
How Can Strategic CTI Help CISOs Fulfil Their Task?
Cyber threats have an emerging adversarial impact on organizations such as enterprises and governments. In parallel with increasing cyberattacks and data breaches, although deployed cybersecurity tools and software have increased in number with advanced features, unfortunately, threat actors often reach their goals. Even if cybersecurity measures are taken entirely on the defensive and offensive side, which usually cannot act agile and is sometimes ignored, it cannot be asserted that provided security is 100%. We can only claim that taking steps to minimize the security risks. Indeed, although there are basic reasons, such as the expansion of attack surfaces, it becomes clear that C-level executives who sit at the decision-making table where strategic decisions, policies, and procedures are prepared for the whole organization should be fed with some knowledge and insights. We’ll discuss how to help CISOs working under intense stress in the context of strategic CTI as a type of threat intelligence.
What is the Strategic CTI?
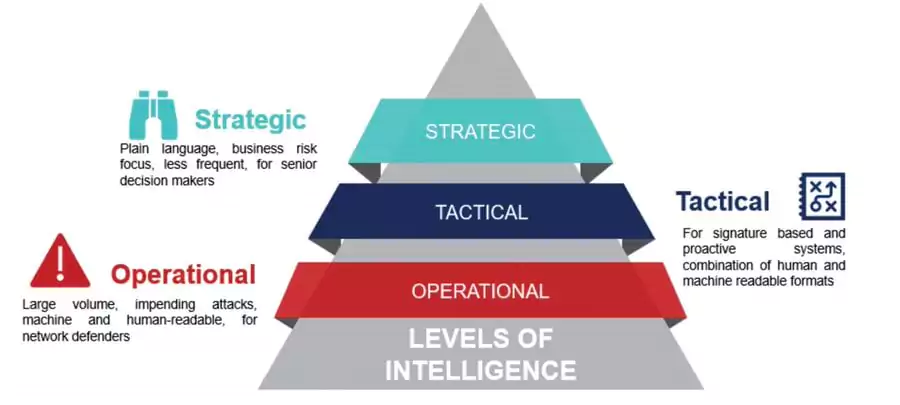
Cyber Threat Intelligence (CTI) is a discipline of obtaining, analyzing, and filtering data related to the occurrence and assessment of cyber, operational, and physical potential cyber threats worldwide. CTI is also a crucial part of the security program and is also required by both the NIST Cybersecurity Framework and ISO 27001:2022. This discipline is divided into three main areas: Tactical, Operational, and Strategic Threat Intelligence.
Tactical CTI addresses short-term and real-time what (IoCs and TTP) questions with low-level technical details. It appeals to SOC analysts, incident response teams, and IT security products (SIEM, firewalls, IDS/IPS, EDR) administrators.
Operational CTI deals with how and where (TTPs) questions; it includes detailed information that will better explain vulnerabilities, threats, and changing capabilities of cyber attackers at the operational level for decisions to be made in the medium term. It is located between Tactical and Strategic CTI, so both technical teams and managers like CISOs can use it. It is less technical than the tactical level but more technical than the strategic level.
Strategic CTI deals with the who (attribution) and why (motivation/intention) with a high-level overview of the cyber threat landscape and big-picture details about attack trends and focuses on long-term strategic planning. Based on Strategic CTI enables executive staff to drive high-level organizational strategy. (e.g., developing policies and procedures, allocating resources, and prioritizing investments in security technologies). It comprises the least technical intelligence that provides a broad view of the capabilities and intent of malicious actors. It is able to help high-level staff like the company board of directors on long-term or broader security strategy issues to understand the risks and vulnerabilities associated with the organization and the goals of threat actors.
It is also a proactive and predictive mechanism for creating integrated insights within the business security program. It enables them to make more informed risk-based decisions about mitigating risks and defending the organization against potential threats.
Strategic intel is where threats are coupled with organizational impact, taking more of a risk-based view that helps you align your security program to your threat reality. Who, why, and where?
Strategic CTI focuses on the future, including emerging trends, and is used to make longer-term decisions. It tends to be the hardest form to generate. It can emerge as a result of an insight blended with experience together with information filtered from data analyses. It requires a holistic approach, like a good understanding of both cybersecurity and the nuances of the world’s geopolitical situation during data collection and analysis. For instance, state-organized attacks are usually linked to geopolitical and geostrategic conditions. In addition, financially motivated cybercrime groups are always evolving their TTPs to achieve bigger payoffs. Furthermore, long-standing campaigns through malware are widely sold on the dark web market with the MaaS (Malware-as-a-Service) model and distributed through large-scale botnets.
Business executives can benefit from strategic CTI by gaining critical and beneficial insights and establishing meaningful cybersecurity benchmarks to monitor and assess as part of business strategy sessions.
To give an example to better understand how Strategic CTI can help the decision-making process if you want to acquire or partner with another business, it is important to put a threat-oriented cyber risk rating as part of the due diligence process. In this way, you can observe how your position compares to competitors in terms of cyber security preparedness, or you can estimate whether this attempt is the right decision for your organization and so turn an intelligence-based risk approach into value for your business.
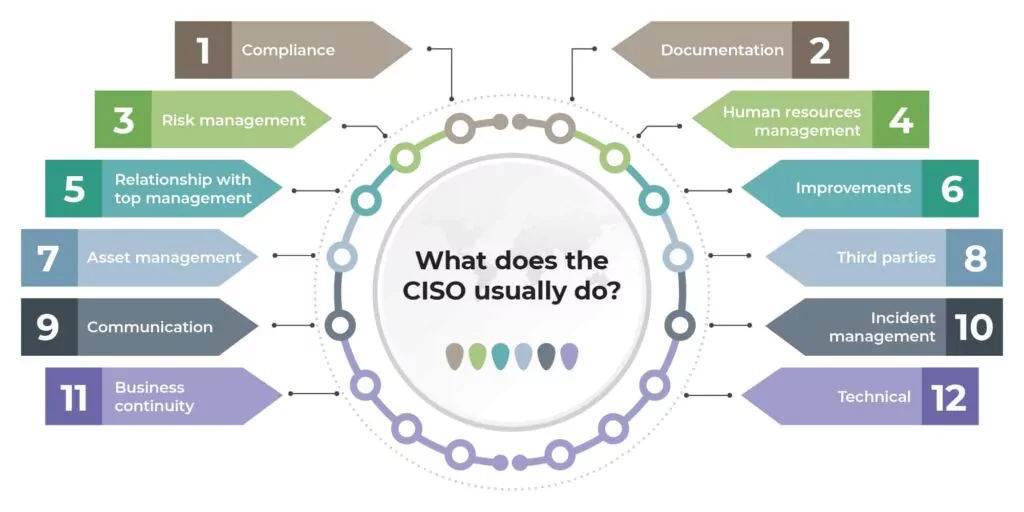
What are the CISO Roles and Responsibilities?
Chief Information Security Officer (CISO/CSO) is a high-level executive who oversees and administers an organization’s information, cyber, and technology security. The position of a CISO can take on a diversity of tasks and responsibilities depending on the size, hierarchy, industry vertical, and compliance regulations applicable to the organization.
The modern CISO’s responsibilities can include:
- Safeguarding the organization’s sensitive information and maintaining the trust of customers and stakeholders.
- Developing and implementing security processes and systems to prevent, detect, mitigate, and recover from cyberattacks.
- Educating and managing technology risks in collaboration with business leaders, creating and driving cybersecurity strategies, policies, procedures, and frameworks with initiatives to secure the organization’s cyber and technology assets.
- Continuously evaluating and managing the organization’s cyber and technology risk posture, implementing and managing the cyber governance, risk, and compliance (GRC) process.
- Reporting to the most senior levels of the organization (like the CEO and board of directors), developing, justifying, and evaluating cybersecurity investments.
- Developing and implementing ongoing cybersecurity awareness training and education for personnel.
- Leading cybersecurity operations and ensuring business continuity in the face of cybersecurity challenges.
Chief Information Security Officers (CISOs) hold a critical and challenging role in today’s rapidly evolving cybersecurity landscape. There are the common security challenges CISOs face, including sophisticated cyberattacks, insider threats, compliance, and regulatory requirements, cloud security, security skill gap, third-party and supply chain risk, security awareness training, incident response and recovery, emerging technologies, and budget and resource constraints.
As organizations increasingly depend on technologies to drive their operations, CISOs encounter complex security challenges that demand their expertise and strategic decision-making. A CISO expects that a CTI practice will reduce the risk for the organization. However, with budgets under tight scrutiny, a CISO needs to have effective and timely reporting on CTI performance. Furthermore, IT leaders need to understand what they are up against to plan strategically with appropriate investment levels.
Armed with strategic CTI, CISOs can direct or re-direct cybersecurity efforts to ensure they align with business priorities. Thus, you may have prevented wasted investments. With the starting point of CTI capabilities, it is possible to see the forest for the trees.
While carrying out these hard and heavy tasks, at which critical points can the Strategic CTI come to the aid of CISO, or what questions or requirements CISO get the answers to:
|
Are we well positioned against cyber threats, or are we not? If not, is something wrong? |
|
Are there any specific threats to our lines of business? |
|
Could cyber threats change over time? What threats do those in the same industry face that we do not know about? |
|
What are the most likely potential threats? How are they being accomplished by threat actors? |
|
What are the most important cyber assets and critical data, and what is being done to keep those secure? |
|
Have there been recent cyber incidents, and if so, have weak links and entry points been identified and necessary measures taken? |
|
Have any of our partners/vendors or those in our third-party/supply chain vendors suffered a cyber-attack or been exposed to a critical vulnerability such as zero-day? What are we doing about it? |
|
Have we conducted a gap analysis of our organization’s risk posture and assessed its readiness to handle cyberattacks? Are we actively monitoring that presence for fraud risks or cyber threat events? |
Strategic Intelligence Use Case Scenarios For CISO
For example, you are rendering service in the telecommunication sector and trying to keep up with an environment of rapid technological change and transformation. You are constantly transferring technological products to get ahead of your competitors and implement them, perhaps without taking security concerns into account holistically. Before making such a strategic decision that will affect your organization in the long term and make you dependent, you decided to consult Strategic CTI information. You have gained the insight that the third-party software you will purchase is constantly struggling with vulnerabilities. It is an easy bite for threat actors targeting your sector and even persistently armed on it. The risk scores of its products are high, and it is a technology that will increase your burden instead of taking off from the perspective of the security manager. Such reliable intelligence information not only saves the CISO but is also a lifeline for board members.
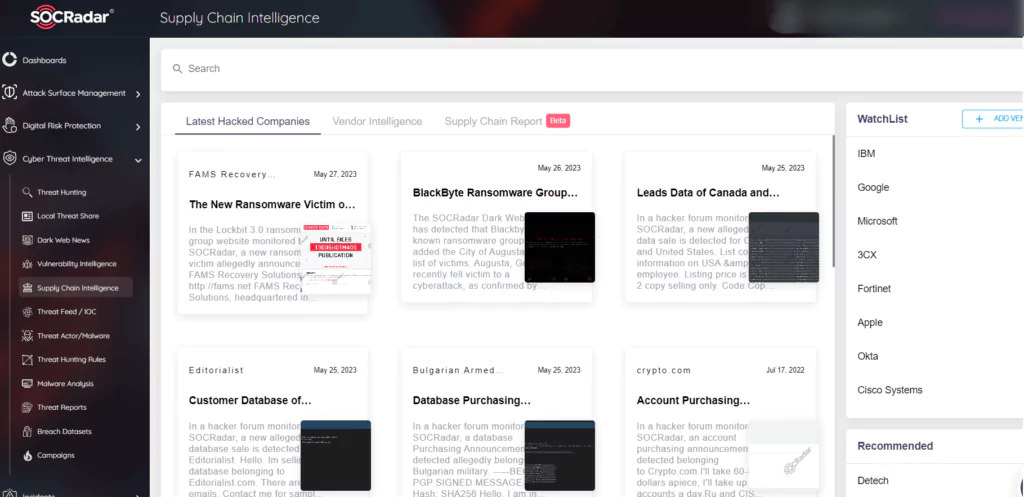
Moreover, supply chain attacks are especially emerging threats that target organizations by infecting legitimate software to distribute malware, usually linked to vendors’ vulnerabilities. Therefore, to avoid adding service providers as a weak and insecure link in the digital supply chain that could weaken your security posture, SOCRadar Supply Chain Intelligence module can alert you about companies already targeted to cyber attacks, extract actionable intelligence information from retrospectively collected and analyzed data which vendor related cyber incidents and data breaches, and provide you with a report enriched with threat intelligence.
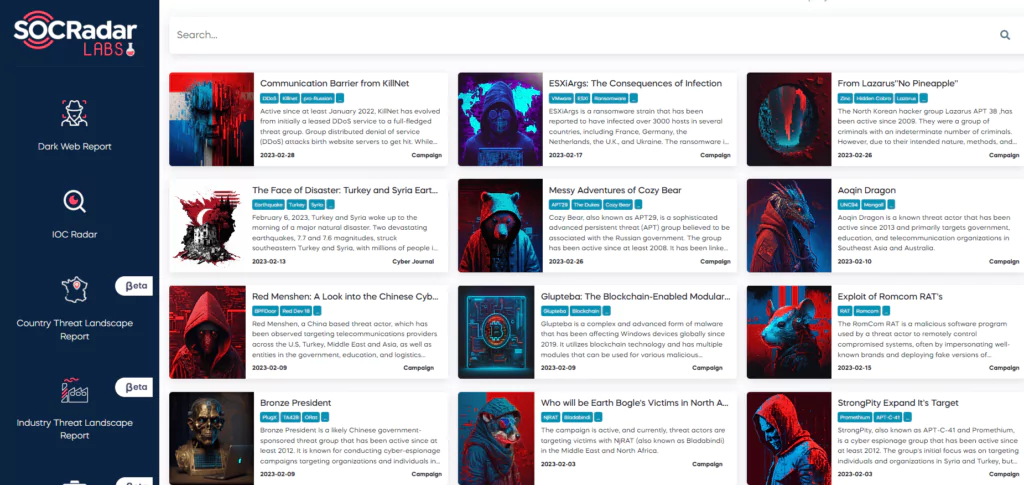
In addition, intelligence information about recent campaigns in attack categories can also be critical for your business. Campaigns can be defined as a group of unauthorized intrusion activities carried out over a certain period with common goals and objectives. The typical feature of these activities may or may not be directly and individually linked to a specific threat actor. Therefore, you can follow these threat elements spread over a very wide area on the SOCRadar Campaign page and develop strategies by gaining insight into country and sector-based targets.
Conclusion
Strategic threat intelligence can help organizations reset the corporate culture, shifting cybersecurity accountability from its silo and elevating cyber risk understanding and decision-making to business leaders. An important way to bridge the gap so that cyber issues and solutions are relevant and understandable to the C-suite and boardroom is to look at cyber threats through the lens of threat intelligence. A powerful way to start is to create the “blueprint” for each business unit in your organization using the key questions highlighted above in a structured way and shoot for delivering a finished intelligence product that provides the business unit leader with insight and context into where they stand on cyber threats and what actions they can take to mitigate these threats to their business unit.
Ultimately, strategic CTI should drive your cybersecurity program and approach. It ensures your organizational strategy is linked to your cyber risk management and lays the groundwork for more meaningful risk assessments and threat impact analysis to help you move to a more proactive stance that improves your overall cyber hygiene.
Organizations not only need to develop sufficient capabilities to protect themselves but also to do so at a reasonable and predictable cost. For providing and enabling a formation of a threat intelligence practice, it has been recommended to examine and explore CTI solutions on how to ingest and acquire threat intelligence information properly and integrate it into your decision-making process.


































