
Top Cyber Threats to the Finance Sector in 2021
Threat actors are increasingly targeting financial institutions for monetary gains. SOCRadar CTIA team continuously monitors the deep and dark web sources to gain visibility into threat actors tirelessly targeting the finance sector in 2021. We observe threat actor posts of stolen credit cards, database access, banking customer data for sale almost every day.
As we close 2021, we wanted to compile the cyber threats that the entire financial sector has experienced throughout the year. But before we start the compilation, it would be good to talk about the transformation of the financial industry in 2021.
Growing Cyber Threats to Interconnected Finance Ecosystem
According to the Bank for International Settlements, the financial sector is experiencing the second-largest share of COVID-19–related cyberattacks, following the health sector. The global financial system is undergoing a remarkable digital transformation, accelerated by the COVID-19 pandemic and, malicious actors are benefiting from this transformation.
In February 2016, hackers tried to steal $1 billion from the central bank of Bangladesh by exploiting vulnerabilities in SWIFT, the global financial system’s primary electronic payment messaging system. $101 million still disappeared, although most transactions were blocked. The potential economic costs of such events and the loss of public trust and confidence can be immense.
International Cooperation Led by IMF
After the 2016 Bangladesh incident, The IMF and other global organizations received numerous requests for cybersecurity support from member nations. G20 governments and central banks could create an international mechanism to build cybersecurity capacity for the financial sector, with a global agency such as the IMF designated to organize the effort.
Improving connections between financial inclusion and cybersecurity is especially critical in Africa, with many countries encountering a transformation to digital financial services. It is the time for the international community—including governments, central banks, supervisors, industry, and other related stakeholders—to gather to address this urgent and vital challenge.
The threat actors behind the attacks include not only daring hackers—such as the Carbanak group, which attacked financial organizations to steal more than $1 billion during 2013–18—but also states and state-sponsored attackers.
For instance, North Korea has taken $2 billion from at least 38 countries in the last five years. Digital financial services are also a target-rich environment for cybercriminals. The October 2020 attack on Uganda’s most extensive mobile money networks, MTN and Airtel, resulted in a four-day interruption of service transactions.
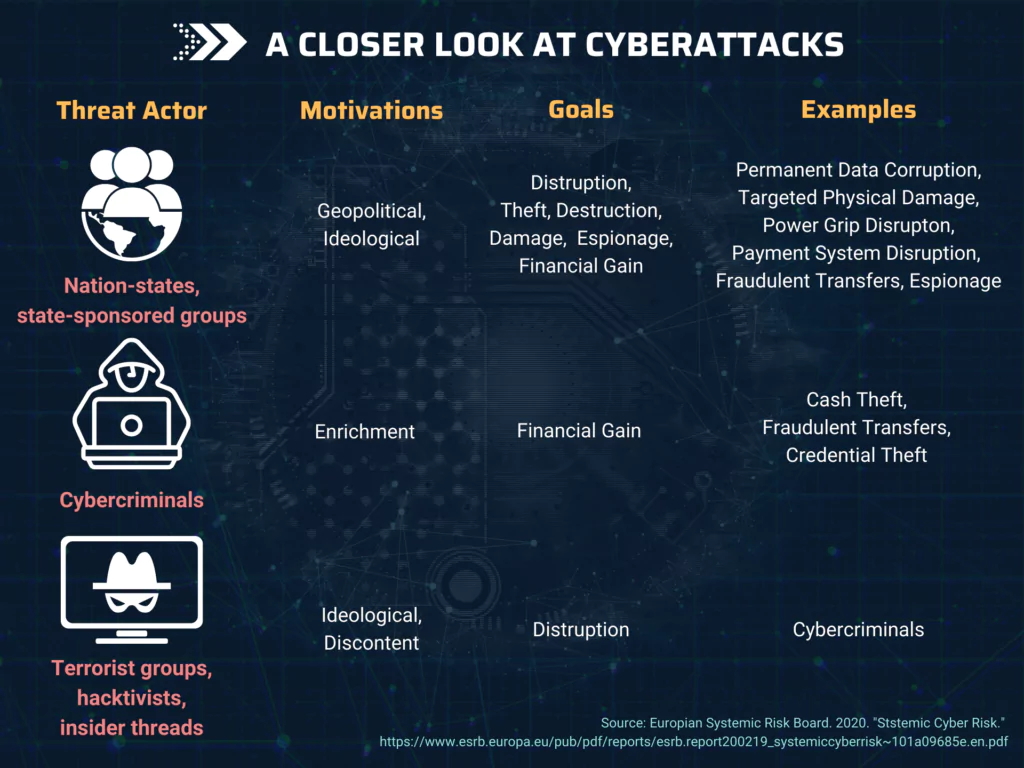
For more robust protection of the global financial system against cyber threats, the Carnegie Endowment for International Peace published a report in November 2020 called “International Strategy to Better Protect the Global Financial System against Cyber Threats.”
Elaborated in collaboration with the World Economic Forum, the report suggests specific actions to reduce fragmentation by promoting international cooperation among government agencies, financial firms, and tech companies.
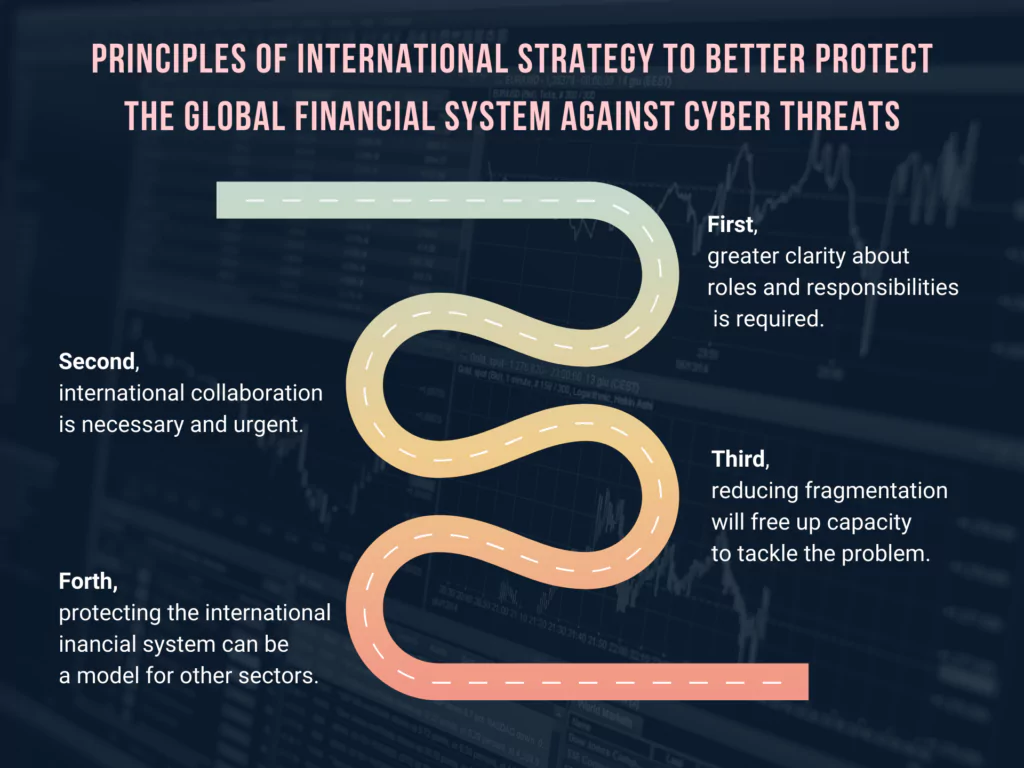
Governments and the industry should interoperate to reinforce security by sharing information on threats and building financial computer emergency response teams (CERTs), modeled on Israel’s FinCERT.
The governments of Australia, The Netherlands, and the United Kingdom have already taken the first step with statements indicating that malicious attacks from abroad can be considered the unauthorized use of force or intervention in the domestic affairs of another state.
Recent Cyber Attacks Targeting Financial Sector
Cl0p’s Newest Alleged Victim

On October 15, SOCRadar has found a post on the Cl0p Ransomware group’s website allegedly announcing a new victim. The victim has 111 employees, and the company revenue is $21 million, according to the post on Cl0p’s website. Operating in the United States, the firm specializes in giving financial consultation on investment and retirement.
New Android Banking Trojan Announced: ERMAC
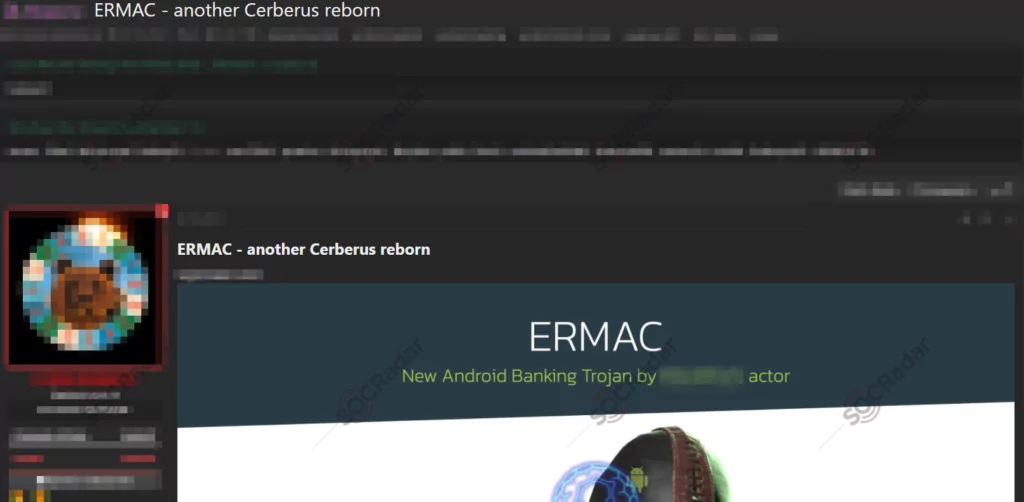
On October 14, SOCRadar has discovered a new mobile banking trojan in a hacker forum. The new trojan, named ERMAC, targets Android devices and is almost entirely based on a well-known banking trojan called Cerberus. The threat actor behind ERMAC, responsible for another mobile banking trojan discovered in 2020, has posted a message stating that the ERMAC botnet is for sale to a limited number of people for $3000 per month.
Credit Cards of US Citizens are for Sale
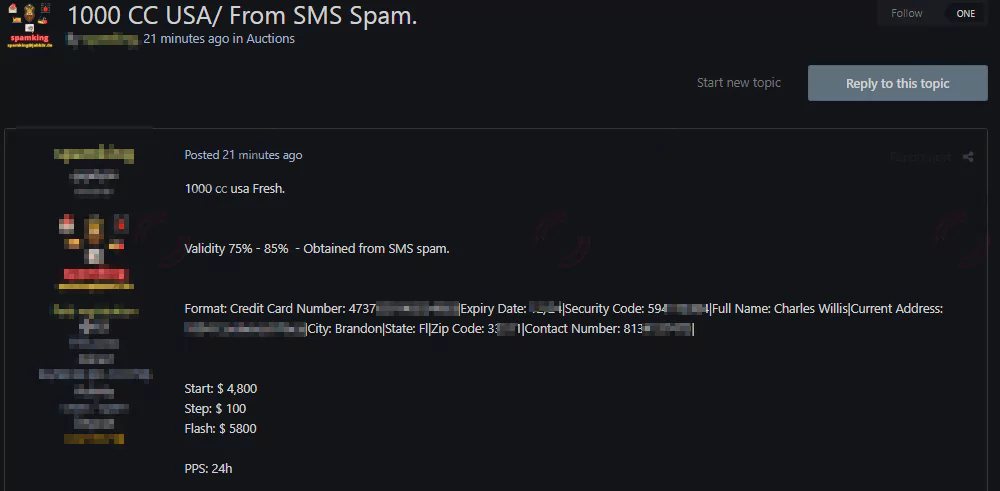
On the 23rd of October, SOCRadar has detected a new alleged credit card sale on a hacker forum. Credit card sale is one of the most common financial sector threats and a headache for the banks’ fraud departments. The deal includes 1000 credit cards and the victims’ contact information, allegedly stolen from US citizens.
The threat actor states that the credit cards are more than %75 valid. They were obtained by SMS spam, a mass smishing (SMS phishing) attack aiming to deceive recipients of the message into providing sensitive information. The sale was auctioned with the start price of $4800, increasing by $100 in each step.
Customer Database for Sale of an Indonesian Bank
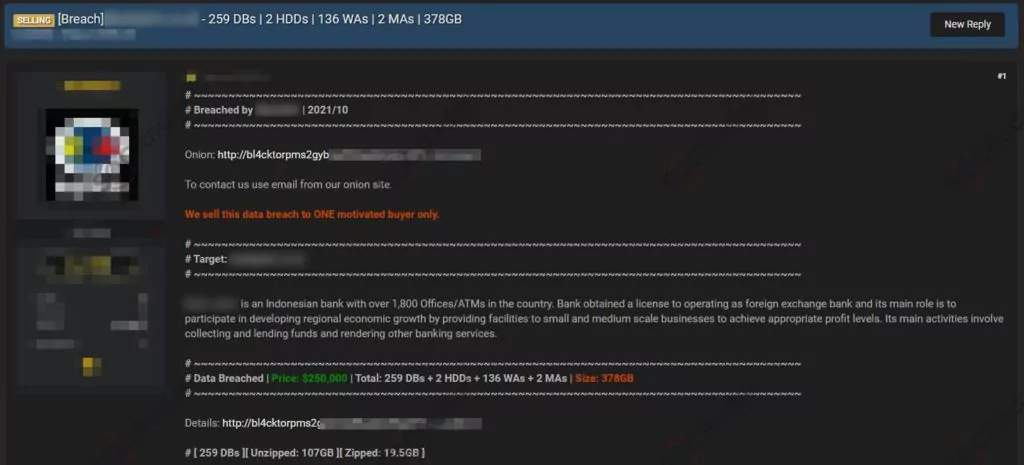
On the 20th of October, SOCRadar has detected an alleged customer database sale of an Indonesian Bank in a hacker forum. The victim has over 1800 offices and ATMs in the country and primarily provides small and medium-scale enterprises. The threat actor states that the database is 378GB in size, and the price for the database is $250.000.
According to the post, the database will be sold to one motivated buyer only. The buyer may use the database to perform malicious attacks such as mass phishing and smishing (SMS phishing), blackmail, and social engineering attacks such as vishing (voice phishing or phone phishing). Or, the buyer can also use the login credentials found in the bank accounts of others in the database to gain access.
Customer Database of a FinTech Company is for Sale
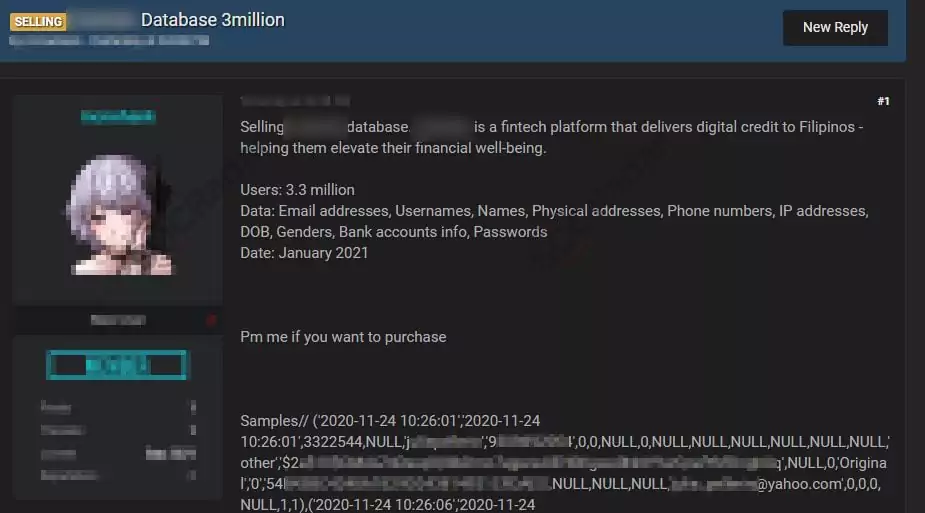
On September 22, SOCRadar has detected a post in a hacker forum, including an alleged customer database sale of a FinTech company based in the Philippines. Financial Technology (FinTech) enterprises aim to develop new technology to improve and automate financial services. The victim company primarily operates by delivering digital credits to Filipinos.
Hackers target FinTech companies more than traditional finance companies because the automated procedures generally have more vulnerabilities hackers can exploit. The threat actor states that the data includes name and surname, date of birth, gender, address, phone number, IP address, bank account info, and passwords of 3.3 million users. The threat actor did not explicitly state the price for the database.
Click here to read the detailed report prepared by SOCRadar for the Finance Industry.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging.
One click-by-mistake can result in malware bot infection. SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by targeted country or industry.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free



































