
Popular Platforms’ User Data Leaks Could Boost Future Attack Campaigns
The holiday season begins with large-scale user data leaks on popular social platforms. Given the sensitivity of the information they expose, the leaked data may end up being used in other attacks.
To take proper precautions, end users should always be aware of breaches and their scope in leaks.
Near 500 Million Phone Numbers on Sale
In mid-November, a threat actor offered 487 million WhatsApp users’ phone numbers for sale on a breach forum. The database was allegedly recent, dating from this year, and contained phone numbers from users in 84 countries. It is unclear how the threat actor obtained access to these records, though it is likely scraped.
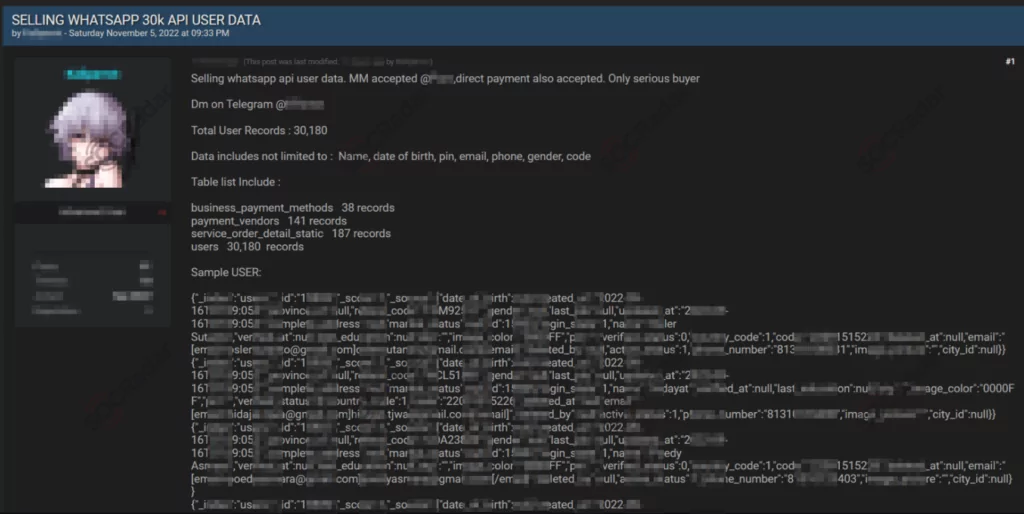
The threat actor sold the records by separating the countries into datasets; most records were from Egypt, Italy, and the U.S., while they offered phone numbers from the United States for $7000.
The Risk Persists
The post was later removed, but other posts began to appear, leaking similar information. Some records may have already been sold or used, which increases the possibility of following phishing campaigns. Attackers may deceive users via phone calls or SMS messages using the exposed phone numbers.
Another well-known application, Twitter, experienced a significant data leak in July, which is still impacting.
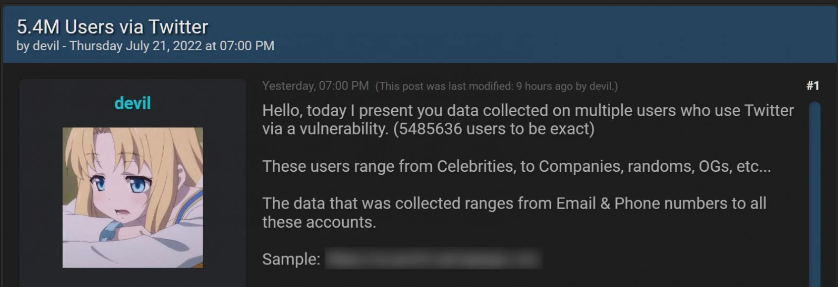
On a hacker forum, a threat actor revealed that they had obtained over 5.4 million Twitter user records with private information by exploiting an API flaw that had been fixed in January. The threat actor started selling the personal data for $30,000 in July.
Hackers Scrape Private Data
This information was gathered in December 2021 by utilizing a Twitter API flaw that was made public through the HackerOne bug bounty program.
The flaw allowed users to submit their phone numbers and email addresses to access the Twitter ID that went along with them. The threat actors could then use this ID to scrape the account’s public data to produce a user record that contained both private and public data.
Total of 7 Million Twitter Users Records Leaked
Nearly 7 million Twitter profiles with private information were found overall, including the 5.4 million records for sale and an additional 1.4 million suspended user profiles that were gathered using a different API.
Pompompurin, the owner of the Breached hacking forum, claimed that this second data dump was only privately distributed to a select group of individuals and was not sold.
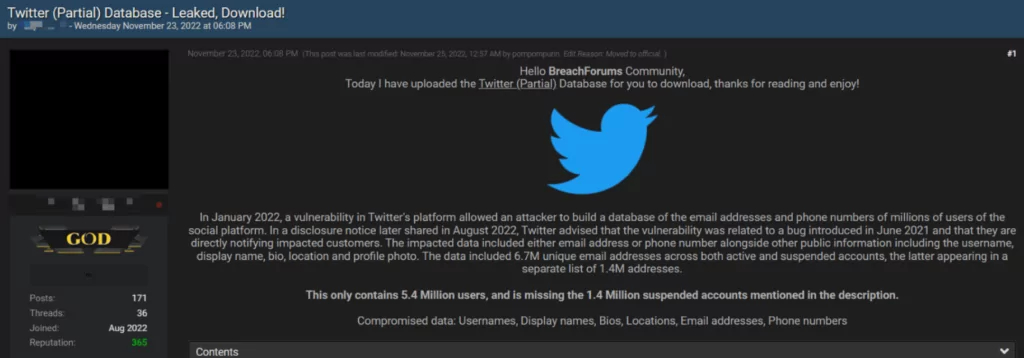
Although it is troubling that threat actors gave away 5.4 million records, it is also claimed that they used the same vulnerability to create a much larger data dump.
This data dump may contain tens of millions of Twitter records, including public data like verified status, account names, Twitter IDs, bios, screen names, and personal phone numbers.
It is claimed to contain over 17 million records, but this could not be verified.
You should disregard and delete any emails that prompt you to log in to a non-Twitter domain and claim that your account has been suspended, there are login problems, or you are about to lose your verified status. These emails are likely phishing attempts.
Various Attacks are Possible
Although the stolen data may cause financial and reputational damage to organizations, it may also cause harm to everyone if it contains PII (personally identifiable information). Threat actors can use leaked phone numbers, emails, and similar PII to select suitable phishing victims or use them to impersonate.
That creates an attack vector for phishing attacks to provide initial access or by using it to abuse the trusted relationship. A threat actor who obtains your personal information can impersonate you, reach other internal sources and gain an in-house foothold with a malicious attachment in a phishing email. They can sell your leaked contact information, paving the way for you to be exposed to many phishing attacks.
Unfortunately, the dangers are not limited to these. They also endanger your accounts connected to your leaked email address, especially the ones using the same or similar passwords. Even if your password is complex, it can be added to the threat actors’ word lists and can accelerate your password to be cracked.
How Can SOCRadar Help Protect Your Organization?
In the era of GDPR, personally identifiable information (PII) is turning into a valuable target. The number of data breach attempts increased as malicious actors threatened the GDPR fine, which could be up to 4% of global turnover or €20 million.
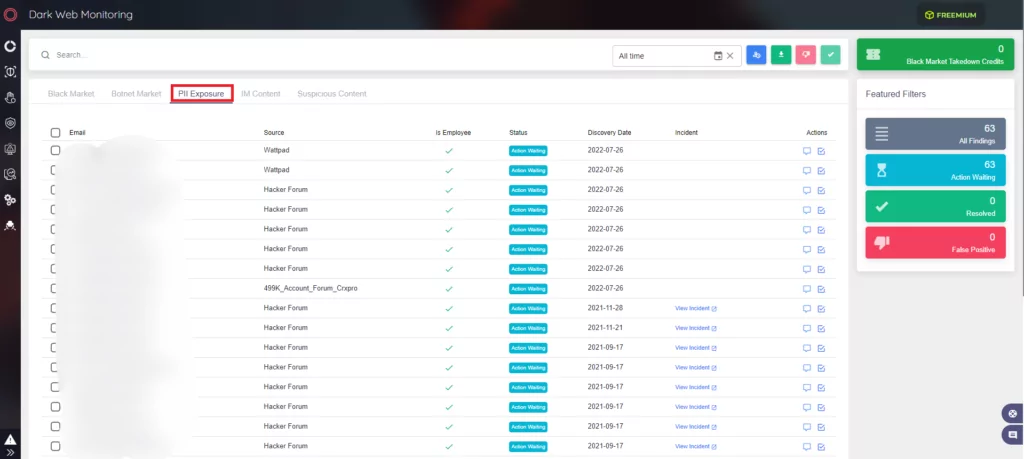
SOCRadar monitors the entire internet for personally identifiable information (PII), including the most recent credit card numbers and account credentials relevant to your business. This information is delivered by searching a wide range of Internet sources (surface and deep/dark web) to safeguard your business against fraud and identity theft.
The CEO, CFO, and other key executives of your company are the main targets of threat actors. Limiting harm in both the cyber and physical spheres requires constant monitoring for exposed personal information or the impersonation of important executives. With the SOCRadar VIP Protection module, security teams can check whether C-suite people’s critically important personal email addresses are listed anywhere in the expanding database of significant global breaches that may be searched for by adversaries.



































