
Hackers Don’t Hack, They Log In – Stealer Logs and Identity Attacks
Cyber threat actors are moving beyond traditional methods like exploiting vulnerabilities or brute-forcing passwords. Instead, they are increasingly relying on stolen credentials to breach systems with precision and minimal effort. A significant enabler of these breaches is the rise of stealer logs—collections of stolen usernames, passwords, cookies, and session tokens harvested by infostealer malware.
According to the 2024 Verizon DBIR, stolen credentials were involved in 80% of data breaches. Stealer logs provide attackers with a direct route to sensitive systems by often serving such credentials. Moreover, the thriving trade of these logs on the Dark Web has elevated them to a highly sought-after resource among cybercriminals, fueling the rise of modern threats.

“Hackers Don’t Hack, They Log In” (Illustrated by DALL-E)
This blog explores the role of stealer logs in modern identity attacks, supported by statistics, examples of real incidents, and insights into the latest hacking trends. Stay informed and secure by understanding how these logs enable identity compromise and what steps you can take to protect your organization.
The Threat Landscape – Why Identity Attacks Dominate
Identity-based attacks are rapidly outpacing traditional hacking techniques, creating a critical challenge for organizations worldwide. As highlighted earlier, stolen credentials are at the center of these attacks. Combined with the staggering $4.24 million average financial damage per breach, reported by IBM, these figures emphasize the immense risks associated with compromised identities.
Recent research highlights that 62% of interactive intrusions involved the abuse of valid accounts, showcasing how attackers exploit existing access for malicious activities. Even more concerning is the 160% rise in attempts to gather secret keys and credentials via cloud instance metadata APIs. This reflects a clear trend: attackers are targeting the underlying infrastructure of cloud services and applications, exploiting the access provided by compromised accounts.
Phishing and social engineering, primarily used to deliver malware, aim to harvest credentials and secrets for exploitation. With organizations migrating to cloud-based infrastructure, a compromised credential today can have far-reaching consequences, including access to sensitive data, service disruptions, and the launch of secondary attacks.
In this landscape, a single compromised credential is no longer a minor issue; it’s a potential entry point for ransomware, data theft, and business disruption.
Common Techniques in Identity Attacks
With this rise in credential abuse, let’s examine the methods attackers use to exploit these vulnerabilities. Attackers use various methods to access and exploit identities, such as:
- Phishing: Fake emails, cloned websites, and social engineering trick users into surrendering credentials, bypassing email and endpoint defenses.
- Infostealers: Malware like Redline and Raccoon collects login data, cookies, and tokens, creating an inventory for attackers.
- Credential Stuffing: Automated tools recycle stolen login details across multiple platforms to find valid matches.
Needless to say, poor password practices significantly contribute to the success of these attacks. Despite widespread awareness campaigns, many users still rely on weak and easily guessable passwords. In fact, passwords like “123456,” “password,” and “admin” consistently top the lists of most commonly used passwords globally. Additionally, users often reuse passwords across multiple accounts, amplifying the risk when one account is compromised.
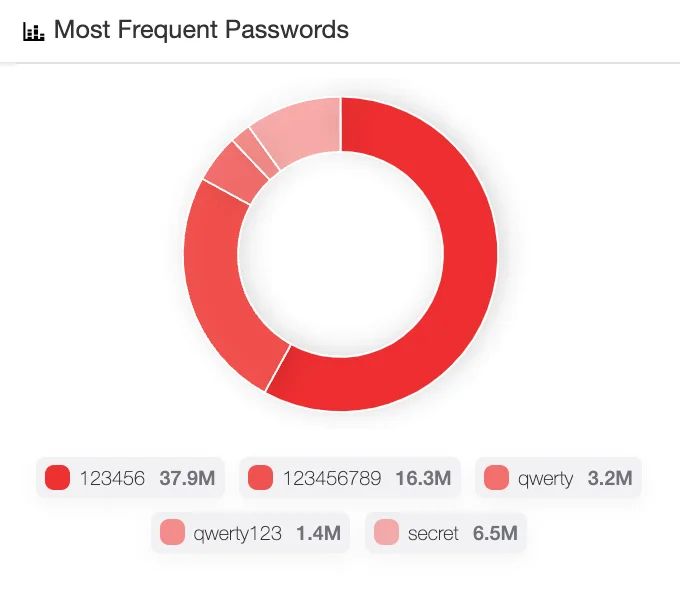
Most frequent passwords observed by SOCRadar (Identity & Access Intelligence module)
For instance, 45% of remote workers use the same password for both work and personal accounts, significantly increasing cybersecurity risks. This widespread reuse of credentials means that a single breach can cascade into broader exploitation across platforms.
By capitalizing on these vulnerabilities, attackers find it easier to “log in” rather than “hack in.”
The Role of Stealer Logs in Identity Attacks
As identity attacks dominate the threat landscape, stealer logs have emerged as a pivotal enabler of these breaches. These logs, harvested from infected devices by infostealer malware, often contain usernames, passwords, cookies, session tokens, and even autofill data. Accessible on Dark Web forums and marketplaces, they provide attackers with everything they need to impersonate legitimate users and infiltrate systems undetected.
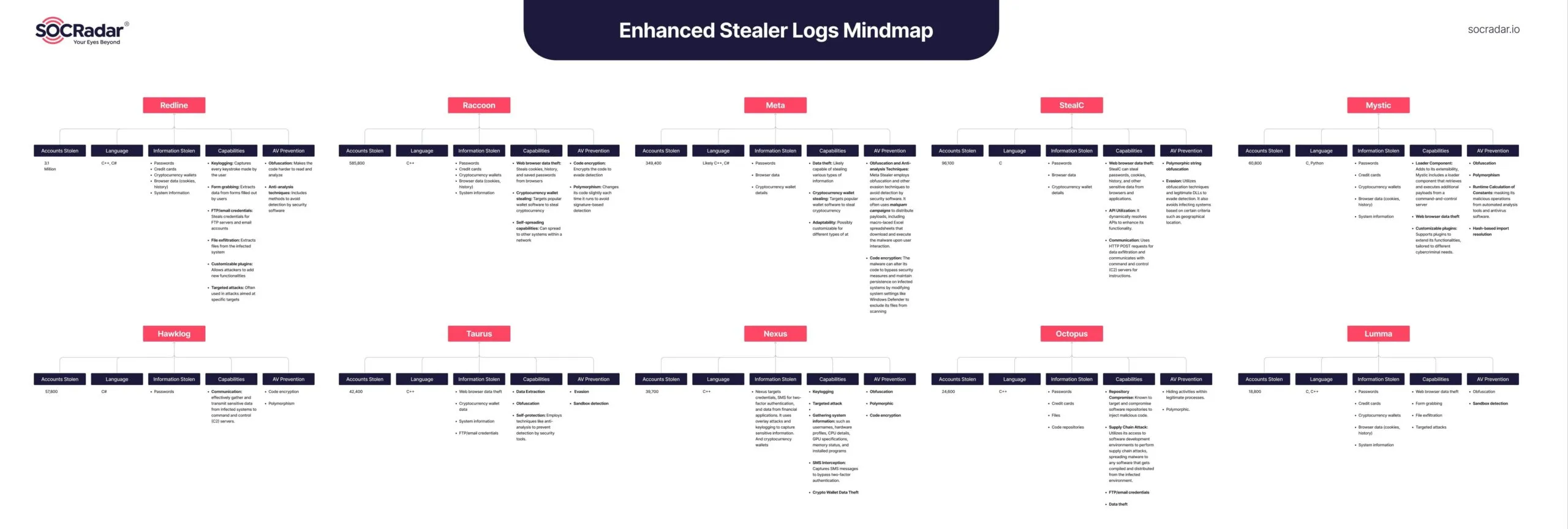
Learn about world’s top infostealer logs through SOCRadar’s article: “Top 10 Stealer Logs”
Infostealer malware typically spreads through phishing campaigns or malicious downloads. Once deployed, it silently collects sensitive data from the victim’s device and transmits it to the attacker. The Snowflake breach serves as a notable example: attackers used stolen credentials from infostealer logs to target customer-specific accounts, exploiting the absence of Multi-Factor Authentication (MFA). This breach impacted high-profile organizations, including Ticketmaster and Neiman Marcus, and demonstrated how stealer malware facilitates large-scale compromise.
Other notable cases, such as the MGM Resorts and Okta hacks, also highlight the role of compromised credentials in catastrophic breaches. In the MGM incident, attackers gained privileged access through compromised accounts, escalating privileges to deploy ransomware and disrupt operations. Similarly, the Okta breach leveraged session tokens, obtained from a past breach, to impersonate employees and infiltrate customer systems.
Rise of Access Brokers in Dark Web
With stealer logs, Initial Access Brokers (IABs) have also risen, which are cybercriminals specializing in selling access to compromised systems. These brokers extract credentials and advertise access on Dark Web forums, where demand has surged. According to CrowdStrike, Access Broker advertisements increased by 147%, reflecting the growing reliance on stealer logs for initiating attacks.
By selling pre-verified credentials, IABs simplify the attack process for ransomware groups and other threat actors, enabling them to bypass the initial stages of intrusion and focus on exploitation.
To counter the growing threat of stolen access and credentials, SOCRadar offers Advanced Dark Web Monitoring, which provides vital insights by scanning underground forums, marketplaces, and chat channels for compromised assets. With real-time alerts and actionable intelligence, you can preemptively secure vulnerable points, mitigating the risks associated with access sales and stolen credentials.
Why Stealer Logs Are a Hot Commodity
The value of stealer logs lies in their versatility. Attackers use them to execute a range of malicious activities, including:
- Identity Attacks: Leveraging credentials to infiltrate systems and impersonate legitimate users.
- Ransomware Deployment: Gaining initial access to encrypt systems and extort victims.
- Lateral Movement: Using stolen session tokens to navigate within an organization’s network.
- Privilege Escalation: Exploiting credentials to gain administrator-level access.
This ease of access and utility makes stealer logs a cornerstone of modern cyberattacks. They serve as one of the most prevalent sources of stolen credentials traded on the Dark Web, directly enabling large-scale identity-based attacks by reducing technical barriers for attackers.
SOCRadar’s Threat Hunting module can empower your security team to look up information exposed in stealer logs. This module enhances proactive defense strategies by correlating findings from stealer logs with broader threat intelligence, helping you identify trends, track threat actor activity, and strengthen incident response capabilities.
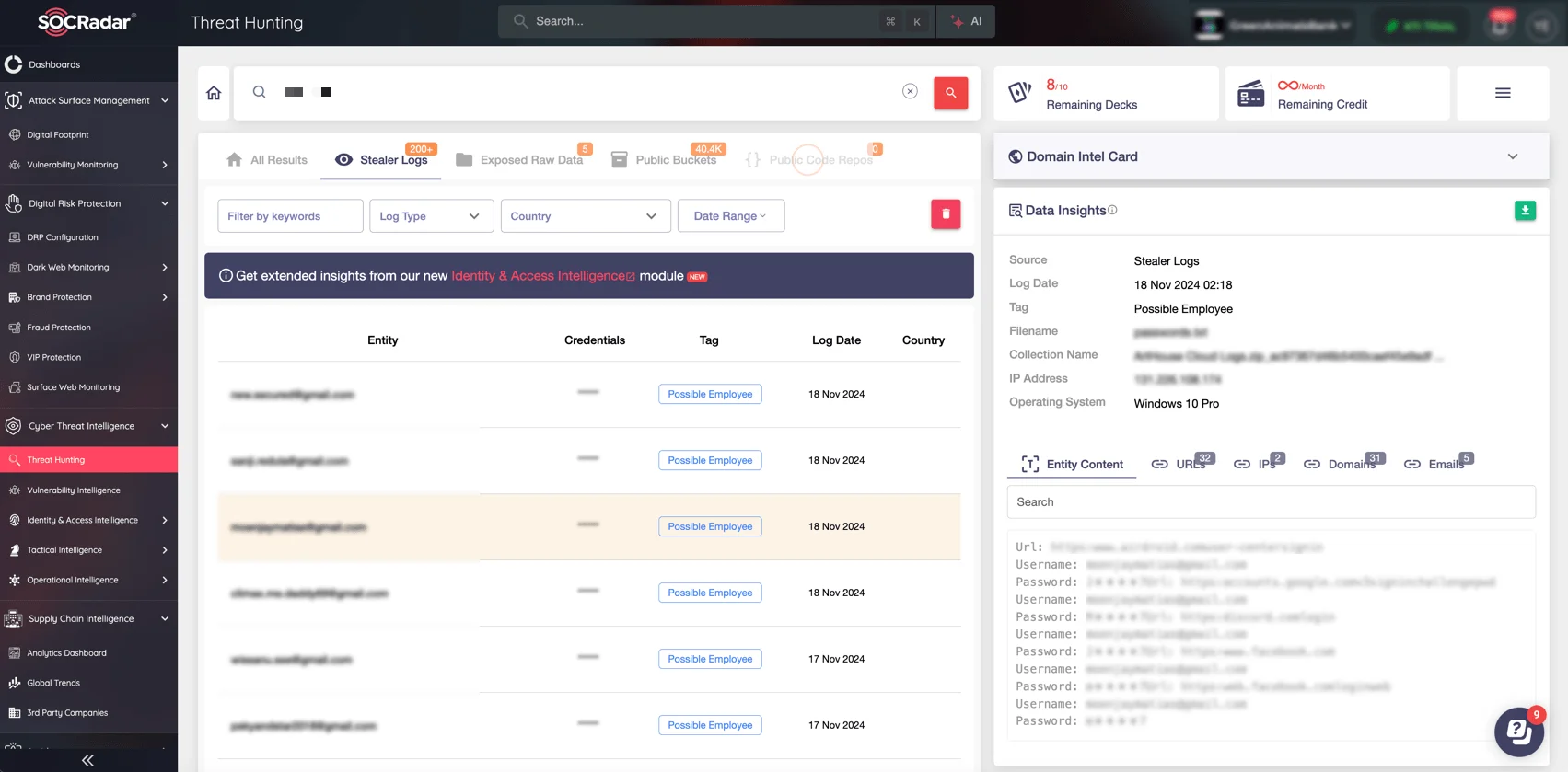
SOCRadar’s Threat Hunting module
Examples of Real Incidents
Examining recent high-profile breaches reveals a consistent theme: attackers leveraging stolen credentials to infiltrate systems and escalate privileges. Every breach highlights the need to secure credentials, which are often traded on the Dark Web, making them a common enabler for cybercrime.
While not all incidents are directly linked to stealer logs, credentials sold on the Dark Web are a common enabler, illustrating the critical importance of securing access points.
The Snowflake Breach
The Snowflake breach exemplifies how compromised credentials can lead to devastating consequences. Stealer malware harvested user credentials, which were then sold on Dark Web marketplaces. Threat actors used these credentials to access Snowflake customer tenants, bypassing protections in the absence of Multi-Factor Authentication (MFA).
The breach affected 165 organizations, including prominent names like Ticketmaster and Neiman Marcus. With access to customer-specific accounts, attackers exfiltrated sensitive data, leveraging the lack of MFA to escalate their operations across connected systems.
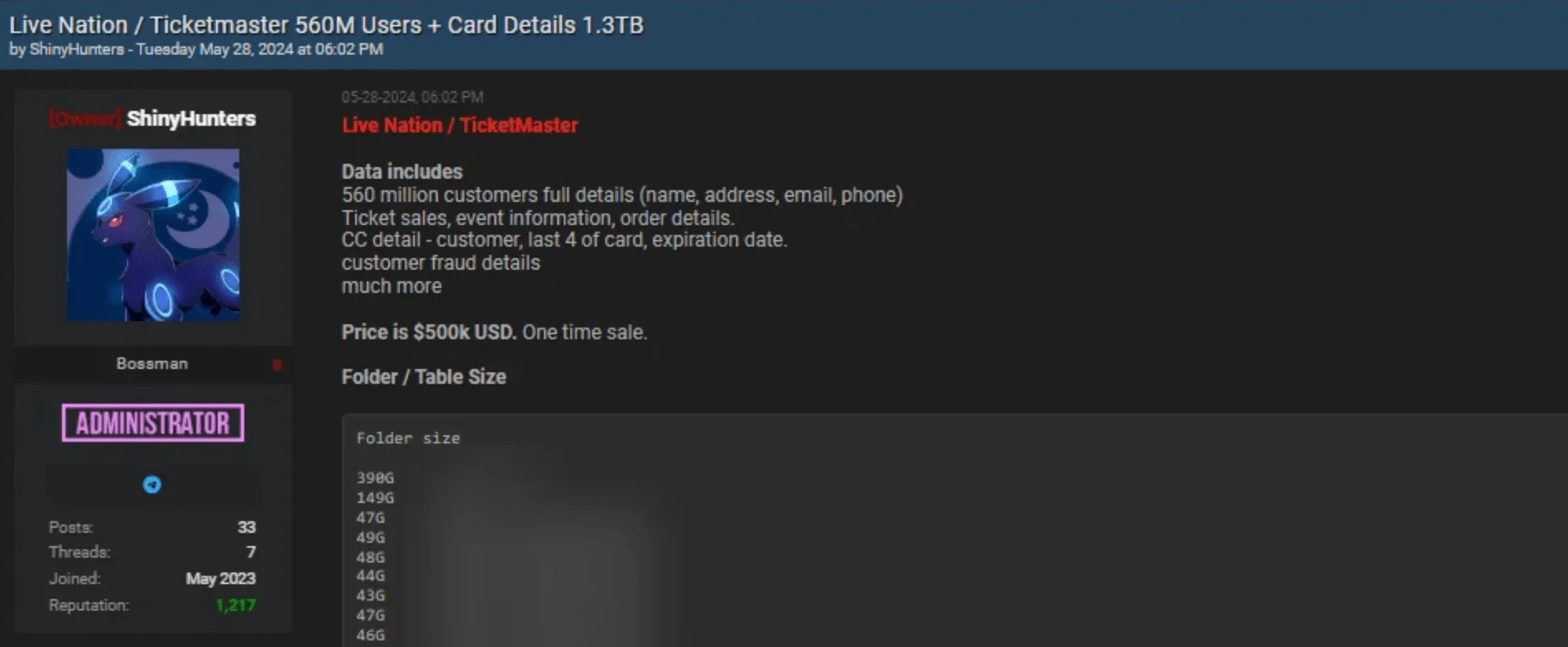
ShinyHunters leaked Ticketmaster user data in May 2024, in connection with the Snowflake breach
Other Notable Attacks
A closer look at other major breaches highlights how attackers exploit credentials and identity attacks to bypass defenses and achieve their goals:
- Okta Breach: Attackers used stolen session tokens to impersonate employees and infiltrate customer environments, demonstrating the impact of compromised credentials on a company’s wider ecosystem.
- MGM Resorts Incident:Social engineering tactics enabled attackers to compromise privileged accounts, escalate access, and bypass MFA. The attackers deployed ransomware and caused widespread operational disruptions.
- SEC X SIM Swapping Attack: Threat actors used SIM swapping to hijack the account of the U.S. Securities and Exchange Commission (SEC) on the social platform X (formerly Twitter). With no proper MFA in place, attackers reset the account password and issued a fraudulent announcement, showcasing the risks tied to weak account protections.
These cases underline the widespread exploitation of stolen credentials, often originating from sources like stealer logs.
How Businesses Can Defend Against Stealer Logs and Identity Attacks
As stealer logs continue to fuel breaches, businesses must adopt proactive measures to safeguard their systems. Below are key strategies to mitigate risks and protect against these threats.
Strengthen Password Hygiene and Identity Security
Improving identity security starts with implementing strong authentication measures. Multi-Factor Authentication (MFA) adds a critical layer of defense, making it significantly harder for attackers to exploit stolen credentials. Single Sign-On (SSO) can also reduce the attack surface by consolidating access points under one secure platform.
Equally essential is enforcing strong password policies. Businesses should mandate unique, complex passwords for every account, supported by regular password rotation. User education plays a pivotal role here, as human errors remain a leading cause of breaches. According to Gartner, 99% of cloud security failures through 2025 will result from customer mistakes, such as poor identity and access management. Strengthening password hygiene minimizes these risks and helps protect both on-premises and cloud environments.
Monitor the Dark Web for Exposed Credentials
Detecting compromised credentials before they’re exploited is critical. Continuous monitoring of the Dark Web enables your organization to identify when employees’ credentials are exposed in stealer logs or credential dumps, allowing for swift remediation.
By actively monitoring and addressing exposed credentials, organizations can outpace attackers and protect their infrastructure from exploitation.
Get Your Free Dark Web Report
Stolen credentials and stealer logs are driving modern cyberattacks, reshaping the way organizations must approach security in today’s landscape. Addressing these risks is no longer optional—it’s critical for securing your organization’s access points and protecting your assets.
To help your business take a proactive stance, SOCRadar’s Free Dark Web Report provides valuable insights into your organization’s exposure on the Dark Web, enabling swift action to mitigate risks.
Free Dark Web Report page on SOCRadar LABS
What’s in the Free Dark Web Report?
Gain a comprehensive view of your organization’s presence on the Dark Web with key findings, including:
- Threat Severity: Assess the level of Dark Web risk your organization faces.
- Dark Web Mentions: Discover who and what is being discussed about your organization.
- Employee Credentials: Identify whether your employees’ credentials are part of any leaks.
- Data from Infected Machines: Detect malware-infected devices within your company.
- Latest Exposure: Track when your sensitive data was last exposed.
- Data for Sale on Black Markets: Uncover whether your organization’s data is being sold on underground markets.
Find out how popular your organization is on the Dark Web. With SOCRadar Labs’ Dark Web Report, instantly determine if your data has been exposed on forums, black markets, leak sites, or Telegram channels.


































