
Dark Web Profile: Moses Staff
Over the past months, the SOCRadar Analyst Team has been tracking the Iranian hacker group known as Moses Staff. The group was first spotted in October 2021 and claimed its motivation was to harm Israeli companies by leaking sensitive, stolen data.
Aside from Israel, which appears to be the group’s primary target, Moses Staff was observed targeting organizations in other countries, including Italy, India, Germany, Chile, Turkey, UAE, and the US. The group targets a variety of industries, among them government, finance, travel, energy, manufacturing, and the utility industry.
Which Tools is Moses Staff Using?
Following recently published research detailing the group’s TTPs, including their main tools “PyDcrypt” and “DCSrv,” the Cybereason Nocturnus team discovered a previously unknown Remote Access Trojan (RAT) in the Moses Staff arsenal dubbed StrifeWater.
The StrifeWater RAT appears to be used in the initial stage of the attack, and this stealthy RAT can remove itself from the system to cover the Iranian group’s tracks. The RAT possesses other capabilities, such as command execution and screen capturing, as well as the ability to download additional extensions.

Politically Motivated Attacks
Once the group infiltrates an organization and steals sensitive data, they deploy ransomware to encrypt the infected machines. Unlike financially motivated cybercrime ransomware groups who encrypt the files as leverage for the ransom payment, the encryption of the files in the Moses Staff attacks serves two purposes: inflicting damages by disrupting critical business operations and covering the attackers’ tracks.
The end goal for Moses Staff appears to be more politically motivated rather than financially. Analysis of the group’s conduct and operations suggests that Moses Staff leverages cyber espionage and sabotage to advance Iran’s geopolitical goals by inflicting damage and spreading fear. (Related Iranian APT research: PowerLess Trojan: Iranian APT Phosphorus Adds New PowerShell Backdoor for Espionage).
Moses Staff’s Usual Attack Scenario
- Novel Remote Access Trojan: A newly undocumented RAT dubbed StrifeWater was assessed to be part of the arsenal used by Iranian APT Moses Staff. The RAT is evaluated to be used explicitly in the initial phase of infection and is later replaced with other tools.
- Various Functionality: The StrifeWater RAT has multiple capabilities, among them: listing system files, executing system commands, taking screen captures, creating persistence, and downloading updates and auxiliary modules.
- Under the Radar: The StrifeWater RAT appears to be removed from the infected environment in time for the deployment of the ransomware. This is likely the reason the RAT was not detected before.
- State-Sponsored Ransomware: Moses Staff employs ransomware post-exfiltration, not for financial gain but to disrupt operations, obfuscate espionage activity, and inflict damage to systems to advance Iran’s geopolitical goals.
- Victims Across the Globe: The group’s list of victims includes multiple countries and regions, among them: Israel, Italy, India, Germany, Chile, Turkey, UAE, and the US.
Though StrifeWater managed to stay off the radar for some time, Cybereason researchers found that StrifeWater RAT was deployed under calc[.]exe. This came to be identified when the analysis of PyDCrypt malware was found to be used by Moses Staff.
PyDCrypt was written in PyInstaller, which dropped the payload DCSrv, a ransomware variant based on the tool DiskCryptor. Exciting findings included that the Moses group created a new sample of PyDCrypt separately for each targeted organization.
The hard-coded parameters in PyDCrypt included usernames, passwords, local domain addresses, and even a machine list. This concludes that PyDCrypt is deployed only after infiltrating the organization and gathering sufficient information to map the environment.
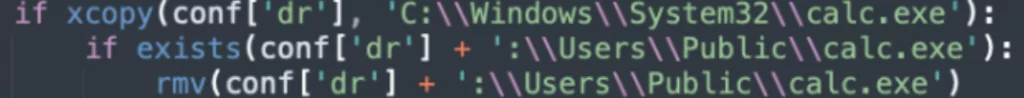
The group often used the “C:UsersPublic” folder for all the tool deployment. PyDCrypt was coded in such a way that it copies the original Windows Calculator binary (calc[.]exe) from the System32 folder to the tool deployment folder (C:UsersPubliccalc[.]exe) and then deletes it.
References:
- https://cybersecuritynews.com/apt-group-moses-staff-adds-new-tools-to-ransomware-operations/#:~:text=The%20Iranian%20hacker%20group%20Moses,%2C%20Chile%2C%20U.S%20and%20UAE
- https://www.cybereason.com/blog/research/strifewater-rat-iranian-apt-moses-staff-adds-new-trojan-to-ransomware-operations#:~:text=State%2DSponsored%20Ransomware%3A%20Moses%20Staff,to%20advance%20Iran’s%20geopolitical%20goals

































