
Top 20 Free APIs for Cybersecurity: Threat Intelligence, Malware Analysis & More
APIs matter because they serve as the glue that connects different software applications, enabling seamless communication and data exchange between systems. They simplify integration, allowing developers to build on top of existing functionalities rather than reinventing the wheel, which accelerates innovation and enhances efficiency across the digital ecosystem.
APIs are fundamental to cybersecurity as they enable seamless communication and integration between security tools and systems, allowing organizations to automate threat detection and response. By standardizing how data is exchanged, APIs help security teams to quickly identify vulnerabilities, orchestrate countermeasures, and maintain robust defenses against evolving threats.
- Enhanced Integration and Automation: APIs facilitate the integration of various security solutions, allowing for automated, real-time threat intelligence sharing and rapid incident response.
- Streamlined Security Monitoring: With APIs, security systems can continuously exchange data, improving the visibility across networks and enabling proactive vulnerability management.
By focusing on these key factors, we aim to provide you with a comprehensive guide that not only lists free APIs but also highlights why they are the right choices for your projects.
Threat Intelligence APIs
1. AbuseIPDB

AbuseIPDB is a community-driven database and reporting platform that aggregates information on such as hacking attempts, spam, and other forms of cyber abuse. It allows users, security professionals, and organizations to both report and look up IP addresses associated with malicious activities. AbuseIPDB offers a centralized resource to help identify and mitigate threats from known bad actors on the internet.
AbuseIPDB API Capabilities:
- Detailed IP address verification and assessment
- Comprehensive reporting system including bulk reports
- Blacklist management
2. BinaryEdge.io

BinaryEdge is a cybersecurity company that specializes in providing data-driven threat intelligence services. It operates by scanning the internet and mapping out various digital infrastructures, like devices, services, and technologies, across the globe. BinaryEdge collects data on exposed systems, vulnerabilities, and other potential security risks, which organizations can then use to improve their security posture.
BinaryEdge API V2 Capabilities:
- IP Intelligence:
- Query current and historical data about specific IP addresses
- Perform advanced searches across various IP addresses
- Torrent Monitoring:
- Track torrent activity associated with specific IP addresses
- View historical torrent data for targeted IPs
- Search torrent information with custom parameters
- Vulnerability Assessment:
- List of CVEs that might affect a specific IP address
- Domain Intelligence:
- Discover subdomains for a target domain
- Retrieve DNS records for domains
- Find domains associated with specific IP addresses
- Perform comprehensive domain enumeration
- Generates a list of homoglyphs for a base domain
- Sensor Data:
- Retrieve details about a scanner. It will list recent events from the specified host, such as the details of scanned ports, payloads and tags.
- Get events based on a query.
- Get a list of IPs that have been associated with a specific TAG.
3. EmailRep

EmailRep is a service that provides reputation intelligence for email addresses, helping to identify whether an email address is associated with malicious or suspicious activity. EmailRep provides comprehensive email risk assessment by analyzing over one hundred data points from diverse sources. These include social media and professional networking profiles, dark web credential breaches, phishing intelligence, spam databases, domain reputation metrics, deliverability statistics, and numerous other indicators to accurately evaluate the risk profile of any email address.
EmailRep Alpha Risk API Capabilities:
- The API evaluates reputation scoring and flags suspicious or risky email addresses based on multiple risk indicators. It tracks malicious activities like phishing or fraud, distinguishing between recent incidents (within 90 days) and historical patterns. The system monitors credential leaks and data breaches, providing first and last seen dates for suspicious activities.
- Domain analysis includes verification of domain existence, reputation scoring, age assessment (identifying domains created within the last year), and flagging of suspicious TLDs. The API detects spam behavior, free email providers, and disposable email services. Email deliverability is assessed through verification of valid MX records, accept-all policies, and actual deliverability status.
4. Pulsedive

Pulsedive Threat Intelligence is a cybersecurity platform that provides threat intelligence data on Indicators of Compromise (IOCs) such as IP addresses, domains, and URLs. It offers a free community-driven database as well as premium threat intelligence solutions for organizations and security professionals.
Pulsedive API Capabilities:
Core Data Types:
- Indicator Data: Comprehensive information about domains, IPs, URLs including risk scores, technical details, and relationships
- Threat Data: Intelligence about identified threats including news references and associated indicators
- Feed Data: Information from threat intelligence feeds and their linked indicators
Key Capabilities:
- Rich Technical Intelligence: Access to DNS records, WHOIS data, SSL certificates, HTTP headers, web technologies, and more
- Risk Assessment: Risk scores, risk factors, and identification of risky properties
- Geolocation: Physical location data for relevant indicators
- Visual Evidence: Screenshots available for upgraded tiers
Core Functions:
- Search: Pivot across indicators, threats, and feeds using almost any data point
- Scan: Perform on-demand passive or active scans of hosts to retrieve live data
5. ThreatMiner

ThreatMiner is an open-source threat intelligence platform that helps cybersecurity researchers and analysts gather and analyze threat data. It provides information on Indicators of Compromise (IOCs), such as domain names, IP addresses, SSL certificates, malware samples, and passive DNS data.
ThreatMiner is useful for threat hunting, malware analysis, and incident response, as it aggregates data from multiple sources to provide contextual insights. Analysts can use it to track threat actors, correlate indicators, and understand the infrastructure used in cyber attacks.
ThreatMiner API Capabilities:
- Multi-indicator Threat Intelligence: Provides detailed information on domains, IPs, malware samples, hashes, SSL certificates, and more.
- Domain Intelligence: Offers WHOIS data, passive DNS information, related URIs, connected malware samples, subdomains, and report tagging for domains.
- IP Address Analysis: Delivers WHOIS details, passive DNS records, URIs associated with IPs, related malware samples and SSL certificates.
- Malware Sample Analysis: Provides comprehensive sample metadata, HTTP traffic analysis, host connections (domains/IPs), mutants, registry keys, antivirus detections, and report tagging.
- SSL Certificate Intelligence: Maps SSL certificates to hosts.
- Email Investigation: Offers reverse WHOIS lookups to discover domains associated with specific email addresses.
- AV Detection Correlation: Allows searching for samples based on antivirus detection names and associated threat reports.
SOCRadar’s Offerings
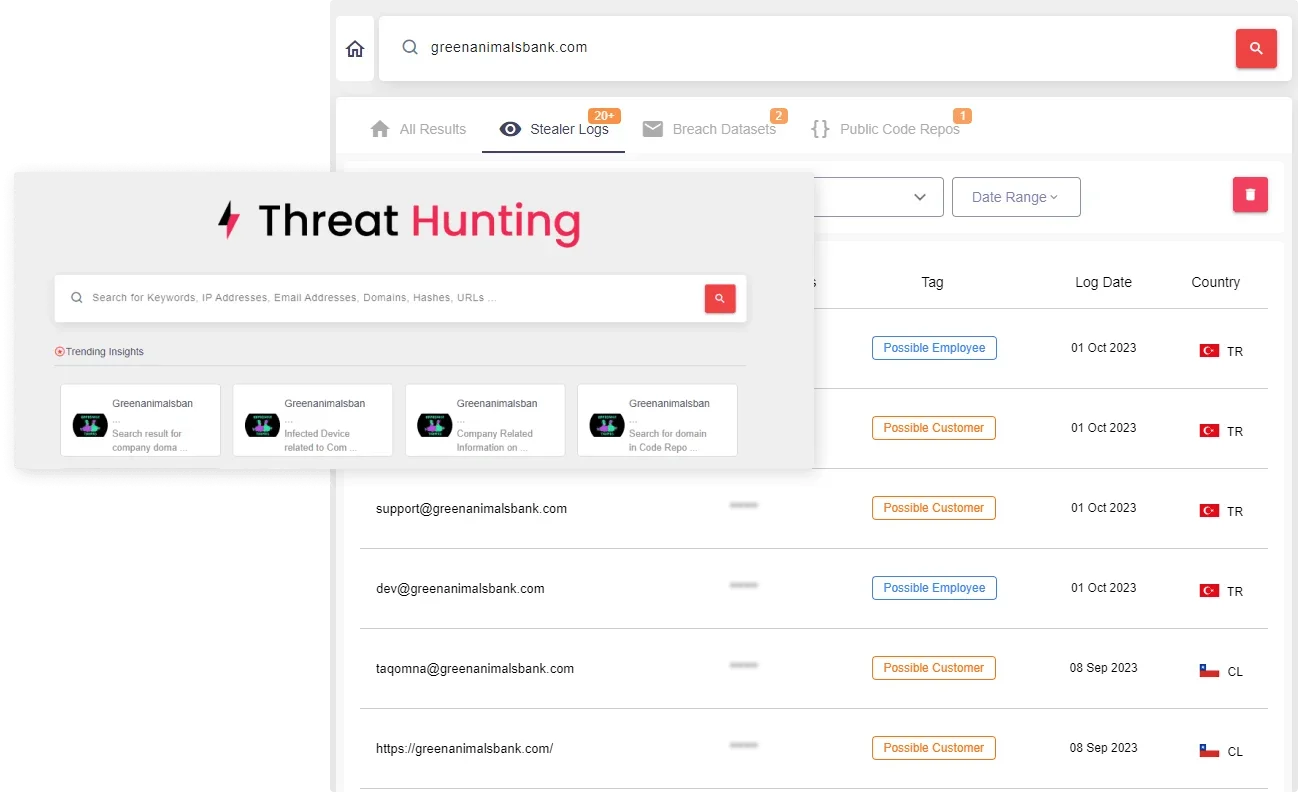
SOCRadar Threat Hunting Module
SOCRadar Threat Intelligence API Capabilities:
- Threat Hunting Rules Download API:
- Allows downloading Yara and Sigma rules content
- Designed for streamlined access to threat hunting rules
- Threat Hunting Rules Search API:
- Enables searching and filtering through available threat hunting rules
- Returns Yara and Sigma rules matching specified criteria
- Supports comprehensive filtering options including:
- Rule type filtering
- Source type filtering
- Tag-based filtering
- Date range filtering (start_date and end_date)
- Includes pagination support (page and limit parameters)
- Core Benefits:
- Enhances user experience through programmatic access to threat intelligence
- Provides automation capabilities for threat hunting workflows
- Enables integration of SOCRadar’s threat intelligence into existing security infrastructure
- Helps users maximize value from the SOCRadar platform
SOCRadar CTI Threat Investigating API Capabilities:
- Provides access to the latest Threat Hunting results from the SOCRadar platform
- Delivers key threat intelligence data including:
- Breach Datasets
- Stealer logs
- IP Risk Scores
- Additional threat intelligence data
- Returns data for a three-month lookback period
- Supports date-based filtering through start_date and end_date parameters
- Requires queries to be limited to three-month periods for optimal results
- Enables targeted threat intelligence searches through the query parameter
- Designed for cybersecurity teams to investigate potential threats and vulnerabilities
SOCRadar Surface Web Monitoring API Capabilities:
- Provides comprehensive access to all data within the Surface Web Monitoring page
- Enables users to submit new monitoring requests programmatically
- Allows for automated monitoring of specified web content or assets
- Facilitates retrieval of monitoring results through API integration
- Supports flexible data filtering using multiple parameters:
- Pagination support via ‘page’ parameter
- Custom search functionality
- Date range filtering (start_date/end_date)
- Record status tracking and filtering
- Status reason categorization
- Alarm status monitoring
- Source-based filtering
- Takedown pending status tracking
- Results can be accessed via both the platform interface and email notifications
- Designed for seamless integration with existing security workflows and systems
SOCRadar Threat Analysis API Capabilities:
- Provides threat intelligence analysis through multiple endpoints
- Calculates a “trust score” (0-100) for entities based on SOCRadar’s threat feed evaluations
- Offers three main API endpoints:
- Trigger Threat Analysis: Initiates a new analysis for a specified entity
- Get Triggered Threat Analysis List: Retrieves a list of previously triggered analyses
- Get Threat Analysis Result: Obtains detailed results for a specific analysis
- Supports parameters for customization:
- Enables integration of SOCRadar’s threat intelligence capabilities into security workflows and platforms
- Allows organizations to automate threat assessment of various entities as part of their security operations
SOCRadar Threat Feed IOC API Capabilities:
- Provides over 130 Intelligence on Compromise (IoC) feeds, including Shodan, DDoS, Botnet C&C, ransomware groups, APT groups, and Log4j attackers
- Delivers approximately 160,000 current IoCs daily with near 100% reliability and minimal false positives
- Updates feeds daily and purges outdated IoCs weekly to maintain accuracy
- Implements rigorous validation processes with whitelist policies containing over 50 million entries
- Allows users to create custom feed lists by selecting up to 10 feeds from 115+ available options
- Enables users to modify sources in their collections without requiring reintegration
- Features country filters for creating region-specific rules and IoC type filters (SHA256, URL, Hash, Domain, IP, etc.)
- Supports customer-provided threat feed sources that undergo SOCRadar’s verification and whitelist checks
- Offers multiple format options (JSON, CSV, raw) for integration with various security products
- Provides multiple integration methods: Endpoint API, MISP Server, or TAXII Server
SOCRadar Dark Web Monitoring API Capabilities
- Dark Web Monitoring – Allows detection of company account leaks with filtering options by date range, leak type, and pagination controls.
- PII Exposure (Leak) Detection – Enables retrieval of personal information exposures related to your company from leaked data sources.
- Blackmarket Data Access – Provides visibility into data being shared on black market forums with date filtering and pagination.
- Suspicious Content Monitoring – Offers access to suspicious content detected across monitored channels with customizable date ranges.
- Botnet Intelligence – Delivers botnet-related data that can be filtered by date range and specific leak types.
- IM Content Analysis – Enables access to Threat Hunting results including breach datasets, stealer logs, and IP risk scores with keyword-based searching.
- Request Management – Supports the ability to make and track specific monitoring requests using email identifiers, blackmarket IDs, and notes.
- Customizable Parameters – Most endpoints support pagination (limit/page) and date range filtering (start_date/end_date) for targeted intelligence gathering.
SOCRadar Dark Web Monitoring API V2 Capabilities:
- Key Capabilities:
- Comprehensive Dark Web Intelligence: Monitor five distinct sources of dark web data in real-time
- Customizable Queries: Filter and search data using consistent parameters across all endpoints
- Time-Based Analysis: Track threats over specific time periods with start/end date parameters
- Alert Management: Monitor and manage security alerts with alarm status tracking
- Pagination Support: Efficiently retrieve large datasets with page and limit controls
- Record Status Tracking: Track the status and resolution of security incidents
- Historical Data Access: View historical records with the includeHistory parameter
- Data Sources Available:
- Botnet Data: Monitor compromised credentials and systems in botnet communications
- Black Market: Track stolen data, credentials, and services offered on dark web marketplaces
- Suspicious Content: Identify potentially threatening content across dark web sources
- PII Exposure: Detect exposed personally identifiable information, with special flagging for employee data
- IM Content: Monitor instant messaging platforms for security threats and data leaks
Domain & URL and IP Security APIs
6. Google Safe Browsing

Google Safe Browsing is a security feature that helps protect users from malicious websites, phishing attacks, and malware. It works by maintaining a constantly updated list of unsafe websites and warning users when they attempt to visit such sites through Google Search, Chrome, and other supported browsers.
Safe Browsing API Capabilities:
- Check pages against our Safe Browsing lists based on platform and threat types.
- Warn users before they click links in your site that may lead to infected pages.
- Prevent users from posting links to known infected pages from your site.
7. PhishTank

PhishTank is a community-driven platform that collects, verifies, and shares data on phishing websites. It serves as a centralized repository where users can submit suspected phishing URLs, and the community helps validate these reports. This collaborative approach provides an up-to-date and reliable resource for identifying phishing threats, making it easier for organizations and developers to defend against such attacks.
PhishTank API Capabilities:
- Checks URLs against PhishTank’s phishing database to determine if they are known phishing sites
- Offers direct links to detailed phishing reports
- Helps organizations protect users by identifying and avoiding known phishing threats
8. URLhaus

URLhaus is a threat intelligence initiative developed by abuse.ch that focuses on collecting, tracking, and sharing information about URLs used for malware distribution. It serves as a centralized repository of known malicious URLs, providing cybersecurity professionals with valuable insights into emerging threats and trends in cyber attacks. By aggregating data on harmful websites, URLhaus helps organizations proactively block and mitigate risks associated with malicious content.
URLhaus API Capabilities:
- Database dump (CSV):
- Depending on the needs two type of dumps can be gathered
- A full dump which is a dump of active malware distribution sites only.
- This contains URLs that are either actively distributing malware or that have been added to URLhaus within the past 90 days.
- A dump of any URL added to URLhaus within the past 30 days.
- A full dump which is a dump of active malware distribution sites only.
- Depending on the needs two type of dumps can be gathered
- Daily MISP Events: You can download URLhaus IOCs as daily MISP events.
- DNS Response Policy Zone (RPZ): By using an DNS Response Policy Zone (RPZ), you can block the resolution of certain domain names on your DNS resolver.
- Snort / Suricata IDS ruleset: If you are using a network intrusion detection and prevention systems (IDS / IPS) like Snort or Suricata, you may use the URLhaus IDS Ruleset to identify network traffic towards known malware URLs.
- hostfile: Some commercial and open source security software (such as Pi-hole) can block access to domain names based on the host file format. For this purpose, URLhaus offers a list of domain names associated with malware URLs.
- Plain-Text URL List (URLs only): The Plain-Text URL List is a dump of all malware URLs known to URLhaus. It does not contain anything else than one URL per line, which is useful if you want to use the URLhaus dataset as an IOC (Indicator Of Compromise).
- Collected Payloads (CSV): URLhaus regularly checks the content served by malicious URLs that are known to URLhaus.
- ClamAV signatures: URLhaus generates a ClamAV signature database which gets updated once per minute. This allows you to add almost real time detection of malware distribution sites on your email gateway / spam filter.
9. urlscan.io

urlscan.io is a web security tool and search engine for scanning and analyzing URLs. It allows users to inspect websites for potential threats, phishing attempts, and malicious activities. When a URL is submitted, urlscan.io retrieves the page, captures its structure, and provides insights such as:
URLscan.io API Capabilities:
- URL Scanning: Submit any URL for automated analysis and scanning
- Public/Private Results: Option to keep scan results private or make them publicly accessible
- Results Retrieval: Access detailed scan results for any previously completed scan
- Search Functionality: Search through the database of previous scans with custom queries to find relevant information
10. CriminalIP.io

CriminalIP.io is a cybersecurity intelligence platform that provides threat intelligence, attack surface monitoring, and digital asset tracking. It helps users investigate suspicious IP addresses, domains, and devices across the internet. The platform is often used by security researchers, law enforcement, and businesses to detect potential cyber threats, vulnerabilities, and malicious activities.
Criminal IP API Capabilities:
IP Address Intelligence:
- Identification of malicious IPs and associated threats
- Privacy threat detection and analysis
- Banner data retrieval
- DNS server safety verification
- Suspicious activity monitoring
- Comprehensive IP data retrieval and summary reports
Domain Intelligence:
- Full and lite domain security reports
- Domain scanning (public and private options)
- Quick analysis for hash verification, malicious activity, and trusted domains
11. IP ASN History (D4 Project – CIRCL)

According to their website, “The project’s goal is to provide a constant and reliable view of Distributed Denial of Service (DDoS) and malicious activities and disseminate the information within networks of Computer Security Incident Response Teams (CSIRTs) by building a large-scale distributed DDoS sensor network (D4 platform) and relying on existing information sharing platforms for dissemination.”
IP ASN History API Capabilities:
- IP Address Lookup: Query historical ASN information for IPv4 addresses
- Historical Data Access: Retrieve ASN and prefix information for specific dates
- Caching Options: Can query with a special parameter to use only cached data
- Latest Data Retrieval: Can request most recent ASN information without specifying dates
SOCRadar’s Offerings
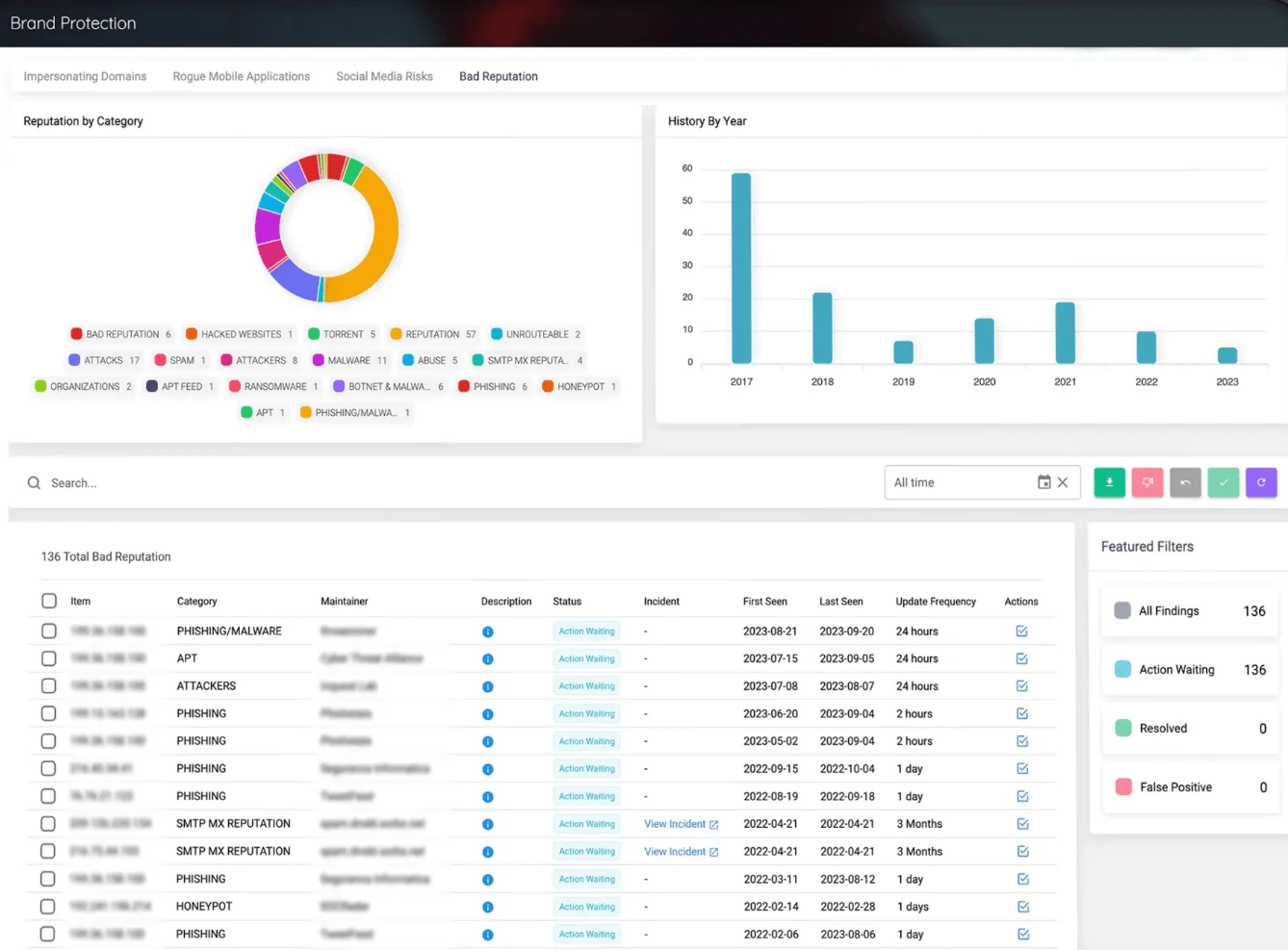
SOCRadar Brand Protection Module
SOCRadar Digital Footprint API Capabilities:
- Asset Discovery and Management:
- Retrieve comprehensive digital asset inventory with customizable parameters (filtering, sorting, pagination)
- Access and manage your company’s complete digital footprint
- Cloud Infrastructure Monitoring:
- Add and track cloud buckets across different platforms
- Specify access states and service configurations for cloud resources
- Data Quality Control:
- Mark assets as false positives with annotation capabilities
- Add contextual notes to flagged assets
- Asset Registration:
- Manually register various digital assets including domains, IP addresses, and websites
- Add technical details like SSL certificates, login pages, and domain types
- Monitoring Controls:
- Enable or disable monitoring for specific assets
- Configure monitoring settings by asset type and sub-type
SOCRadar Fraud Protection API Capabilities:
- Enables communication and information sharing between different systems about detected fraud instances
- Primarily designed for e-commerce websites and financial systems
- Main purpose is to improve security measures and reduce fraudulent activities
- Supports parameter-based filtering
Vulnerability & CVE Data APIs
12. National Vulnerability Database

NIST is a U.S. federal agency that develops and promotes measurement standards, including cybersecurity frameworks and guidelines. It is part of the U.S. Department of Commerce and is responsible for advancing technology to enhance economic security.
The NVD is a comprehensive database of publicly disclosed cybersecurity vulnerabilities, managed by NIST. It is part of the U.S. government’s cybersecurity initiative and is based on the Common Vulnerabilities and Exposures (CVE) system.
Key components of the NVD:
- CVE Entries: Each vulnerability is assigned a unique CVE identifier.
- CVSS Scores: Vulnerabilities are ranked using the Common Vulnerability Scoring System (CVSS) to indicate severity.
- Mitigation & Impact Information: NVD provides references to patches, security advisories, and mitigation strategies.
NVD API Capabilities:
- CVE Information: Access to detailed vulnerability data including CVE-ID, source identifier, publication date, modification date, and vulnerability status
- Contextual Tags: Retrieve categorization tags that provide additional context about each vulnerability
- Impact Metrics: Access comprehensive vulnerability severity ratings through CVSSv2 and CVSSv3 scoring systems
- Weakness Information: Obtain data on specific weaknesses (CWEs) that are the root causes of vulnerabilities
- Product Configurations: View detailed applicability statements showing which products are affected by each vulnerability
- Reference Resources: Access supplemental vulnerability information with categorized reference links (advisories, technical papers, media mentions)
- Official Vendor Comments: Retrieve authorized statements from vendors about vulnerabilities affecting their products
13. CVE Search (CIRCL)

The Computer Incident Response Center Luxembourg (CIRCL) is a government-driven initiative designed to provide a systematic response facility to computer security threats and incidents. CIRCL is the CERT for the private sector, communes and non-governmental entities in Luxembourg.
cve-search is a publicly accessible service operated by CIRCL, providing a web interface and an HTTP API for searching publicly known security vulnerabilities in software and hardware, along with their corresponding exposures. It aggregates data from multiple sources, including the NIST National Vulnerability Database, Common Platform Enumeration (CPE), Common Weakness Enumeration (CWE), CIRCL incident statistics and threat ranking, and toolswatch/vFeed. By integrating these data feeds, cve-search enables users to efficiently identify and analyze security threats.
CIRCL CVE Search API Capabilities:
- Browse vendor and product information: Retrieve a comprehensive list of vendors or view all products associated with a specific vendor
- Search vulnerabilities by vendor/product: Obtain detailed JSON data on all vulnerabilities affecting a particular vendor’s product
- Retrieve specific CVE details: Access complete information about any vulnerability using its unique CVE identifier
- Monitor recent vulnerabilities: Get the latest 30 CVEs with expanded information including CAPEC, CWE, and CPE data
- Access database metadata: Retrieve information about the current databases in use and their last update timestamps
14. Vulners

Vulners is a threat database and vulnerability search engine that brings together dozens of manufacturers’ vulnerability publications, exploits and other vulnerability bulletins, allowing you to track published vulnerabilities in a single place.
Vulners API Capabilities:
- Comprehensive Vulnerability Data: Provides access to detailed vulnerability information with unique identifiers and CVE references
- Classification System: Categorizes security information by vendor type and bulletin family (Unix, Exploit, etc.)
- Severity Assessment: Includes CVSS scoring metrics to understand vulnerability impact
- Source Verification: Provides direct links to original sources and references
- Technical Details: Includes source data such as code snippets for exploits and scanner bulletins
SOCRadar’s Offerings
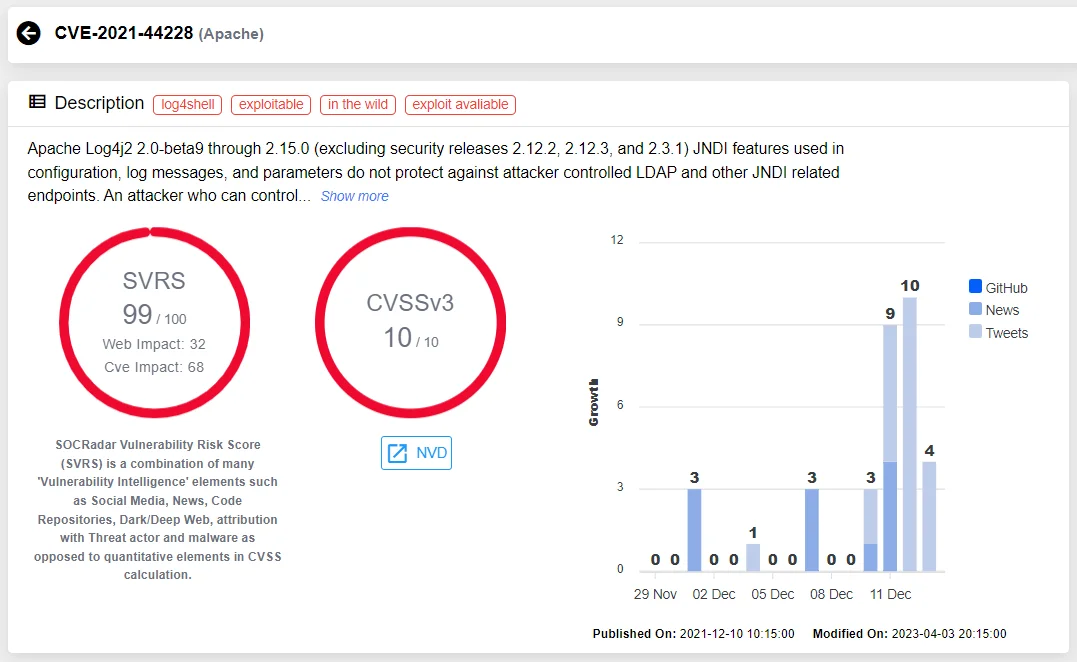
SOCRadar Vulnerability Intelligence Module
SOCRadar ASM Vulnerabilities API Capabilities:
- Vulnerability Monitoring: Obtain detailed information about vulnerability incidents affecting your company
- Time-Based Filtering: Filter vulnerability data using the start_date and end_date parameters to focus on specific time periods
- Action-Oriented: Take direct action on identified vulnerabilities through the API endpoints
- Dual-Interface Access: Access the same vulnerability data through both the API and the SOCRadar platform interface
- Incident Examination: Comprehensive examination capabilities for vulnerability incidents
SOCRadar CTI Vulnerability API Capabilities:
- Detailed CVE Information Retrieval: Access comprehensive information about specific Common Vulnerabilities and Exposures (CVEs), including related social media mentions and news.
- Advanced Vulnerability Search: Filter vulnerabilities by multiple criteria including date ranges, CVSS scores, severity ratings, exploitability status, and specific CPE identifiers.
- Remote Code Execution (RCE) Filtering: Specifically identify vulnerabilities that enable remote code execution attacks.
- Vulnerability Trend Analysis: Track and monitor vulnerability trends for better security planning and risk assessment.
- Dork Integration: Access associated dorks (specialized search queries) that could be used to identify vulnerable systems.
- CWE Filtering: Filter vulnerabilities by Common Weakness Enumeration (CWE) categories.
- IOC and Country Statistics: Retrieve indicators of compromise and geographic distribution data for specific vulnerabilities.
- Tag-Based Filtering: Group and retrieve vulnerabilities based on custom or predefined tags.
Malware Analysis & Sandbox APIs
15. VirusTotal

VirusTotal is an online service that analyzes files and URLs to detect viruses, worms, trojans, and other types of malicious content. Virus Total aggregates the scanning results from over 70 antivirus engines and various website scanners, providing a comprehensive view of potential threats. This makes it an invaluable resource for both individual users and cybersecurity professionals who need to quickly assess the safety of digital content.
VirusTotal API Capabilities:
- Submit files and URLs for comprehensive security analysis
- Retrieve detailed scan reports and threat intelligence
- Automate commentary on submitted samples
- Access VirusTotal’s extensive security database for IoC Reputation and enrichment
16. Hybrid Analysis

Hybrid Analysis is a dynamic malware analysis service that provides in-depth insights into the behavior of suspicious files and URLs. It leverages sandbox technology to execute potentially malicious code in a controlled environment, allowing security professionals to observe its actions—such as file system modifications, network communications, and process interactions. This detailed behavioral analysis helps in understanding how a threat operates and in developing effective countermeasures.
Hybrid Analysis API Capabilities:
Falcon Sandbox has a powerful and simple API that can be used to submit files/URLs for analysis, pull report data, but also perform advanced search queries. You can benefit from:
- Search functionalities
- Quick scan services
- File collection management
- Analysis capabilities
- Sandbox submission
- Sandbox report retrieval
17. Malshare
Malshare is a free, open-access repository of malware samples that serves as a valuable resource for security researchers and analysts. It collects and archives a wide array of malware from various sources, enabling users to study malicious code, understand threat trends, and develop effective detection strategies.
MalShare API Capabilities:
- Retrieve sample hashes
- Download stored malware samples directly
- Access detailed information about stored files
- Search samples by hash value, source, or filename
- Filter hash lists by specific types (MD5/SHA1/SHA256)
- View statistics on file types
- Upload new samples
- Submit URLs for automatic downloading into the collection
- Enable recursive crawling of specified URLs
- Monitor sample sources
18. MalwareBazaar (by abuse.ch)

MalwareBazaar is an open-source platform developed by abuse.ch that serves as a repository for malware samples. It enables researchers, threat analysts, and cybersecurity professionals to access and share known malware samples, facilitating deeper analysis and improved threat intelligence.
MalwareBazaar API Capabilities:
- Sample Management
- Upload malware samples for analysis
- Download specific malware samples
- Query Capabilities by Identifiers
- Search by cryptographic hash values
- Query by TLSH
- Search by imphash and gimphash
- Content-Based Queries
- Search by malware hash
- Query by detected signatures
- Find samples by specific file types
- Search for ClamAV signature matches
- Query using custom YARA rules
- Certificate Analysis
- Query by code signing certificate issuer
- Find samples by certificate serial number
- Access the Code Signing Certificate Blocklist (CSCB)
- Batch Operations
- Download hourly malware batches
- Access daily malware collections
SOCRadar’s Offerings
SOCRadar Malware Analysis API Capabilities:
- Offers real-time malware analysis capabilities through API integration
- Allows users to upload suspicious files for immediate analysis
- Handles files up to 15 MB in size
- Available specifically for Enterprise-Premium license holders
- Uses a simple interface with a single parameter (“file”) for submissions
- Enables automated security workflows through the API functionality
SOCRadar Threat Actor Malware API Capabilities:
- Access to Threat Actor Intelligence: Retrieve detailed information about threat actors targeting your company or industry
- Threat Group Profiling: Obtain comprehensive data about specific threat actor groups, their activities, and targeting patterns
- Content Filtering Options: Filter threat intelligence by date ranges, content types, and checkpoints
- Sectoral Threat Analysis: Identify threat actors targeting specific industry sectors
- Geographic Targeting Insights: Discover threat actors focusing on particular countries or regions
- Malware Attribution: Link specific malware tools to the threat actor groups that deploy them
- CVE Exploitation Tracking: Monitor which threat actors are exploiting specific vulnerabilities
- State-Sponsored Activity Identification: Recognize threat actors with suspected government backing
- Multi-dimensional Search: Combine multiple parameters to perform precise threat intelligence queries
Other Security Data & Intelligence APIs
19. HaveIBeenPwned

HaveIBeenPwned (HIBP) is a widely recognized online service that aggregates data breaches to help individuals and organizations determine if their email addresses, usernames, or passwords have been compromised. Developed by Troy Hunt, it serves as a crucial resource in the cybersecurity community by providing access to a comprehensive database of breached data, enabling users to take proactive measures against potential security threats.
Have I Been Pwned API Capabilities:
- Breach Monitoring: Search for compromised accounts across multiple data breaches by email address or domain
- Site-Specific Breach Information: Access detailed information about specific breached websites and their impact
- Stealer Log Detection: Identify if email addresses have been captured in malware stealer logs
- Paste Monitoring: Discover if sensitive data has been exposed in paste sites like Pastebin
- Subscription Management: Check and manage notification subscription status for monitored domains
- Pwned Password Verification: Securely check if passwords have been exposed in data breaches using k-anonymity
- NTLM Hash Verification: Verify if Windows authentication hashes have been compromised
- Bulk Data Access: Download complete datasets of compromised passwords for enterprise security solutions
- Domain Monitoring: Track all email addresses associated with an organization’s domain across breach data
- Data Classification: Understand what types of data were exposed in different security incidents
20. SSL Labs

According to their website, “SSL Labs is a collection of documents, tools and thoughts related to SSL. It’s an attempt to better understand how SSL is deployed, and an attempt to make it better. I hope that, in time, SSL Labs will grow into a forum where SSL will be discussed and improved.”
SSL Labs API Capabilities:
- Invoke assessment and check progress
- Retrieve detailed endpoint information
- Retrieve root certificates
- Choose between summary data or comprehensive information about individual hosts or endpoints
- Retrieve detailed information about certificates
Final Thoughts & Recommendations
Free cybersecurity APIs offer a powerful way to enhance security operations, streamline threat detection, and automate incident response without breaking the bank. Whether you’re a developer integrating threat intelligence, an analyst monitoring malware activity, or a security researcher conducting investigations, these APIs provide valuable data and capabilities.
While free options have limitations—such as usage caps or restricted datasets—they can serve as an excellent starting point for organizations and individuals looking to bolster their security posture. By leveraging the right combination of APIs, you can build a more robust, automated, and efficient cybersecurity workflow.





































