
Windows Shortcut Zero-Day (ZDI-CAN-25373) Exploited by State-Backed Threat Actors Since 2017: Overview of Key Details
A sophisticated zero-day vulnerability, ZDI-CAN-25373, has been secretly exploited for years by multiple state-backed hacking groups, highlighting its critical security implications. This exploit takes advantage of Windows shortcut (.lnk) files, allowing attackers to discreetly execute malicious commands without detection. Security analysts have linked this vulnerability to cyber-espionage campaigns and data theft targeting organizations worldwide.
Researchers have most recently revealed that since 2017, ZDI-CAN-25373 has been actively used by 11 nation-state actors from North Korea, Iran, Russia, and China. Trend Micro’s Zero Day Initiative (ZDI) have uncovered nearly 1,000 malicious .lnk samples that utilize this exploit, with evidence suggesting far more instances remain unidentified.
Despite the clear risks associated with this vulnerability, Microsoft has opted not to issue a security patch so far, citing that it does not meet their criteria. As a result, organizations must take immediate steps to defend against this growing threat.
What is ZDI-CAN-25373?
Before diving into the full scope of this vulnerability, let’s first examine how it works and how Advanced Persistent Threat (APT) groups have leveraged it for years.
To exploit ZDI-CAN-25373, threat actors use specially crafted .lnk files, concealing malicious command-line arguments. These hidden commands allow attackers to execute payloads stealthily, evading detection by traditional security measures.
The exploitation method is particularly dangerous because:
- Malicious commands are embedded within shortcut files, making them difficult to detect.
- Attackers use whitespace padding in the COMMAND_LINE_ARGUMENTS structure to hide execution details.
- Windows does not display these hidden commands in its user interface, requiring third-party tools for inspection.
- The ability to mimic legitimate files makes these attacks highly deceptive.
- The exploitation method allows attackers to bypass some security software, which typically focuses on executable file-based threats rather than shortcuts.
- The low-level nature of the exploit enables cybercriminals to use it as an entry point for deploying more sophisticated malware strains.
- Attackers frequently leverage social engineering techniques to deliver malicious .lnk files to targets, often disguising them as documents, images, or legitimate software installers.
Who Is Exploiting ZDI-CAN-25373?
Research shows that state-sponsored APT groups have been abusing ZDI-CAN-25373 primarily for cyber espionage and data theft.
The highest number of APT attacks originate from North Korea (45.5%), followed by Iran (18.2%), Russia (18.2%), and China (18.1%). Aside from APTs, various other threat actors from these four countries, as well as from countries such as India and Pakistan, have demonstrated some level of activity.
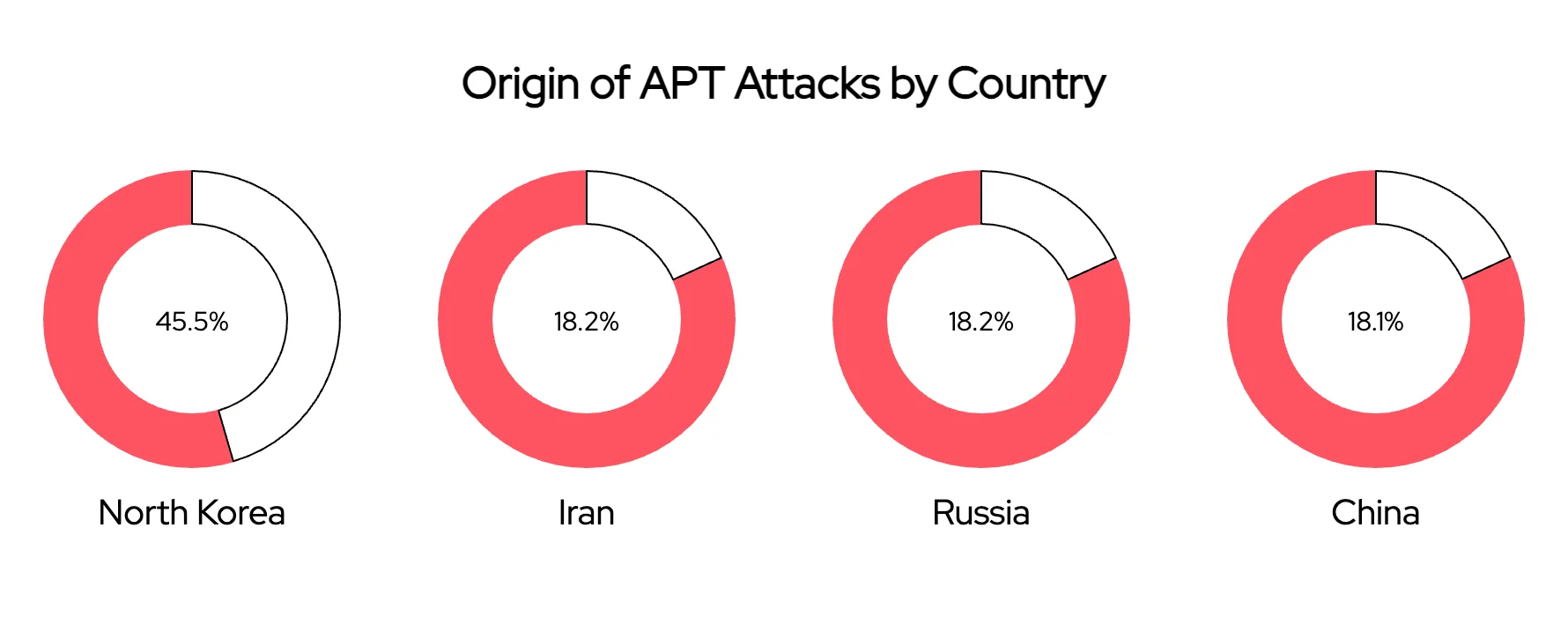
Origin of APT attacks targeting the Windows Shortcut Zero-Day ZDI-CAN-25373
It must be noted that APT groups often share Tactics, Techniques, and Procedures (TTPs) among themselves, making it difficult to attribute specific attacks to one entity. Researchers furthermore note that some financially motivated cybercriminal organizations have also leveraged ZDI-CAN-25373 for targeted intrusions. Some state-sponsored groups appear to work in tandem with cybercriminal enterprises, trading exploits and tactics in underground forums.
Which Sectors Have Been Targeted?
Now that we’ve covered the key details about the countries where these attacks originate, let’s shift our focus to the industries that have been targeted the most by these cyber threats. According to Trend Micro’s data, the industries affected by these attacks include:
| Sector | Percentage of Attacks |
| Government | 22.8% |
| Private sector | 14% |
| Financial institutions | 8.77% |
| Think tanks | 8.77% |
| Telecommunications | 8.77% |
| Military and defense | 8.77% |
| Energy | 8.77% |
| Cryptocurrency | 5.26% |
| Education, healthcare, and media | 3.51% each |
| Critical infrastructure and nuclear sectors | 1.75% each |
Governments and private-sector organizations in North America, Europe, East Asia, and Australia are particularly vulnerable, with intelligence agencies and financial entities frequently targeted due to the high value of their data. State-backed actors often prioritize government and defense targets to gain access to classified information and strategic intelligence, while cybercriminal organizations exploit the vulnerability for financial gain through ransomware deployment and credential theft.
Malware Payloads Linked to ZDI-CAN-25373
Lastly, let’s look at the malware strains used in these campaigns. A variety of malware strains have been deployed in campaigns exploiting this vulnerability. Here are the key categories and malware/tools:
- RATs and Loaders: Xeno RAT, Quasar RAT, PupyRAT, Warzone RAT, Remcos
- Banking Trojans and InfoStealers: Gozi, Snake Keylogger, Lumma Stealer, Racoon Stealer
- Malware-as-a-Service (MaaS): Exploited extensively with 79 tracked samples
- Cobalt Strike and Sliver: Common penetration testing tools repurposed for malicious use
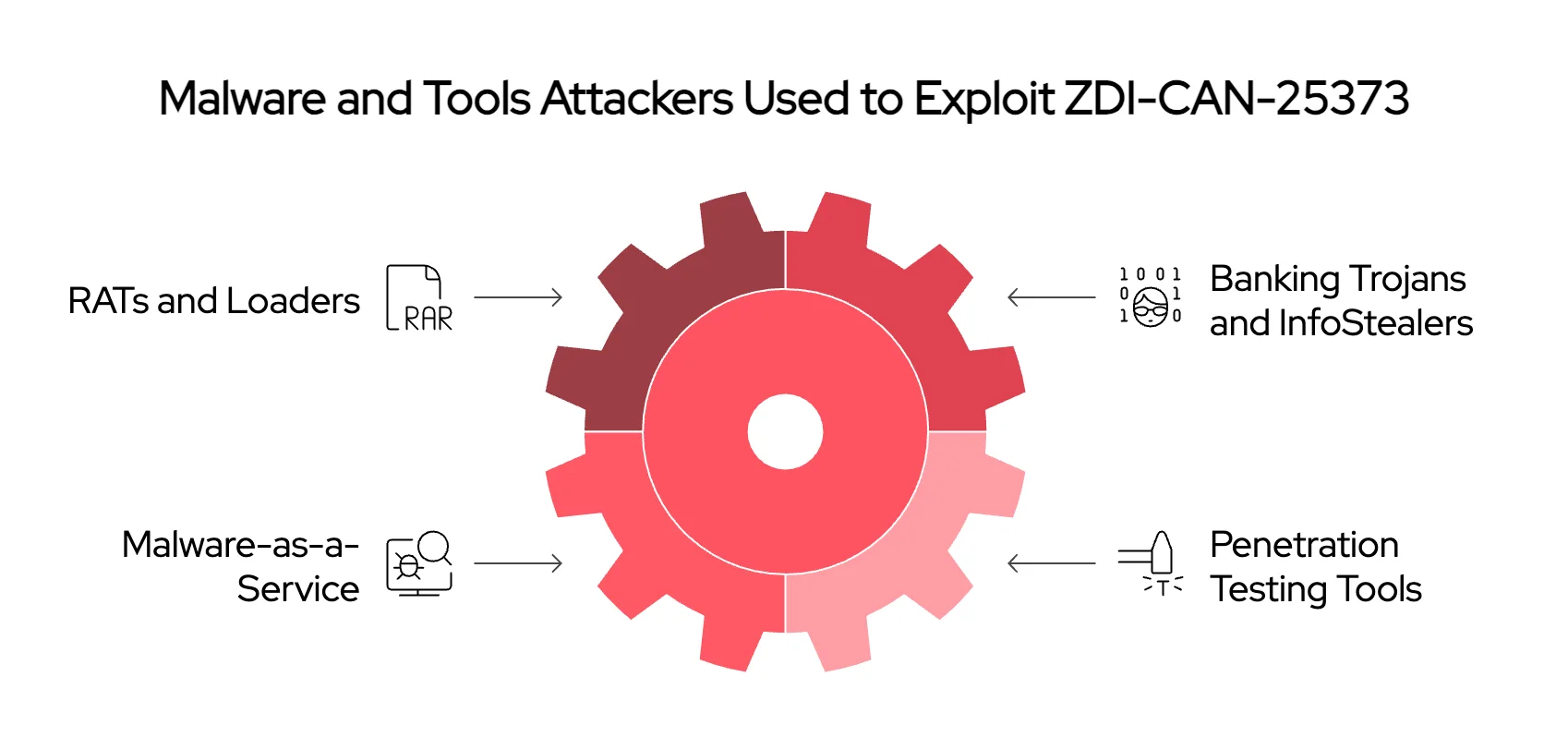
Types of malware and tools attackers used to exploit ZDI-CAN-25373
Interestingly, the cybercrime group Evil Corp has used ZDI-CAN-25373 in their Raspberry Robin campaigns, further demonstrating its wide abuse. These malware payloads allow attackers to establish persistent access, exfiltrate sensitive data, and even deploy ransomware attacks in some cases.
Researchers also found that nearly 70% of attacks leveraging ZDI-CAN-25373 were primarily focused on espionage and information theft, while around 20% had financial motives. Some groups appeared to use the financial gains from these campaigns to fund additional cyber espionage efforts.
About Microsoft’s Response & Security Recommendations
Trend Micro researchers state that they submitted a Proof-of-Concept (PoC) exploit for ZDI-CAN-25373 to Microsoft through ZDI’s bug bounty program, but Microsoft declined to issue a patch.
In order to defend against continued exploitation in the interim, security researchers and organizations are left to look for alternate mitigation strategies. Best practices include:
- Monitor and restrict .lnk file usage: Organizations should enforce policies limiting the execution of shortcut files from untrusted sources.
- Implement endpoint protection: Ensure security solutions can detect and block suspicious shortcut files and hidden command-line execution.
- Conduct network monitoring: Log and analyze anomalous activities related to .lnk files, especially those originating from unknown or unverified sources.
- Regularly update and patch software: Although Microsoft has not issued a direct fix, ensuring that all Windows systems are updated can help mitigate other vulnerabilities that attackers may chain with ZDI-CAN-25373.
- Train employees on phishing risks: Since many .lnk-based attacks begin with phishing emails, organizations should educate staff on identifying suspicious attachments and links.
- Inspect shortcut files using security tools: Since Windows does not display hidden command-line arguments within .lnk files, organizations must use forensic tools to analyze shortcut metadata.
- Use behavioral analysis: Security teams should employ advanced detection mechanisms that focus on behavioral indicators rather than relying solely on static malware signatures.
- Restrict execution of script-based attacks: Attackers often use .lnk exploits to execute PowerShell scripts and other malicious scripts. Disabling unnecessary scripting capabilities can reduce risk.
For broader protection beyond this vulnerability, organizations should leverage comprehensive threat intelligence platforms like SOCRadar Extended Threat Intelligence (XTI).
SOCRadar XTI integrates multiple intelligence sources – Dark Web, vulnerability insights, Attack Surface Management, and threat actor tracking – delivering actionable alerts and context-rich insights. This holistic view empowers security teams to anticipate threats, prioritize defenses, and rapidly respond to incidents, enhancing overall resilience against sophisticated cyberattacks.
SOCRadar XTI platform, Dashboards
Conclusion
With no official patch from Microsoft, organizations must take defensive actions to mitigate risks. By implementing strong security policies, monitoring for unusual activity, and leveraging threat intelligence, organizations can better protect themselves against this ongoing threat.
For further technical details, readers can explore the official research blog. Additionally, Indicators of Compromise (IOCs) can be found here.
To aid defenders in detecting and mitigating attacks leveraging ZDI-CAN-25373, researchers have also provided a YARA rule designed to identify malicious .lnk files associated with this exploit. Here is the supplied rule:
YARA Rule:
rule ZTH_LNK_EXPLOIT_A
{
meta:
author = “Peter Girnus”
description = “This YARA file detects padded LNK files designed to exploit ZDI-CAN-25373.”
reference = “<LINK_TO_BLOG>”
target_entity = “file”
strings:
$magic = {4C 00 00 00 01 14 02 00}
$spoof_a = {20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00}
$spoof_b = {09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00}
$spoof_c = {0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00}
$spoof_d = {0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00}
$spoof_e = {11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00}
$spoof_f = {12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00}
$spoof_g = {13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00}
$spoof_h = {0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00}
condition:
$magic at 0x00 and ($spoof_a or $spoof_b or $spoof_c or $spoof_d or $spoof_e or $spoof_f or $spoof_g or $spoof_h)
}




































