
GuptiMiner Campaign: The Trojan Tango of Infiltrating Antivirus Updates for Deception
The GuptiMiner malware campaign is creating significant disruption in the cybersecurity landscape by exploiting a vulnerability in eScan antivirus software. Attackers are using this flaw to install cryptocurrency mining malware on devices, operating unbeknownst to the users.

An AI illustration of the Guptiminer Campaign
This blog post will explain the impact of the GuptiMiner campaign, describe the methods these attackers use, and offer strategies organizations can employ to protect themselves from similar threats.
The Anatomy of the GuptiMiner Campaign
The exploit in eScan antivirus software has significantly accelerated the spread of the GuptiMiner malware campaign. Capitalizing on the trust placed in antivirus updates, the attackers used this channel to distribute cryptocurrency mining malware across numerous devices and networks.
Understanding the reliance on antivirus updates for security, the GuptiMiner group cleverly mimicked these updates to push their malicious software, thereby infecting a wide array of devices. This strategy not only breached individual systems but also affected many corporate devices and networks.
The GuptiMiner malware notably employs tactics like installing backdoors and using XMRig, a popular open-source mining software, to mine cryptocurrency covertly. The flaw in the antivirus software allowed the attackers to evade detection, install these malicious tools, and operate undetected.
In essence, the vulnerability in the eScan antivirus was a significant factor in the success of the GuptiMiner campaign, highlighting the urgent need for robust cybersecurity measures to guard against such sophisticated threats and protect broader digital ecosystems.
Who is Behind the GuptiMiner Campaign?
The campaign has been linked to the North Korean APT group ‘Kimsuky’, known for targeting government and military organizations. This connection raises concerns about potential espionage activities associated with the campaign.
Visit Guptiminer’s Campaign page on the SOCRadar platform (SOCRadar Campaigns)
Covert Mining of Monero Cryptocurrency
XMRig, the chosen tool for covert mining, enables the GuptiMiner campaign to secretly mine XMR (Monero) cryptocurrency, while the eScan antivirus vulnerability proved to be a critical gateway for the GuptiMiner campaign, enabling threat actors to infiltrate systems and distribute their malicious payloads.
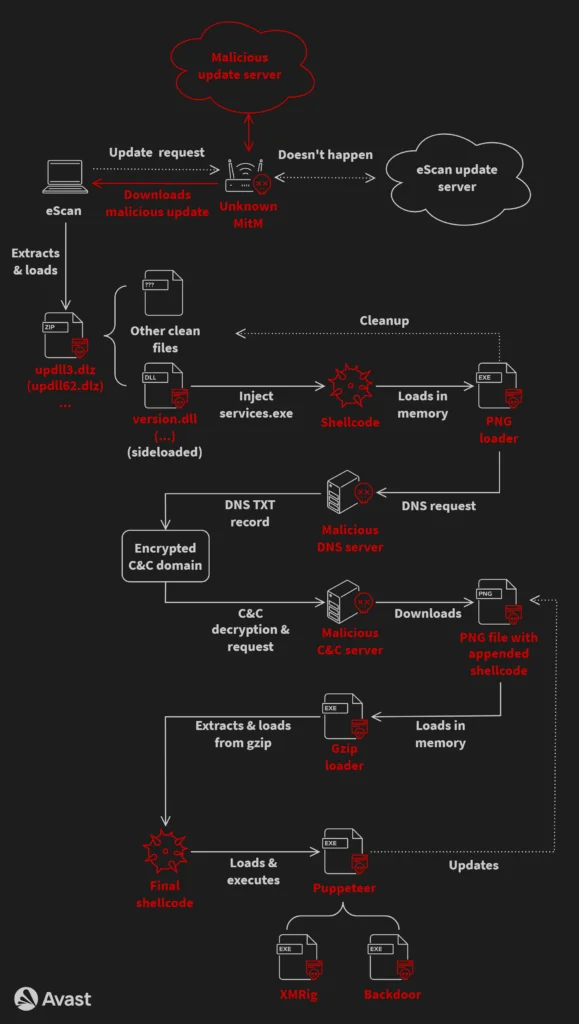
GuptiMiner’s infection chain
By learning about how this campaign works, organizations can be better prepared to stop future attacks. In the following sections, we will explore:
- The details of the GuptiMiner campaign itself.
- The specific eScan antivirus vulnerability that it took advantage of.
- The step-by-step process it uses to carry out its attacks.
- How it has changed over time to avoid being detected.
Understanding GuptiMiner’s Attack Chain
GuptiMiner is a sophisticated threat that uses various techniques to infiltrate and compromise systems. By understanding its attack chain, organizations can better protect themselves against this malware. Here are the key aspects of GuptiMiner’s attack chain:
- Initial infection: GuptiMiner enters the system through a vulnerable entry point, such as a malicious email attachment or a compromised website.
- Propagation within the network: Once inside, GuptiMiner spreads to other devices on the same network, increasing its reach and potential impact.
- Privilege escalation: GuptiMiner attempts to gain higher levels of access within the system, allowing it to carry out more malicious activities.
- Data exfiltration or cryptocurrency mining: Depending on its objectives, GuptiMiner either steals sensitive data from the infected system or uses its resources for cryptocurrency mining.
One critical element of GuptiMiner’s attack chain is its use of malicious DNS infrastructure. This involves registering domain names specifically for carrying out malicious activities. By analyzing these domain names, security professionals can uncover potential points of compromise and take proactive measures to mitigate the threat.
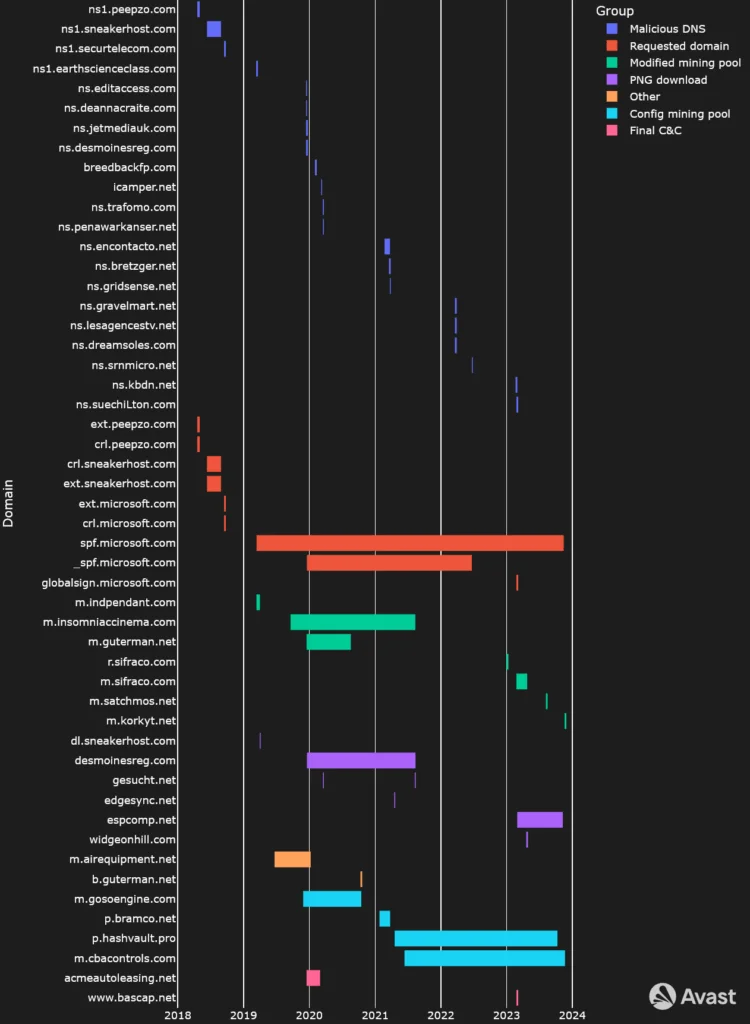
Timeline illustrating GuptiMiner’s usage of domains in time
Another key aspect of GuptiMiner’s attack chain is its utilization of malicious DLLs. These are files containing code and data that multiple programs can use simultaneously. GuptiMiner leverages these DLLs to:
- Compromise targeted systems
- Facilitate unauthorized access
- Maintain persistence on infected devices
The use of DLLs allows GuptiMiner to remain hidden and undetected for extended periods, making it harder for security solutions to identify and remove the malware.
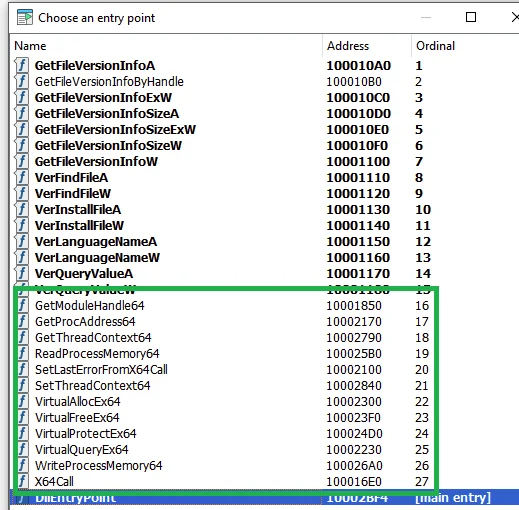
Additional exported functions
By understanding each stage and component of GuptiMiner’s attack chain, organizations can gain valuable insights into the tactics employed by threat actors and strengthen their cybersecurity defenses against such advanced threats. To further enhance their defenses, organizations can also leverage advanced security solutions like Microsoft Defender for Cloud, which provide additional layers of protection against sophisticated malware attacks.
GuptiMiner Campaign’s Evolution: Adapting to Stay Ahead
GuptiMiner, the notorious malware campaign that hijacked the eScan antivirus update mechanism, has shown a remarkable ability to adapt and evolve over time. By incorporating new techniques and strategies, GuptiMiner aims to evade detection and stay one step ahead of security researchers. In this section, we will explore some of the key evolutionary changes that GuptiMiner has undergone.
Compilation Timestamps as a Tool for Evasion:
One of the notable adaptations of GuptiMiner is the inclusion of compilation timestamps in its components. These timestamps serve as a means to deceive security researchers and make it more challenging to analyze the malware. By changing the compilation timestamps of its files, GuptiMiner can create the illusion of constant updates, making it difficult to track and identify its latest version.
Network Obfuscation Techniques:
To counteract detection and hinder analysis efforts, GuptiMiner has employed network obfuscation techniques. These techniques aim to conceal malicious communication between infected systems and command-and-control servers. By disguising network traffic patterns or using encryption methods, GuptiMiner can make it harder for security tools to identify and block its communication channels.
Mutexes for Persistence:
In its quest for persistence, GuptiMiner has utilized mutexes (mutual exclusion objects). Mutexes are synchronization primitives that ensure mutually exclusive access to shared resources. By implementing mutexes within its code, GuptiMiner can maintain persistence on infected systems even after reboots or system updates. This technique makes it more challenging for analysts to reverse engineer the malware and understand its inner workings.
Exploring .pdb Paths for Insights:
Another avenue worth exploring is examining .pdb paths (debugging symbols) associated with GuptiMiner. Debugging symbols contain valuable information about the software development process, including function names, source file paths, and compiler versions. Analyzing these symbols could provide insights into the campaign’s evolution and shed light on the development techniques employed by the threat actors.
Key Takeaways from the GuptiMiner Campaign
- The exploitation of the eScan vulnerability by threat actors highlights the critical need for robust security measures in antivirus software.
- The use of backdoors and coin miners by GuptiMiner underscores the importance of continuous monitoring and threat detection to prevent unauthorized access and cryptocurrency mining activities.
- The potential ties between GuptiMiner and the North Korean APT group Kimsuky emphasize the global impact of such campaigns and the need for international collaboration in addressing cybersecurity threats.
Indicators of Compromise (IoCs)
To detect and mitigate GuptiMiner’s presence, organizations should look out for these signs:
- Unusual patterns of DNS requests: GuptiMiner may generate abnormal amounts of DNS traffic as it communicates with its command-and-control servers. Organizations can leverage DNS analytics to identify these patterns.
- Suspicious domain names related to GuptiMiner activity: Monitoring and blocking access to known malicious domains can help prevent initial infections. This can be achieved by utilizing threat intelligence feeds or following cybersecurity advisories.
Detecting, Mitigating, and Preventing Future Malware Campaigns Like GuptiMiner
To effectively counter malware campaigns like GuptiMiner, organizations must adopt proactive defenses and understand the mechanics of the infection process. Here are consolidated strategies for detecting, mitigating, and preventing these threats:
- Continuously monitor network traffic and endpoints to detect unusual activities or patterns that might indicate a breach. Employ advanced threat detection solutions to identify irregular network behaviors, unauthorized access attempts, and suspicious file activities.
- Utilizing advanced threat intelligence solutions to identify and respond to emerging threats in real time.
- Regularly update antivirus software and security patches to mitigate known vulnerabilities that threat actors may exploit.
- Conducting regular security assessments and penetration testing to identify potential vulnerabilities that could be exploited by threat actors.
- Implementing strict access controls and user permissions to minimize the risk of unauthorized access and lateral movement within the network.
- Educate employees about cybersecurity best practices, including recognizing phishing attempts, avoiding suspicious downloads, and reporting any unusual system behaviors promptly.
Additionally, Man-in-the-Middle (MitM) attacks can be a common tactic used by threat actors to intercept communication between systems and compromise sensitive data. To prevent such attacks, organizations can:
- Implement robust network security measures, such as intrusion detection systems, to detect and prevent Man-in-the-Middle (MitM) attacks that could be used as an entry point for malware distribution.
- Implement strong encryption protocols such as Transport Layer Security (TLS) to secure communication channels and prevent unauthorized interception.
- Use digital certificates to authenticate the identities of communicating parties and ensure the integrity of transmitted data.
- Employ network segmentation techniques to isolate critical systems and limit the impact of potential MitM attacks.
Prioritizing Security in Antivirus Update Mechanisms
It is essential for software vendors to prioritize security in the development of antivirus update mechanisms:
- Secure Update Protocols: Implement secure update protocols that include cryptographic verification of update packages to prevent unauthorized tampering or distribution of malicious updates.
- Threat Intelligence Integration: Integrate threat intelligence feeds into antivirus software to enhance its capability to detect and block emerging threats proactively.
Conclusion
Regular security audits, robust incident response plans, and proactive threat intelligence sharing are all integral components of a comprehensive defense strategy. By investing in advanced detection and response technologies, organizations can better detect and mitigate sophisticated threats like GuptiMiner.
However, it is important to note that no defense strategy is foolproof. Cybercriminals are constantly evolving their tactics, and new vulnerabilities are discovered every day. Therefore, organizations must also prioritize continuous education and training of employees on cybersecurity best practices. By fostering a culture of security awareness and vigilance, organizations can empower their workforce to be the first line of defense against cyber threats.
You can access the GuptiMiner malware campaign and many other campaigns via SOCRadar LABS.
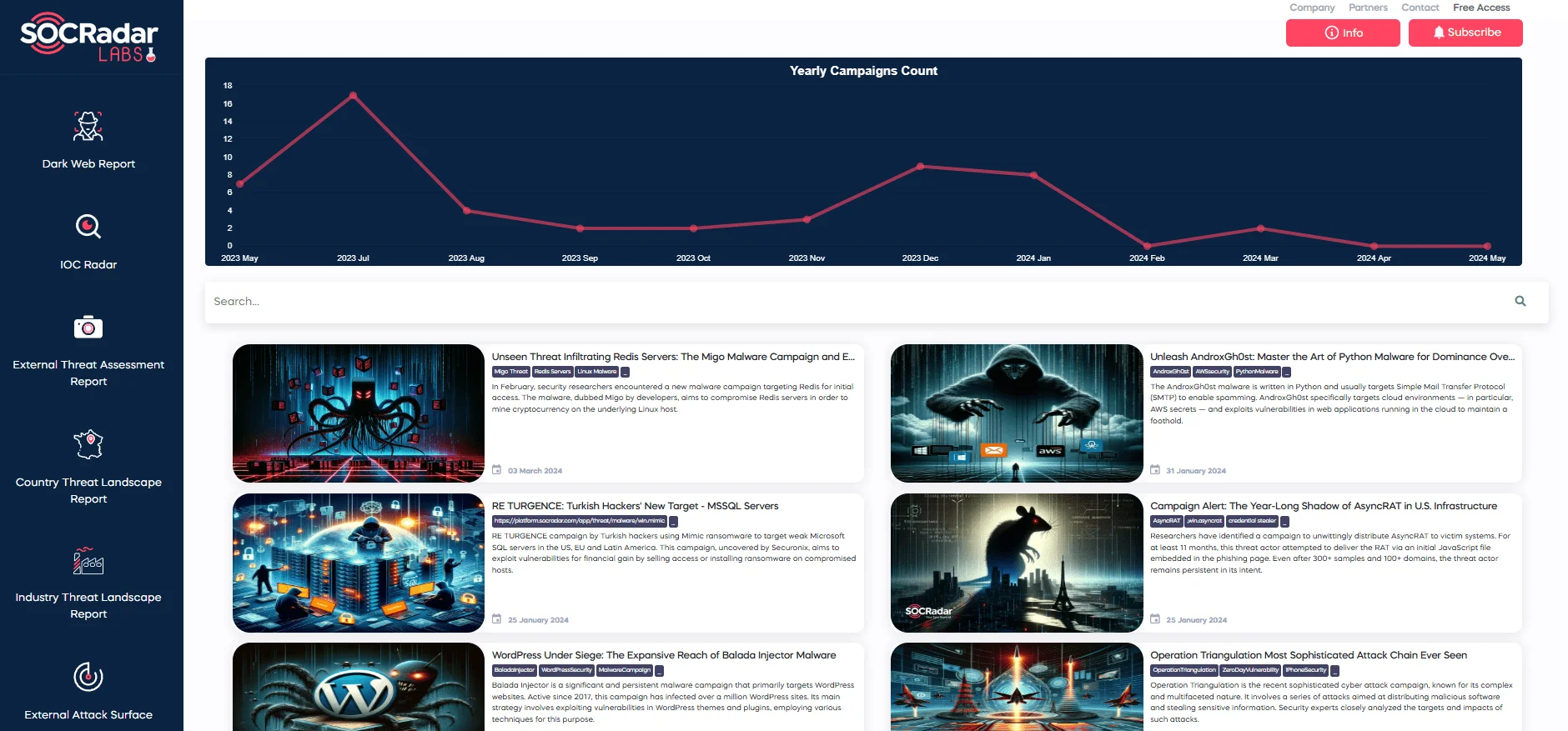
SOCRadar LABS’ Campaigns page



































