
Penetration Testing vs. External Attack Surface Management vs. Vulnerability Management
In an environment where attack methods are diversified, threat actors are constantly improving, massive attacks, data breaches, digital frauds, and ransomware attacks continue unabated. And it becomes more challenging to secure cyberspace.
To cope with these challenges, we should evaluate the possible cybersecurity solutions and invest in the options with the best ROI (return on investment). But first, we should learn the basics of cyber security.
When we look at the provision of cyber security, we come across the following essential concepts: Vulnerability, Threat, Risk, and Security Measures. Let us have a look at the definitions of those terms.
Return to Basics
- A vulnerability is a weakness that threat actors can exploit to gain unauthorized access to your digital assets. After the exploitation, they can run malicious code, install malware, and even steal sensitive data.
- A threat is a malicious activity that exploits the vulnerabilities to damage, reveal or steal sensitive data or disrupt the availability of digital assets.
- Risk is the likelihood of damage or loss when a threat exploits a vulnerability. It is also formally defined as a product of impact and possibility.
- Security measures, also known as security controls, are methods used to reduce the risks to which digital assets are exposed.
While securing cyberspace, practitioners utilize numerous security measures to reduce risks. Some of these measures have both similarities and differences.
In this article, we will focus on three of these measures; Vulnerability Management (VM), Penetration Testing (PT), and External Attack Surface Management (EASM). We will talk about what these three methods mean, their scope, similarities, and differences.
What is Vulnerability Management?
Vulnerability Management is a process that continuously identifies, evaluates, prioritizes, manages, and tries to reduce the impact of vulnerabilities.
In this process, practitioners continually run scheduled vulnerability scans on the scope of assets to detect newly emerged vulnerabilities and apply various patch and remediation procedures. While prioritizing patches, they use vulnerability scoring schemes – such as CVSS (Common Vulnerability Scoring System) – and risk calculations.
In vulnerability management, asset scope is defined beforehand, and there is no additional asset discovery beyond this scope. It is usually a known IP range of the company.
After identifying the vulnerabilities, there is no exploitation phase to validate them. Some detected vulnerabilities are not exploitable so false positives may arise.
To summarize, vulnerability management provides real-time visibility for our pre-determined known assets.
What is Penetration Test?
A penetration test is a set of simulated cyber-attacks to detect vulnerabilities that attackers can exploit and gain unauthorized access to systems and/or data. This test is conducted within a particular scope and permissions.
Like Vulnerability Management, it is conducted within a previously defined scope and with permission. But the coverage is more limited than vulnerability management.
There are several types of Penetration Testing based on prior knowledge about the system being tested; black, white, and gray box tests. While testers have no prior knowledge about the system in a black box test, they may have the source code in a white box one. And in a gray box test, they may have some privilege on the system beforehand.
Penetration testers attempt to breach the system’s security through the same tools and techniques as an adversary might. These tools might be either automated or manual.
Pentesters exploit detected vulnerabilities and research specific attack vectors toward the organization. Therefore, there are no or few false positive findings. However, it is a one-time activity that occurs between one and four times a year and does not provide real-time visibility of the attack surface.
In summary, penetration testing verifies the efficacy of defensive mechanisms and guides patching/mitigating detected vulnerabilities and updating security policies.
External Attack Surface Management
Attack surface is everything adversaries can discover and abuse as they research the Internet for the target organization.
We can reduce the attack surface by proactively mapping the digital footprint, monitoring online channels for attack indicators, quickly defusing identified threats, and protecting customers, employees, and networks.
External Attack Surface Management is a continuous process that detects and manages risks in Internet-facing assets.
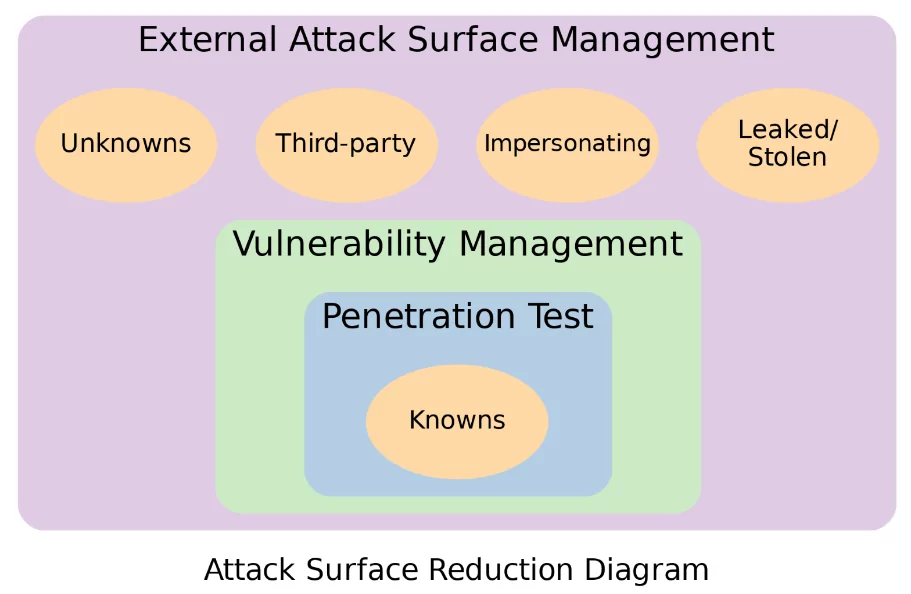
In this process, all known or unknown assets (on-premises, cloud, subsidiary, third-party, or partner environments) are detected from the attacker’s perspective, a view from outside the organization. We can only protect the attack surface once all assets that attackers can see are visible.
Unlike Vulnerability Management and Penetration Testing, a distinct continuous phase is vital; asset discovery, in which we can find the unknowns.
Therefore, asset scope is not limited to previously defined ones; unknown assets are also included in our precious digital footprint.
Like vulnerability management, we don’t consider the exploitation of the findings. Thus, there might be some inevitable false positives. But these false positives can be excused for the sake of complete visibility.
External Attack Surface Monitoring covers known and unknown digital assets operated by your organization or authorized third parties. However, the attack surface is beyond that and includes malicious/fraudulent assets created by cyber criminals and stolen/leaked sensitive data of employees or customers. Therefore, with EASM, we also monitor;
- Impersonating assets that are used for phishing or brand abuse,
- Stolen and leaked account details or sensitive data of employees or customers.
Eventually, the risks that may arise are minimized by managing the vulnerabilities in those detected assets.
Similarities and Differences
Vulnerability scanning and assessment tools used in the VM process are also used in PT and EASM.
The VM and the EASM processes have similar phases; detection, evaluation, prioritization, and remediation. Continuous asset discovery is the primary distinction of EASM.
VM and EASM are continuous activities, while PT is a one-time assessment. Therefore, VM and EASM provide real-time visibility, while PT does not.
In VM and PT, we evaluate the system from the external or internal network or somewhere in between. However, at EASM, we evaluate the system as a threat actor – from an external point of view.
In EASM and VM, we do not exploit detected vulnerabilities, but in PT, we assess through exploitation.
We can validate the vulnerabilities with exploitation in PT only. Therefore, there are fewer False Positive findings than in the other duo.
In EASM, we do not limit ourselves to the assets we know and discover unknown assets. However, there is no asset discovery on VM and PT.
As shown in the attack surface reduction diagram, only known assets are in the scope of VM and PT. At the same time, we consider known, unknown, third-party, impersonating, and stolen/leaked assets in EASM.
A summary of the similarities and differences is shown in the table below.
| Vulnerability Management | Penetration Test | External Attack Surface Management | |
| Schedule | Continuous | One time | Continuous |
| Real-time visibility | Yes | No | Yes |
| Exploitation | No | Yes | No |
| Asset scope | Known | Known | Known, unknown, third-party, impersonating |
| Asset discovery | No | No | Yes |
| False positives | Some | Very few | Some |
| Phases | Detection, evaluation, prioritization, and remediation | Planning, discovery, exploitation, reporting, remediation, retesting | Detection, evaluation, prioritization, and remediation |
| Evaluation perspective | External, internal, or somewhere in between | External, internal, or somewhere in between | External |
| Tooling | Automated | Automated and manual | Automated |
Conclusion
Each of these measures provides mutually exclusive benefits that the other does not. And utilizing each is essential for complete security. For example, while vulnerability management focuses on known vulnerabilities, penetration testing can find unknown in-house product vulnerabilities, and external attack surface management can find unknown vulnerable assets.
However, if we have a limited budget, we can prioritize based on the risk formula – impact multiplied by likelihood. Remember, if we cannot calculate the entire risk, we cannot take appropriate action.
We can determine the risk score of all our visible or previously invisible assets with EASM;
- With the increase of the attack surface visibility, the risk’s impact factor increases.
- Adversaries seek the path of least resistance to entering the organization. Therefore, the probability of an attack will be at its peak for assets exposed to the Internet.
As a result, EASM should be considered the first choice among the three options.
How Can SOCRadar Help You with External Attack Surface Management?
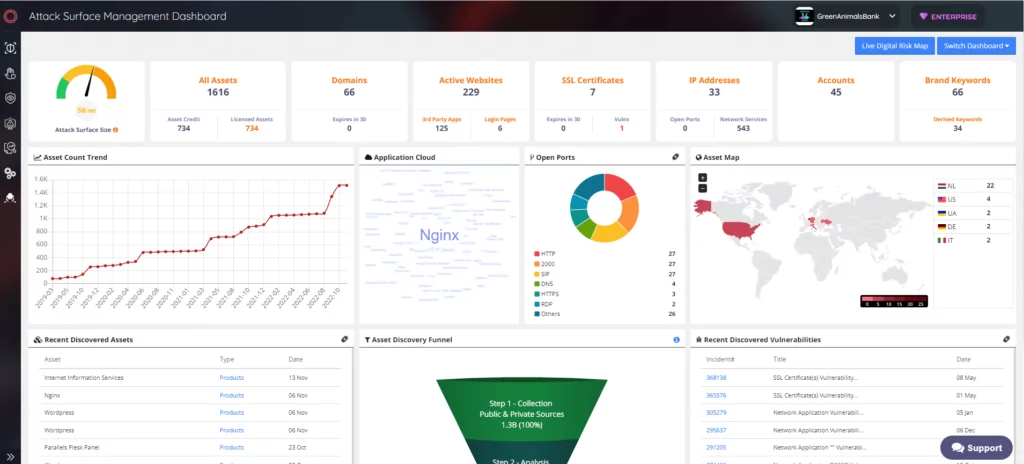
EASM helps customers gain additional visibility and context regarding the severity of unknown external-facing digital assets in an automated manner. Through SOCRadar’s advanced internet-wide monitoring algorithms, AttackMapper provides security teams with direct visibility into all internet-facing technological assets in use as well as assets attributed to IP, DNS, Domain, and cryptographic infrastructure.
SOCRadar EASM solution, AttackMapper, detects the digital footprint of companies using only the main domain address information and can automatically extract the asset inventory by classifying it.
It regularly monitors your organization’s assets and detects changes related to them. Monitoring the assets that make up the attack surface enables us to follow the attacker and prevent possible attacks.
Also, it can provide information to security teams about missing security configurations that occur within the company, critical open ports, expired SSL certificates/domains, etc.
SOCRadar provides the following modules as a service;
- Critical Port Detection: Get notified when a critical port is exposed, which threat actors often target
- Digital Footprint: Get a holistic and up-to-date view of your public-facing digital assets
- Digital Asset Monitoring: Keep a watchful eye on your domains, subdomains, WHOIS info, and IP addresses
- DNS Monitoring: Safeguard and monitor your DNS infrastructure for threats and misconfigurations
- Vulnerability Detection: Continually monitoring your attack surface to cross-reference to vulnerabilities
- SSL Certificates Monitoring: Keep track of your SSL/TLS certificates for expiry, validity, or vulnerability
- Website Monitoring: Keep your brand reputation intact by early spotting of issues like web defacement
- JavaScript Threat Monitoring: Monitoring malicious JavaScript injection to identify web skimming attacks rapidly



































