
Open-Source RATs Leveraged By APT Groups
The complexity and continuous evolution of cyber threats make the attack techniques developed by attackers with objectives such as information theft, espionage, or remote control of systems increasingly sophisticated. In this context, Advanced Persistent Threat (APT) attacks, known as long-term and targeted attacks by advanced cyber attackers, come to the fore. In these attacks, it is sometimes observed that APT groups use open-source Remote Access Trojan (RAT) software. In this research paper, why APT groups also utilize open source RATs, the characteristics and detection of these RATs will be discussed in detail.
Why Do They Prefer To Use Open Source RATs?
Open-source RATs offer APT groups several advantages that make their work easier and increase their attack techniques. This software’s free and ready-to-use availability also helps APT groups save time and resources.
APT groups may prefer to use open-source RATs to have the advantage of customizing and adapting their attack tools precisely to their needs. Since these groups have access to the software’s source code, they can add features, modify existing features and optimize their attack operations.
Attackers may employ various evasion techniques to disguise their attacks and make them difficult to detect. Open-source RATs may include anti-analysis and detection measures to circumvent security measures and maintain long-term persistence in the system.
These anti-analysis and detection measures are designed to prevent their attacks from being analyzed and detected while at the same time aiming to execute attacks that are less detectable and without attracting the attention of defense systems. According to this result, it is understood why APT groups may prefer open-source RATs in their attacks.
Open-source RATs, supported by a large developer community, can be continuously updated. APT groups can improve their attack tools by utilizing the information and resources these communities provide. They can also carry out targeted attacks through RATs by exploiting vulnerabilities. Mandiant researchers authored “Demonstrating Hustle: Adversary Tactics for Defence Teams” by Mandiant researchers can provide more information on this topic. Information sharing between communities contributes to developing attack techniques and defense strategies. During our research on Telegram channels, we collected information about AsyncRAT, and our results support that this RAT type is frequently used in purposeful attacks due to its customizability.
As shown in the screenshot, AsyncRAT is open-source and customizable, so it can often be used in purpose-built attacks.
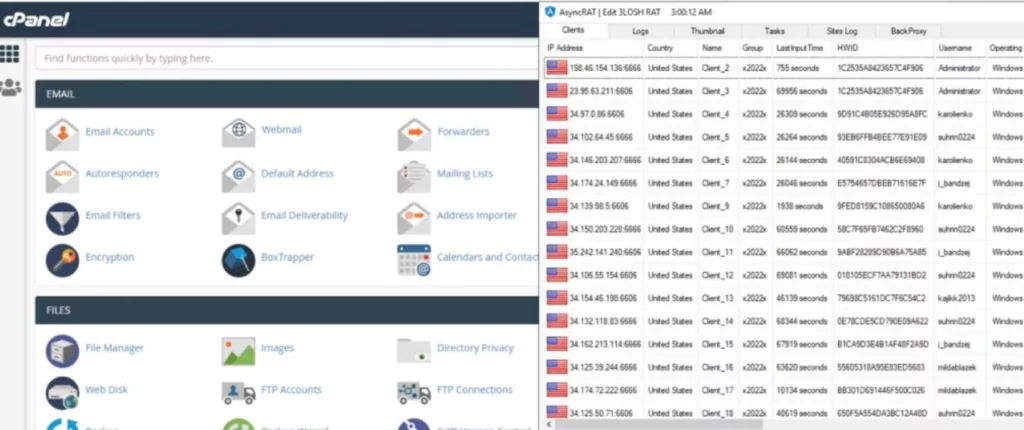
APT groups can reduce the traceability of their attacks by using open-source RATs. While carrying out their attacks using this software, they can use various techniques to leave no trace. It also provides plausible deniability by enabling the people who carry out the attacks to deny themselves.
As a result, free access, flexibility, customization, advanced evasion techniques, community-based development and information sharing, traceability, and plausible deniability are important factors for these groups to prefer open-source RATs as part of their attack strategies. Therefore, security experts need to understand these threats and consider the characteristics and usage scenarios of open-source RATs in order to take effective measures.
Most Used RATs by APT Groups
In the first phase of our research as SOCRadar Threat Research team, we used various sources to determine which RAT types are preferred more frequently. Reports on research conducted in recent years reveal that some open-source RAT types are used more frequently than others.
To perform our detections, we relied on the blackorbird GitHub repository, which contains many reports on APT groups. Thanks to these reports, we were able to access information on various open-source RAT types discovered and studied by security vendors and researchers. We successfully performed our detections through a Python script we wrote by scanning these sources. Thus, we were able to advance our research to the next stage to obtain more detailed information about the more frequently detected open-source RAT types used by APT groups and make analyses based on up-to-date data. In the image below, you can see the results of the Python script we wrote.
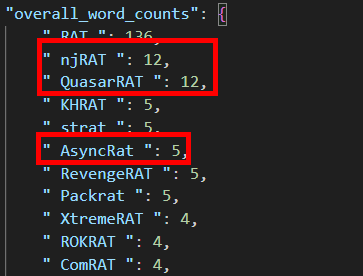
We reached the result in the visual by selecting 63 of the PDF files of APT groups in the GitHub repository, which we use as a source that we can use in our research. At this point, the RATs we targeted due to their widespread use were as follows:
- NjRAT
- QuasarRAT
- AsyncRAT
When we examined these 3 different open-source RATs that we identified in our research, we concluded that NjRAT is included in our list because its source codes have been leaked due to its widespread use. It is easily accessible on platforms such as GitHub, but it is not an open-source RAT type. For this reason, we preferred to include NjRAT in our research due to its widespread use.
NjRAT is known as a Remote Access Trojan, also known as Bladabindi. A group of hackers developed it in June 2013. In our research, one of the groups we identified for using NjRAT is APT 41, an advanced threat actor based in China. APT 41 is known as both a nation state-sponsored and a commercial group.
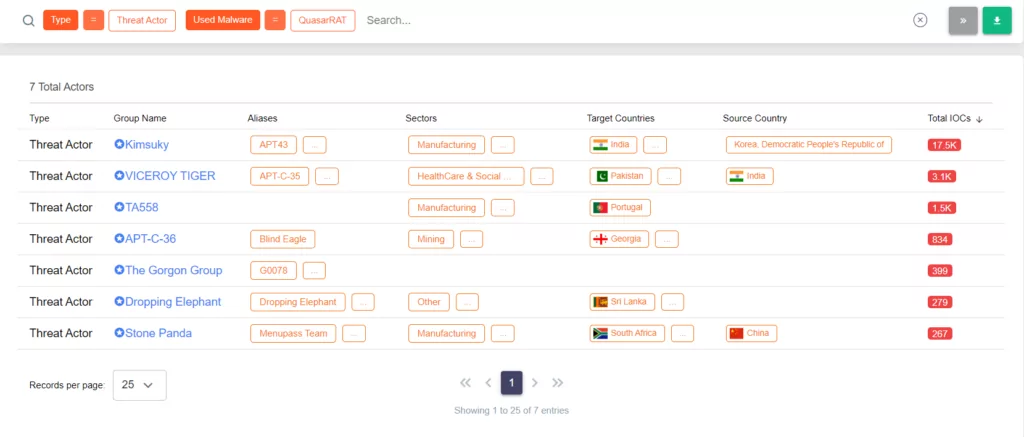
QuasarRAT, developed using the C# .NET programming language and used by various attackers, this RAT is fully functional and open source. Dropping Elephant (also known as “Chinastrats” and “Patchwork“), associated with the use of QuasarRAT, is a threat actor that attacks a variety of high-profile diplomatic and economic targets using a specialized set of attack tools. These attacks are usually directed at victims related to China’s foreign affairs and are often carried out through methods such as spear-phishing or watering hole attacks. In addition to Patchwork targeting China, QuasarRAT has also been observed to be used by the Chinese state-sponsored APT10, also known as Stone Panda threat actor.
AsyncRAT is a Remote Access Trojan (RAT) that is developed using the C# programming language and grants attackers remote access and control over the targeted system. It operates based on asynchronous logic and enables various malicious activities to be conducted on the compromised system. The group associated with the utilization of AsyncRAT is known as Blind Eagle (APT-C-36), which has been active since April 2018. There are indications suggesting that this group originates from South America, and it has been identified that they have carried out persistent, targeted attacks against significant entities across multiple sectors, including Colombian government institutions, the financial industry, the oil sector, and professional production.
As a result of this research, we recommend you visit the Threat Actor / Malware page in the Cyber Threat Intelligence on our platform to access more technical information about threat actors, tactics, techniques, and procedures. This page provides more detailed information about the malware used by the relevant threat actors.
Threat Hunting: RAT Detections and Statistical Result Analysis
In our Threat Hunting process, we focused on the numerical statistics of the RATs we detected from the beginning of 2023 until May 1, 2023. These statistics provide important information about the prevalence and threat level of RATs. In this paper, we will explain the value of this information to the cybersecurity community by sharing statistical data such as the number of RATs we detected, their connections to command and control centers, and their country distribution. We aim to help you learn more about the evolution of RAT threats and prevention efforts.
To start the hunting process for the RATs we identified, we downloaded sample files and performed our analyses using the malware databases of platforms such as MalwareBazaar and Hybrid Analysis. These platforms are known for having a large collection of malware and are often used as valuable resources in threat hunting. Our analyses included behavioral analysis of RAT samples, source code analysis, and network traffic analysis. Thanks to these methods, we gained a better understanding of the working principles, interactions, and potentially harmful effects of RATs. In addition, we started the hunting process by creating YARA Rules for further detection. Using the UnpacMe platform, we obtained several samples for NjRAT, QuasarRAT, and AsyncRAT in the date range we determined. These samples contain different variations of these RAT species and are used in our analyses. According to UnpacMe statistical data, in the date range we determined:
- NjRAT: 171,
- QuasarRAT: 80,
- AsyncRAT: 71 pieces
A total of 322 RAT samples were detected.
The biggest factor in using UnpacMe in this research and hunting process is the inclusion of the Malware Config Extract section.
Country Statistics
For the IP addresses connected to the command and control centers of the sample files we obtained, we performed information query operations such as Whois, ASN, etc., and thus obtained a wide range of country statistics. The image below shows that the detections were made in a large number of countries.
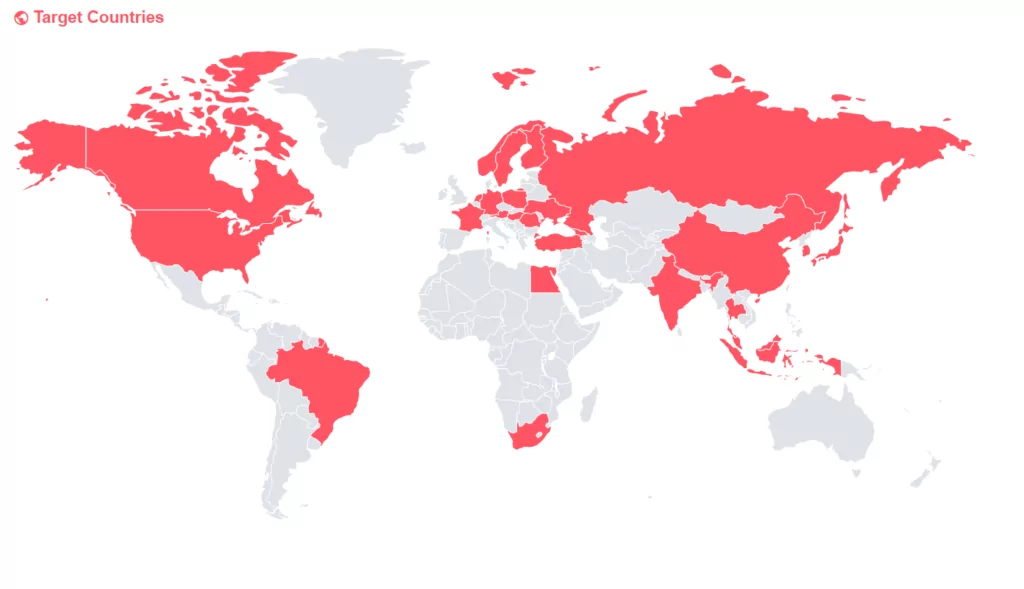
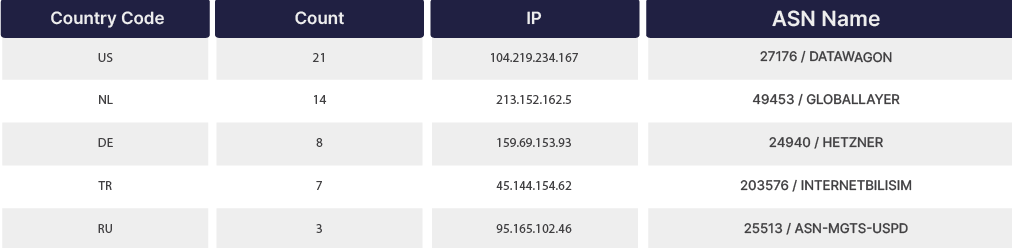
Within the scope of our research, information on the targeted RATs has been identified in many countries. In total, control provision was detected in 98 countries and different cities. The number of unique countries is 27. These results show a similar picture with the country statistics for stealers we obtained in the article “Snapshot of 70 Million Stealer Logs“.
For example, during the reverse engineering and static analysis process, we performed on QuasarRAT, certain steps were followed to reach the command and control address.
|
SHA-256 |
78eb982abdfb385ac2e0c9a640856077379355f16e29788456a6551c166b00fe |
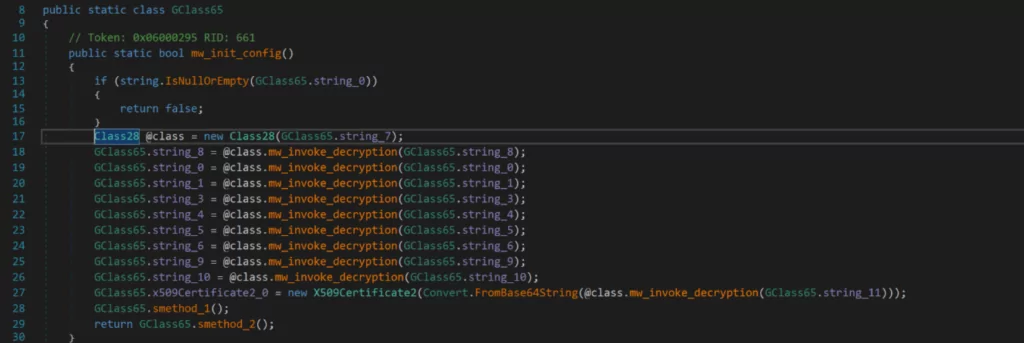
The values GClass65.string_8 refer to a value encrypted with the AES encryption algorithm and then using base64 encoding.
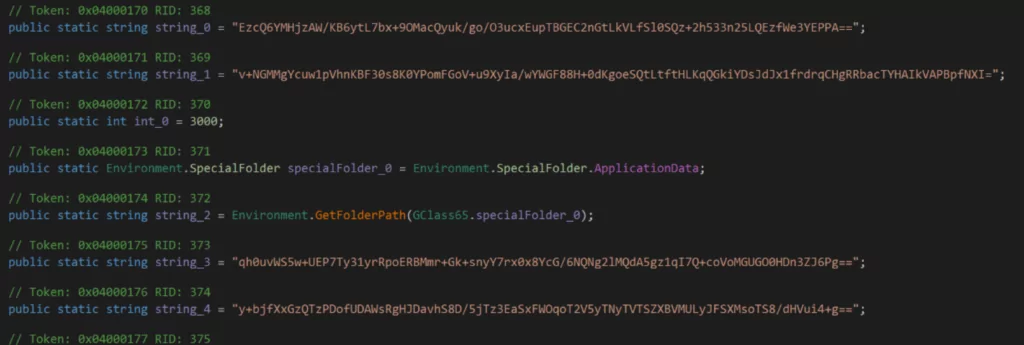
After these steps were completed, we identified the function to be AES analyzed by static code analysis and tried to find the control center connected to the relevant instance without establishing a connection by running it step by step in the debugging process.
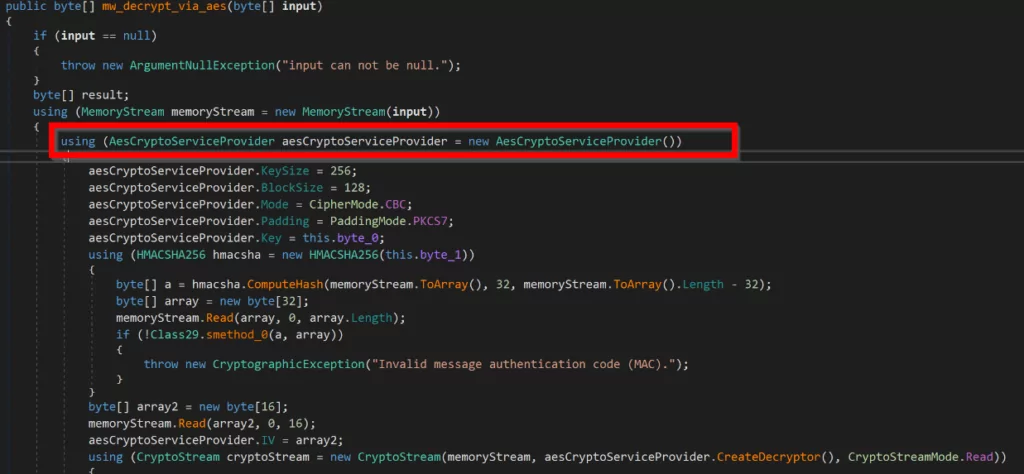
As can be seen from the screenshot, the function specified for AES decoding is specified as “CipherMode = CBC.” This indicates that they perform the decryption process by specially selecting the CBC (Cipher Block Chaining) mode in AES decryption. In CBC mode, each cipher block is XORed with the previous cipher block, and a dependency is created between successive blocks.
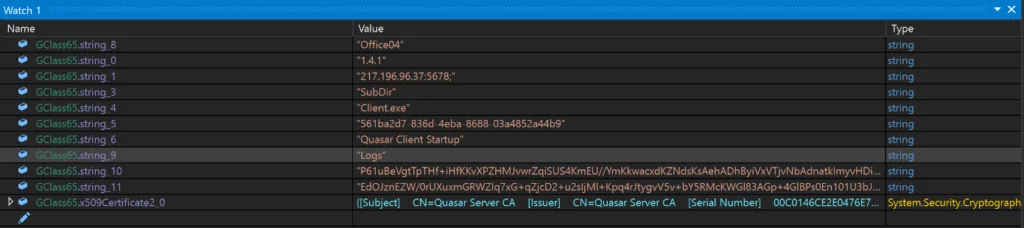
According to our observation, the address 217[.]196[.]196[.]96[.]37:5678 can be identified as the command and control center. A striking point in the “Subject” section is “CN=Quasar Server CA.” It should be known that by using the Shodan service, we can detect other addresses other than this address. The purpose here is to discover other addresses associated with the same CN (Common Name).
After several attempts to perform this search through Shodan and obtain successful results, we verified that the ssl.cert.subject.cn: “Quasar Server CA” query gives the best result. You can see the results of Shodan in the image below.
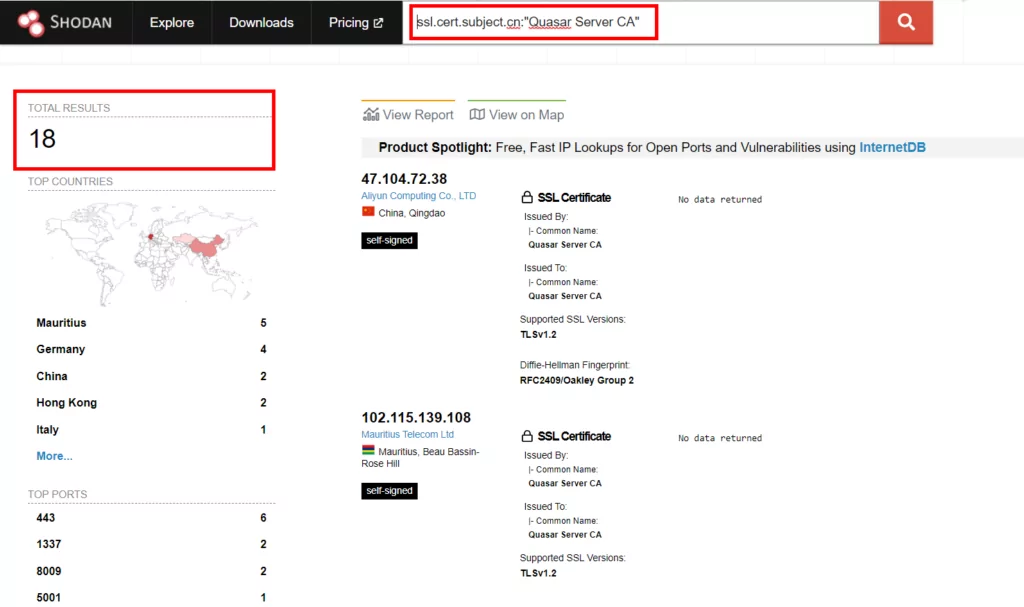
There are 18 active results that match the countries we specified in our country statistics. As mentioned, we have detected many sample files with the YARA rules we created within the scope of Threat Hunting. However, manually extracting the config information for each file separately would be time-consuming. For this reason, we preferred to use open-source Python scripts and the information contained in the malicious files we detected at UnpacMe. This method allows us to save time by automating the process.
A part of the resulting output of the open-source Python script we used to extract configuration information is shown below.
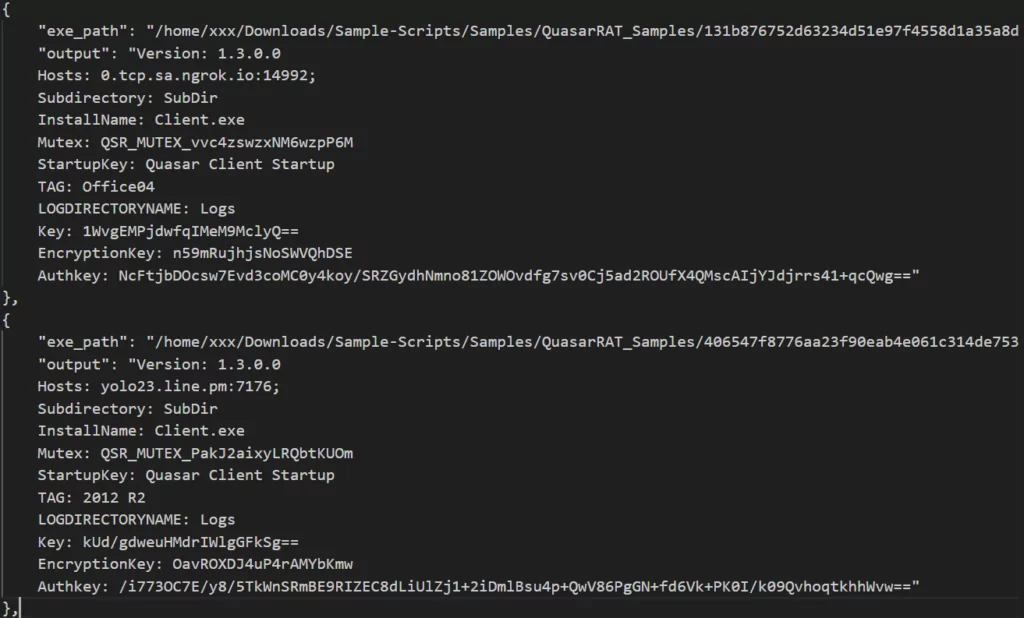
As we mentioned at the beginning for NjRAT, the Python script fails at this point because the source code is leaked, and the versions are different. As a result, the reason for choosing the UnpacMe address emerges at this point. We checked whether there is a match between the results of the command and control centers we obtained, that is, whether the address of the same command and control center is used for AsyncRAT, QuasarRAT, and NjRAT. After our checks, the use of the address “dnuocc[.]com” on different ports for AsyncRAT and QuasarRAT in different date ranges was detected. After our detections, when we checked the relevant address from our IOC Radar and SOCRadar Platform, it was among the blacklisted domains in our records. At this point, it is a clear answer to the question of why we should get help from the threat intelligence company.
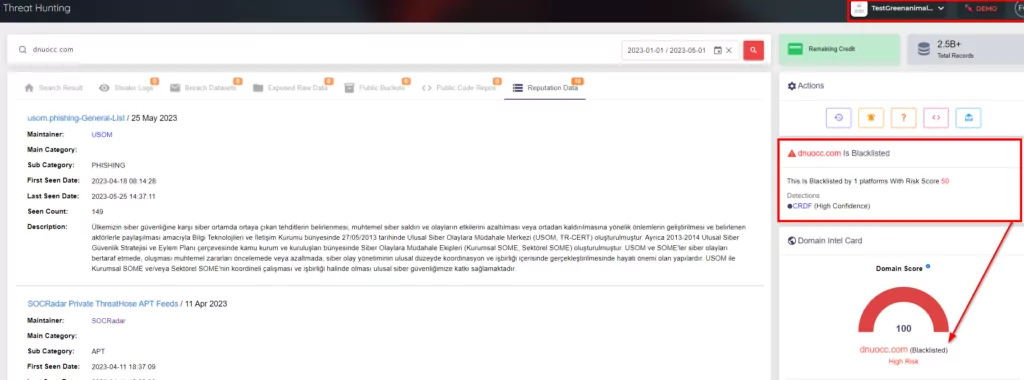
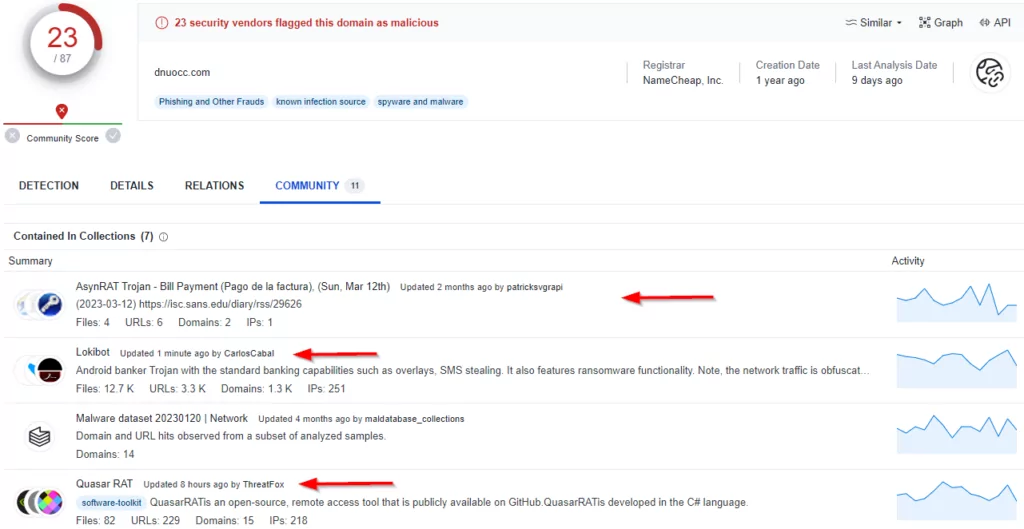
When we searched VirusTotal for the address “dnuocc.com,” we observed references to LokiBot in addition to AsyncRAT and QuasarRAT. As can be understood from this, addresses detected for many malware can also be used for different malware.
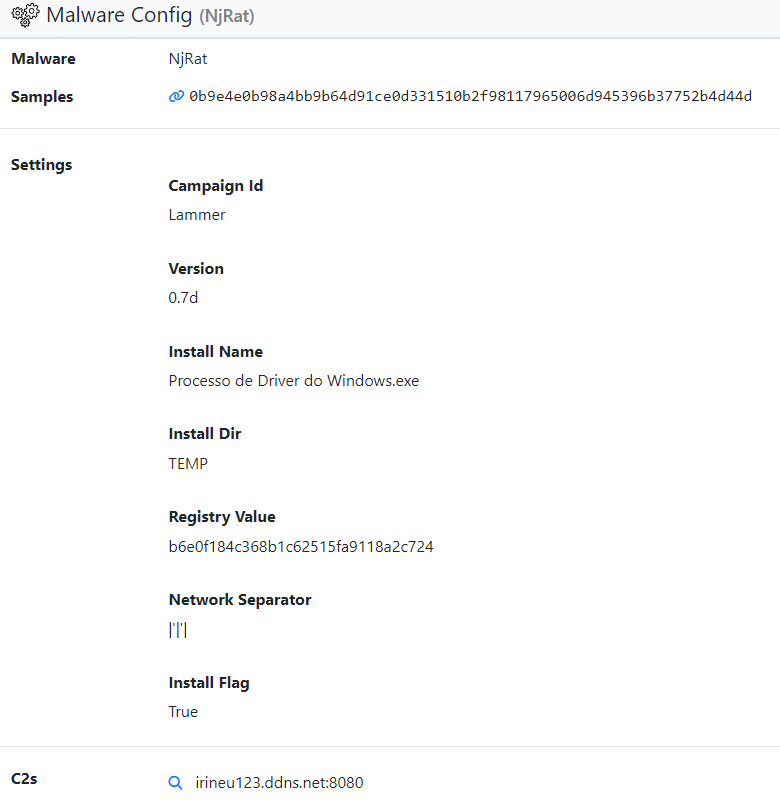
The image below gives the output of the configuration (config) information of the NjRAT sample file that we detected with the YARA rule we created.
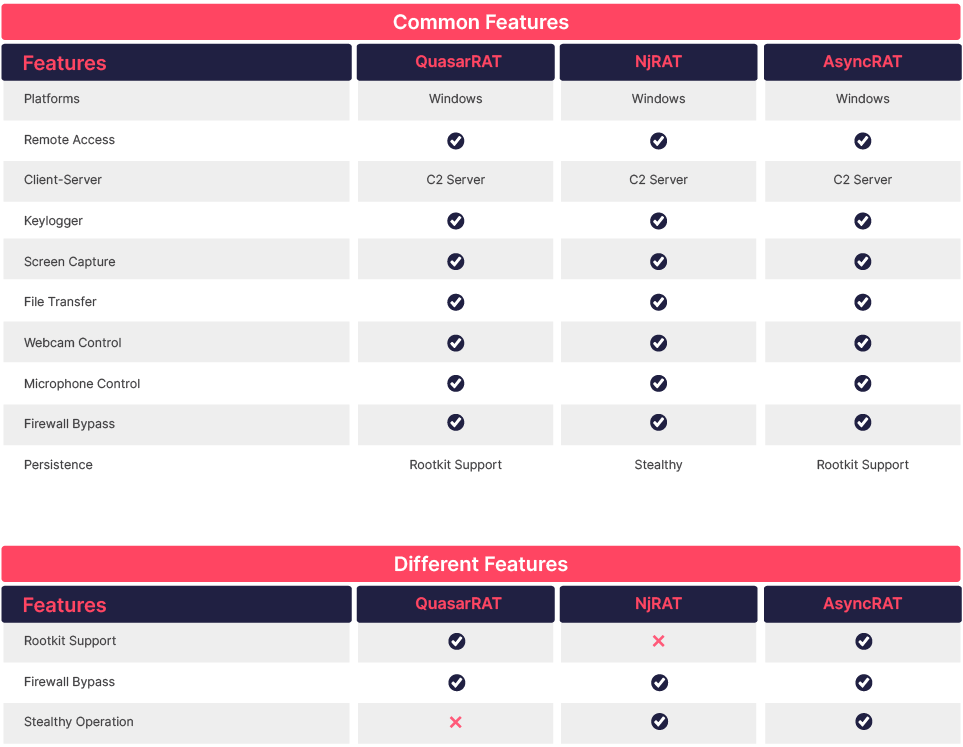
TTPs and Common Features
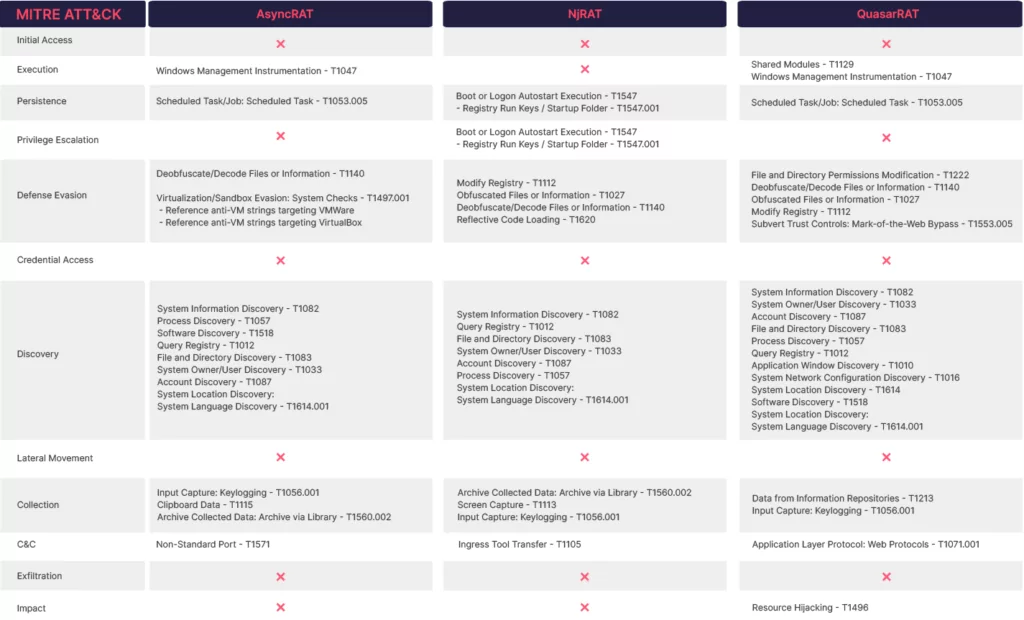
Our Tactics, Techniques, and Procedures (TTPs) analysis on malware such as AsyncRAT, NjRAT, and QuasarRAT have yielded interesting results. Although these RATs are in the same malware family, they are called by different names and have different operating mechanisms. By analyzing the Tactics, Techniques, and Procedures (TTPs), many different aspects emerge, and conclusions can be drawn about why different choices were made. To see in more detail the commonalities and differences we have established for the characteristics of TTPs and RATs, we present the results in the table below. This table will provide a better understanding of the relationship between the characteristics of TTPs and RATs.
SOCRadar Platform: Threat Hunting
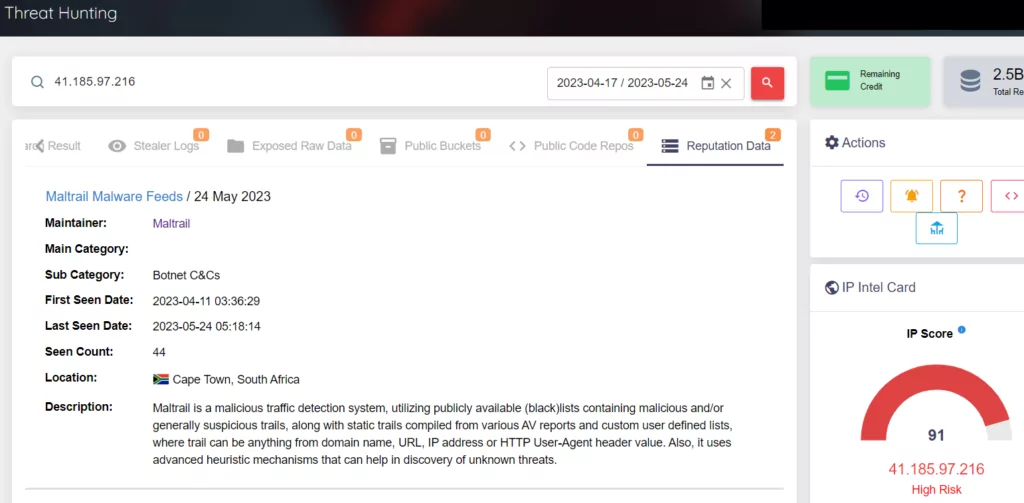
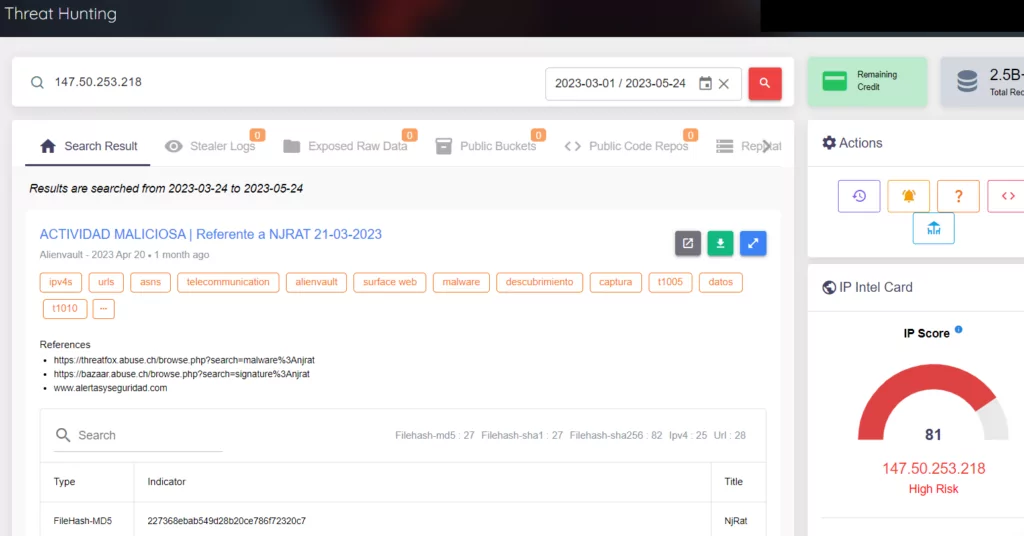
Through our platform, we are able to obtain more detailed results by performing all of the queries of the command and control centers we have obtained about RATs. In the images below, you can see our results about AsyncRAT, QuasarRAT and NjRAT. These results are available on our Threat Hunting page.
AsyncRAT:

QuasarRAT:
NjRAT:
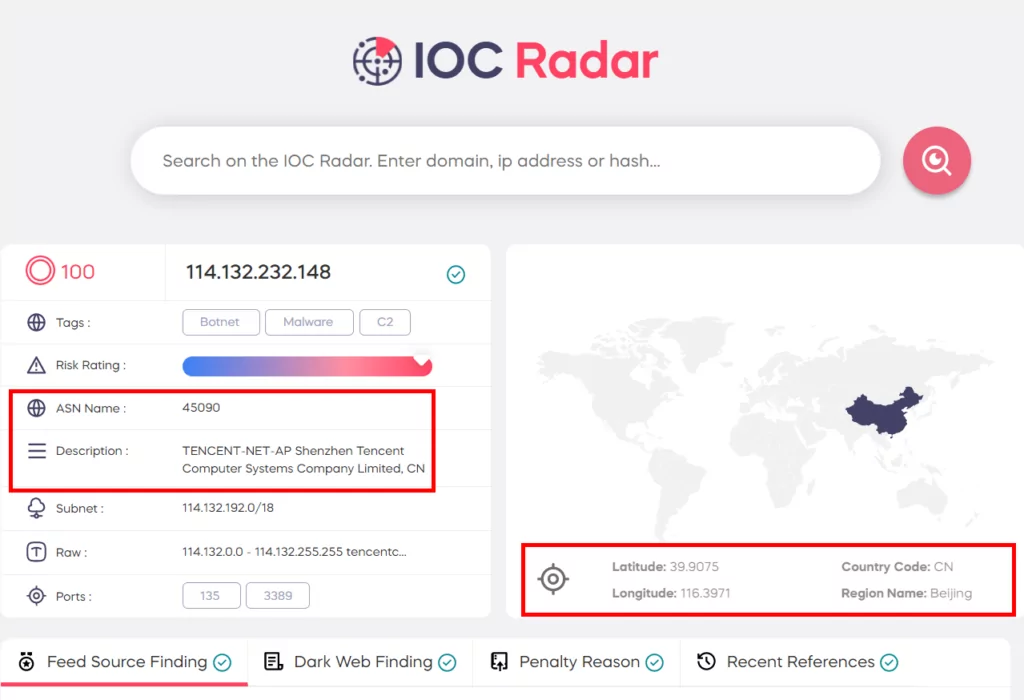
Apart from the SOCRadar Platform, you can easily access ASN, country, and other information using IOCRadar, and you can easily access supporting information for your research from a single page.
Conclusion
This research paper presents a general analysis of open-source RATs used by APT groups. Our review shows that cyber attackers often prefer these tools in their sophisticated attacks.
The research reveals that cybersecurity professionals need to have the appropriate skills and tools to diagnose and analyze RAT-based attacks. This highlights the need to invest in advanced analysis methods and threat intelligence platforms to understand and detect RATs used by threat actors. It is also known that APT groups exploit zero-day vulnerabilities in their attacks, and vulnerability scanning and patching processes are of great importance. It is possible that vulnerabilities can be exploited and result in the infection of targeted RATs or other malware. Therefore, as part of an organization’s cybersecurity strategy, continuous vulnerability scans should be conducted and identified vulnerabilities should be patched quickly. In addition, cybersecurity teams should continuously monitor security threats to detect zero-day attacks by APT groups and keep defense measures up to date. Vulnerability scanning and patching processes are critical to minimizing an organization’s vulnerabilities and becoming more resilient to potential attacks. In addition, it is also important to implement security measures such as up-to-date and effective use of anti-virus programs, use of EDR (Endpoint Detection and Response) solutions, tightening access control or authorization privileges, IDS/IPS (Intrusion Detection and Prevention System). In addition, raising cybersecurity awareness and providing the necessary training to employees also play a critical role in preventing attacks.
The importance of end-user training and awareness is clearly seen in phishing attacks, which are preferred as the beginning of an attack. Users trained against social engineering attacks can reduce the risk of being the target of RAT-based attacks. Informing users about potential dangers and raising awareness of appropriate security measures can help organizations create a more secure environment.
Finally, the necessity of an effective incident response process should be emphasized. If malware such as RATs is detected, ensuring a fast and effective response is important. A good incident response process is critical to quickly stop attacks, isolate affected systems and identify the attack’s origin. As a result of these results, cybersecurity intelligence firms and defense teams should consider this research paper to understand the threats of RATs and take countermeasures. At the same time, the cybersecurity community needs to work together to continuously share information to identify and analyze new threats and develop defense strategies.
As an Extended Threat Intelligence (XTI) company, SOCRadar provides such critical information to its customers as soon as possible and informs them to take the necessary measures.

































