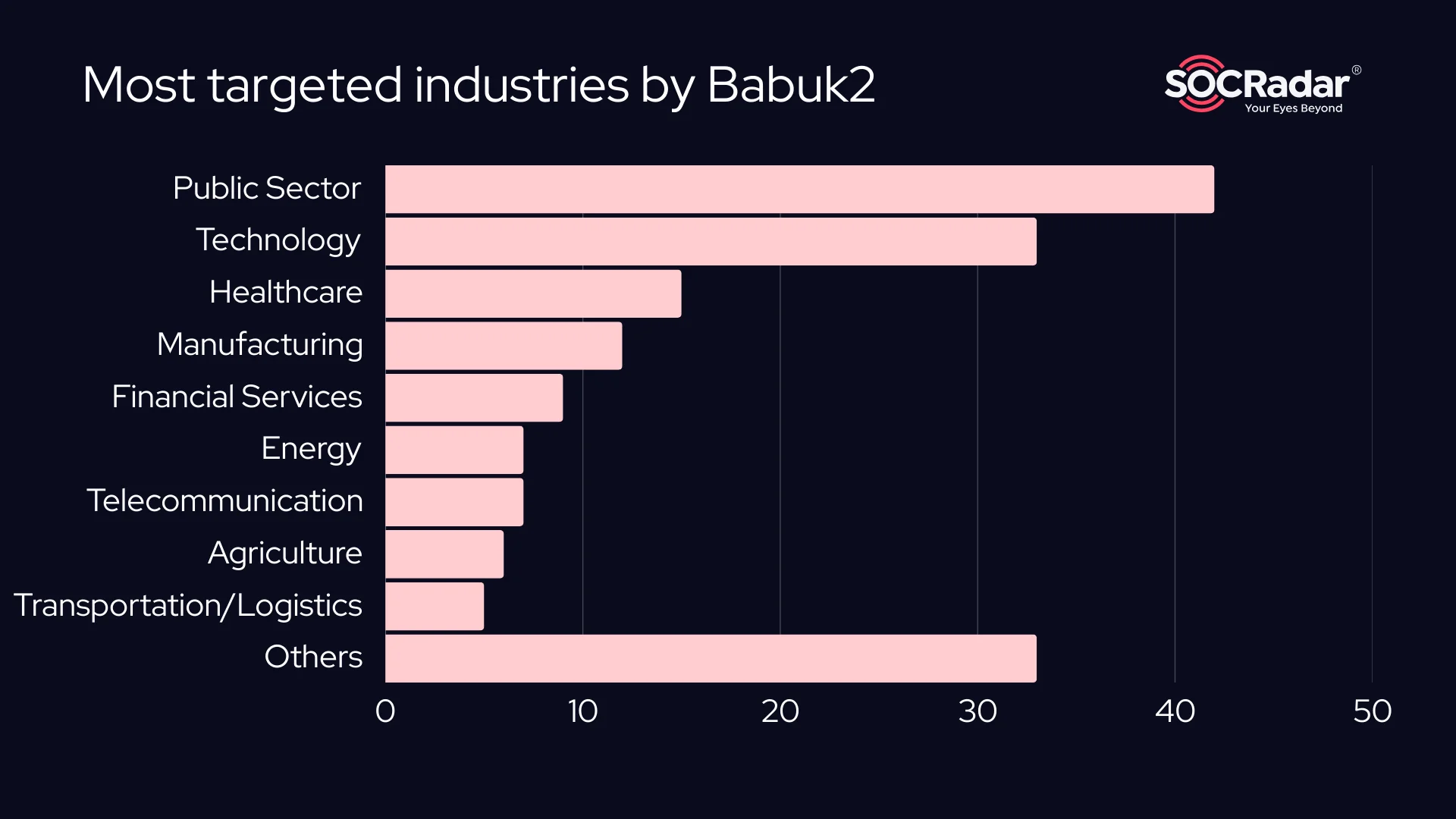
Babuk2’s recent alleged ransomware campaign reveals a diverse targeting pattern across countries and sectors. The United States is by far the most heavily targeted nation, with 31 separate incidents, followed by Brazil, India, and Indonesia. The breadth of victim geography—spanning North and South America, Asia, and parts of Europe—suggests that Babuk2’s operations are either highly distributed or make use of widely available vulnerabilities across different infrastructures.
From an industry perspective, public institutions bore the brunt of the attacks, with 42 victims from national ministries, defense departments, municipal governments, and law enforcement agencies. This indicates a calculated interest in institutions with operationally critical data and potential geopolitical leverage. Technology firms come next, with 33 victims—many of which offer digital services, manage cloud infrastructure, or are involved in R&D. The presence of high-value intellectual property or exploitable access channels likely plays a role here.
Healthcare, another commonly targeted area, had 15 confirmed incidents. These attacks can be especially disruptive given the life-and-death stakes of healthcare operations and the sensitivity of patient data.
Manufacturing and energy follow close behind, with attacks likely focused on industrial espionage or operational sabotage. Financial services, while fewer in number, remain valuable targets due to direct access to funds and the potential for high payouts. Meanwhile, telecommunication, agriculture, and logistics round out the top 10, reflecting the group’s broad interest in systemic and economic infrastructure.
Overall, Babuk2 appears to operate with both opportunistic and strategic motives. While there’s clear focus on governments and critical infrastructure, the group also casts a wide net across industries that hold data, money, or influence.
How to Defend Against Babuk2 or Similar Threats?
- Strengthen Endpoint Security
Deploy advanced endpoint protection with behavioral detection, machine learning, and heuristic analysis. Since Babuk2 ransomware is based on a leaked builder, its variants may share core features. This makes it possible to detect suspicious patterns even if the strain is slightly modified.
- Keep Systems Updated
Regularly patch and update operating systems, software, and security tools. Babuk2 and similar ransomware campaigns often exploit unpatched vulnerabilities for initial access, making outdated software a major risk.
SOCRadar Vulnerability Intelligence helps identify and prioritize critical vulnerabilities before attackers can exploit them
- Network Segmentation
Isolate critical systems and apply strict internal access rules. Segmentation helps contain infections within specific parts of the network and prevents Babuk2 from spreading laterally.
- Regular Backups and Recovery Plans
Back up essential data routinely and store backups offline or in air-gapped environments. Babuk2 encrypts files using strong cryptography, and without the decryption key, recovery is nearly impossible. Reliable backups are your best fallback.
- Raise Employee Awareness
Train staff to spot phishing attempts, suspicious links, and email attachments. Since social engineering is a common entry method, awareness significantly reduces the chances of successful intrusion.
- Email and Web Filtering
Use filtering tools to block malicious emails and web content before they reach users. Suspicious files like .eml attachments can be analyzed using SOCRadar Malware Analysis to verify threats before impact.
- Limit Access Rights
Apply the principle of least privilege. Ensure users only have access to the systems and data necessary for their roles. Regularly audit permissions to reduce the blast radius of a compromised account.
- Monitor Threat Intelligence
Stay informed on the latest tactics and techniques used by ransomware groups. Use continuous monitoring to catch early signs of an attack. Threat actor’s methods are evolving—real-time visibility is essential.
- Prepare an Incident Response Plan
Have a clear, tested incident response plan specifically covering ransomware scenarios. Drills and simulations will help your team act quickly if a ransomware infiltrates your systems.
How Can SOCRadar Help?
Understanding the methods and motives behind ransomware operations like Babuk2 is essential for proactive defense. SOCRadar’s Threat Actor Intelligence gives you visibility into emerging and evolving threat groups, including their known tactics, targets, and communication channels. By tracking ransomware actors tied to leaked builders or revived operations, you can stay ahead of shifting risks.
Through the Ransomware Intelligence module, organizations can access detailed profiles, Indicators of Compromise (IoCs), and YARA rules for detecting LockBit, Babuk and similar strains. This intelligence-driven approach enables faster detection, more effective response, and long-term resilience against ransomware campaigns.
With SOCRadar, you can turn insight into action—detecting, contextualizing, and mitigating ransomware threats before they cause damage.
Conclusion
It’s hard not to view Babuk2 as more theater than threat—a smoke-and-mirrors act banking on nostalgia for chaos. Rather than evolving the ransomware game, they’ve chosen to weaponize the remnants of past operations, mixing recycled leaks with borrowed code and a borrowed name. In some ways, it’s less about hacking systems and more about hacking perception.
For now, Babuk2 is playing the role of a ransomware actor without writing much of its own script—just repackaging old scenes in a new costume and hoping the audience doesn’t notice. Whether this act can hold attention or fizzle out like its predecessors remains to be seen. It’s also important to consider that these tactics might just be a temporary form of advertisement; the noise they create could be a placeholder, hinting at possible shifts in strategy as circumstances or ambitions change.