
Investigating APT Groups’ Attempts to Reuse Old Threat Indicators
Introduction
The landscape of cybersecurity is a complex and evolving battleground. In this arena, Advanced Persistent Threat (APT) groups are the master tacticians, continuously adapting and employing new methods to breach defenses and fulfill their malicious agendas. One such tactic gaining prominence involves resurrecting and repurposing historical Indicators of Compromise (IOCs), including artifacts like malicious IP addresses and domains.
Once used for malicious intent, an IOC always carries potential risk from a threat intelligence standpoint. Even if an IOC has been inactive or seemingly dormant for a while, it necessitates continued vigilance and monitoring. Threat actors may reutilize these apparently ‘spent’ IOCs, breathing new life into them for fresh campaigns. This tactic presents a significant challenge for cybersecurity professionals, as it adds a new dimension to threat detection and incident response.
We aim to delve deep into this issue in this research conducted by the SOCRadar Threat Research Team. We seek to uncover the probability and impact of APT groups reactivating previously used IOC addresses and the potential threats such actions may generate. By examining historical cases and leveraging data from reputable sources, including published research reports and incident response engagements, we aim to highlight the implications of IOC reuse and identify the associated risks.
Our investigation extends to an in-depth analysis of the tactics employed by APT groups, the vulnerabilities they exploit, and the motivations behind their operations. This research endeavors to equip security practitioners and organizations with the knowledge required to assess the threat landscape effectively. By understanding the potential risks associated with IOC reuse, stakeholders can bolster their defenses, implement robust monitoring systems, and develop strategic response mechanisms to mitigate the impact of emerging APT threats.
Key Points
- Malicious Domains and IP Addresses: The research examined 274 domains and 629 IP addresses used for malicious purposes.
- Sinkhole: A “sinkhole” in cybersecurity is a technique used by security teams to redirect network traffic toward a monitored server to isolate, study, and potentially mitigate malicious activity. This is often done by taking over a domain used by malicious software and redirecting traffic from this domain to the sinkhole server.
- Rented and Idle Domains: Of the malicious domains, 112 are still rented, while 162 domain addresses are idle.
- Autonomous System Numbers: ASNs are unique identifiers assigned to individual networks or organizations that operate their own routing policies on the Internet. It was found that the currently registered malicious domain names were registered through various companies. The top five most frequently encountered companies with relevant AS numbers are Amazon.com, Inc., OVH SAS, Cloudflare, Inc., GMO Internet, Inc., and LeaseWeb Netherlands B.V.
- C2 Applications: Among the malicious C2 domain addresses, the most popular C2 application was identified as CobaltStrike. Approximately 71% of the C2 domain addresses mentioned in the reports were CobaltStrike C2 addresses.
- C2 Addresses and Risks: Out of the 162 idle domain addresses, 91 have been used as C2 addresses. These addresses are not blacklisted in many blacklist services or are classified as low-risk.
- Organizations Hosting the IP Addresses: Among the identified 629 IP addresses, there are 235 different organizations. The top five most frequently seen organizations are AS12874 Fastweb SpA, AS23470 ReliableSite.Net LLC, AS16276 OVH SAS, AS7018 AT&T Services, Inc., and AS52048 DataClub S.A.
- SOCRadar Extended Threat Intelligence Solution: SOCRadar Extended Threat Intelligence solution effectively protects against these significant threats, which often go unnoticed. The company offers a proactive approach to detecting these types of threats early and taking necessary precautions.
APT Groups Do Not Give Up Old Toys
Sometimes, we may have to wear what we have worn before, which is with APT groups. The inspiration behind this research stems from a notable incident involving the TurlaAPT group, which reutilized a previously used IOC to orchestrate a targeted attack. As reported in research, the Turla APT group’s reclamation of an IOC domain address catalyzed this study. Building upon this incident, our analysis delves into the implications and potential risks of using historical IOCs by APT groups.

Reusing domain names previously employed for malicious purposes by APT groups can pose a renewed risk when these domains become available again and are re-registered. In such cases, compromised machines that still harbor the associated malware may unknowingly attempt to communicate with the reactivated domain, inadvertently resurrecting past threats.
This phenomenon, known as domain reanimation or domain shadowing, is a well-documented tactic utilized by threat actors. By re-registering expired or abandoned domains, these actors can exploit existing infrastructure and compromised machines that are still infected. This enables them to regain control, establish command and control communication, or distribute additional malware.
The implications of domain reuse lie in the fact that security systems and network defenders may not be aware that these once-malicious domains are now active again. Consequently, they may fail to detect the resurfaced threat and take appropriate defensive measures. This provides a prime opportunity for threat actors to leverage the existing compromised machines and launch new attacks, potentially circumventing security controls and inflicting further harm.
To mitigate these risks, organizations and security professionals must adopt proactive measures to monitor the landscape of expired and re-registered domains. By actively identifying and flagging domains with a history of malicious activity, defenders can enhance their defensive capabilities, update security measures, and effectively mitigate the potential threats associated with the resurgence of past indicators of compromise (IOCs).
Analyzing IOCs
As the SOCRadar Threat Research Team, we keep a vigilant eye on all indicators present in the cyber landscape. New and old attack vectors are rigorously evaluated for risk, and these observations feed into our platform. This research centered on two indicators: the domain and IP addresses reported within various cybersecurity reports.
Following our manual investigation to identify the malicious use of domain addresses gleaned from these reports, we assembled a list of suspicious domains. We make a table of these domains in subdomains and full URL formats. Simultaneously, we extracted all IP addresses presented in the reports to create a comprehensive list.
We divided the domain information into two categories: rented and available. We then ran all domains through Shodan, blacklist checks, and SOCRadar XTI, with registered domains also undergoing whois verification. To identify Command and Control (C2) servers, all domains and IP addresses were processed using scripts capable of C2 detection (e.g., grab_beacon_config.nse), checking whether they are currently involved in any attack campaigns.
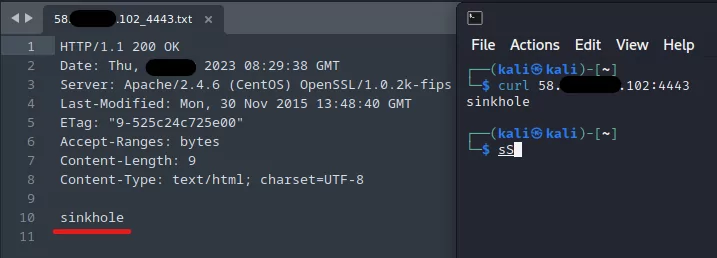
We found no traces indicating the current C2 use of these domains and IP addresses. Similarly, various scripts were run to identify if any current vulnerabilities existed in the domains and IP addresses. Some of these domains have been reclaimed for research purposes by cybersecurity organizations for sinkhole. This rigorous process underscores our commitment to providing the most comprehensive and up-to-date threat intelligence.
Investigation of IOCs Used in the Past
SOCRadar Threat Research Team has reviewed an extensive collection of threat research reports providing a comprehensive analysis. 49 PDF reports spanning from 2015 to 2023 were rigorously analyzed. These reports encompass contributions from recognized cyber security vendors, threat researchers, and intelligence firms, including these various sources, which aim to provide a well-rounded perspective on APT activities and help identify patterns and trends related to IOC reuse.
Within the scope of this research, an extensive range of APT groups were considered. Specifically, reports associated with 15 distinct APT groups were examined, including APT28, APT29, APT34, APT36, Carbanak, CharmingKitten, EquationGroup, Lazarus, Machete, Magecart, MuddyWater, OceanLotus, Sandworm, Turla, and WizardSpider. By reviewing reports specific to each APT group, we sought to identify instances where historical IOCs had been employed, enabling a comprehensive understanding of the potential risks posed by IOC reuse across various threat actors.
Statistics of Domain and IP Addresses Used by APT Groups
Domain and IP Address Use Statistics
Our analysis encompassed a total of 274 distinct domains that were maliciously used, according to the examined reports. Furthermore, these reports revealed 629 unique IP addresses implicated in these threats.
Domain Status
Within the malicious domains identified, we found that 112 remain leased at the time of writing, whereas 162 are currently available for registration. This raises concerns, as these available domains, once used for nefarious purposes, especially if they are not correctly flagged in cyber threat intelligence services.
ASN Registrations of Domain Addresses
Regarding the current registration of these domains, we identified the top five Autonomous System Number (ASN) provider companies that manage these domains. Approximately 18.37% of the domains are registered with Amazon.com, Inc., followed by OVH SAS and Cloudflare, Inc., each holding approximately 10.20%.GMO Internet, Inc. accounts for roughly 8.16% of these domains, while LeaseWeb Netherlands B.V. manages about 4.08%.
C2 Domains and Applications
A significant observation from our research pertains to using C2 (Command and Control) domains. According to our analysis, CobaltStrike was the most popular C2 application, as it was associated with approximately 71% of the reported C2 domains.
Of the 162 available for rent domains, 91 were previously used as C2 addresses. Interestingly, many of these C2 addresses are not blacklisted or labeled low-risk in some threat intelligence services. This leaves open the possibility of victim computers still attempting to communicate with these addresses.
It is, therefore, critical that organizations, especially those without web traffic risk control or strong threat intelligence support, are aware of the potential reactivation of these addresses. Ignoring this possibility could put them at high risk.
In conclusion, understanding these usage patterns and statistics contributes to more effective threat intelligence, helping to predict, prevent, and respond to future cyber threats.
IP Address Ownership
Investigating the ownership of the 629 unique IP addresses revealed in our report unveils another layer of understanding about the infrastructure used for cyber threats. Our findings show that these IP addresses are registered to 235 different organizations.
The top five organizations with the most registered IPs provide insight into the infrastructure most frequently utilized by APT groups. The organization with the most IPs is Fastweb SpA (AS12874), with roughly 3.49% of the total IPs. This is closely followed by ReliableSite.Net LLC (AS23470) with approximately 3.34%. OVH SAS (AS16276) comes in third, accounting for around 3.02% of the IPs. AT&T Services, Inc. (AS7018) and DataClub S.A. (AS52048) round out the top five with about 2.07% and 1.91%, respectively.
Delving further into the geolocation data of the 629 unique IP addresses revealed an interesting pattern in the preferred locations for Advanced Persistent Threat (APT) groups. Our analysis revealed a clear distribution of the most common countries where these IPs were registered.
The United States leads the chart with 141 IPs, forming a notable portion of the analyzed dataset. Italy follows with 58 IPs, and Germany is not far behind, hosting 36 of the reported IPs. France and Japan come next, with 31 and 30 IP addresses, respectively. South Korea presents 28 IPs, while India accounts for 19. The Netherlands and Taiwan host 14 IPs each, and Russia, despite its notorious reputation in the cyber landscape, comes in last in this top 10 list with 14 IPs.
This geographical dispersion underscores the global scale and broad reach of APT groups. It also highlights that while some countries may traditionally be viewed as more significant sources of cyber threats, they can originate from virtually anywhere. This understanding reinforces the importance of a robust and globally-focused cybersecurity strategy to effectively counter such threats.
This information can be invaluable for cyber defense measures, as it highlights the most commonly used networks and may provide a basis for improved threat detection and prevention strategies.
Dark Spots in Threat Intelligence
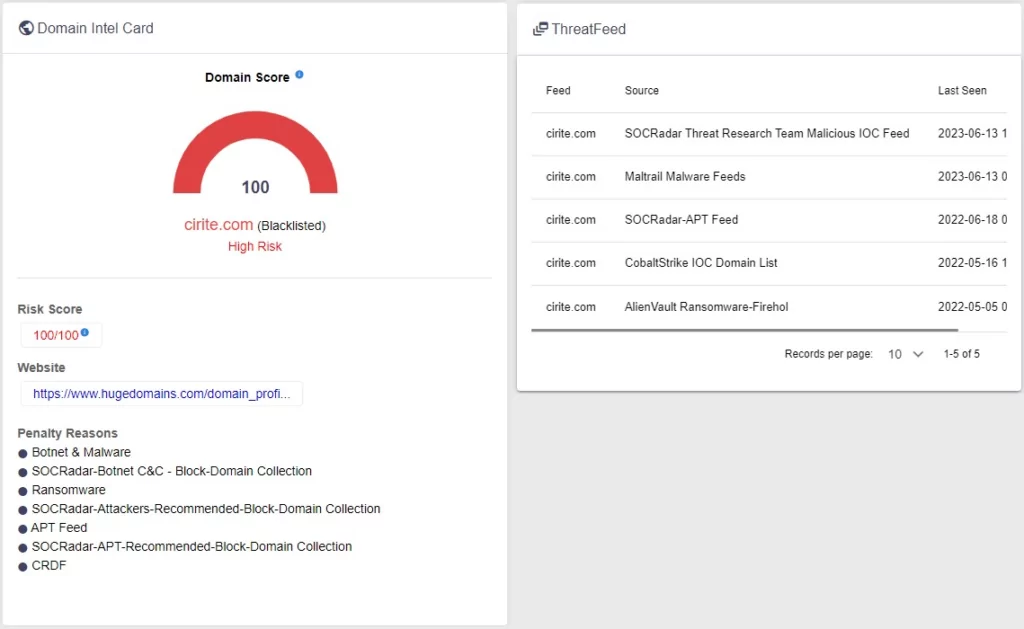
In the data table below, we examined, we see that many of the C2 domains that have been used in malicious acts in the past and are still registered or available for rent are not included in the blacklist services or do not serve acceptable risk scores. This shows that traditional blacklist methods may not always be able to react quickly enough in an ever-changing and evolving cyber threat environment. Since these domains are valuable assets that potential attackers can target, this lack of detection poses a significant risk, especially for organizations that do not receive threat intelligence support or do not provide adequate protection. This risk is unacceptable as we know that in the past, APT groups have reacquired domains with a significant impact on victim machines.
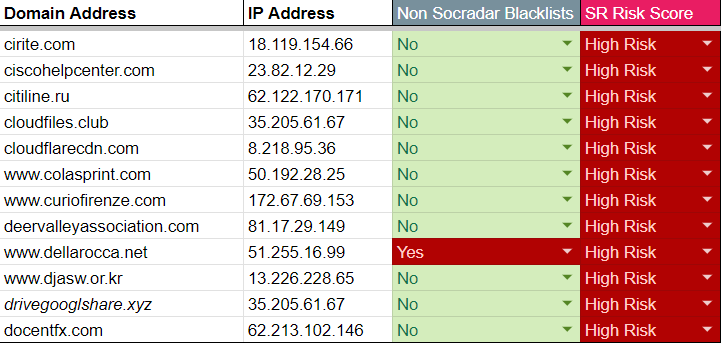
SOCRadar Extended Threat Intelligence comes into play in such situations. Our solution monitors and detects malicious domains and IP addresses not seen in threat intelligence and blacklist services. In this way, even at the initial stage of an attack, SOCRadar users can be aware of these threats and take the necessary measures. This approach ensures a security posture that is reactive and proactive, keeping our users one step ahead of potential attacks. This is one of the most striking and valuable features of SOCRadar’s Extended Threat Intelligence service. With us, your digital assets will always be protected, and you’ll be one step ahead of threats.
Usage Types of Expired Domains
The list of domains previously used for malicious purposes provides valuable information about the activities of APT groups. Analyzing the list reveals some recurring trends and inferences. For example, the Lazarus APT group focused on social engineering and command and control infrastructure using IOCs such as downloaders, fake login panels, and C2 server domains. The Dukes APT group is associated with IOC-related domains, indicating that they prefer to establish communication channels. CobaltStrike C2 servers stand out and show widespread adoption by multiple APT groups for various purposes, including exploiting zero-day vulnerabilities. In addition, the OceanLotus APT group uses multiple IOCs, such as C2 and downloader, to enable command and control operations and malware propagation. Reusing these IOCs by different APT groups underlines the risk of re-emergence of past threats when domains are reactivated. This highlights the need for continuous monitoring and proactive measures to mitigate the potential risks associated with the re-emergence of these malicious indicators.
Strategies of APT Groups in Selecting Domain Names Pattern
Based on the list of domain names you provided, we can see that APT groups used them for different purposes, such as IOC (Indicator of Compromise), C2 (Command and Control), and as a Downloader. Let’s delve into the domain types and the differences in selection for IOC and C2 purposes.

Before we begin, it’s important to note that the categorization depends on the purpose of the domain at the time of its use. A domain used as an IOC in one instance might be used as a C2 server in another. The analysis here is based on the specific purpose attributed to each domain in your list.
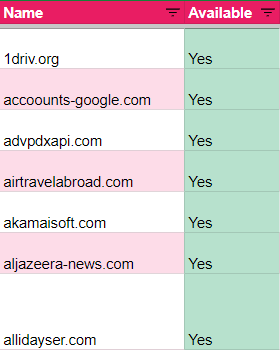
- Deceptive Similarity: This approach is prevalent in domains. These domains often mimic well-known websites or services to trick users into visiting them. Examples include ‘accoounts-google.com,’ ‘apple-checker.org,’ ‘googledrive.download,’ and ‘googleupload.info.’
- Randomly Generated Strings: This method appears more frequently in the C2 type domains. Examples include ‘advpdxapi.com,’ ‘allsafebrowsing.com,’ ‘befatu.com,’ and ‘akamaisoft.com.’ The seemingly random and unrelated string of characters in these domain names can make them harder to identify and track, thus providing an advantage for APT groups.
- Typosquatting: Domains with topical or sector-specific relevance are used for both IOC and C2 purposes but are more commonly seen in the IOC type. These domains are designed to attract individuals within particular sectors or with specific interests. Examples include ‘defenceiq.us,’ ‘defencereview.eu,’ and ‘militaryobserver.net.’
Based on this preliminary analysis, the distribution of domain types could be estimated as follows (percentages are approximations):
- Deceptive Similarity: 40%
- Randomly Generated Strings: 35%
- Topical Relevance: 25%
The pattern difference between IOC and C2 selection mainly lies in the higher usage of deceptive similarity and topical relevance in domains. In contrast, C2-type domains seem to utilize random string generation more frequently. This can be attributed to the fact that IOC domains are often used for initial compromise or phishing attempts, where mimicking a legitimate service or attracting a target group’s interest is crucial. On the other hand, C2 domains are primarily used for controlling compromised systems, where obfuscation and evasion from detection are of paramount importance.
Proactive Defense: Brand and Domain Monitoring with SOCRadar
As SOCRadar, a prominent threat intelligence company, we firmly believe in staying ahead of potential threats. One critical aspect is our ability to track newly registered domains and conduct comprehensive brand monitoring. These activities allow us to promptly detect domains that have been registered with malicious intent, or those that exploit similarities to well-known brands or industries, attempting to mislead or confuse internet users.
Our approach enables us to identify these potentially harmful domains swiftly, providing ample opportunity to initiate preventive measures. As a result, our clients can fortify their defenses against such threats, significantly reducing the likelihood of successful cyber-attacks and reinforcing their overall security posture. Through our vigilant monitoring and robust threat intelligence, SOCRadar empowers organizations to tackle the evolving threat landscape proactively and efficiently.
Protection Strategies against the Reuse of Malicious Domains
The potential threat posed by the reactivation of domains previously utilized by Advanced Persistent Threat (APT) groups cannot be overstated. Upon reviewing 49 different threat reports, we’ve analyzed the risks associated with domains that may have been released and subsequently used to re-infect systems still attempting to establish a connection.
Adopting proactive and robust cyber security measures is crucial to mitigate these risks. Here, the role of Threat Intelligence solutions, such as those provided by SOCRadar, becomes crucial. A proactive Threat Intelligence approach facilitates early detection of potentially harmful network connections, enabling timely initiation of corrective actions.
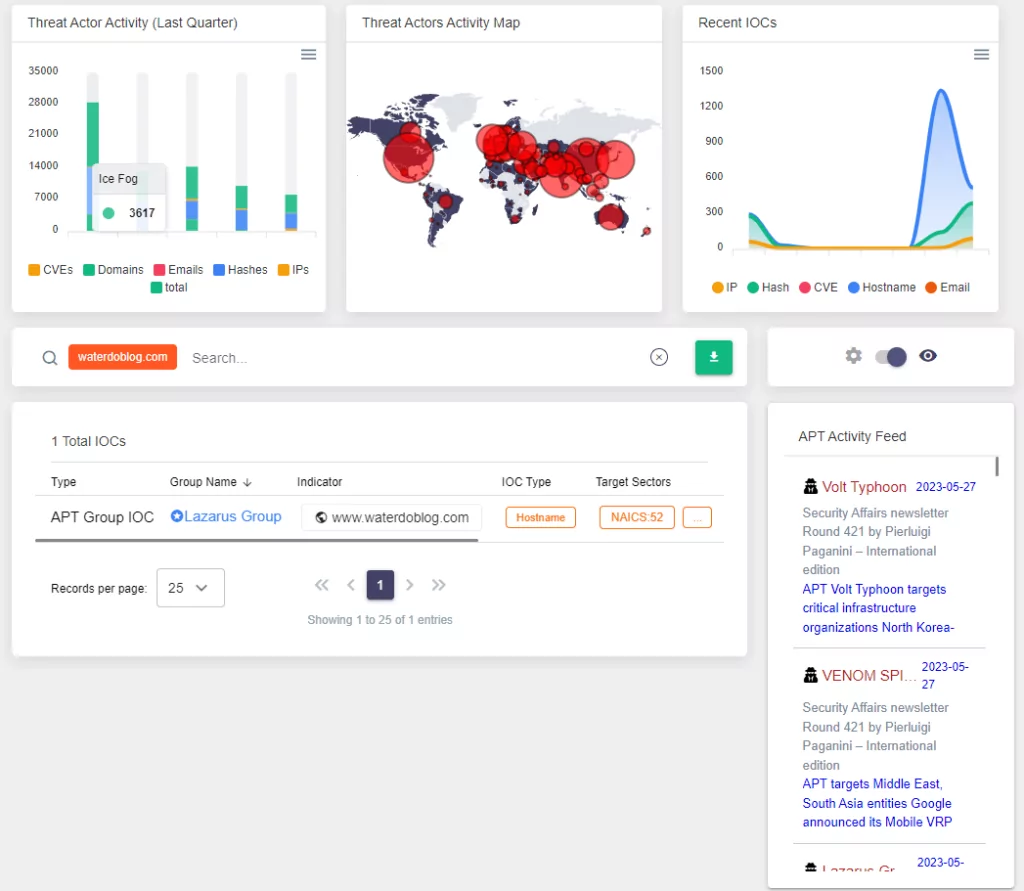
SOCRadar’s Extended Threat Intelligence solutions have been designed to provide comprehensive coverage and protection. Continuously monitoring the internet-wide domain and IP data provides a real-time understanding of the global threat landscape. This includes tracking malicious domains’ reactivation and potential implications and ensuring client organizations are always apprised of these risks.
Implementing these solutions is critical, but that alone might not be enough. The dynamic nature of cyber threats requires a multi-layered defense strategy, such as a defense-in-depth approach, that includes robust intrusion detection systems, firewalls, anti-malware software, and strong password policies. Regular updates and patches for all software, combined with secure, encrypted connections for all network activities, can also significantly reduce exposure to threats.
Furthermore, employee training and awareness programs can help prevent accidental clicks on malicious links or falling victim to phishing attacks, two common ways APTs gain initial access.
Ultimately, combining solid cybersecurity policies, implementing proactive threat intelligence solutions like SOCRadar, and a well-informed workforce can significantly enhance an organization’s resilience against the persistent threat of APTs.
Conclusion
This report examines the threat potential of domains used in malicious activities that can be reactivated. This research, prepared by our Threat Intelligence Team, aims to raise awareness of the possibility of re-renting these domains and communicating with previously infected systems.
Such a threat can severely threaten business continuity and the organization’s reputation. Therefore, detecting such threats on time and taking the necessary measures is essential. This is where SOCRadar’s Extended Threat Intelligence solution comes into play.
SOCRadar’s Extended Threat Intelligence solution can help you detect and block such potential threats in advance by continuously monitoring and analyzing the global threat landscape. Although these domains may have expired in the present day, there’s still a possibility, as witnessed in past incidents, that groups like the Turla APT may reactivate these domains for their nefarious activities. To guard against such a probability, it’s recommended to integrate these feeds with your security technologies using the CTI platform and leverage SOC use cases. Detection of reactivated malicious domains is just one aspect of this service. It also offers the necessary information and tools to initiate precautions if systems persist in communicating with these domains.
Please note that the results in this report reflect the status of the domains at the time of research, conducted and published between (start-date) and (end-date). The current status of these domains may differ, as domain information and associations can change over time due to various factors such as domain expiration, re-registration, or changes in threat intelligence ratings.
In conclusion, SOCRadar’s Extended Threat Intelligence service provides an effective and reliable solution for organizations to strengthen their cyber security posture and proactively approach potential cyber threats. This is vital for dealing with current cyber threats and increasing resilience against future threats.



































